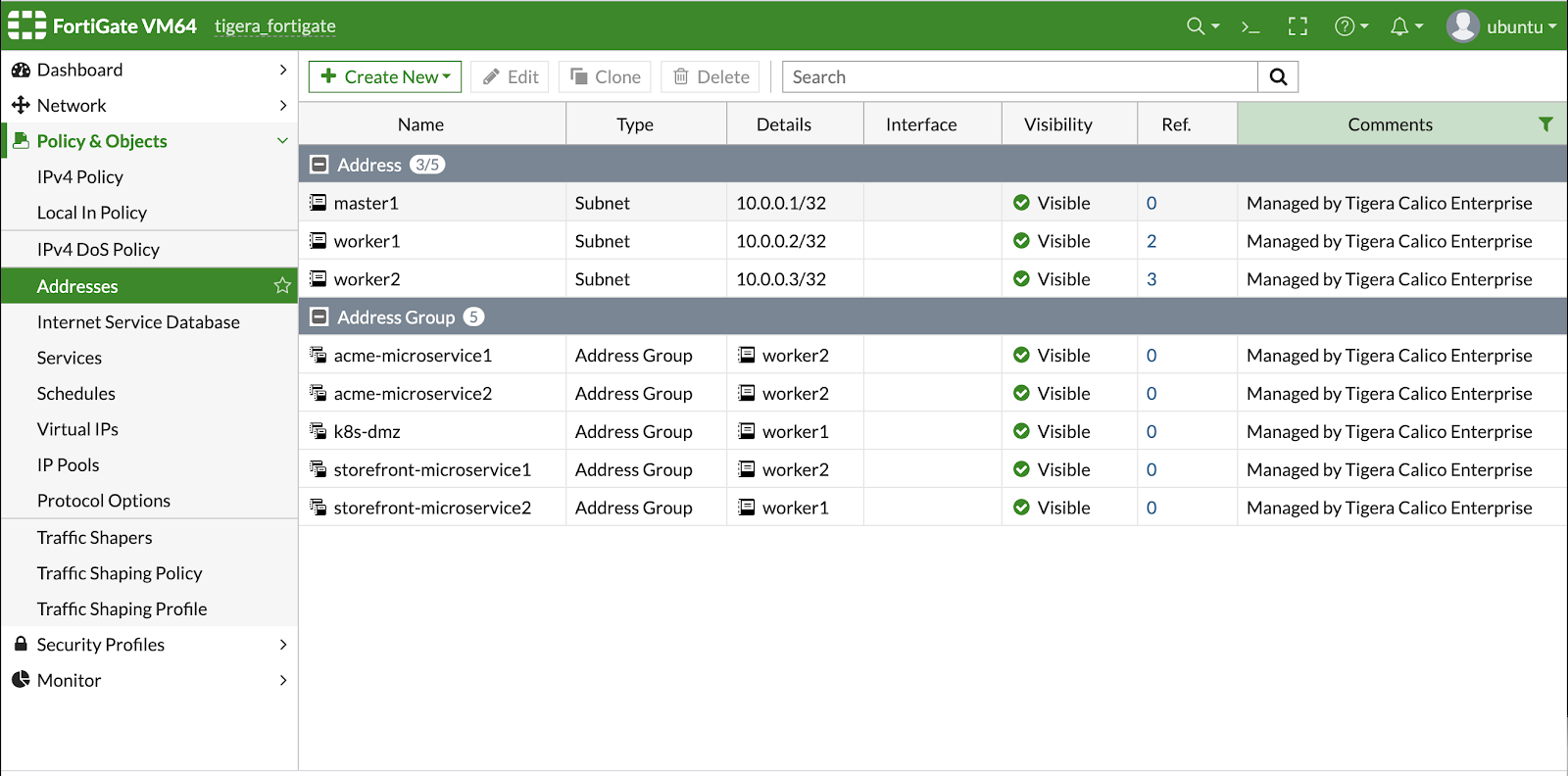
We are excited to announce the general availability of Calico Enterprise 2.7. With this release, Fortinet’s 400,000 customers can use FortiGate to enforce network security policies into and out of the Kubernetes cluster as well as traffic between pods within the cluster.
- Kubernetes workloads populate the FortiGate GUI
- The network team can then create and enforce policies in FortiGate and have them enforced as Calico Policy
- Saves time and money and lets the network team retain the firewall responsibility (which also frees up time for ITOps)
We have also added many new exciting capabilities that help platform engineers blow through barriers blocking their path to production, and advanced cybersecurity capabilities for those already running production workloads.
- Manage Network Security Across Multiple Kubernetes Clusters
- Enforce a Common Set of Security Controls Across Multiple Clusters
- Detect and Alert on Unauthorized Changes and Other Attack Vectors
- Self-Service Troubleshooting for End Users
- Detect and Prevent Malicious Data Exfiltration
Manage Network Security Across Multiple Kubernetes Clusters
As the adoption of Kubernetes continues to accelerate, our customers are seeing the number of clusters in their environments rapidly multiplying. This has created a management challenge for IT Ops teams who are constantly pushed to find ways to do more with less. With Calico Enterprise 2.7, you can now manage security policies across multiple clusters from a single, centralized management console. This greatly simplifies cluster administration and opens the way for customers to more easily scale as new clusters are deployed within the organization.
Enforce a Common Set of Security Controls Across Multiple Clusters
Another way that Calico Enterprise 2.7 supports scalability and simplifies cluster administration is through its ability to enforce a common set of security controls across multiple clusters. Corporate or regulatory security controls are implemented once and are then propagated across multiple clusters. Any subsequent change to security controls immediately rolls out to all clusters. All logging is captured in a central Elastic datastore and can be accessed for troubleshooting and proof of compliance with security requirements.
Detect and Alert on Unauthorized Changes and Other Attack Vectors
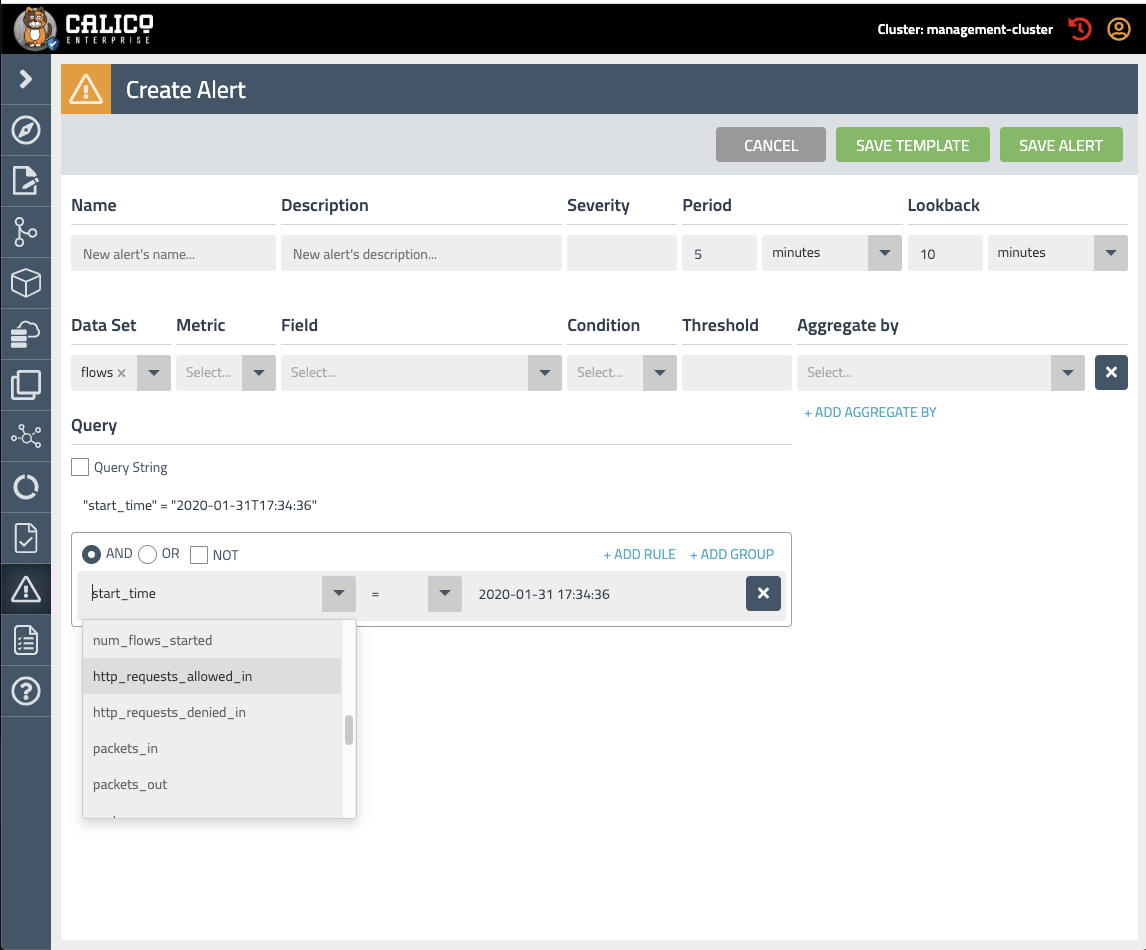
As clusters migrate into production, data security and access controls become paramount concerns. Every organization has its own unique data protection requirements and processes. The Alert Builder in Calico Enterprise 2.7 enables security teams to define custom alerts that are consistent with the unique compliance requirements in their organization. Alert Builder can help security teams create a “tamper-proof” environment. For example, alerts can be created that detect and raise an alarm when an unauthorized change has been made in a cluster.
Self-Service Troubleshooting for End Users
The last thing the platform team wants to be is a choke point in the system. But ITOps can occasionally be overwhelmed with a backlog of service requests, each one creating a source of frustration for the platform team and their internal customers. To ease the burden on ITOps, we have enabled Role-based Access Control (RBAC) for the Flow Visualizer in Calico Enterprise 2.7. With RBAC, granular privileges can be assigned to specific individuals (or teams) to access Flow Visualizer for the purpose of troubleshooting their own distributed applications, while restricting them from accessing other applications and sensitive data. Sharing the load helps speed problem resolution and frees the platform team to focus on more strategic activities.
Detect and Prevent Malicious Data Exfiltration
Tor exit nodes are the gateways where encrypted Tor traffic hits the Internet and can be abused to monitor traffic. Consumer VPNs can sometimes be a cover for threat actors. Connections like these may indicate a compromise within a Kubernetes cluster and should be assumed to be suspicious until confirmed otherwise. New threat defense capabilities in Calico Enterprise 2.7 can detect the presence of Tor exit nodes and consumer VPNs, and alert the security team to take appropriate action.
————————————————-
Free Online Training
Access Live and On-Demand Kubernetes Tutorials
Calico Enterprise – Free Trial
Solve Common Kubernetes Roadblocks and Advance Your Enterprise Adoption
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!