
Organizations require different types of reports to prove compliance. Notable ones include:
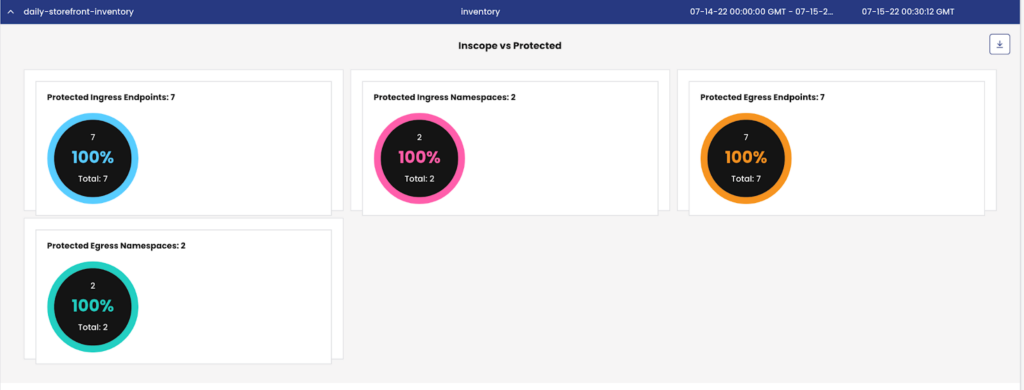
Inventory Report
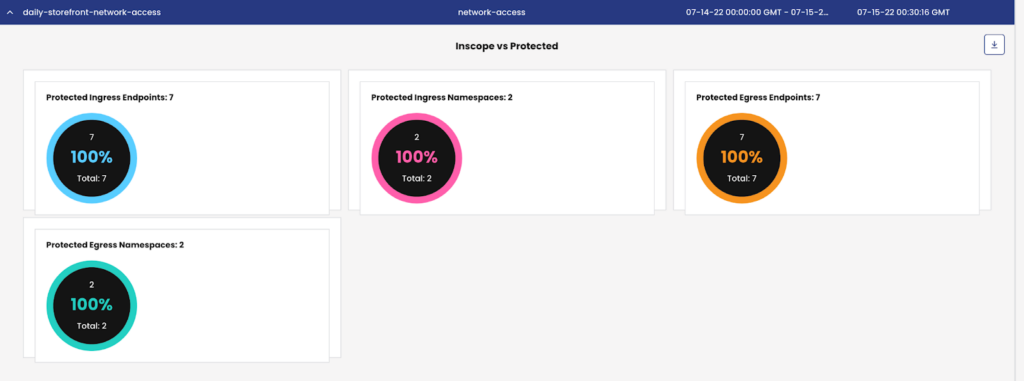
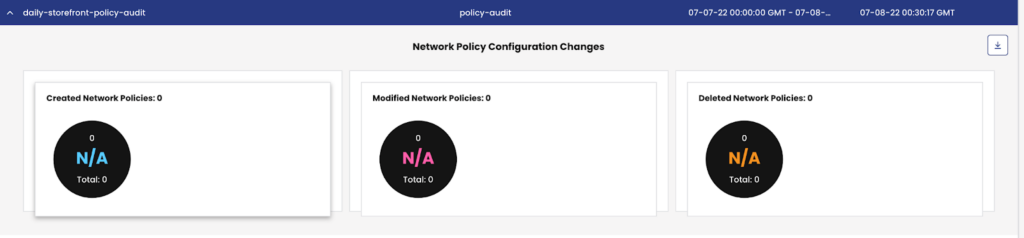
Network Audit
Security Policy Controls
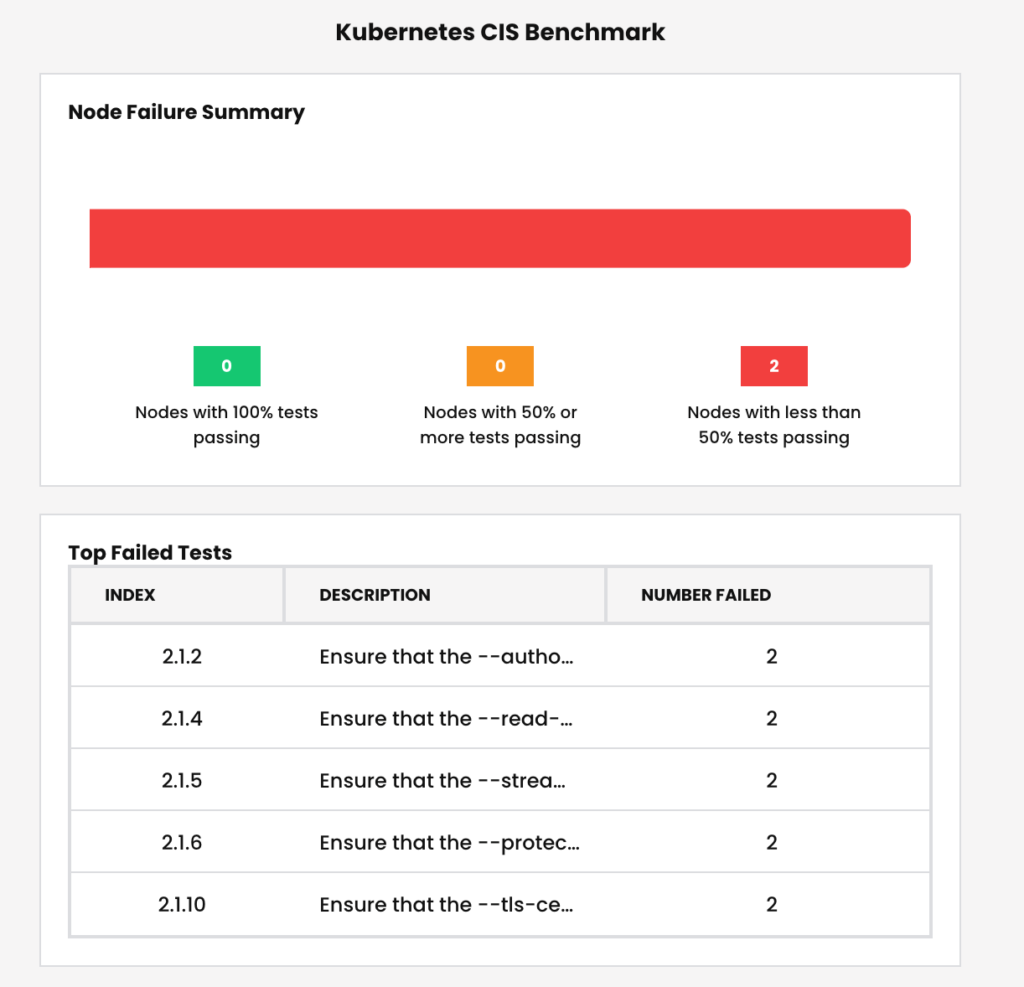
Standardized Benchmark Reports
Attend a live, hands-on, instructor-led workshop
Learn how to address security challenges for containers and Kubernetes—all at your own pace
Attend a webinar to learn how to get your Kubernetes environment PCI or SOC 2 compliant
Custom session to get you started on the compliance journey
Copyright © 2024 Tigera, Inc.