
Calico is the most widely used networking and security solution for Kubernetes. In the latest v3.18.0 release, the Calico team has extended its eBPF data plane to offer support for host protection. This brings it into line with the battle-hardened standard Linux data plane. When combined with Calico’s automatic host endpoints feature, this offers a robust way to secure Kubernetes pods and hosts together using a unified policy model.
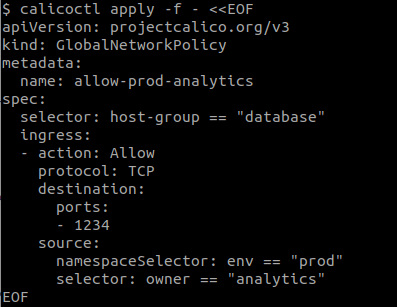
In today’s fast-moving security environment, attacks are automated and it’s important to minimize the blast radius of a compromised workload. A key defense is to adopt a least-privileged model: use security policy to restrict every workload, so that it can access only what it needs. But if your workloads are Kubernetes pods that also need access to external hosts, how exactly do you limit access to a host to only “pods in the prod namespace owned by the analytics team”?
With a traditional IP-and-port firewall, there’s no way to keep up with a shifting set of ephemeral Kubernetes pods — an IP belonging to one pod right now might belong to a different pod in a few seconds’ time. Only a cloud native solution can understand shifting pod identity, labels and selectors in real time. That’s why, a long time ago, the Calico team extended its security policy to cover hosts as well as workloads. By deploying Calico for host protection as well as for pod security, your host protection policy becomes just as dynamic as your workload policy. It matches not a static IP address or CIDR block of addresses, but rather the identity of the workload (carried in its metadata labels).
Calico’s eBPF data plane leverages the Linux kernel’s embedded eBPF virtual machine to implement a more flexible and powerful datapath than is possible with iptables. Extending the eBPF data plane with host protection is part of Calico’s drive to unite the flexibility of the eBPF data plane with the complete feature set of the standard Linux data plane. However, Calico’s goals for the eBPF data plane are not limited to parity!
The eBPF data plane already exceeds the standard Linux data plane in several areas. It has great performance and lower latency for load-balanced traffic (beating kube-proxy even in IPVS mode):
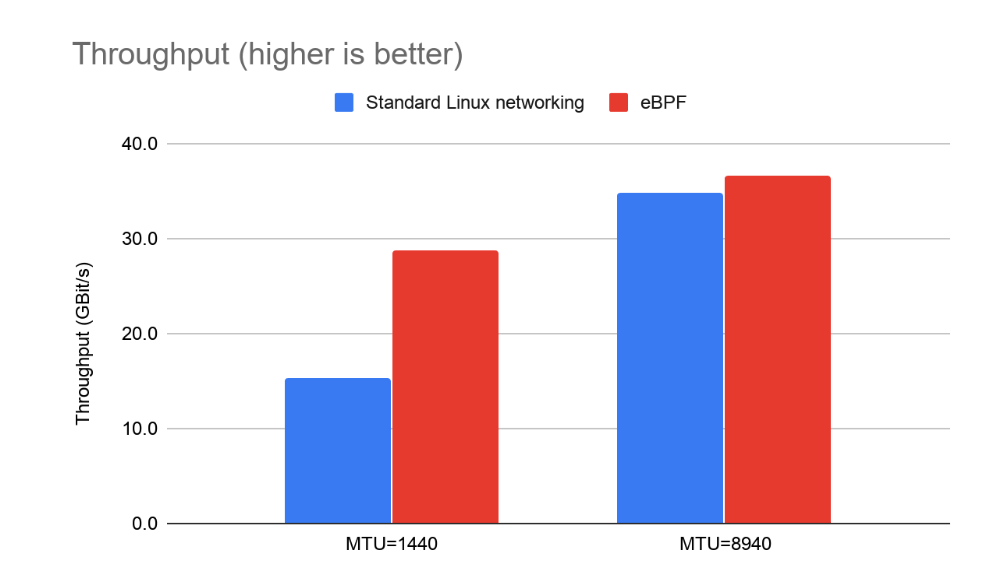
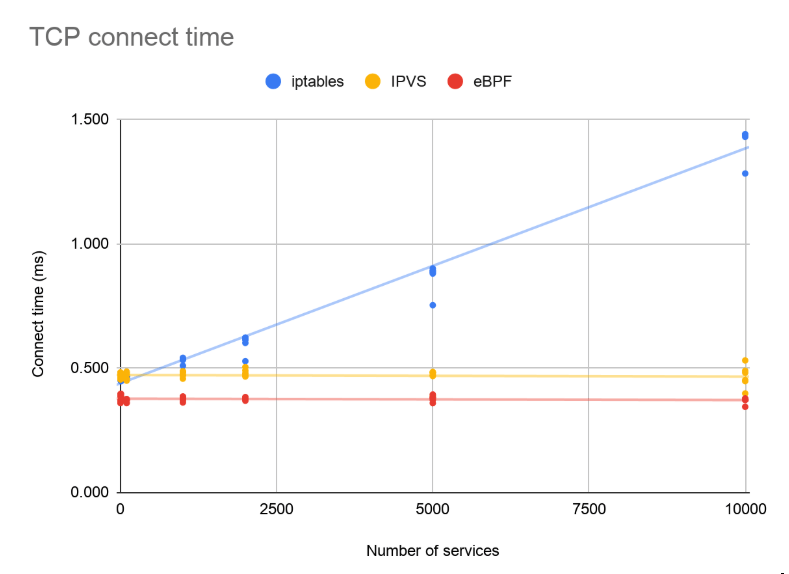
The benefits are not limited to performance; eBPF’s flexibility unlocks some important usability improvements. Previously, it was difficult to identify the source IP of traffic hitting a pod from outside the cluster, leading to challenges in observability and accounting — both of which are important for many workloads in many use cases.
With Calico’s eBPF data plane as a replacement for kube-proxy, the source IP of external connections is preserved:
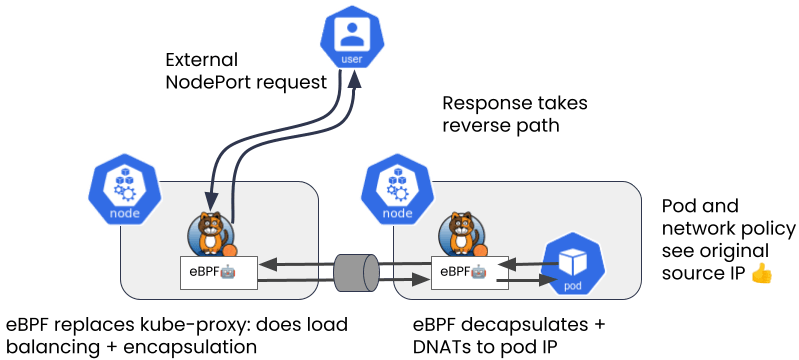
This makes it much easier to write security policy and makes access logs more meaningful.
Finally (for now), if supported by your network, the eBPF data plane allows for “direct server return,” which allows the backing node to respond directly to the external client — reducing latency even further. This kind of feature was simply impossible with the non-eBPF approach and we’re excited to see where we can take the eBPF data plane next.
Did you know you can become a certified Calico operator? Learn Kubernetes networking and security fundamentals using Calico in this free, self-paced certification course.
Tigera, the inventor and maintainer of open-source Project Calico, is the industry leader in Kubernetes security and observability. Tigera’s solutions, Calico Cloud and Calico Enterprise, build on open-source Calico to provide Kubernetes-native security and observability capabilities. To learn more about Tigera’s offerings, visit www.tigera.io.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!