Introduction
2020 is predicted to be an exciting year with more organizations adopting Kubernetes than ever before. As critical workloads with sensitive data migrate to the cloud, we can expect to encounter various Advanced Persistent Threats (APT) targeting that environment.
Domain Generation Algorithm (DGA) – What is It?
DGA is a technique that fuels malware attacks. DGA by itself can’t harm you. But it’s a proven technique that enables modern malware to evade security products and counter-measures. Attackers use DGA so they can quickly switch the command-and-control (also called C2 or C&C) servers that they’re using for malware attacks. Security software vendors act quickly to block and take down malicious domains hard-coded in malware. So, attackers used DGA specifically to counter these actions. Now DGA has become one of the top phone-home mechanisms for malware authors to reach C2 servers. This poses a significant threat to cloud security.
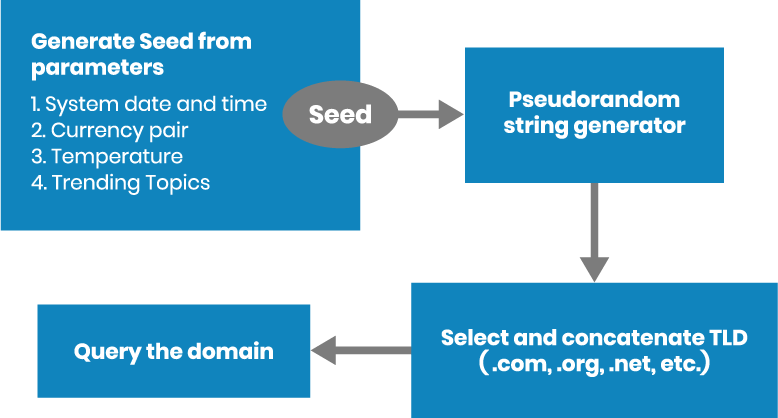
Mitre defines DGA as “The use of algorithms in malware to periodically generate a large number of domain names which function as rendezvous points for malware command and control servers”. Let’s examine this definition more closely. DGA at its core generates domains by concatenating pseudo-random strings and a TLD (e.g. .com, .org, .cc). The malware queries the domain to see if it gets a valid IP in response. Attackers are able to use this simple mechanism to avoid hard-coding C2 IPs or domains into the malware code, which becomes useless once blocked by traditional filtering mechanisms.
Now attackers just need to register a single domain out of thousands that a DGA produces. This single domain then becomes a rendezvous point for malware, botnet or backdoor embedding a DGA. Generated domain names are randomized, making it impossible to use traditional filtering mechanisms to block every single domain generated by DGA. For example, the infamous banking trojan Zeus was able to generate 1,000 domains in a single day. In addition, DGA often uses randomized seeds to evade prediction, e.g. the daily temperature in San Francisco.
Why does DGA matter?
To better understand DGA, we need to look at how DGA generates domains and the complexity associated with detection. The attacker needs to reproduce the same results as his malware embedded in DGA. Typically the following items are needed:
- Common seed which can be anything: System date and time, currency pair rate, daily temperature, or even Twitter and Facebook trending topics
- List of TLDs like .com, .org, .cc, .net and a mechanism to append these. Attackers have even started using exotic TLDs such as .tickets, .blackfriday and .feedback
- Pseudorandom generator using the seed
Attackers can register one of the domains generated by the algorithm, wait for the targeted malware to generate, and query domains until the one that’s registered is found. This results in resilient C2 servers which are more difficult to take down by law enforcement, as attackers can always register the next domain by using the algorithm. Additionally, they can time the attacks down to the minute because the dynamic nature of DGA makes it extremely hard to detect.
The DGA domain generation process begins with a “seed” derived from ordinary parameters.
Can DGA be detected in action?
Researchers are trying to reverse engineer the malware and get the exact DGA implementation to predict all future domain lists. But keeping up with huge malware families using manual efforts is not practical. For example, DGA implementation complexity enables the Dyre malware alone to generate 300+ DGA domains everyday.
Meaningfully addressing DGA requires a sophisticated approach that can target the entire attack class. Anomaly detection using machine learning has proven to be effective in this case. Machine learning algorithms can be trained on large datasets like Alexa or Majestic Million and learn what a valid domain name looks like. Then they can ingest large amounts of data and classify anomalous behaviour by detecting a DGA in action.
How can Calico Enterprise help detect DGA?
Manually detecting DGA domains in cloud infrastructure is not an easy task for security teams, as it adds significant overhead. We created a machine learning algorithm in Calico Enterprise which specifically targets the DGA use case and identifies anomalous behavior, making it easy to detect DGA activity. Detection of DGA in a cloud environment is one of the high confidence indicators of compromise (IOC) that can aid information security and IT professionals in detecting data breaches, malware infections, or other threat activity such as an APT.
Malware which predominantly uses DGA to create resilient C2 servers includes Zeus, Dyre, Conficker and many more. According to the Center for Internet Security (CIS), Zeus and its variants are still a major threat to internet security. Let’s take a look at GOZ (GameOver Zeus) (which is a strain of Zeus) and see how the detection works. Then we’ll look at the extended numbers to see if we were able to detect one of the top malware families.
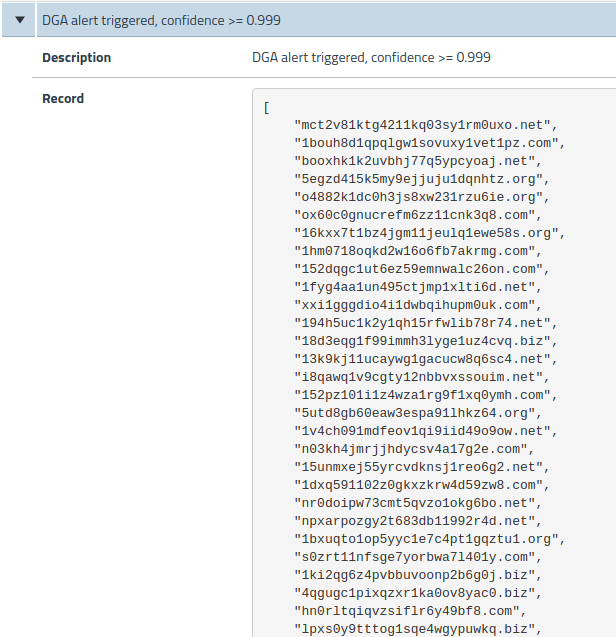
As you can see in the chart below, we used a DGA seed from GOZ to confirm that it’s detected by our DGA algorithm. The detection was successful with a very high confidence level of 0.999 (on scale of 0 to 1). The result included the DGA domain list detected by the algorithm. The DGA domain list is a valuable asset for network security teams, enabling them to easily and quickly trace the source of the GOZ infection and mitigate as necessary. Faster anomaly detection and resolution has the added benefit of reducing dwell time and reducing overall risk.
Calico Enterprise DGA detection will not alert security teams unless its confidence level is north of 99%, which virtually eliminates the possibility of false positives. Additionally our machine learning algorithm is highly trained and tweaked to target the DGA use case. As a result we are able to generate alerts with a high confidence level as well as provide critical forensic data for security teams.
In the following table we show the top 10 malware families detected using the Calico Enterprise DGA detection algorithm.
| Malware Family | Details | DGA detected by Calico Enterprise | |
| 1. | Gameover (Zeus) | Secretly developed botnet by Zeus author | Yes |
| 2. | Padcrypt | Ransomware with chat support | Yes |
| 3. | Conficker | Worm which is still running strong | Yes |
| 4. | Dyre | Banking trojan | Yes |
| 5. | Necurs | Top spam bot distributing malware | Yes |
| 6. | Ramnit | Notorious trojan still running strong | Yes |
| 7. | Virut | Old virus resurfacing in APT campaigns | Yes |
| 8. | Tinba | Smallest banking trojan 20kb | Yes |
| 9. | Monero miner | Mining malware using exotic DGA | Yes |
| 10. | Pushdo | Trojan downloader | Yes |
Summary
- Detecting resilient command-and-control (C2) servers impacted by DGA malware using manual efforts is impractical
- Traditional filtering techniques are inadequate to stop attackers
- A machine learning approach to anomaly detection can help us, but it must be highly efficient and tweaked to target DGA use cases
We showed how the Calico Enterprise DGA machine learning algorithm can detect any present or future APTs using DGA to connect back to the C2 servers, while minimizing false positives. In addition, the DGA domain list provided by the algorithm is a valuable asset for any security team, enabling them to efficiently mitigate threats while reducing dwell time and associated risk.
————————————————-
Free Online Training
Access Live and On-Demand Kubernetes Training
Calico Enterprise – Free Trial
Network Security, Monitoring, and Troubleshooting
for Microservices Running on Kubernetes
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!