We’re excited to announce that Calico Enterprise, the leading solution for Kubernetes networking, security and observability in hybrid and multi-cloud environments, now includes encryption for data-in-transit.
Calico Enterprise is known for its rich set of network security implementations to protect container workloads by restricting traffic to and from trusted sources. These include, but are not limited to, implementing existing enterprise security controls in Kubernetes, managing egress access using DNS policy, extending firewalls to Kubernetes, and intrusion detection and threat defense. As the Kubernetes footprint expands, however, we’ve seen demand for an even greater in-depth approach to protecting sensitive data that falls under regulatory compliance mandates.
Why encryption is necessary
Not all threats originate from outside an organization. According to Gartner, nearly 75% of breaches happen due to insider behavior, from people within the organization such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems. This level of exposure is unacceptable for organizations that have strict data protection and regulatory compliance requirements. No matter where a threat originates, encrypted data is unreadable to anyone except the legitimate keyholder, thus protecting the data should a breach occur.
Encryption requirements for compliance
Several regulatory standards impose data protection and compliance requirements on organizations and specify the use of encryption, including SOX, HIPAA, GDPR, and PCI. For example, the Payment Card Industry Data Security Standard (PCI DSS) applies to organizations that handle branded credit cards and was created to increase controls around cardholder data to reduce credit card fraud. PCI DSS requires organizations to encrypt credit card account numbers stored in their databases and ensure that data remains secure when transferred. Validation of compliance is performed annually or quarterly.
Encryption methods
A common solution is to encrypt traffic at the application layer using protocols like Transport Layer Security (TLS). Traffic can also be encrypted at a lower infrastructure level using IPsec. However, these approaches introduce an additional layer of complexity and performance implications. Encrypting traffic with TLS requires SSL certificates, creating operational overhead for IT organizations that are already overburdened.
Calico’s Data-in-Transit encryption
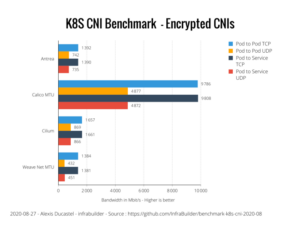
Calico Enterprise avoids that complexity by utilizing WireGuard to implement data-in-transit encryption. WireGuard is consistent with Tigera’s “batteries-included” approach to Kubernetes networking, security and observability. WireGuard runs as a module inside the Linux kernel and provides better performance and lower CPU utilization than IPsec and OpenVPN tunneling protocols. Independent benchmark tests of Kubernetes CNI’s have shown that Calico with encryption enabled is 6x faster than any other solution in the market.
We are pleased to announce that WireGuard encryption is now generally available with Calico Enterprise v3.3. The addition of data-in-transit encryption augments an existing rich security feature set in Calico Enterprise. And with Calico Enterprise, you’ll maintain visibility into all traffic in your Kubernetes clusters even when encryption is deployed. Enabling data-in-motion encryption on Calico Enterprise is easy… all you need is a Kubernetes cluster with WireGuard installed on the host operating system. You’ll find a complete list of supported operating systems and installation instructions on the WireGuard website.
————————————————-
Free Online Training
Access Live and On-Demand Kubernetes Training
Calico Enterprise – Free Trial
Kubernetes Networking, Security and Observability in Hybrid and Multi-Clouds