Kubernetes has become the de facto standard for container orchestration, providing a powerful platform for deploying and managing containerized applications at scale. As more organizations adopt Kubernetes for their production workloads, ensuring the security and privacy of data in transit has become increasingly critical. Encrypting traffic within a Kubernetes cluster is one of the most effective components in a multi-layered defence when protecting sensitive data from interception and unauthorized access. Here, we will explore why encrypting traffic in Kubernetes is important and how it addresses compliance needs.
Why Encryption is Necessary
Two encryption methods are commonly adopted for protecting the data integrity and confidentiality; encryption at rest and encryption in transit. Encryption at rest refers to encrypting stored data, e.g. in your cloud provider’s managed disk solution, whereby if the data was simply copied and extracted the raw information obtained would be unintelligible without cryptographic keys to decrypt the data.
Encrypting data in transit is an effective security mechanism and a critical requirement for organization compliance and regulatory frameworks, as it helps protect sensitive information from unauthorized access and interception while it is being transmitted over the network. We will dive deeper into this requirement.
Encrypting data in transit involves transforming the data into an unreadable format, which can only be decrypted by authorized parties with the appropriate keys. This helps to prevent eavesdropping and man-in-the-middle attacks that can compromise the confidentiality and integrity of the data.
For many years protocols such as IPSEC and OpenVPN have been widely used to provide data encryption for point to point Virtual Private Networks (VPN) and User Remote Access VPNs. Other end to end encryption needs can also be met leveraging TLS which function higher up the OSI stack. Kubernetes does not come with native encryption features but, being extensible by nature, encryption can be implemented in a number of ways using alternative solutions. Before we dive into how we can encrypt our traffic we should understand one important driver for encryption.
Using Encryption in compliance
Compliance regulations, such as the General Data Protection Regulation (GDPR), PCI DSS and Health Insurance Portability and Accountability Act of 1996 (HIPAA), require organizations to implement adequate security measures to protect data in transit.
For example, in the case of PCI compliance here section 4.1 “Data-in-transit encryption to safeguard sensitive data” requires organizations to implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including the encryption of personal data in transit.
The guide to implement HIPAA requirements concisely breaks down HIPAA encryption requirements:
“HIPAA Security Rule requirement (164.312(c): Implement policies and procedures to protect electronic protected health information from improper alteration or destruction”
This can be interpreted as meaning it is the responsibility of system owners to demonstrate the protection against unauthorized access to electronic Protected Health Information (ePHI) and requires Covered Entities and Business Associates to implement encryption to guard against unauthorized access to ePHI transmitted over a communications network. This is because there are multiple points during a transmission at which a communication could be intercepted and accessed without authorization.
Overall, encrypting data in transit is a critical component of IT compliance, and organizations must ensure that appropriate encryption measures are in place to protect sensitive data and meet regulatory requirements. Failure to comply with compliance and regulations can result in significant fines and reputational damage for the organization.
Encryption in Kubernetes clusters
Wireguard is a more recent encryption technology that is seeing increasing adoption in the industry. Whilst encryption protocols like IPSEC and OpenSSL have been widely utilized Wireguard is a technology that has several advantages especially in Kubernetes environments:
- Performance: WireGuard is designed to be lightweight and fast, with minimal overhead. It uses modern cryptographic algorithms and is implemented in the kernel, which makes it much faster than user-space operations.
- Simplicity: WireGuard has a much simpler configuration than IPsec and OpenSSL, which makes it easier to manage and maintain. This simplicity also means that it’s easier to implement correctly and less prone to configuration errors that could lead to security vulnerabilities. Its source code is approximately 4000 lines which is orders of magnitude less than other protocols. Consequently, this makes auditability of the code simpler.
- Scalability: As Kubernetes environments grow in size and complexity, the overhead of IPsec and OpenSSL can become significant. WireGuard’s lightweight design and efficient use of system resources make it a more scalable solution.
- Security: WireGuard uses modern, secure cryptographic algorithms that are less vulnerable to attack than the older algorithms used by IPsec and OpenSSL. It also has a smaller attack surface due to its simplicity, which makes it less susceptible to security vulnerabilities.
For further technical information of how WireGuard operates under the hood, Tigera’s Peter Kelly gave a presentation at KubeCon Europe on this topic.
Although WireGuard is relatively simple to deploy there are still a number of manual operations a standalone implementation would require across all Kubernetes nodes:
- Creating encryption key pairs
- Distributing public keys securely to all nodes
- Creating tunnel virtual interfaces and ip address assignment
- Configure tunnel endpoint addresses for each node in the mesh
- Continuous configuration of pod endpoints and routing through the correct WireGuard tunnel. Every time a pod is created or destroyed kernel configuration is required on all nodes
In a dynamic environment like Kubernetes manually configuring these operations is not feasible or scalable. Calico’s implementation of WireGuard takes care of orchestrating all these tasks continuously to ensure data in transit is securely encrypted no matter what events are taking place in the cluster. Enabling WireGuard on all cluster nodes is a simple command:
kubectl patch felixconfiguration default --type='merge' -p '{"spec":{"wireguardEnabled":true,"wireguardEnabledV6":true}}'
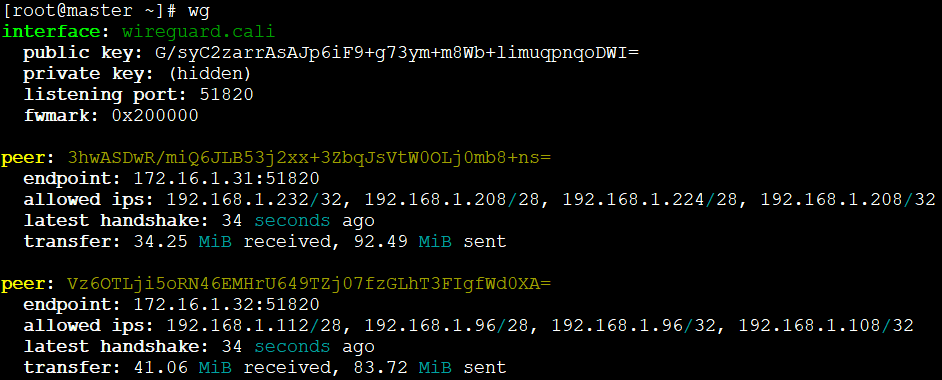
Calico then takes care of all the kernel and WireGuard configurations on all nodes – time to smash the “That was Easy” button. Each cluster node can show what the mesh looks like with all the Endpoints behind each peer:
Conclusion
In today’s world, data breaches and cyber attacks are on the rise, which is why encryption has become a critical component of data protection. Data in transit encryption ensures that data transmitted between devices and networks is secure and cannot be intercepted by unauthorized parties. Compliance requirements such as GDPR and HIPPA require organizations to implement data in transit encryption to protect sensitive information from being compromised.
WireGuard is a suitable technology for data in transit encryption because of its high performance, simplicity, scalability, and security. Its lightweight design and modern cryptographic algorithms make it faster and more secure than traditional VPN protocols. Calico’s implementation of WireGuard automates all the necessary steps to ensure traffic between Kubernetes nodes is encrypted. In this manner, organizations can ensure their sensitive information remains secure and compliant with regulatory requirements.
To try encryption on Calico Cloud, get started with a free trial.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!