Shift Left Security
Automatically define, validate and deploy security policies in a self-service environment

- Calico Cloud
- Shift Left Security
Overview
When deploying a new microservice, security policies must be created to define which other microservices it can and should connect to. But before deployment, each new policy and service must be reviewed to ensure it will not override or interfere with an existing policy. Review and approval typically occurs at a central point of control, creating a choke-point when microservice deployments scale.
Using policy tiers, Calico enables SREs, and developer teams to easily make self-service security policy changes to a cluster without the risk of overriding an existing policy. No central manager or control point is required to create, review, or approve new policies. Deployment of new microservices along with the creation of necessary security policies is a fully-automated process.
Benefits
Maintain Compliance
Maintain compliance: Microservices can be deployed along with security policies, without the risk of overriding other critical security policies required for compliance.
Automate Policies
Automatically identify and eliminate any potential problems caused by incorrect, incomplete, or conflicting security policy deployments.
Speed Deployment
Fully automate and accelerate the end-to-end microservices deployment process, including any necessary security changes, using policy-as-code.
Capabilities
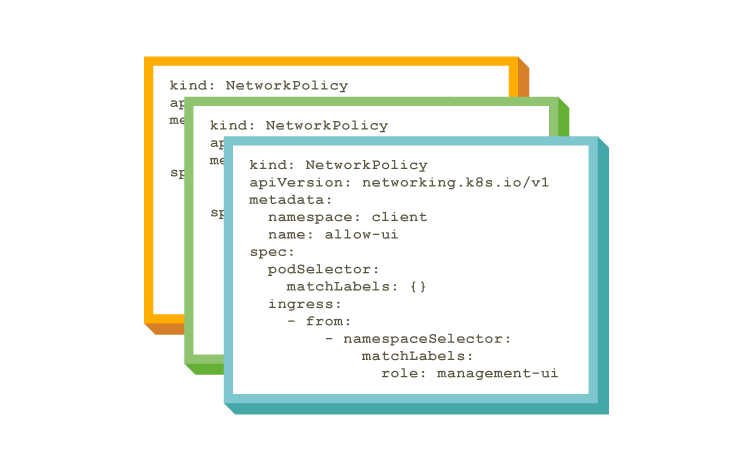
Policy-as-Code
- Calico enables developers to safely deploy their services to secure clusters using Policy Builder, an automated, self-service security policy creation function.
- Calico lets developers create policies without having to learn the intricacies of YAML definitions, or relying on a policy “copy and paste” approach.
- Calico security policies are represented as code that is deployed alongside your microservices, and fully automates the end-to-end deployment process including any necessary security changes.
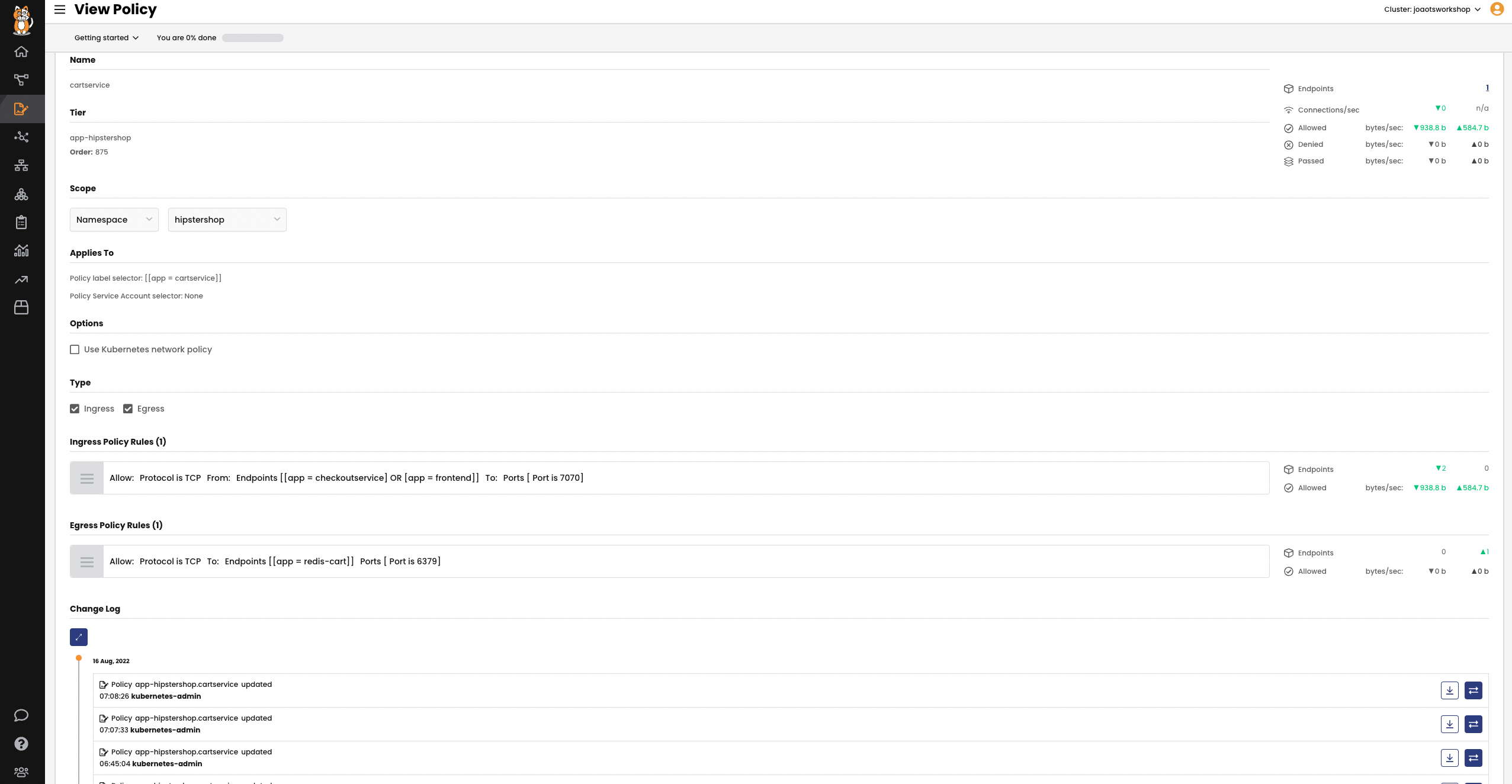
Policy Tiers
-
Calico policy tiers define the order in which security policies are evaluated. Higher tiers evaluate traffic first. Self-service deployments cannot override these controls.
- Calico automates a validation step that ensures your security policy works properly before being committed.
- Calico can deploy your policies in a “staged” mode that will display which traffic is being allowed or denied before the policy rule is enforced
- A policy can then be committed if it is operating properly. This step avoids any potential problems caused by incorrect, incomplete, or conflicting security policy definitions.
- Calico policy tiers can be easily configured and managed from the Calico graphical user interface.
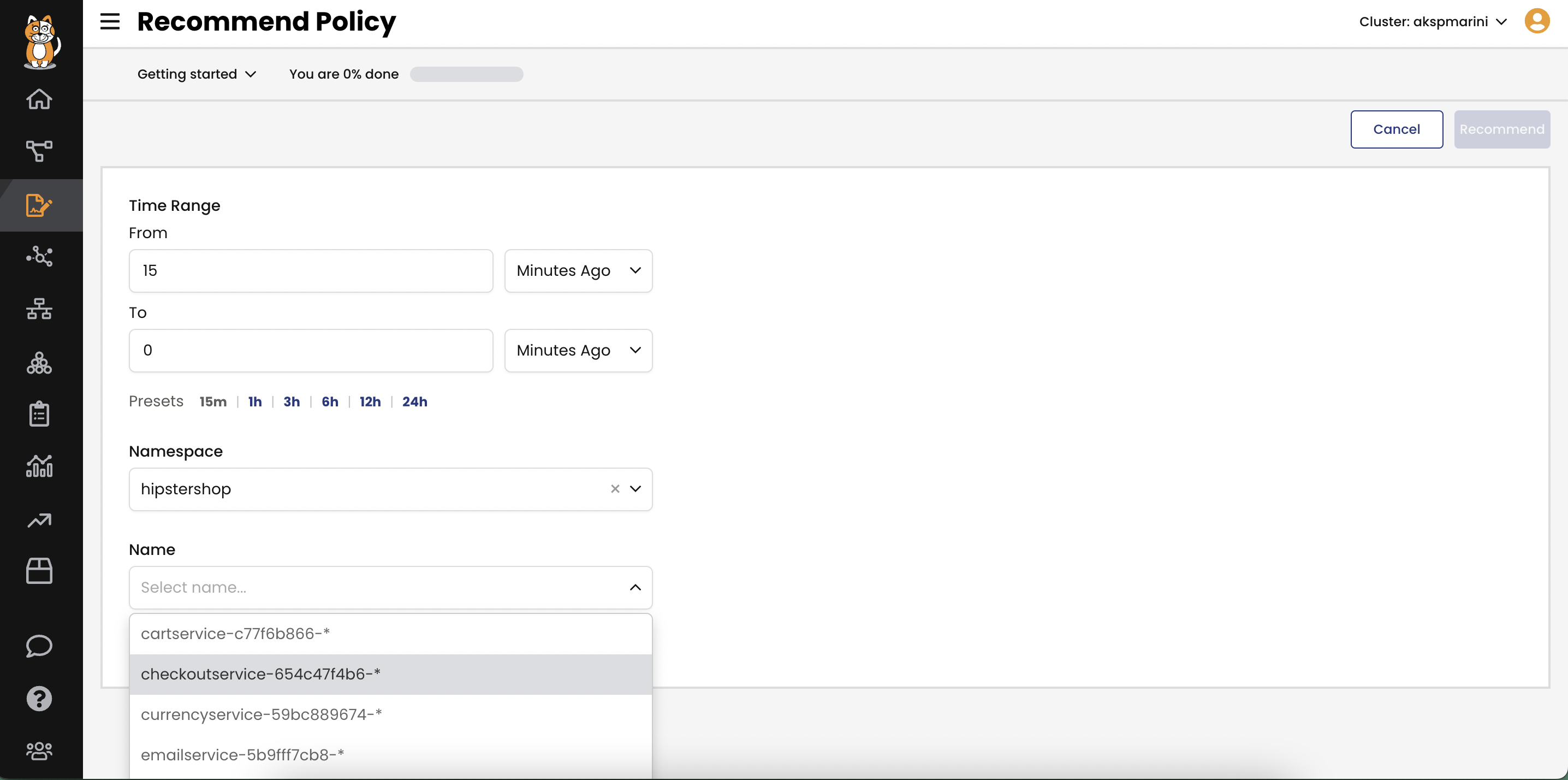
Policy Recommendation
- Developer teams can create security policy workflows that enable security policies to be safely created, QA tested, and deployed.
- Calico can also auto-generate a recommended policy based on ingress and egress traffic between existing services. This can help you implement policy when you are uncertain of the interdependent connections between services.
- Calico Policy Recommendation is the fastest way to implement security policies in an existing cluster if you are unsure what policy is needed.
How It Works
Calico policy tiers enables developers to safely deploy their services to secure clusters using “policy as code” within an automated, self-service security policy process. With policy tiers, developers can create policies without having to learn the intricacies of YAML. Policy tiers define the order in which security policies are evaluated. Calico automates review and validation steps that preview and stage policies to ensure they are working properly before being committed to deployment.