Since the release of CVE-2020-8554 on GitHub this past December, the vulnerability has received widespread attention from industry media and the cloud security community. This man-in-the-middle (MITM) vulnerability affects Kubernetes pods and underlying hosts, and all Kubernetes versions—including future releases—are vulnerable.
Despite this, there is currently no patch for the issue. While Kubernetes did suggest a fix, it only applies to external IPs using an admission webhook controller or an OPA gatekeeper integration, leaving the door open for attackers to exploit other attack vectors (e.g. internet, same VPC cluster, within the cluster). We previously outlined these in this post.
Suggested fixes currently on the market
Looking at the Kubernetes security market, there are currently a few security solutions that attempt to address CVE-2020-8554. Most of these solutions fall into one or two of three categories:
- Detection (using Kubernetes audit logs)
- Prevention (using admission webhook controller)
- Runtime defense (inline defense)
A few of the solutions rely on preventing vulnerable deployments using an OPA gatekeeper integration; these solutions alert users when externalIP (possibly loadBalancerIP) is deployed in their cluster configurations. Most solutions, however, present a dual strategy with a focus on prevention and detection. They use an admission controller for whitelisting externalIP, and Kubernetes audit logs to detect requests to create or patch services with externalIP. While it is easy to detect and prevent the use of externalIP with these approaches, it becomes particularly difficult to do the same with loadBalancerIP. This is because loadBalancerIP is commonly used in Kubernetes clusters, so it easily becomes a big task to separate false positives for this service type.
Both of the above approaches rely on the addition of custom configuration and passive detection, which requires monitoring cycles, tracking, incident response, and false positive mitigation for commonly used service types. A more effective strategy would be to mitigate this type of MITM vulnerability at runtime.
Deploying runtime defense against CVE-2020-8554
By using runtime defense against this vulnerability, organizations don’t need to make any changes to their operation’s workflow or add additional monitoring and enforcement tools. This avoids overhead and saves precious time and resources.
Calico Cloud’s runtime defense provides protection for the three types of Kubernetes services (NodePort, LoadBalancer, and ClusterIP) that are vulnerable to CVE-2020-8554. It protects against multiple attack vectors (e.g. internet, same VPC cluster, within the cluster) without the need for additional admission webhook controllers. In the figure below, we show a Kubernetes packet flow through a Kubernetes service. Calico Cloud’s runtime defense works by enforcing policies on flow both pre- and post-DNAT (destination network address translation). This zero-trust network model prevents traffic from being hijacked by malicious entities and provides runtime defense against CVE-2020-8554’s specific class of vulnerability.
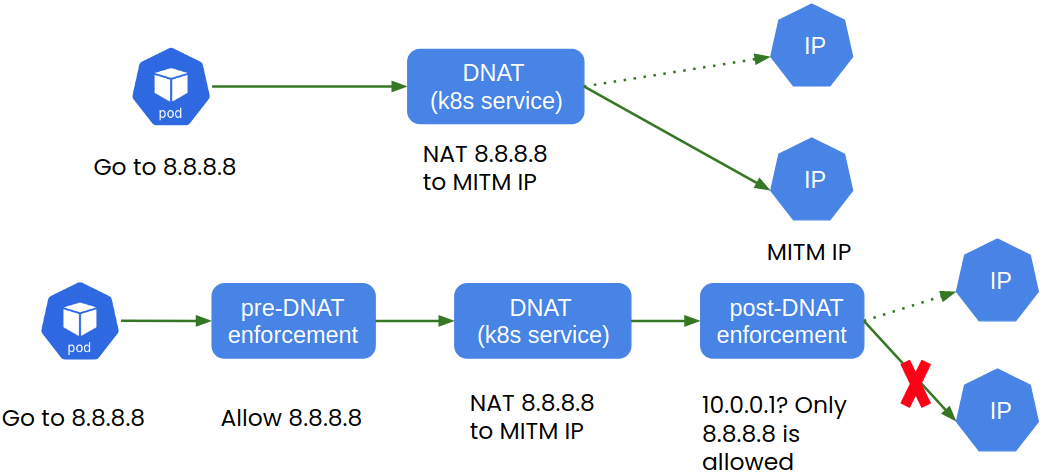

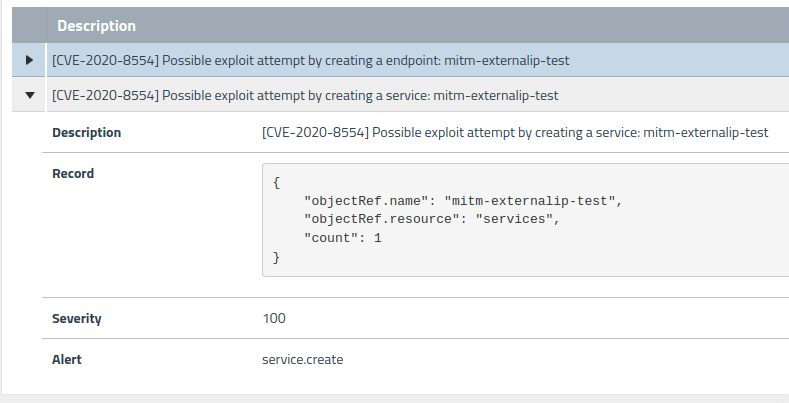
For prevention, Calico Cloud offers OPA gatekeeper integration to whitelist externalIP or loadBalancerIP. This prevents attackers from using attacker-controlled MITM IPs to modify a service. For detection, Calico Cloud uses signals to detect probable exploit attempts using this vulnerability. We uncovered the subtle use of Kubernetes endpoints with selectorless services to exploit the CVE-2020-8554 vulnerability; this is considered an additional indicator of attack (IOA) and is shown in the below alert.
Summary
When choosing a solution to defend against CVE-2020-8554, DevSecOps and SRE teams should consider the requirements for applying protection at all the layers and constructs of this threat. Calico Cloud takes a unique approach to addressing this vulnerability, using a combination of runtime defense, detection, and prevention. With its Kubernetes-native architecture, Calico Cloud provides a complete security solution to mitigate the Kubernetes MITM vulnerability CVE-2020-8554.
To learn more about the latest TTPs being used by threat actors to target Kubernetes clusters, register for our upcoming webinar.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!


