As more enterprises adopt containers, microservices, and Kubernetes for their cloud-native applications, they need to be aware of the vulnerabilities in container images during build and runtime that can be exploited. In this blog, I will demonstrate how you can implement vulnerability management in CI/CD pipelines, perform image assurance during build time, and enforce runtime threat defense to protect your workloads from security threats.
Image scanning and automatic blocking of high-risk images
The majority of images in CI/CD pipelines have vulnerabilities, misconfigurations, or both. An active cloud-native application protection platform (CNAPP) should scan, identify, and list vulnerabilities in container images based on databases such as NIST and NVD. The active CNAPP should then help teams build security policies to determine which images should be deployed or blocked based on several factors such as severity, last scan timestamp, and organizational exceptions. Given the sheer amount of vulnerabilities that appear daily, users will be easily overwhelmed if they have to address all existing vulnerabilities. Security teams will have to build a deploy/block criteria to prioritize vulnerabilities that they will address first—a workflow that is easy to start but difficult to manage and operate long-term. Hence, security teams should look for a security platform that makes this workflow an automated process by building policies to ensure what images can be deployed and have a level of acceptable security exposure.
An active security platform scans container images on-demand and provides the controls to build policies to admit or deny container images into the pipeline, and these functions are all incorporated into Calico Cloud’s image assurance abilities. With Calico Cloud’s Image Scanning and Admission Controller, DevOps and security teams can:
- Build security policies to block the deployment of vulnerable images automatically whose CVSS score is higher than the specified score.
- Categorize vulnerabilities as pass, warn, or fail. Pass and fail deploy and block images respectively, while warn deploys the image with an alert.
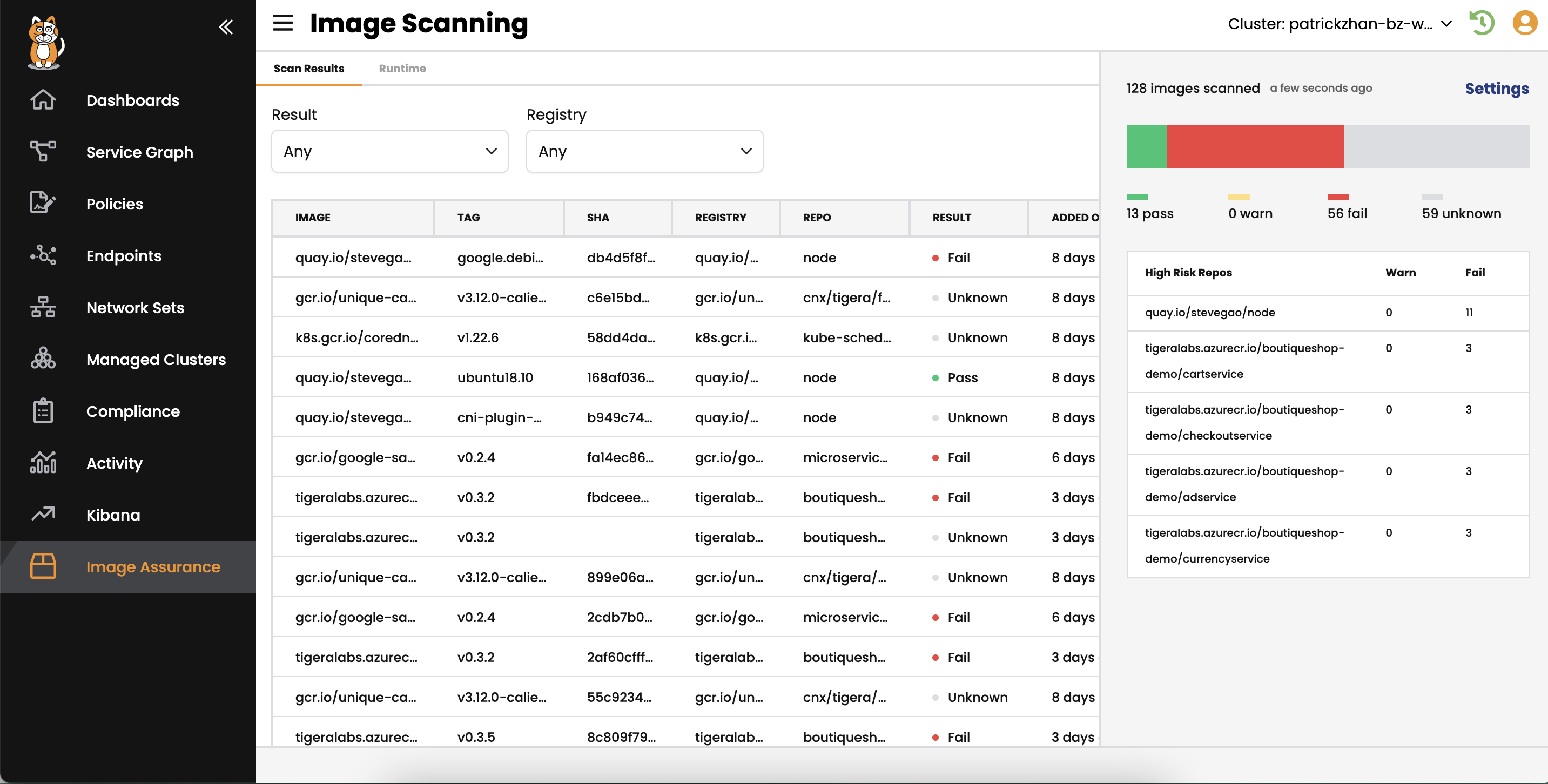
- Build security policies to deploy container images based on the last scan timestamp. For example, a policy can declare:
- Any image that hasn’t been scanned within the last 3 days will not be deployed.
- Any image that hasn’t been scanned within the last 7 days will not be deployed.
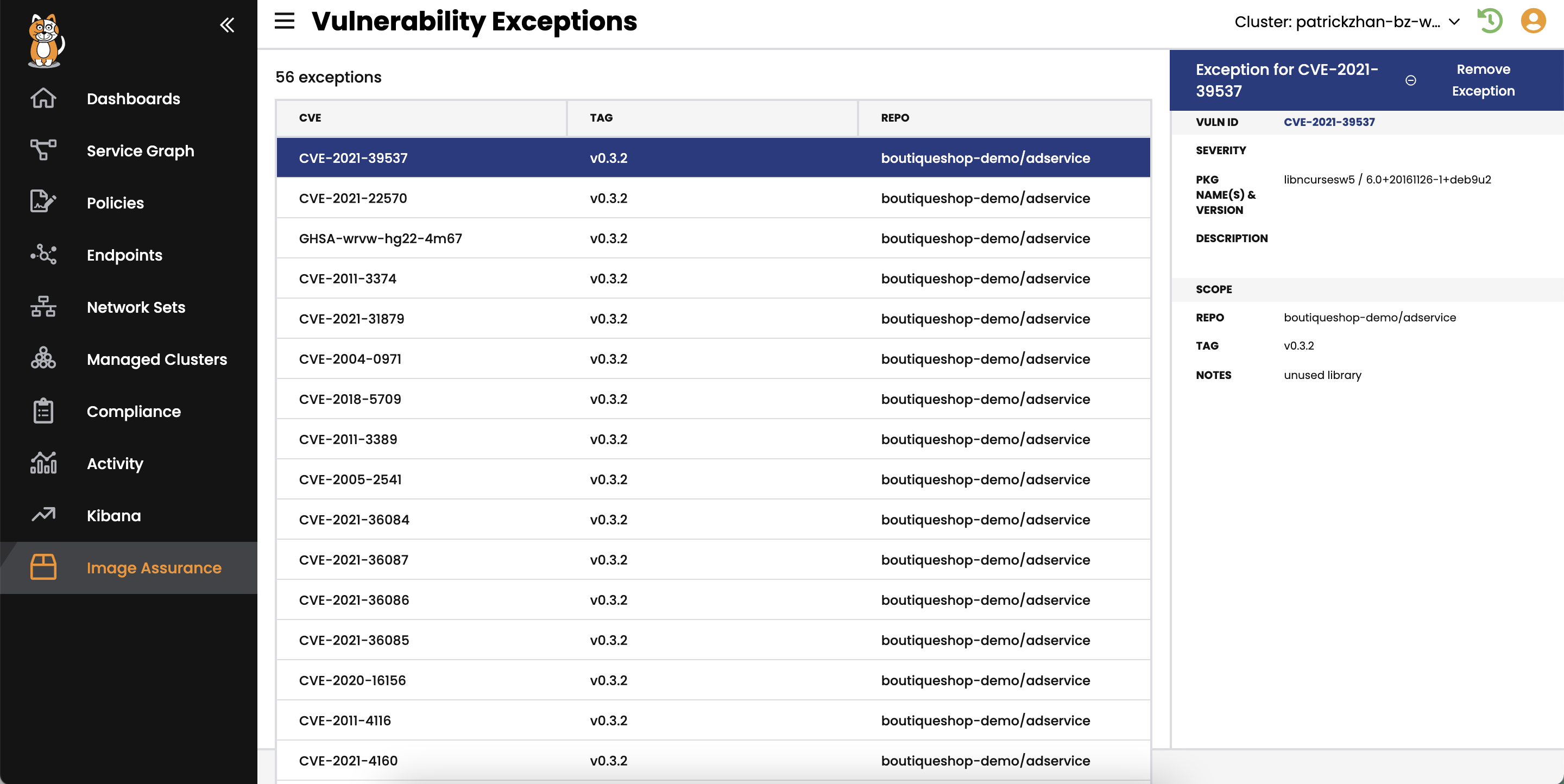
- Create exceptions based on image version or image type.
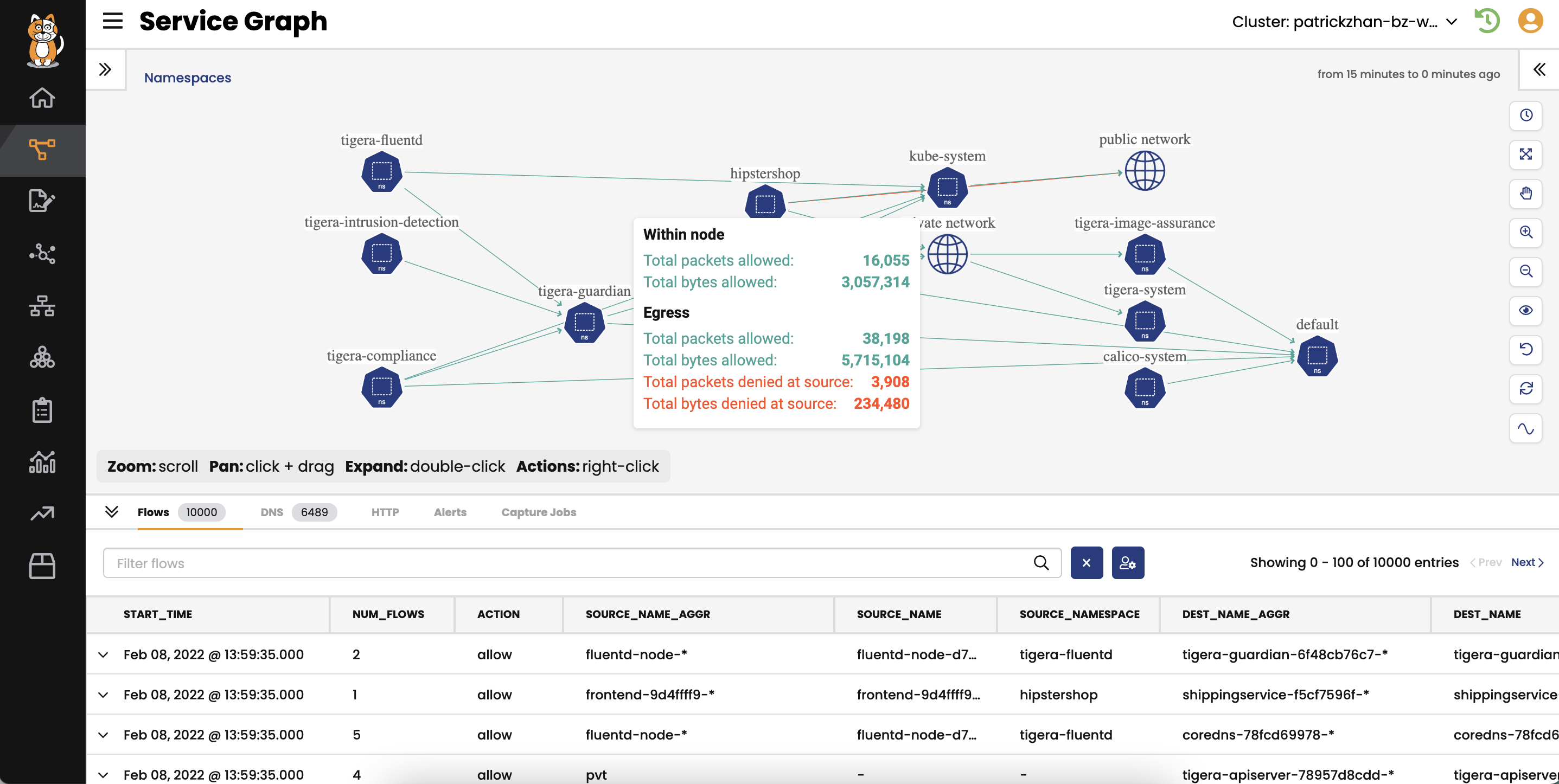
Runtime view of vulnerabilities and active risk mitigations
DevOps, SREs, and security teams don’t have a simplified security view of Kubernetes deployments due to the distributed and dynamic nature of Kubernetes. This means when a security incident occurs, teams must stitch data from the build and run time together, correlate the data, then use that data to build a security incident response plan. This process can take hours or longer. Organizations with a slow incident response time to security threats risk having customer data stolen, losing business, and sacrificing credibility.
Calico Cloud provides a runtime view of workloads and associated clusters, including their existing vulnerabilities. Calico also looks for anomalies and zero-day threats during runtime with ML-based detection and alerts users for unusual activity, even at the namespace level. If malware or a data exfiltration threat is detected, you can mitigate it by utilizing custom rule sets or Calico’s recommended policies. Combined with the workload communication visibility provided in the Dynamic Service and Threat Graph, you can quickly assess your Kubernetes cluster’s security posture during runtime. Teams will have a security view of their cluster across the stack, with all underlying metadata already correlated. This will allow you to quickly and easily identify threats in the runtime environment. You can use these findings to leverage Calico Cloud’s Policy Board to quarantine the affected workloads in seconds until the security risk is mitigated and solved.
Summary
Effective vulnerability management should be quick, simple, and easy. It should result in minimal service disruptions and strengthen the security posture of your cloud-native application, and Calico Cloud’s Image Assurance is built with that in mind. Try it yourself by signing up for a free trial of Calico Cloud.
Ready to learn more? Gain hands-on experience with our upcoming and on-demand webinars and live online workshops.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!


