Cloud-native transformations come with many security and troubleshooting challenges. Real-time intrusion detection and the prevention of continuously evolving threats is challenging for cloud-native applications in Kubernetes. Due to the ephemeral nature of pods, it is difficult to determine source or destination endpoints and limit their blast radius.
Traditional perimeter-based firewalls are not ideal fit for Kubernetes and containers. Firewalls have traditionally been used to block attacks at the perimeter, but if the perimeter is breached, there’s no protection from within the cluster. The dynamic nature of Kubernetes requires a specialized approach to intrusion detection and prevention for containers, Kubernetes, and cloud.
Intrusion detection and prevention methods
Threat intelligence feeds, which record and track the IP addresses of known bad actors, are a critical part of modern cloud-native security. Calico Cloud now provides threat intelligence feeds, such as AlienVault, as part of its default security policies. This means that traffic to suspicious IPs is blocked from day one without the need for any extra configuration. Additionally, an anomaly detection dashboard in Calico’s UI shows full context, including which pod(s) was involved so you can analyze and remediate.
Another advanced method for intrusion detection and prevention introduced in Calico Cloud is deep packet inspection (DPI). DPI inspects, in detail, data being sent over the network and augments the IP-based information with container and Kubernetes-native information to provide real-time intrusion detection and prevention.
Security teams can quickly run DPI in response to unusual network traffic in clusters in order to identify potential threats. DPI can also be used on select workloads to efficiently make use of cluster resources and minimize the impact of false positives.
Calico Cloud provides an easy way to perform DPI using Snort community rules. You can disable DPI at any time, selectively configure for namespaces and endpoints, and view alerts in the alerts dashboard in Calico’s Manager UI.
Let’s take a closer look at how DPI and threat intelligence feeds work with Calico!
Threat intelligence feed
Firewalls often detect and block traffic associated with known bad actors, but don’t have granular visibility into which pod is infected. Calico’s threat feed can pinpoint and report on the exact source of malicious traffic.
How does it work?
Calico Cloud ingests threat feeds that identify IP addresses for known bad actors, such as botnets. Any traffic to those IPs is automatically blocked and generates an alert.
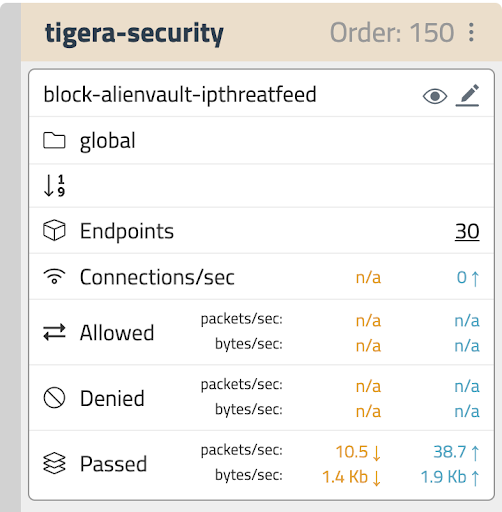
Once you connect a cluster to Calico, all of the workloads in that cluster will be protected with a block-alienvault-ipthreatfeed security policy, which is enabled to block egress and ingress traffic.
Deployment
Calico’s threat feed deployment consists of 3 main components: a threat feed resource, a network set resource, and a global network policy.
First is the threat feed resource, which pulls updates automatically on a daily basis. The threat feed(s) must be available using HTTP(S), and return a newline-separated list of IP addresses or prefixes in CIDR notation.
apiVersion: projectcalico.org/v3 kind: GlobalThreatFeed metadata: name: feodo-tracker spec: content: IPSet pull: http: url: http://feodotracker.abuse.ch/downloads/ipblocklist.txt
Second is a network set resource (NetworkSet). It represents an arbitrary set of IP subnetworks/CIDRs, and gets updated periodically by the threat feeds.
The metadata for the network set includes a set of labels. These labels are used to create the network policy to block the traffic.
The third and last component is the global network policy. It blocks traffic to any of the suspicious IPs. Notice that the suspicious IPs are not defined in the network policy manifest; instead, Calico uses a selector (feed == "otx-ipthreatfeed"), which refers to the NetworkSet.
apiVersion: projectcalico.org/v3
kind: GlobalNetworkPolicy
metadata:
name: tigera-security.block-alienvault-ipthreatfeed
spec:
tier: tigera-security
selector: all()
namespaceSelector: ''
serviceAccountSelector: ''
egress:
- action: Deny
source: {}
destination:
selector: feed == "otx-ipthreatfeed"
- action: Pass
source: {}
destination: {}
types:
- Egress
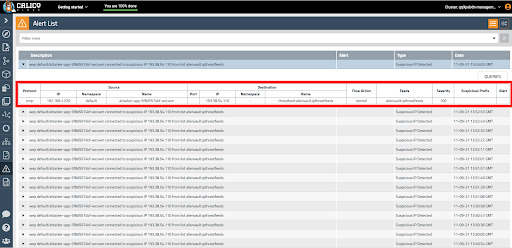
When communication to any suspicious IPs are detected, traffic is blocked and an alert is triggered in the UI. The alert shows the full context, including which pod(s) were involved, so you can analyze and remediate.
Deep packet inspection
Calico Cloud provides DPI as a Kubernetes custom resource. For each DPI resource (DeepPacketInspection), Calico creates a live traffic flow monitor that inspects the header and payload information of packets that match the Snort community rules. An alert is automatically added to the Alerts page in the Calico Cloud Manager whenever malicious activities are suspected.
How does it work?
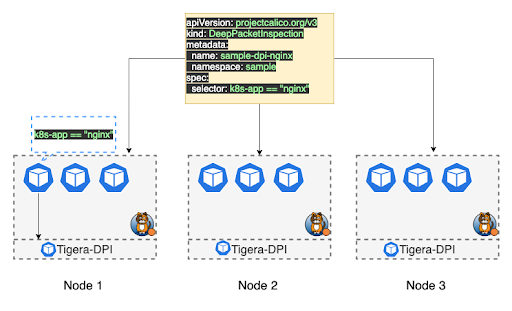
Once you apply a DeepPacketInspection resource, a daemonset gets created, and the DPI pod is deployed on each node. For each workload endpoint that matches the selector in DeepPacketInspection custom resource, a Snort process is started to monitor its interface.
Deployment
The following is an example showing how to use DPI in your deployment:
1. Create a YAML file containing one or more DeepPacketInspection resources.
2. Select a single workload that has the label k8s-app with the value nginx.
apiVersion: projectcalico.org/v3 kind: DeepPacketInspection metadata: name: sample-dpi-nginx namespace: sample spec: selector: k8s-app == "nginx"
3. Apply the YAML file.
kubectl apply -f <your_deep_packet_inspection_filename>
4. Trigger a Snort rule from attacker pod to nginx.sample.
In this example, the attacker pod is in the default namespace and has the label app=attacker-app. The target is nginx pod in the sample namespace.
kubectl exec -it $(kubectl get po -l app=attacker-app -ojsonpath='{.items[0].metadata.name}') -- sh -c "curl http://nginx.sample.svc.cluster.local:80 -H 'User-Agent: Mozilla/4.0' -XPOST --data-raw 'smk=1234'"
5. Access alerts.
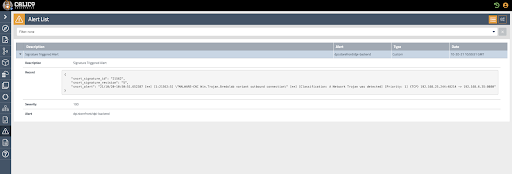
The alerts generated by DPI are available in the Calico Manager UI on the Alerts page. In the alert, you can see the Snort signature ID, signature description, source IP/port, and destination IP/port.
Summary
Threat intelligence feeds and deep packet inspection are critical tools that will help you to respond to and remediate different types of threats quickly and efficiently. With Calico Cloud, you have a feature-rich intrusion detection and prevention solution that is purpose-built for containers, Kubernetes, and cloud. Now you can pinpoint the source of malicious activity, use machine learning to identify anomalies, and create a security moat around critical workloads.
Ready to try threat intelligence feeds & deep packet inspection for yourself? Get started with a free Calico Cloud trial.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!