Extend Enterprise Security Controls to Kubernetes
Meet regulatory and corporate compliance requirements for container workloads by extending your existing enterprise security controls to your Kubernetes environment

Overview
Most businesses are subject to corporate and/or regulatory compliance requirements. From an operational perspective, this may involve isolation of workloads containing sensitive data, or restricting who is allowed to access specific resources. There may also be requirements to implement access control frameworks such as security zones (e.g. trusted, untrusted, and DMZ). Even more advanced controls are sometimes needed, like building a moat around PCI-DSS workloads, or logging all HIPAA data transactions.
Auditors need proof that you are enforcing these controls, but capturing the information required to show proof can be challenging, especially in a dynamic, distributed Kubernetes environment where workloads are ephemeral. Auditors will want to know:
- What security controls are currently implemented?
- Can you detect when your security controls change?
- Can you prove that you were compliant at any given date and time?
Calico continuously monitors your Kubernetes environment for compliance and retains a daily history of your compliance status. Calico also includes predefined compliance report formats, as well as a resource for creating customized reports.
Benefits
Automate and Simplify
Automates and simplifies compliance monitoring, enforcement, and audit by tracking all policy changes and retaining a daily history of your compliance status.
Audit and Report
Enables you to easily access audit reports showing the network security rules in place, in order to demonstrate proof of compliance for your security team and auditors.
Maintain Compliance
Helps DevSecOps teams maintain the security posture needed to meet compliance requirements mandated by legislation or your own internal security team, helping you to get to production faster.
Key Features

Encryption
Several regulatory standards impose data protection and compliance requirements on organizations and specify the use of encryption, including PCI, SOX, HIPAA, and GDPR. Encrypting traffic using a standard approach like TLS, for example, requires SSL certificates and results in more complexity and operational overhead for IT organizations that are already overburdened. Calico avoids unnecessary complexity by utilizing WireGuard to implement data-in-transit encryption. WireGuard runs as a module inside the Linux kernel and provides better performance and lower CPU utilization than IPsec and OpenVPN tunneling protocols. Independent benchmark tests of Kubernetes CNI’s have shown that Calico with encryption enabled is 6x faster than any other solution in the market. And with Calico, you’ll maintain visibility into all traffic in your Kubernetes clusters even when encryption is deployed.
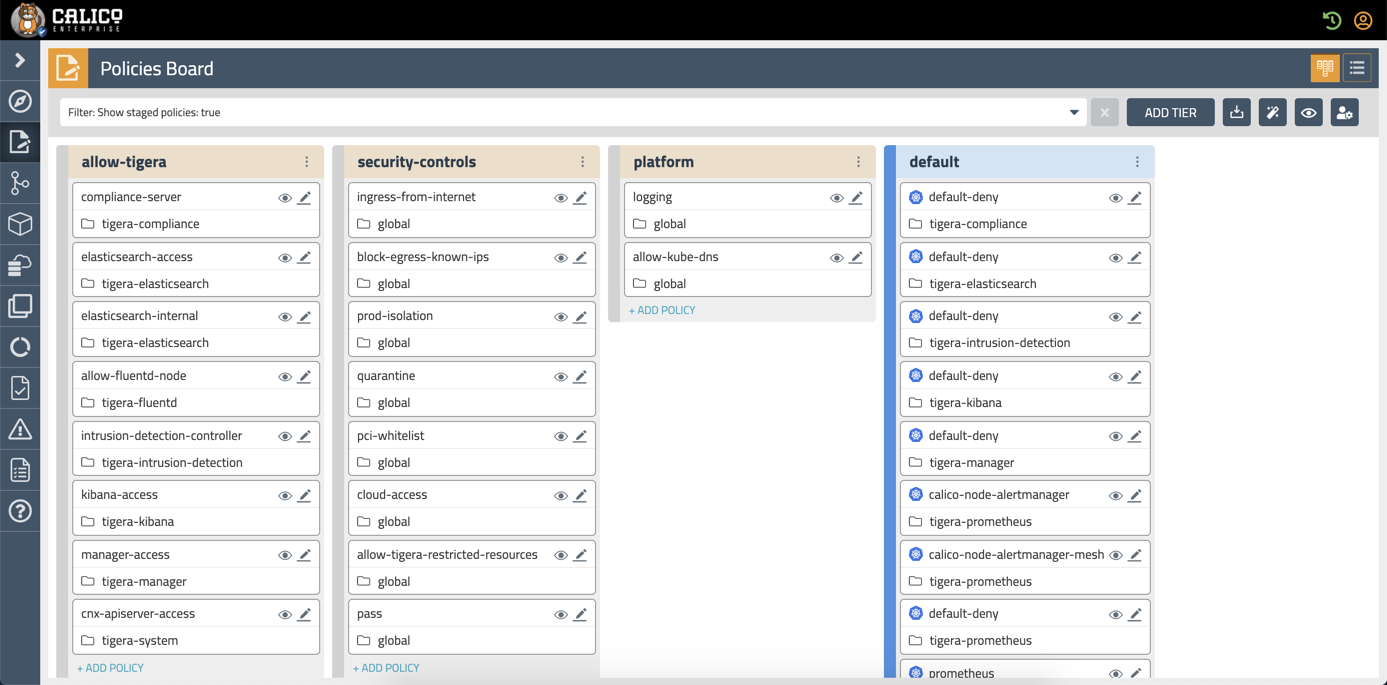
Policy Tiers
Calico introduces the concept of policy tiers. Policy tiers define the order in which security policies are evaluated. Higher tiers evaluate traffic first. This is where you define and implement your security controls.
Policy tiers can federate across multiple clusters using unified control, enabling a single definition of security controls that can be applied to all clusters. If the traffic complies with the security controls then it is evaluated by the lower tiers.
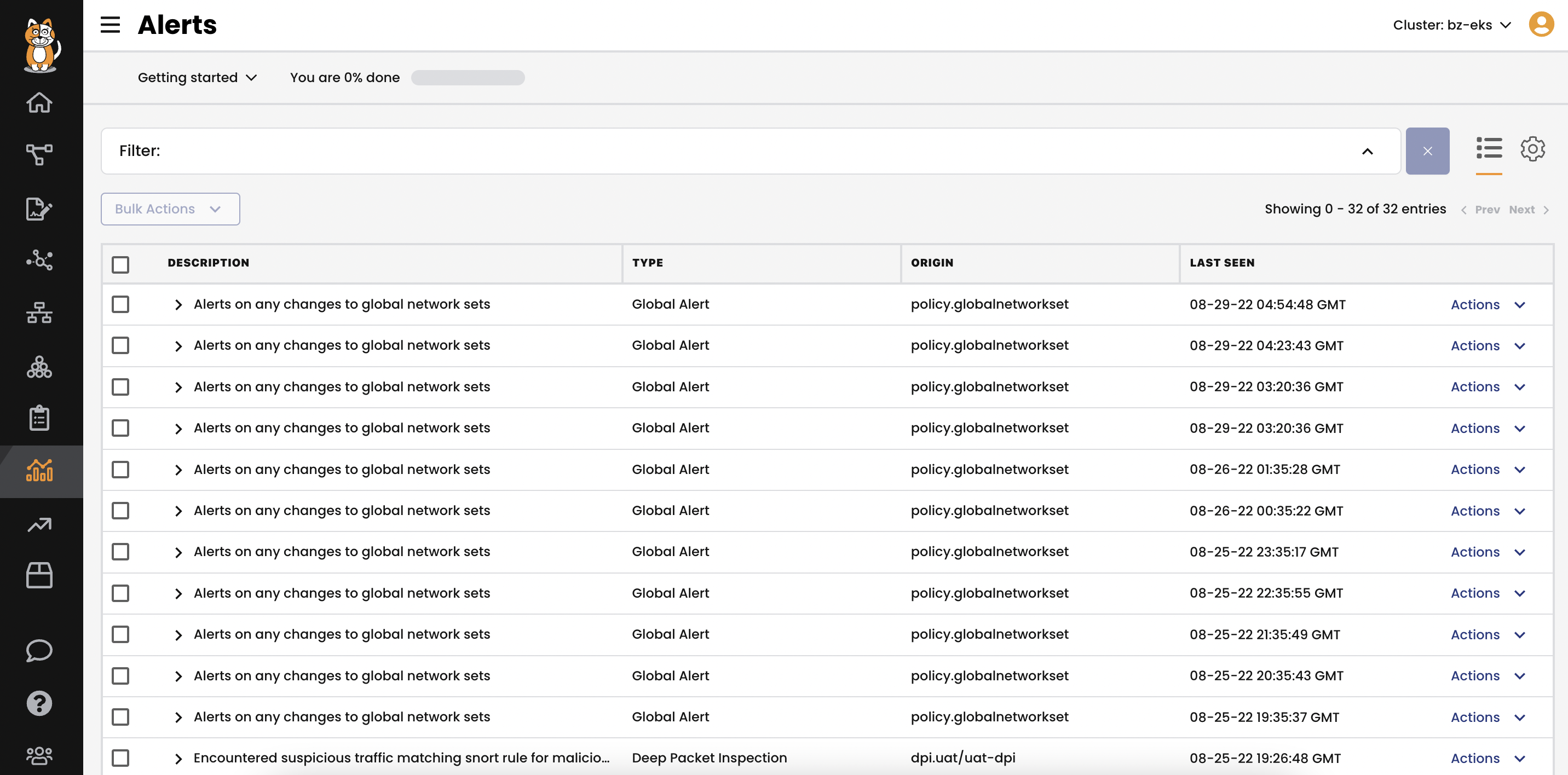
Monitoring and Alerting
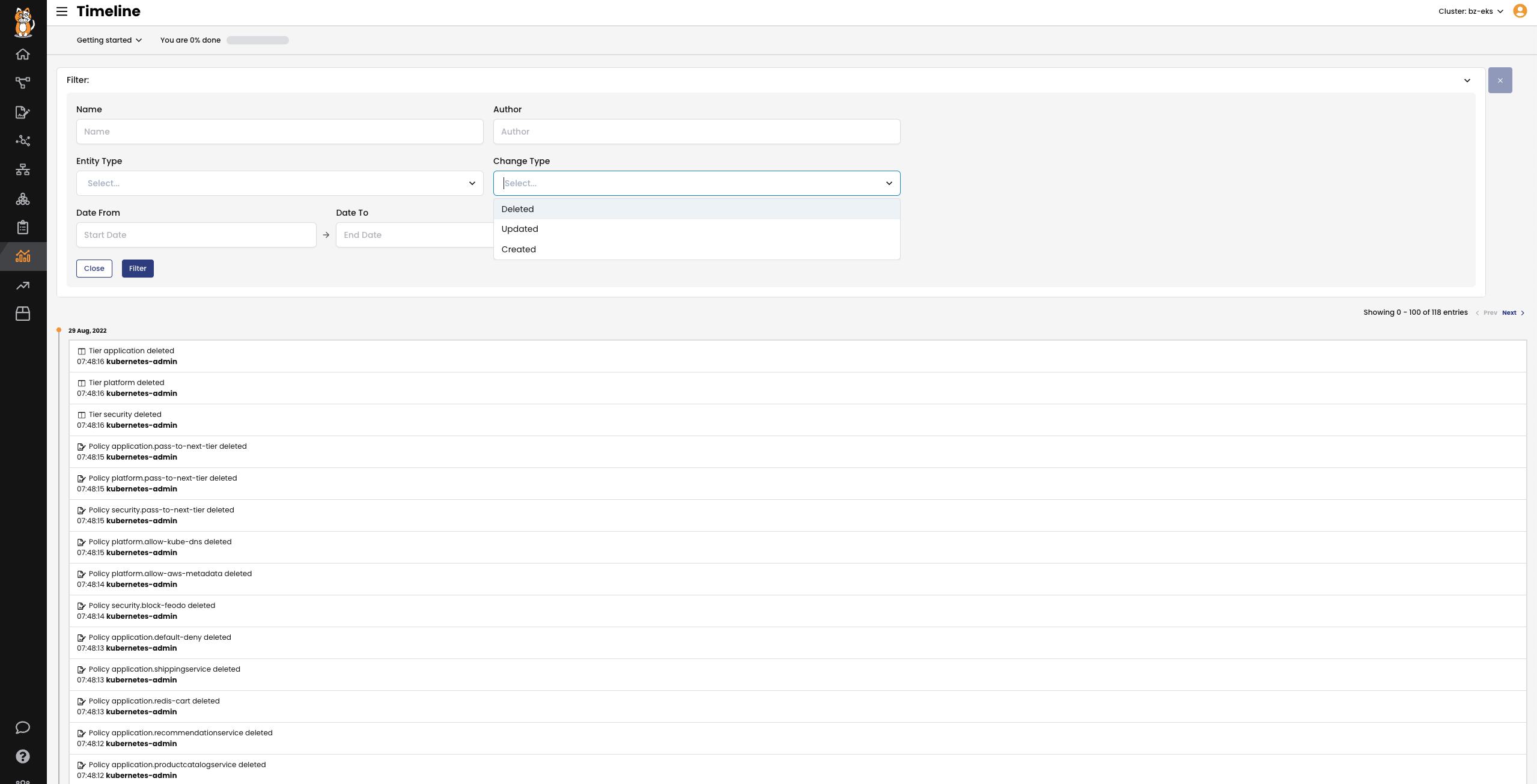
How would you know if someone changed your security policies? Calico monitors and logs all changes to policies, including the version history.
When a policy that implements your security controls changes, you will be alerted of the change. The change history shows exactly what changed and is the first step in providing security forensics that provide a record identifying what happened and how.
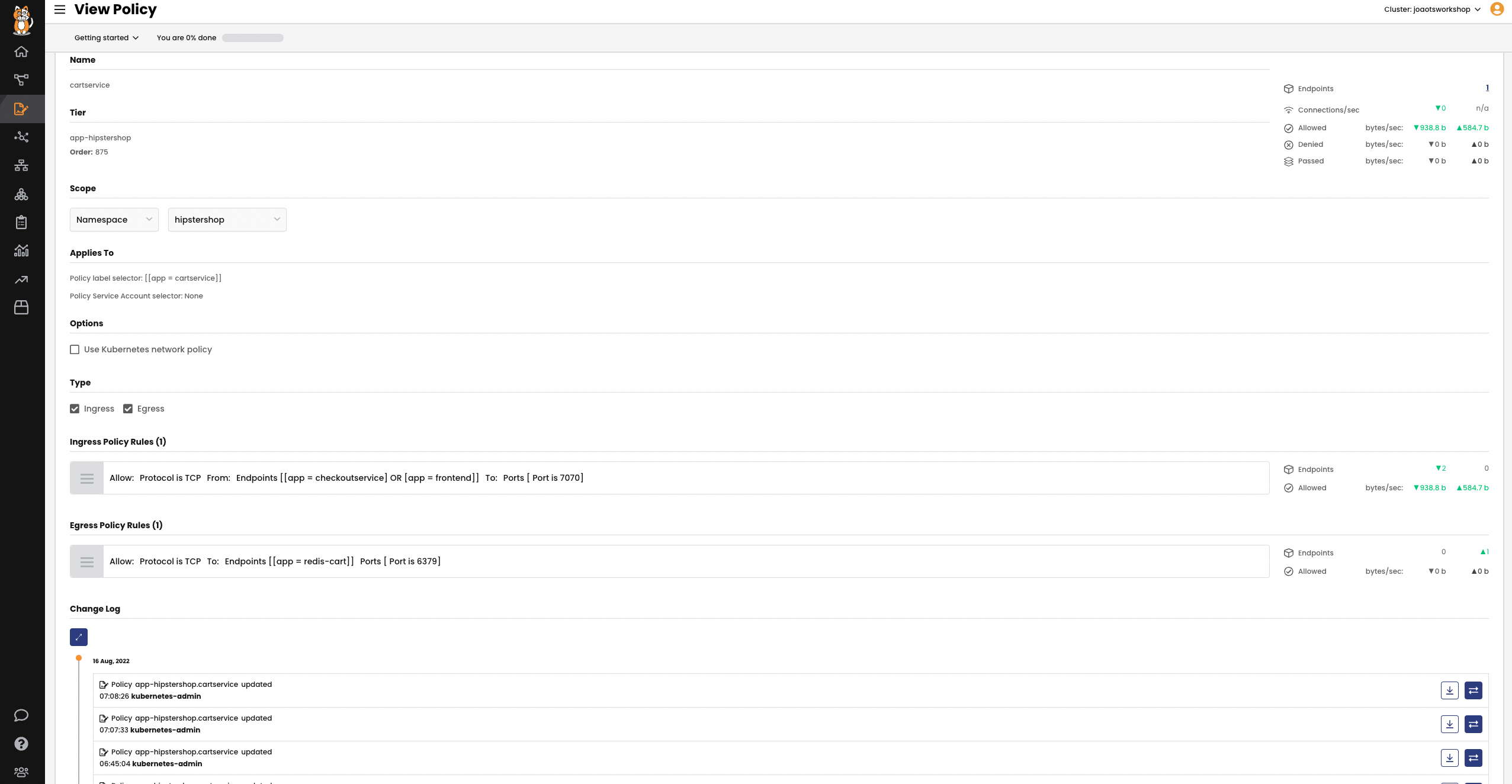
Policy View
When the security team asks to see the corporate security controls you implemented, showing them YAML files is not going to work. Calico includes a web-based GUI that visually describes the security controls in place in an easy-to-understand policy view.
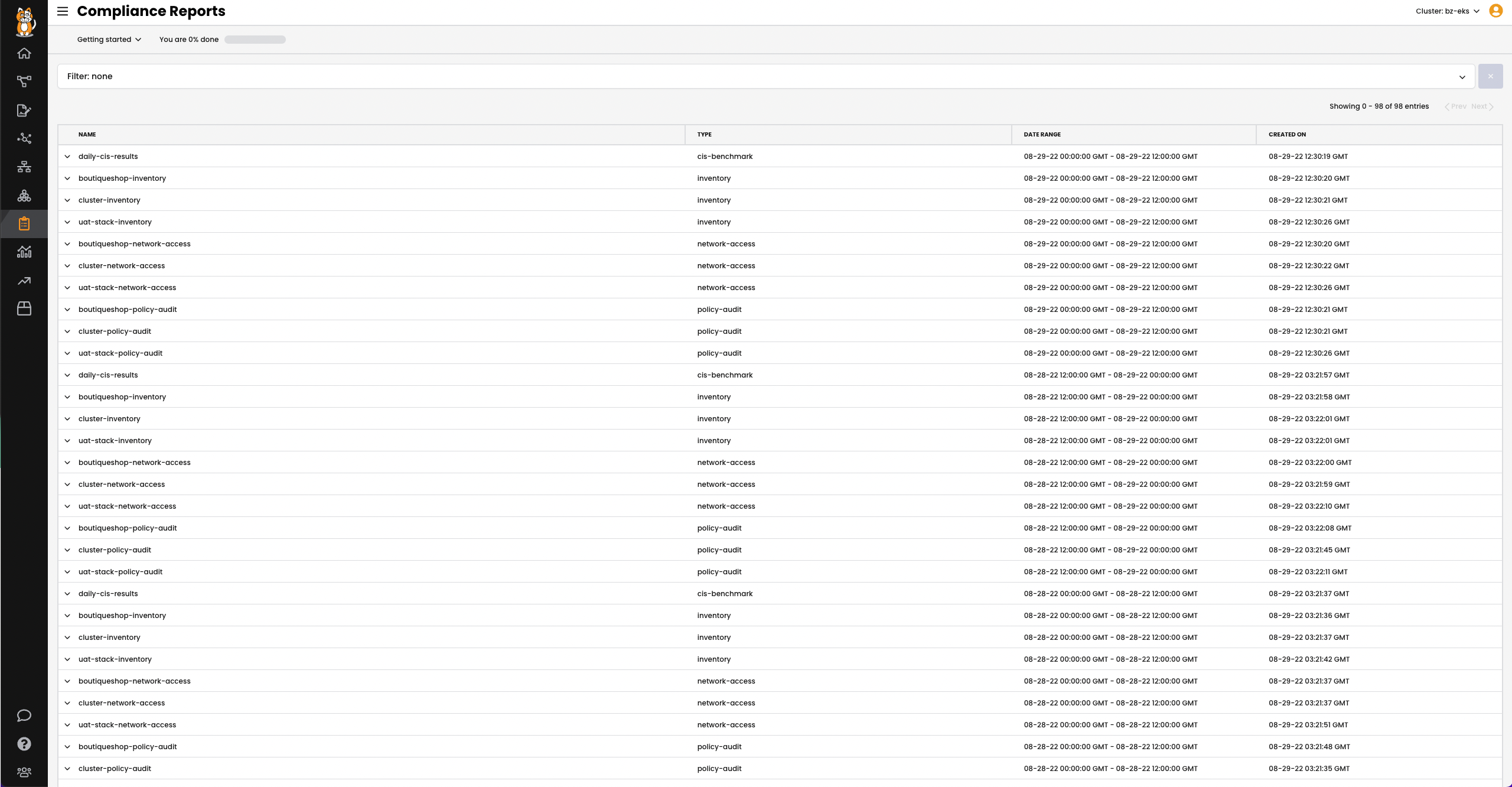
Compliance Reports
The next thing the security team will want to know is which workloads are covered by the security controls and which ones are not? Compliance reports show all workloads that are in-scope and out-of-scope with your policy.
Audit
Finally, the security team will need to ensure that the policies haven’t been tampered with.
For example, a policy may have recently changed for two hours, allowing the controls to be violated. Calico tracks all changes to policies and maintains a version history of those changes. With all of this in place, you should be able to ace your next security audit!