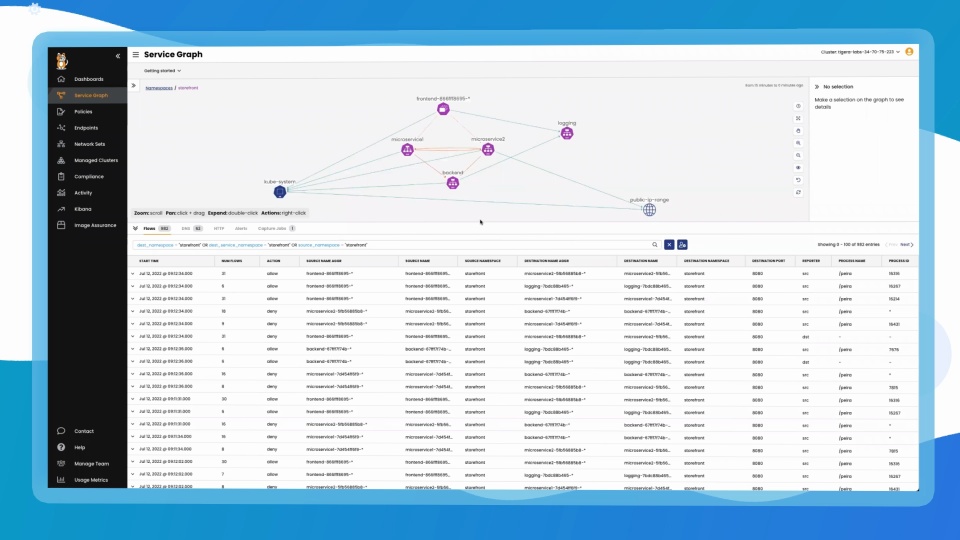
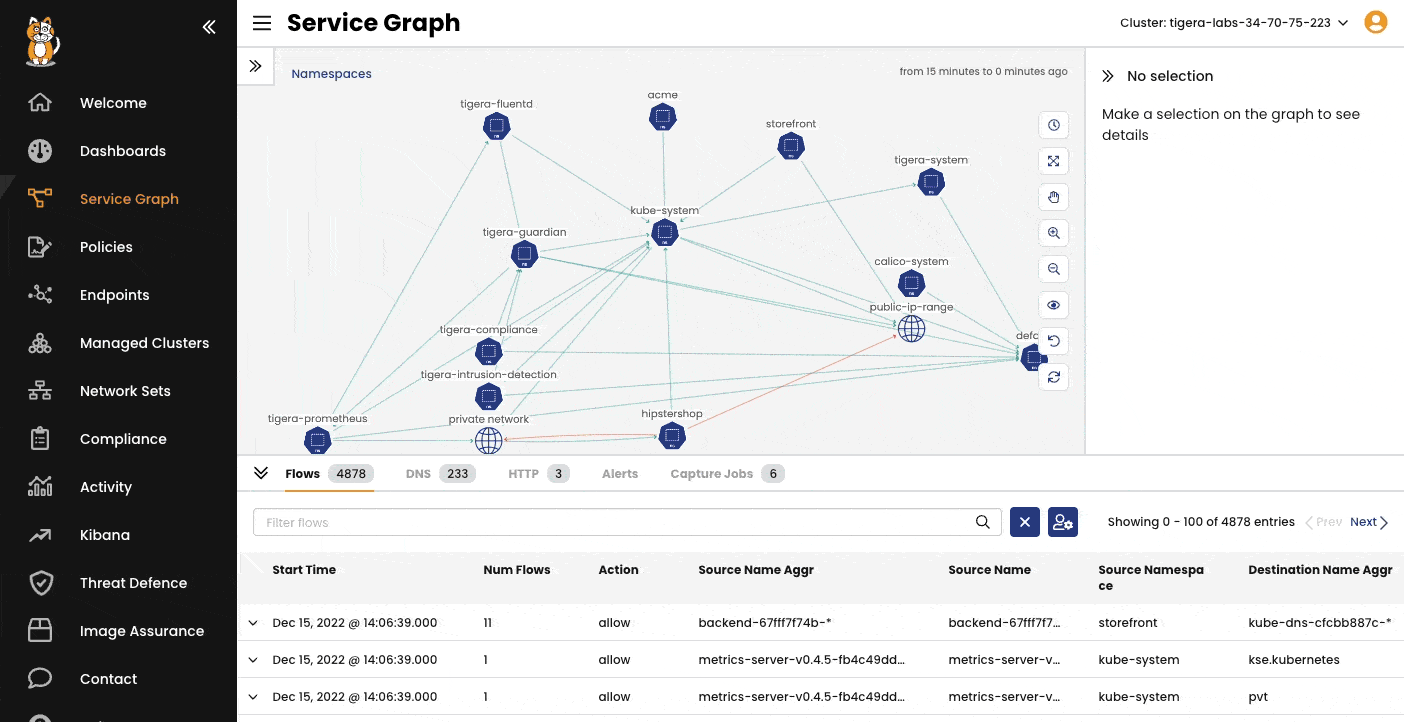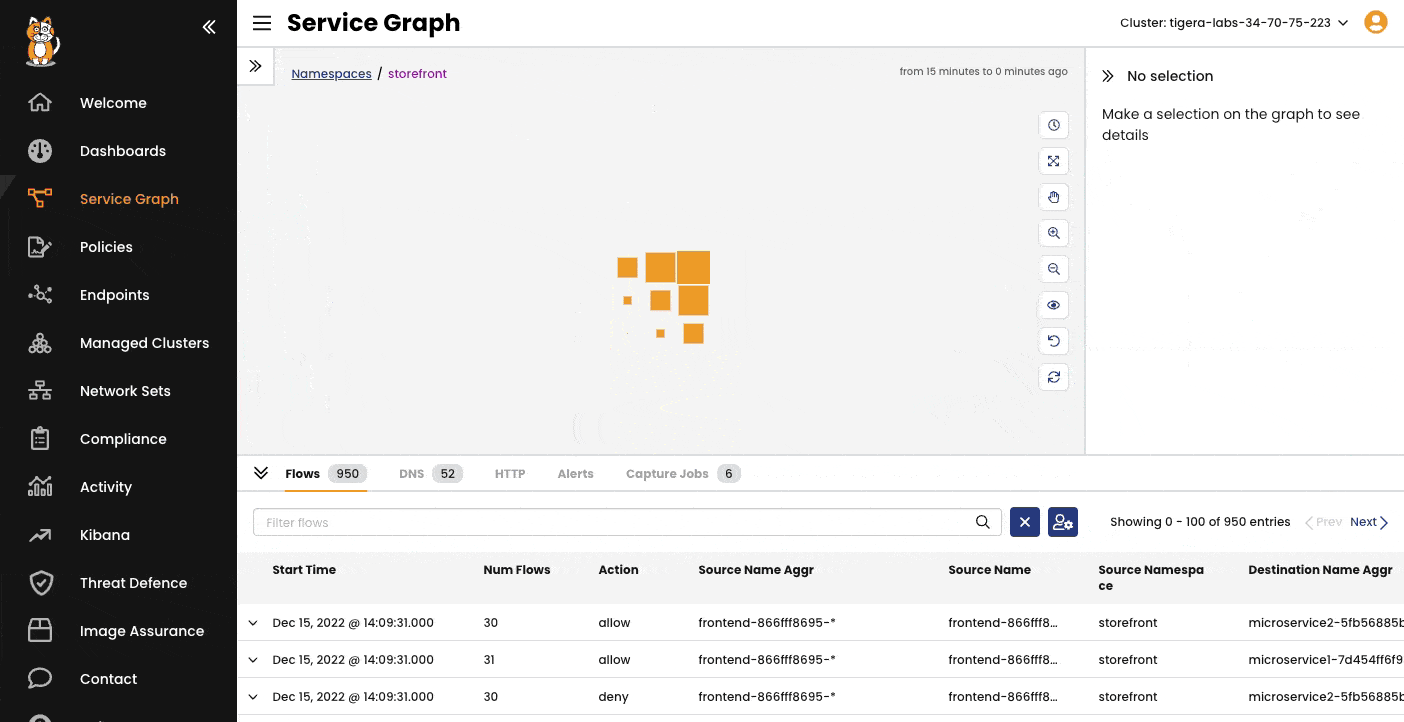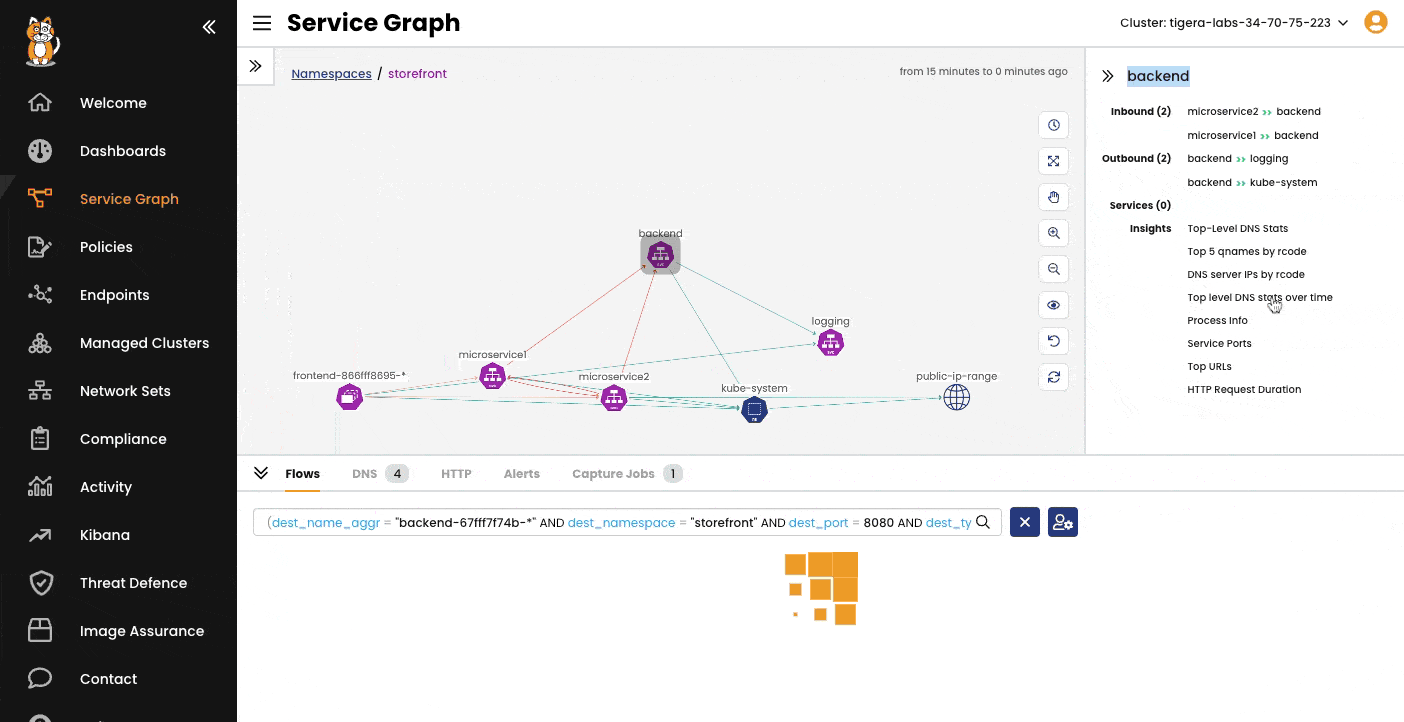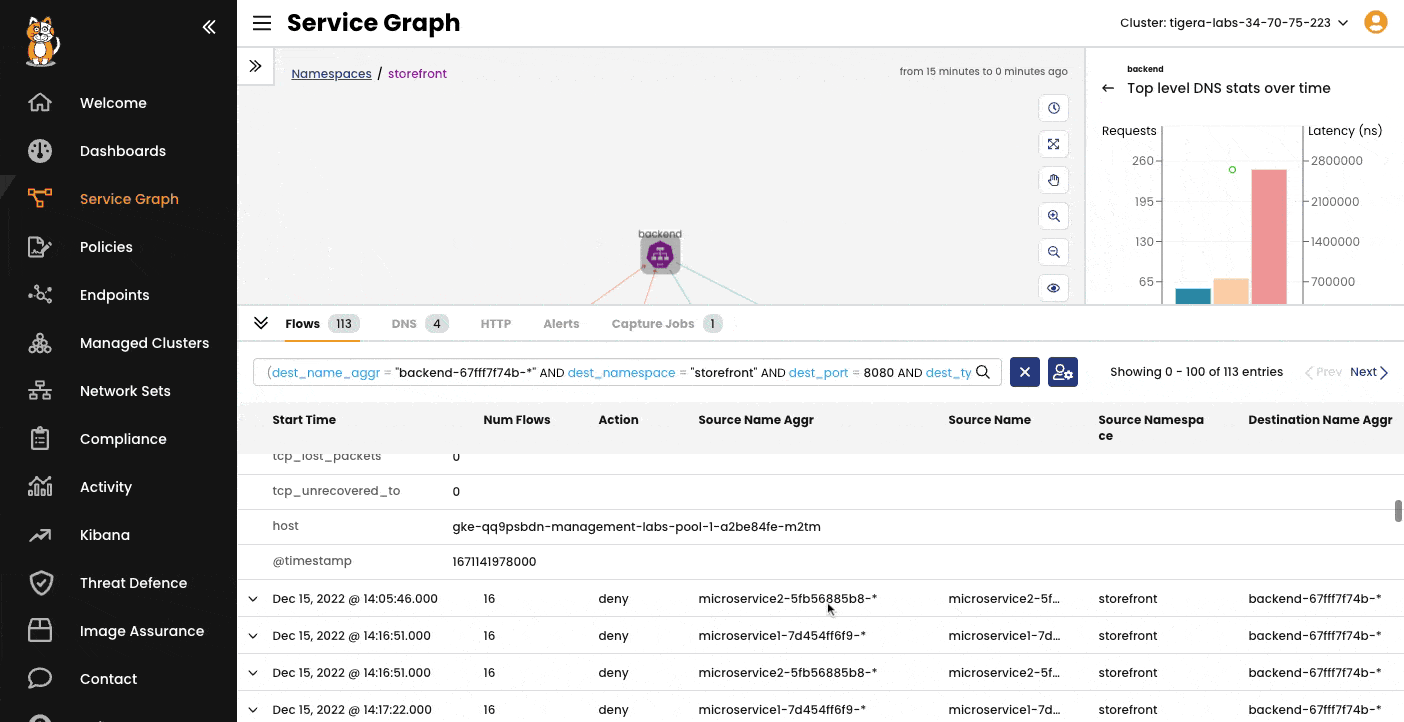
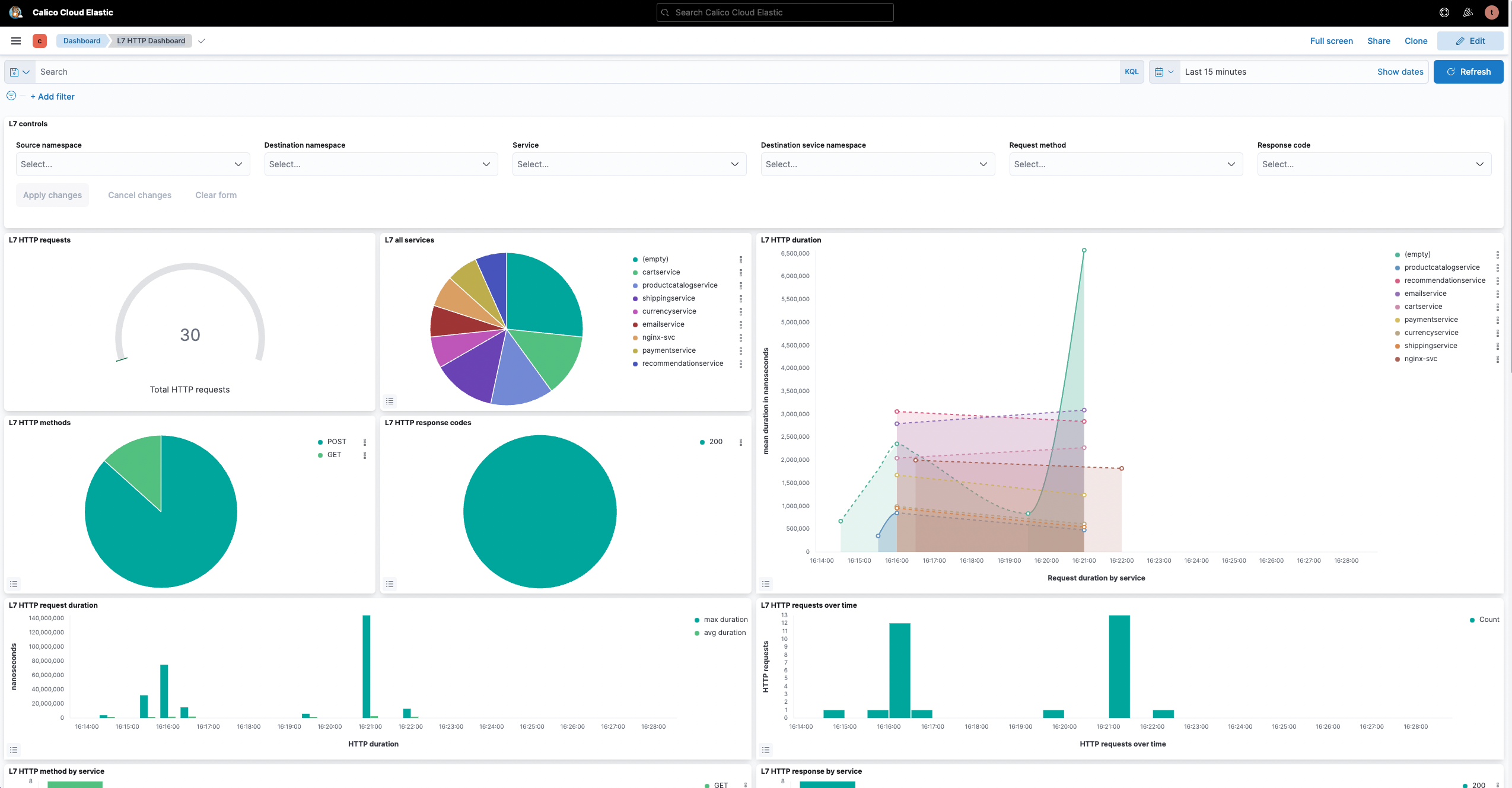
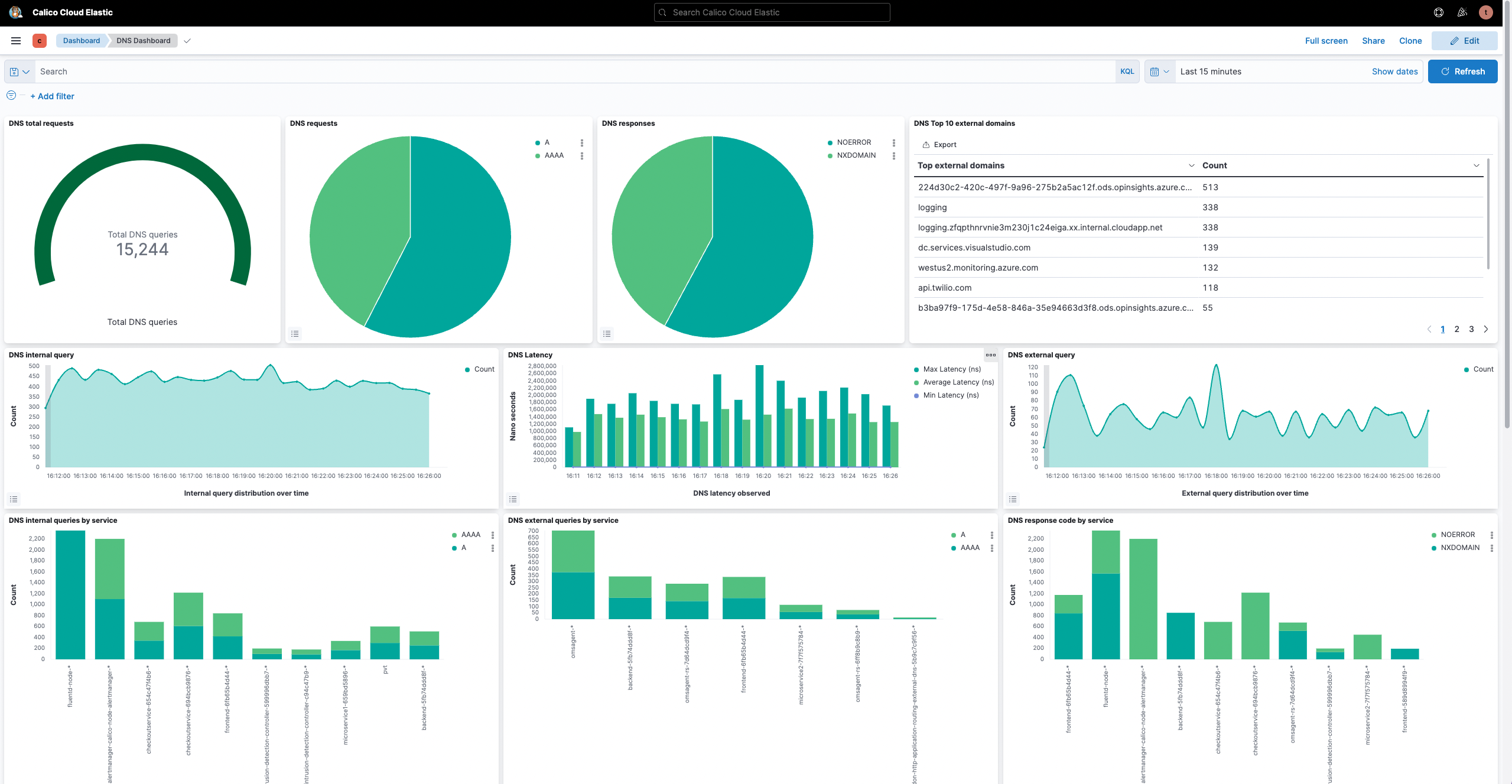
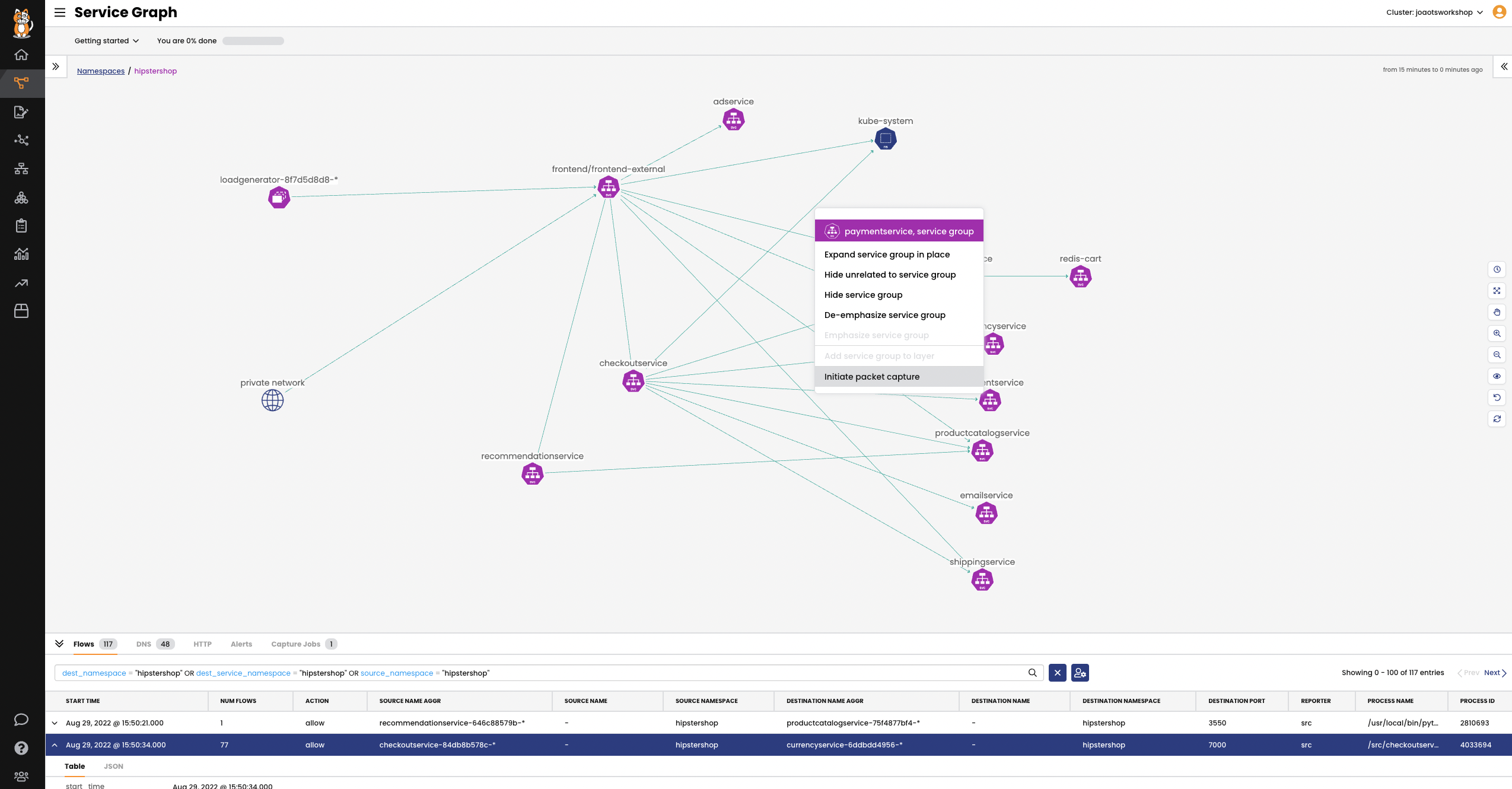
A point-to-point, graph-based visualization of traffic flow and associated workload security policies in the cluster and across namespaces.
Filter resources to understand individual and collective interaction of workloads, save custom views, and share pre-built views. Stage security policy implementation and enforcement on real-time traffic.