Secure Application Connectivity for the Cloud Native World
Today, I’m really excited to share with you details of Tigera Secure Enterprise Edition, the first cloud native enterprise solution for secure application connectivity.
Tigera was founded with the idea of improving secure application connectivity for a cloud native world combined with a drive to overcome the complexity inherent in existing approaches to application connectivity. As enterprises have started to invest in new cloud native application architectures by leveraging microservices, containers, orchestration tools like Kubernetes and elastic cloud infrastructure, it has become evident to them that infrastructure designed for the legacy virtual machine (VM) world isn’t able to meet the needs of these next generation applications. Customers and advisors consistently commented to the Tigera team that “application connectivity using SDNs is too complex and cumbersome”, “security is painful” and “overlay network-focused approaches don’t work and are hard to troubleshoot”. We have been diligently working to overcome those (and other) challenges and are very proud of the progress demonstrated with today’s announcement.
Retrofitting infrastructure or VM-focused solutions for a Kubernetes world results in complexity, instability, inconsistent security, and a mismatch between technology and existing organizational responsibilities
Cloud native application deployment is a tidal wave that puts new demands on application connectivity and security. Retrofitting infrastructure or VM-focused solutions for a Kubernetes world results in complexity, instability, inconsistent security, and a mismatch between technology and existing organizational responsibilities (Dev, Networking, Security). We are seeing new pain points emerge in the enterprise:
- Legacy security models don’t work with modern applications Given the explosion in the number of moving parts inside a cloud native application (can you say “microservices”?), legacy strategies like perimeter security, static firewall rules, and network locality models like micro-segmentation are inadequate and can leave security holes, particularly in a containerized world. Conventional security mechanisms originally designed for the virtual machine generation fall short. The underlying network, workloads and the rest of the infrastructure have to be assumed to be potentially compromised and untrustworthy; every container needs to be protected from the network and every host has to be protected from containers running on it. Given that the containers themselves are very dynamic with a short lifespan, approaches have to be dynamic and enable changes to security policies that instantly ripple through a system. Every device, user and network flow must be authenticated and authorized. All data flowing between microservices has to be encrypted. Policies must be dynamic and calculated from as many sources of data as possible
- Difficulties supporting multi-cloud and legacy environments — Most enterprises are seeking to leverage a combination of resources in their private data center, a private cloud running on OpenStack, and public cloud resources from multiple different vendors to prevent cloud vendor lock-in. Site Reliability Engineers (SREs) and DevOps engineers tasked with rolling out cloud native applications struggle to design networking and security solutions that work across these different platforms. Given that the modern applications running in containers have to co-exist with legacy applications on VMs and bare metal servers, DevOps teams are looking for a single solution that can run across all three environments.
- Mismatches between organizational requirements and technology capabilities — When introducing a cloud native application into an enterprise, a cloud architect faces the unique challenge of working with an organizational structure that was designed by functions (Dev, Networking, Security). Each sub-organization demands controls, including those for internal and external compliance. Additionally, the burden of ensuring compliance frequently falls to an SRE.
- Operational complexity — cloud native applications place unique demands on infrastructure that increase the risk of downtime and become a time sink for Site Reliability Engineers (SREs). Using existing middleware (Enterprise Service Bus) and traditional networking solutions (Software Defined Networking) to address application connectivity challenges puts an unsustainable burden on SREs who are tasked with driving high uptime.
Starting with a clean slate, we took a cloud native approach that leveraged the expertise our team has developed working with open source projects including Kubernetes, Calico and Istio
So what is the news? Tigera Secure Enterprise Edition! Tigera Secure Enterprise Edition is a commercial offering that provides secure application connectivity across multi-cloud and legacy environments along with the enterprise control and compliance capabilities required for mission critical deployments. Tigera Secure Enterprise Edition was born in the cloud native world and solves these challenges in a unique way. Starting with a clean slate, we took a cloud native approach that leveraged the expertise our team has developed working with open source projects including Kubernetes, Calico and Istio.
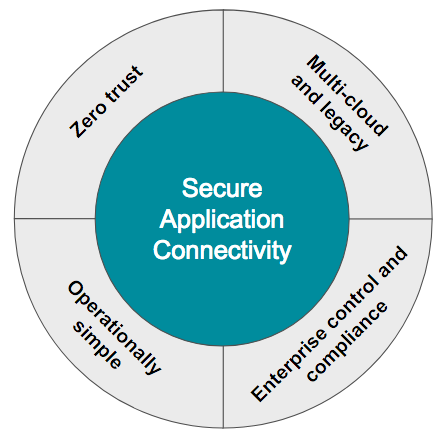
Some of the benefits that Tigera Secure Enterprise Edition delivers include:
- Zero Trust Security:Tigera Secure Enterprise Edition’s unique ZT-Auth™ technology enables organizations to move towards a Zero Trust approach to application connectivity, with multiple levels of intent-based policy enforcement for authentication, authorization and encryption enabling maximum security — independent of the underlying network infrastructure.
- Multi-cloud and Legacy: Tigera Secure Enterprise Edition is the first secure application connectivity solution designed from the ground-up for cloud native environments, including multi-cloud deployments, while also protecting on-premise legacy applications running on virtual machines and bare metal hosts. Tigera Secure Enterprise Edition also works with various orchestration engines giving enterprises a choice.
- Enterprise Control and Compliance: Tigera Secure Enterprise Edition provides the hierarchical, access-controlled policy controls required to integrate with existing organizational structure and processes to provide each functional team the level of control they seek and meet internal and external compliance requirements.
- Operational Simplicity: Tigera Secure Enterprise Edition turns the complex, opaque SDN model of network virtualization and security on its head.Tigera Secure Enterprise Edition uses a flat IP networking model by leveraging proven kernel routing features for optimal reliability and visibility, with a set of powerful operational tools required for rapid problem diagnosis and resolution.
If you are building modern applications with microservices, containers, Kubernetes and elastic cloud infrastructure, you should explore why some of the largest cloud players in the market have chosen Tigera Secure Enterprise Edition. Check out the datasheet, sign up for a demo, or email us at [email protected] to learn more.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!