It has been a while since I have been excited to write about encrypted tunnels. It might be the sheer pain of troubleshooting old technologies, or countless hours of falling down the rabbit hole of a project’s source code, that always motivated me to pursue a better alternative (without much luck). However, I believe luck is finally on my side.
In this blog post we will explore using open-source WireGuard, a new technology that offers encrypted tunnels with remarkable performance and an effortless implementation, to establish secure encrypted tunnels between workloads in K8s clusters.
Introduction: WireGuard
With the release of open-source Calico 3.14 back in June of 2020, Tigera announced a tech preview of its WireGuard integration, which allows node-to-node traffic to be encrypted using WireGuard.
Other encryption methods (e.g. TLS) were available to encrypt workloads’ traffic at higher TCP/IP layers (in this case, the Application Layer). However, WireGuard targets traffic at a lower layer (the Transport Layer), which makes it effective for a wider range of applications, and also reduces complexity for the user.
WireGuard is an open-source project that implements virtual private network (VPN) techniques to establish secure point-to-point connections leveraging Linux kernel capabilities. It aims to be faster, simpler, and leaner than previous technologies. With only around 4,000 lines of code, WireGuard source code is also easier to audit.
WireGuard is designed to be extended by third-party programmers and scripts, which makes the project more valuable to the community. In terms of logging and dynamic firewall updates, this can be a great factor for its adoption.
However, our focus will be on kOps’s new release, which enables easy implementation of Calico and WireGuard in self-managed K8s clusters.
Let’s start by exploring some performance metrics.
Performance
Before we dive into numbers, it is worth mentioning that benchmark results are heavily influenced by the test environment. For this test, we used a K8s cluster with 3 nodes using t3.medium ec2 instances from AWS, with 5Gbps burstable network bandwidth. (You can view t3 tier details at this link.)
WireGuard’s remarkable performance in comparison to older technologies is one of the main reasons behind its integration into Calico. Combined with Calico’s eBPF data plane, WireGuard was able to utilize (on average) 73% of the 5Gbps bandwidth link in order to send encrypted traffic to another node.
The following figure showing network throughput shows the Calico eBPF data plane with different settings.
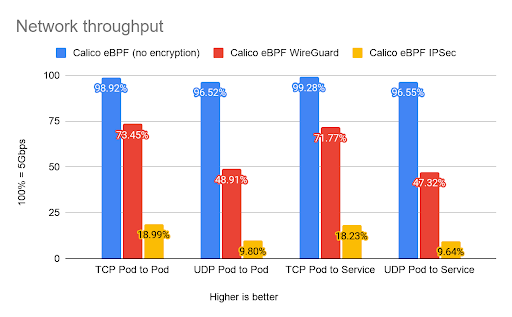
In cryptography, encryption and decryption are the essential building blocks of secure communication. Due to the resource-intensive nature of these procedures, there can be a huge toll on the amount of available resources in a busy cluster. WireGuard was written with a modern approach to cryptography in order to deliver better performance and a softer grip on resources, resulting in more data throughput at higher speed.
The following figure shows an estimate of how much vCPU would be required in order to transmit 10Gbps of data in each scenario.
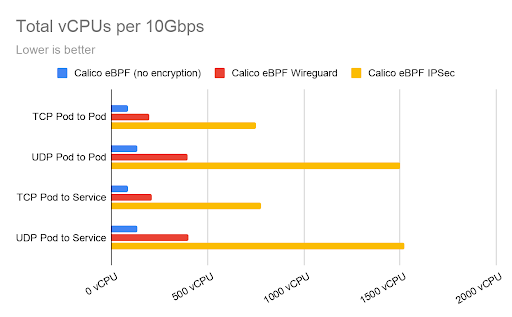
It is worth noting that the performance test was conducted without any tuning, and there are various ways to boost these figures depending on the environment.
Demo
Before we begin
This blog post assumes that you have a running, self-managed K8s cluster named “demo.k8s.local” deployed with kOps version 1.19.1 or higher. If you would like to know more about how to deploy such a cluster, see this article.
WireGuard preparation
Note: If you are using a different kOps cluster name, please replace the name (demo.k8s.local) with your cluster’s name before executing these commands.
Execute the following command to launch the editor:
kops edit cluster demo.k8s.local
Add the following line under the Calico parameters in the networking section:
wireguardEnabled: true
Configuration should look similar to this:
networking: calico: awsSrcDstCheck: Disable bpfEnabled: true bpfExternalServiceMode: DSR encapsulationMode: vxlan wireguardEnabled: true
Save the configuration and exit the editor.
Updating the cluster
kOps uses a `state store` approach in order to save cluster configurations. From the moment a self-managed cluster is created, all configurations and manifests are stored in a specific location (AWS S3 bucket in this instance). It is worth noting that kOps requires you to apply configuration in order to create or make changes.
Apply the configuration change by executing this command:
kops update cluster demo.k8s.local --yes
That’s it, node-to-node traffic is now encrypted.
Verify
In order to run WireGuard, Calico injects a `WireguardPublicKey` into the node manifest; this public key is then used by WireGuard to establish secure tunnels.
It is possible to query this value in order to determine if WireGuard is successfully configured in your cluster.
To do so, execute the following command:
kubectl get nodes -o yaml | grep -i WireguardPublicKey
You should see a result similar to:
projectcalico.org/WireguardPublicKey: 5p8afGSOO6y3h+ztrmJe2gzyvh414YVL+WwD/JvKi3k=
f:projectcalico.org/WireguardPublicKey: {}
projectcalico.org/WireguardPublicKey: p3cyWzMurgMB86usdvGh9mVUFMrU+DErt4eYTHoIaz8=
f:projectcalico.org/WireguardPublicKey: {}
projectcalico.org/WireguardPublicKey: OppRgoRrLo8QJOULrR3gVPGEqFuU7vNPNMKEaxhbS0Q=
f:projectcalico.org/WireguardPublicKey: {}
Conclusion
As we have established in this blog post, Calico offers an effortless way to set up secure communication in a K8s cluster, using open-source WireGuard. This latest kOps release provides an effortless install path, while providing an incredibly powerful and compelling feature for your K8s cluster: networking that is lightweight, low maintenance, highly performant, and secure.
Did you know you can become a certified Calico operator? Learn Kubernetes networking and security fundamentals using Calico in this free, self-paced certification course.
If you enjoyed this blog then you might also like:
- Calico community meeting: Demonstration of WireGuard encryption
- In-cluster encryption documentation
- Getting started with Calico network policy
- Free, online webinars, workshops, and resources
- Learn about Calico Cloud
- WireGuard technical whitepaper
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!


