Secure access from individual pods in a Kubernetes cluster to external resources, including cloud services, databases, and 3rd-party APIs with DNS policies and network sets.
Reduce attack surface and mitigate risk with egress access controls, microsegmentation, and security policy recommendations.
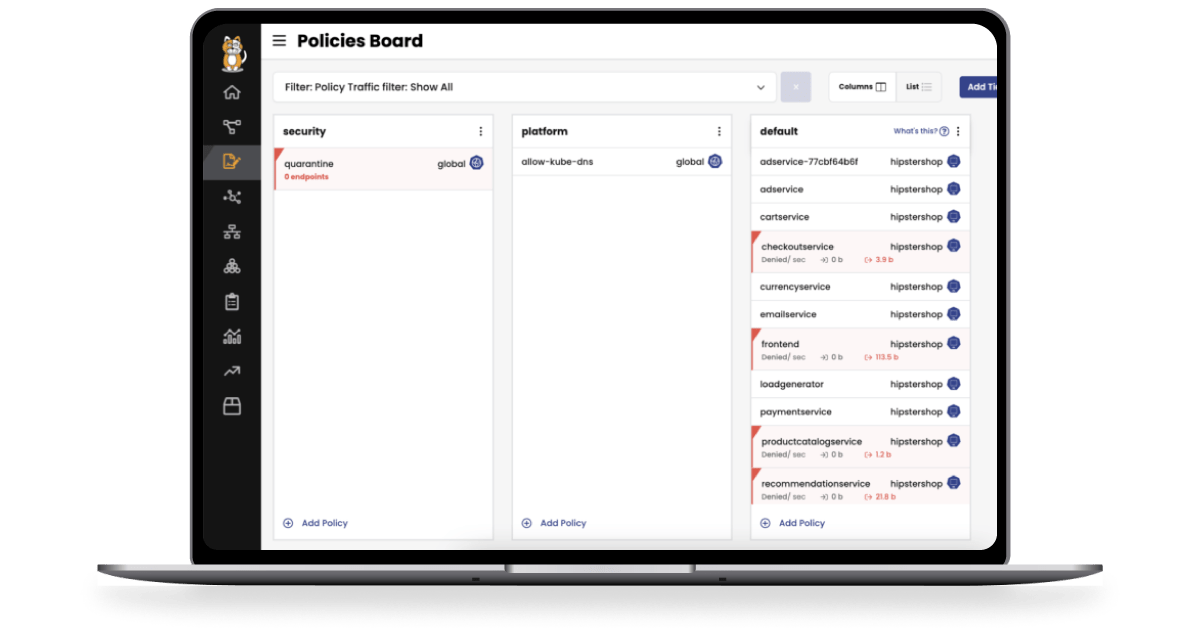
Secure Kubernetes traffic within and outside the cluster to reduce risk, achieve compliance, and actively protect against security threats
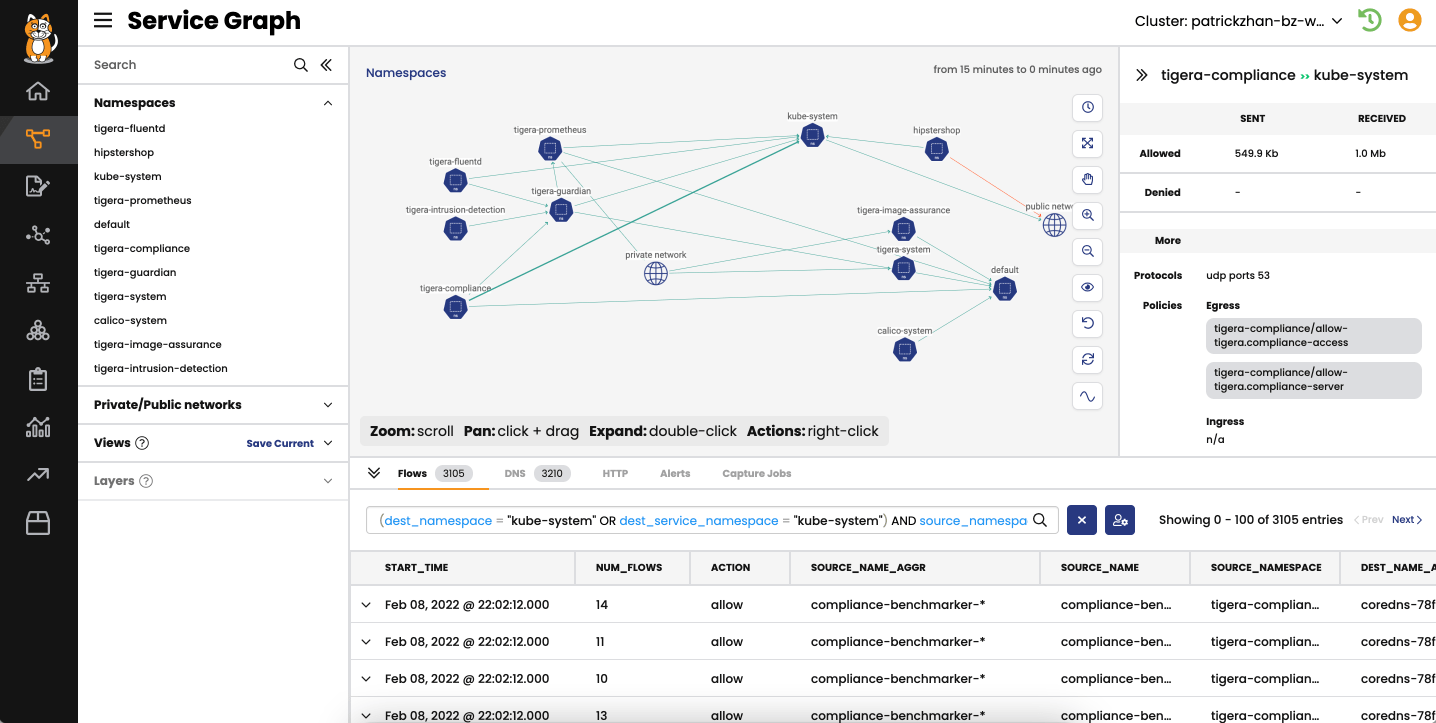
Secure access from individual pods in a Kubernetes cluster to external resources, including cloud services, databases, and 3rd-party APIs with DNS policies and network sets.
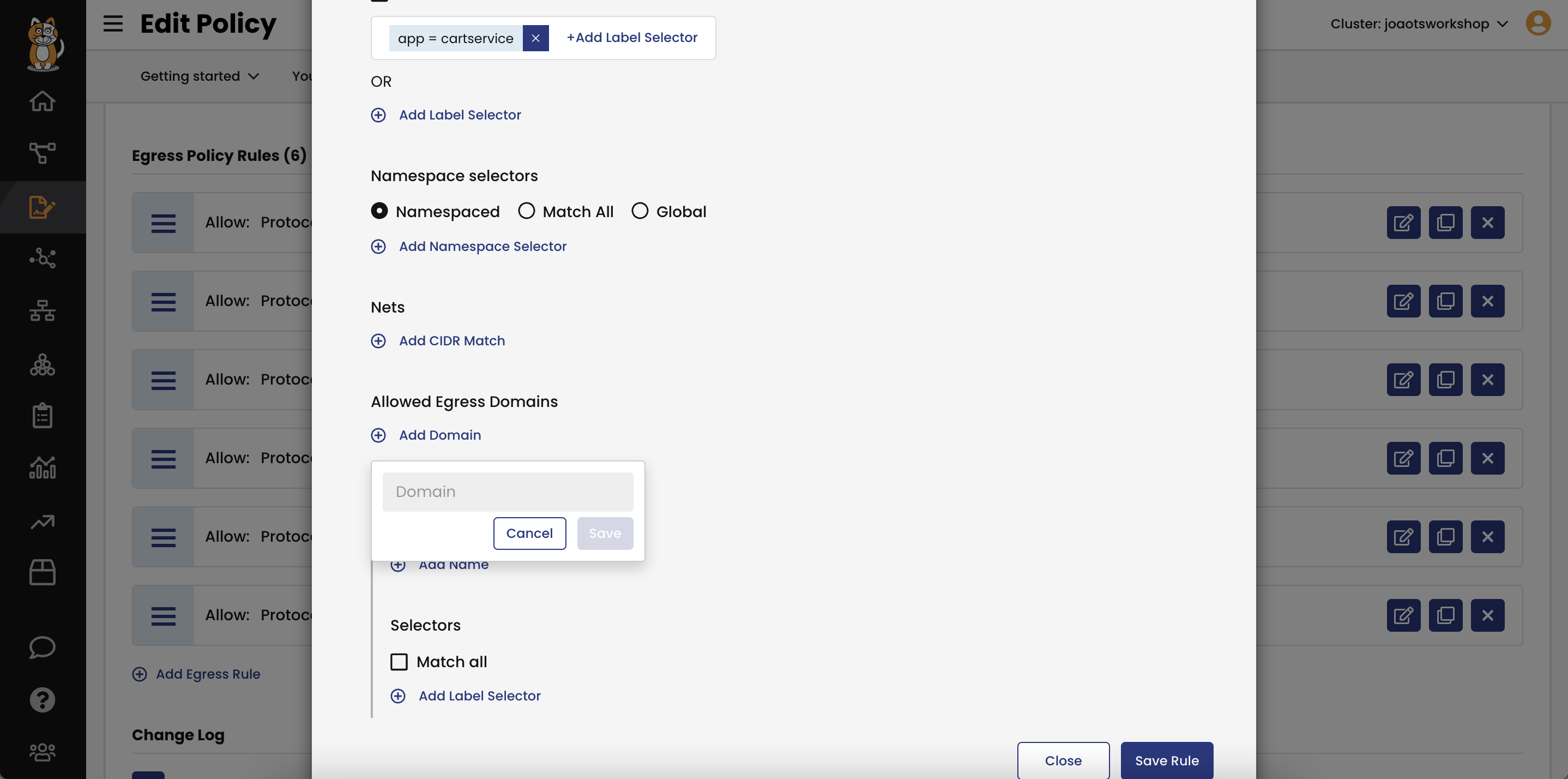
Enforce DNS policies at the source pod so that fully qualified domain names (FQDN/DNS) can be used to allow access from a pod or set of pods (via label selector) to external resources—eliminating the need for a firewall rule or equivalent.
Define DNS endpoints as an exact address (e.g., google.com) or with wildcards (e.g., *.google.com).
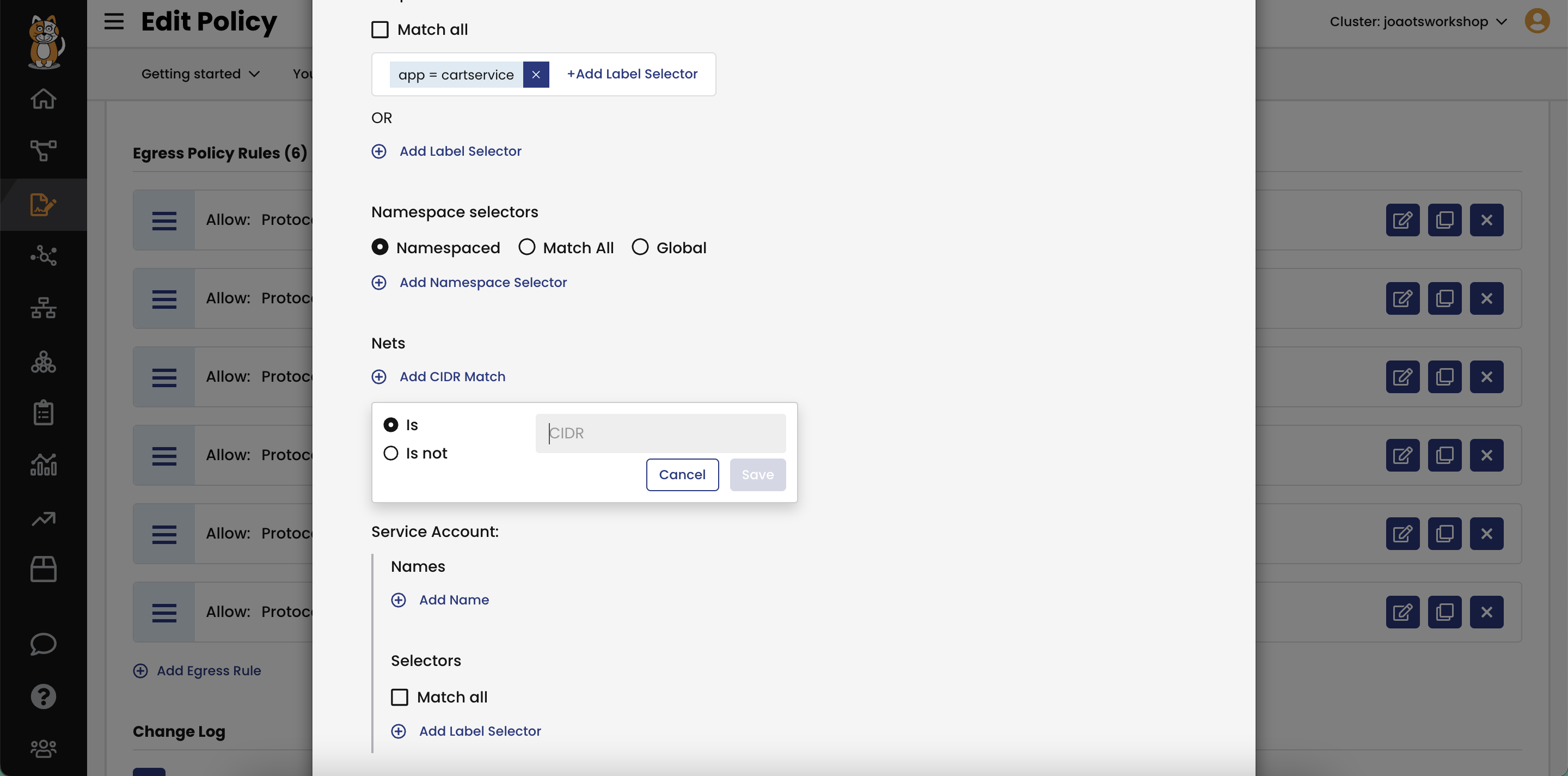
Automatically update access controls for all IPs described by the CIDR notation using IP subnet/CIDR in security policies.
Control incoming or outgoing traffic from external, non-Calico networks with the same policy. Easily scale by using the same set of IPs in multiple policies.
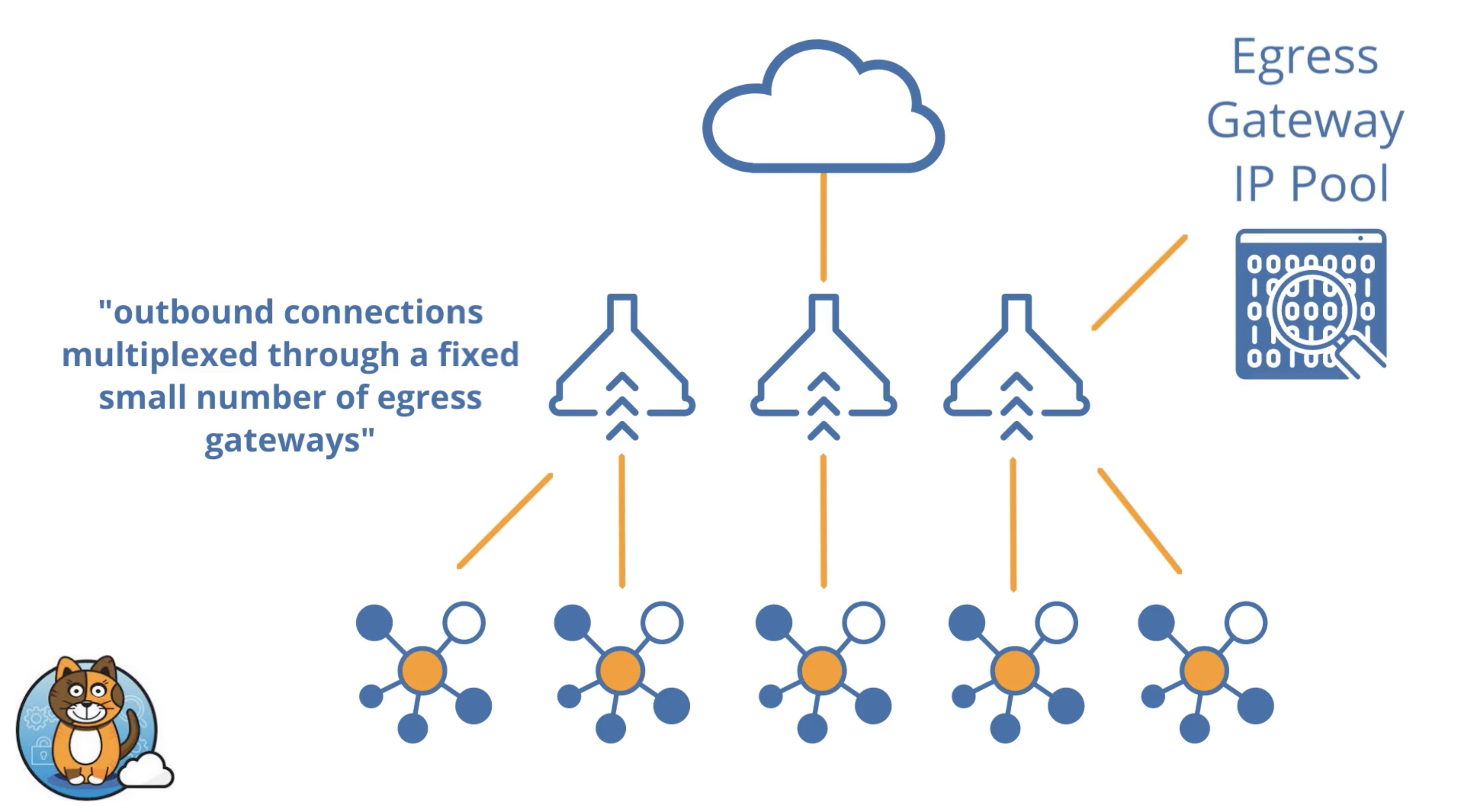
Identify the traffic source at the namespace or pod level from a Kubernetes cluster to communicate to the external resource.
Assign a fixed, routable IP to a Kubernetes namespace to identify workloads running within that namespace.
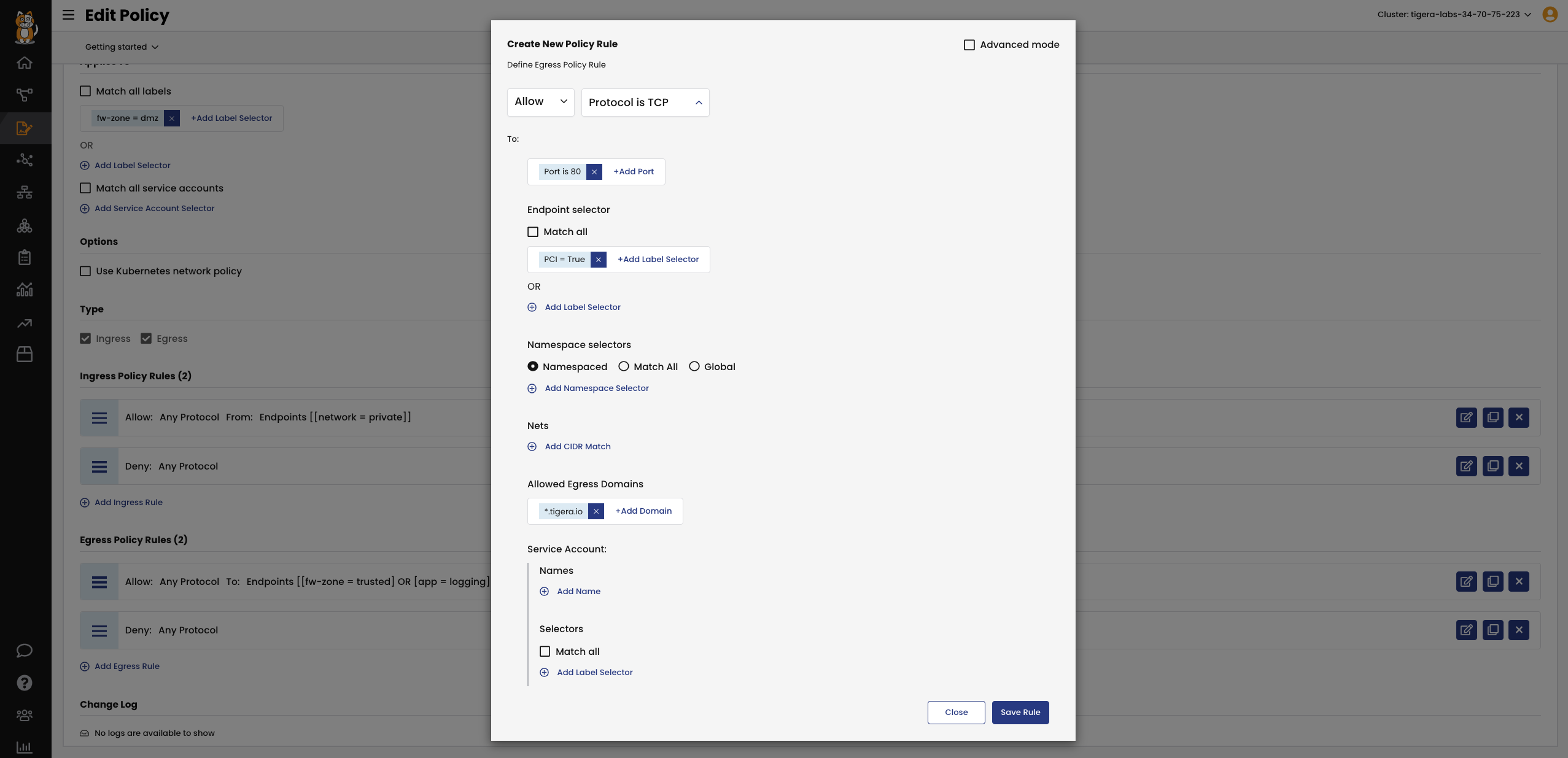
Segment workloads using workload identities to achieve workload isolation and limit lateral communication.
Define security policies as code to enforce consistent segmentation policies across the environment.
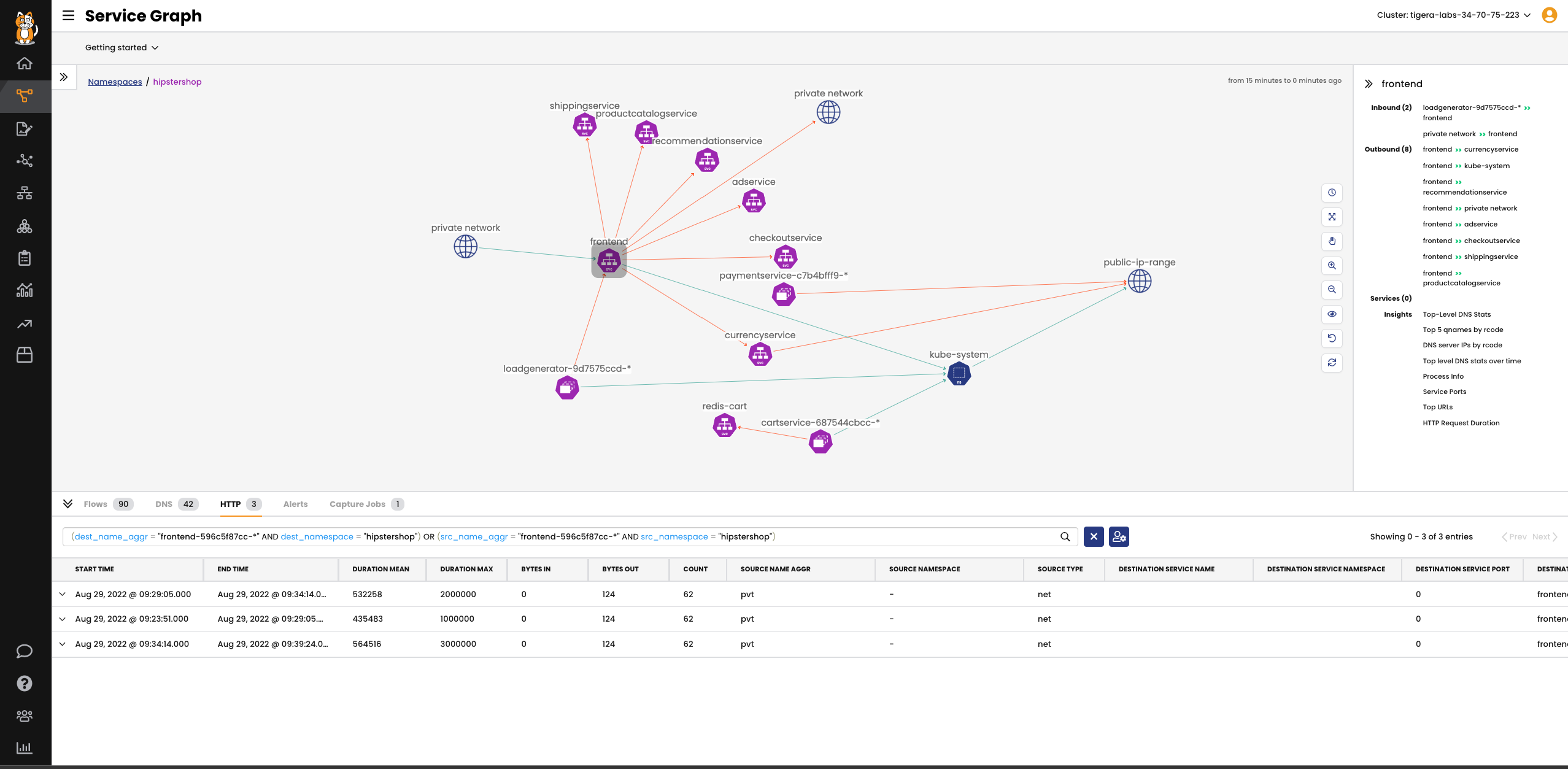
Apply security controls at the application level to secure pod-to-pod traffic, including HTTP methods and URL paths. Eliminate the operational complexity of deploying an additional service mesh.
Gain application-layer visibility into service-to-service communication.
Get started right away on Azure or AWS—every Calico component you need to get up and running is ready to go.
Here’s what our customers are saying about us
Tigera helped Upwork migrate to Kubernetes on Amazon EKS and meet our InfoSec team’s mandate for zero-trust security. We were able to deploy Calico in two weeks and secure our EKS cluster in just six months.

Developer-created resources to help you secure your Kubernetes deployment


Start a free trial or contact us to see Calico in action