A couple of days ago, I was checking my Twitter feed and saw a tweet from someone saying how frustrated he was that DockerHub (a renowned container registry) was down. Someone else replied to the tweet, recommending the tweet’s author to check out Google’s repository, where they have DockerHub mirrors in Google Cloud.
My first reaction was “Nice! How clever of this person (or Google) to have thought of this idea.” My next thought was, wait. This could lead to potential security risks for some developers who are not familiar with how these registries are updated and what images go into these mirrored sites. Imagine when application developers are busy scrambling to check-in their latest update to the CI/CD pipeline of the software they are building, and in that time crunch, their go-to container registry is down. Do developers really have the time to check if there are vulnerable images in every registry they use? Will there be an easy, streamlined way to automatically scan the images no matter which registry developers use to pull their images? The short answer is yes, and we will look into that in this blog.
Scan all your container assets with Calico Cloud
I recently presented a webinar on Calico Cloud’s latest Image Assurance feature, which can scan container images for vulnerabilities. In this webinar, I discussed the various types of threats that application developers and security teams face, and even provided examples of how this software pipeline stage has opened up a new array of vulnerabilities. Hackers and bad actors thrive when something like the DockerHub incident happens, because they know how humans tend to oversee miniscule details when pressed for time.
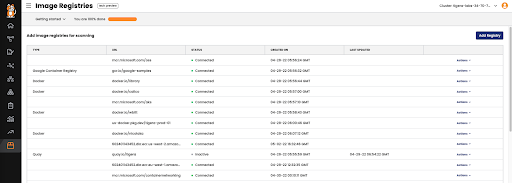
Fig 1: Scanning image registries
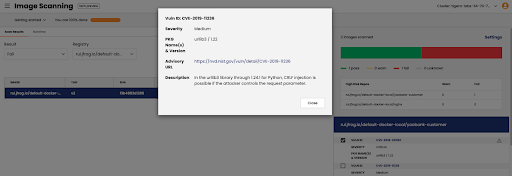
Calico Cloud with Image Assurance will automatically add and scan all the registries in your environment and present a detailed scan result with fields such as CVE ids, risk levels, versions, and so on. You can also manually add registries and create exceptions as part of the admission controller policy, wherein you could still use a “failed” image for your application if you know that it will not break critical software components or you’re just using it in a test environment.
Fig 2: Scan result with CVE ID and description
Is that all I need to worry about?
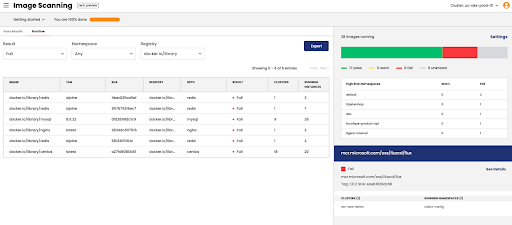
If you want to watch your applications get hacked, then yes. We recommend looking beyond static analysis and looking at runtime threats in your containers and applications. Calico also provides a runtime view of workloads and clusters with vulnerable images (see figure 1). To stop an intruder from getting into your home, do you just lock the front door of the house or do you lock every entry point, and for complete security, have a security system with motion detection and cameras to visually inspect the house? That’s what runtime security provides—Calico looks for anomalies and zero-day threats during runtime with ML-based detection and alerts users for unusual activity, even at the namespace level. Once you are alerted of a possible malware or data exfiltration threat, you can mitigate them by utilizing custom rule sets or Calico-recommended rules.
Fig 3: Runtime view of Calico Image Assurance
What about business productivity?
Before you start thinking you have all the answers to your security questions for containerized applications, let me explain how Calico mitigates these security threats. A typical flow of events after a security incident has been reported involves communicating with the application development teams about the vulnerabilities detected and when fixes need to go in. This can be a frustrating time for developers as they are still working on the next set of features and releases. But fear not! Calico customers have been successful with systematically planning their way around these fixes. You can isolate affected components of the microservice with granular security policies while the security teams wait for the patches to arrive. This process can be part of your organization’s zero-trust model, where you effectively reduce your attack surface and still secure your existing workloads from external and internal attacks.
Can I try it before I buy it?
Yes. Calico Cloud has a free trial. You can sign up with any valid email address and even connect your existing clusters on major Kubernetes distros to run tests.
Want to learn more? Read our container security scanning guide.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!