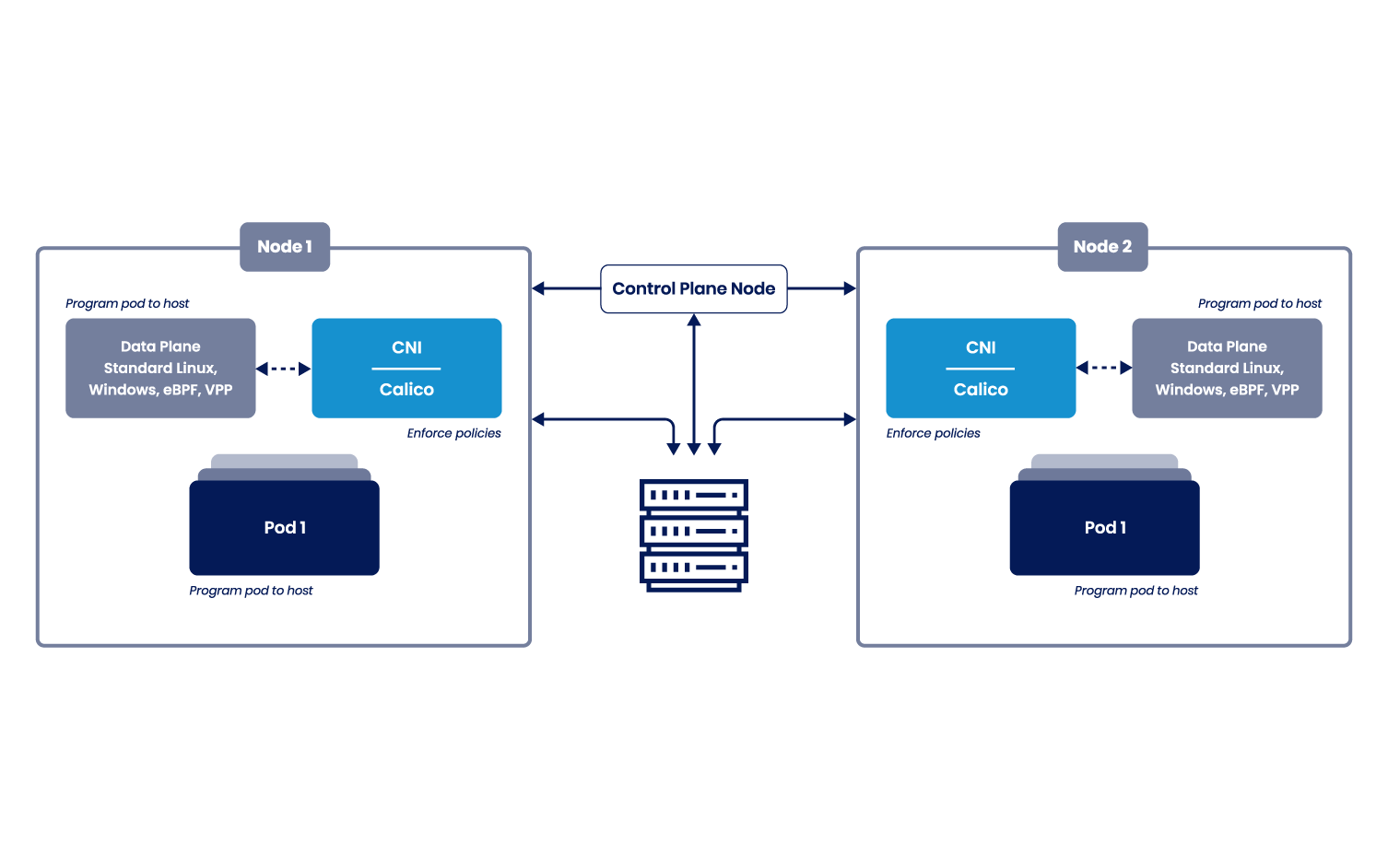
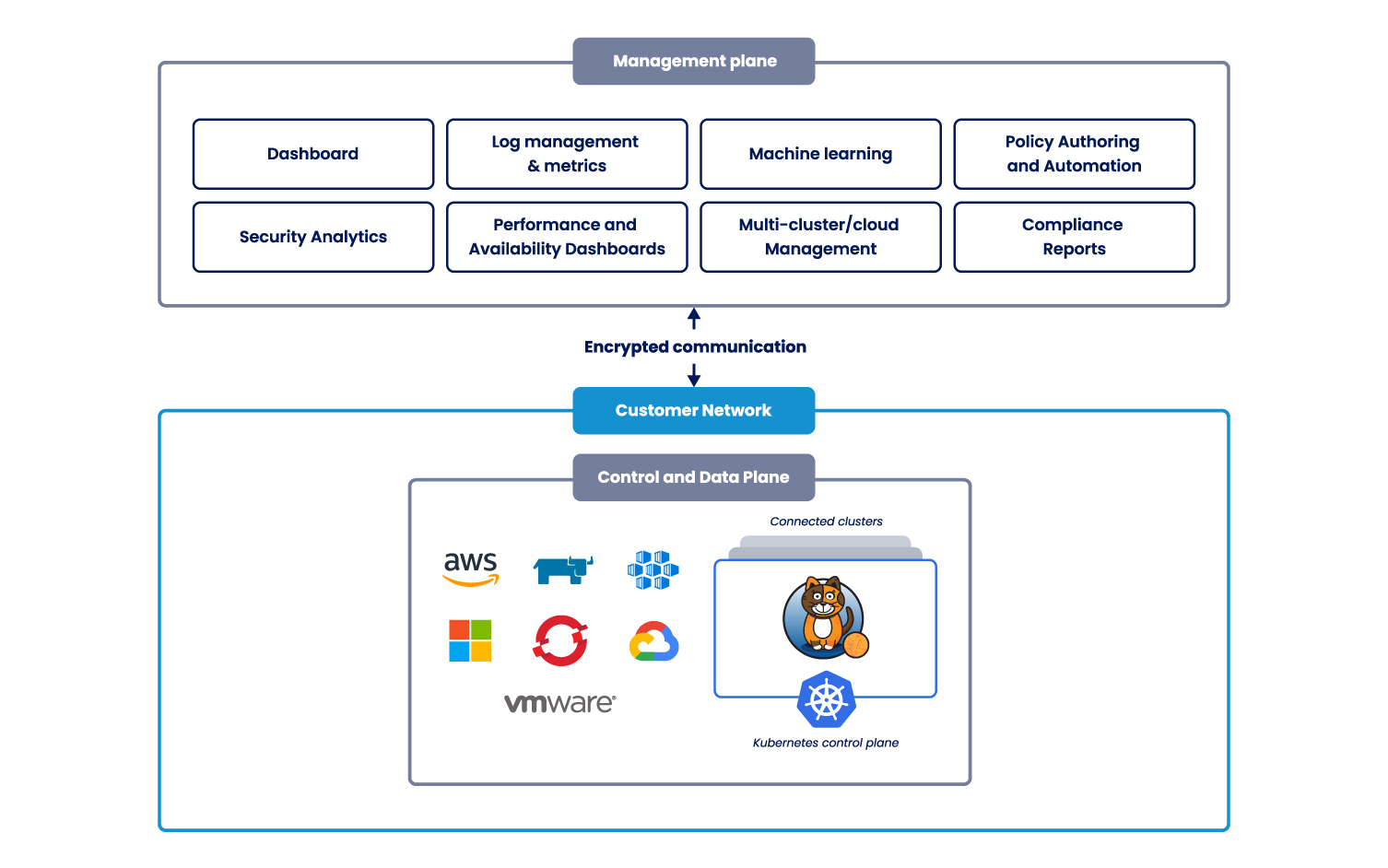
Calico Open Source is a networking and security solution for containers, virtual machines, and native host-based workloads that was born out of Project Calico.
Calico Open Source combines flexible networking capabilities with run-anywhere security enforcement to provide a solution with native Linux kernel performance and true cloud-native scalability.