Security Information and Event Management (SIEM) is essential for enterprise organizations because it provides the tools and capabilities needed to effectively monitor, detect, respond to, and mitigate cybersecurity threats, while also supporting compliance and overall security strategy enhancement.
Why is it crucial to centralize EKS logs in a SIEM?
Due to the unique challenges and complexities presented by containerized and orchestrated infrastructures like Kubernetes, the importance of SIEM for Kubernetes environments is significant and between the key factors we can highlight:
- Anomaly Detection – SIEM solutions equipped with advanced analytics can detect anomalies and unusual behaviors within the Kubernetes ecosystem. This is essential for identifying potential security breaches, unauthorized access, or malicious activities that might otherwise go unnoticed.
- Configuration Management – Misconfigurations in Kubernetes settings can lead to security vulnerabilities. SIEM can monitor Kubernetes configuration changes and alert administrators to any deviations from best practices or security policies.
- Container Security – Containers within Kubernetes can introduce security challenges. SIEM helps monitor container activities, such as image vulnerabilities, runtime behavior, and interactions between containers, helping to ensure that containers are free from vulnerabilities and following security guidelines.
- Multi-Cluster Management – Enterprises often manage multiple Kubernetes clusters. SIEM enables consistent monitoring and security management across these clusters, ensuring that security measures are uniformly applied.
- Integration with Other Security Tools – SIEM can integrate with other security tools like intrusion detection systems (IDS), intrusion prevention systems (IPS), and vulnerability scanners. This integration provides a holistic view of security events and enhances the organization’s ability to respond effectively.
- Automated Responses – Some SIEM solutions support automated responses to security events. In Kubernetes environments, this could involve triggering actions like scaling down or isolating compromised containers, limiting the potential impact of an attack.
- Adapting to Dynamic Environments – Kubernetes environments are highly dynamic, with containers and pods being created and terminated frequently. SIEM tools are designed to handle such dynamic environments and can provide real-time insights into the changing security landscape.
Calico Cloud and SIEM integration helps logging containers and Kubernetes data for a longer period of time for compliance, monitoring and troubleshooting purposes as following:
- Audit and Compliance – Keep the audit logs of the changes from an Amazon EKS Cluster for the time range required by auditors and compliance framework. In some cases like financial institutions the period can reach up to 12 years.
- Integration with other tools – After shipping the logs for an SIEM, it can be integrated with other tools to automate actions and/or trigger custom alerts based on the logs occurrences.
- Forensic analysis – In case of an unsuccessful or successful attack, the logs from the compromised Pods and changes will be available as long as the investigation is needed.
- Log centralization – All logs can be centralized in one SIEM solution hence it simplifies the integration with other tools and makes it easier to cross information during some investigation.
Related guide: EKS security
Exporting Calico Cloud logs for a SIEM
Calico Cloud supports exporting archive logs for three kinds of SIEM:
- Syslog – Logs flow, dns, idsevents, audit
- Amazon S3 Bucket – Logs l7, flow, dns, runtime, audit
- Splunk – Logs flow, audit, dns
The logs are sent by Calico from the K8S/EKS nodes to the SIEM and this communication can optionally be encrypted and, in some cases, encryption is required. Also, it is possible to authenticate the connection using Amazon S3 Bucket or Splunk.
For more information, check our documentation.
In this blog, I will explain how you can integrate Calico logs with your Syslog.
Setting up a Syslog server
As mentioned before Calico Cloud can ship the logs for different destinations/SIEMs, however, for the purpose of this article it will be configured to export the logs to a Syslog Server.
For that, just apply the manifest below in order to update the “tigera-secure” “LogCollector” resource by defining the Syslog IP and also which kind of logs will be sent.
kubectl apply -f - <<EOF
apiVersion: operator.tigera.io/v1
kind: LogCollector
metadata:
name: tigera-secure
spec:
additionalStores:
syslog:
# (Required) Syslog endpoint, in the format protocol://host:port
endpoint: tcp://<SYSLOG_IP>:514
# (Optional) If messages are being truncated set this field
packetSize: 1024
# (Required) Types of logs to forward to Syslog (must specify at least one option)
logTypes:
- Audit
- DNS
- Flows
EOF
The Syslog IP must be replaced for the <SYSLOG_IP> in this manifest and then, apply it. This manifest is configured to ship the Audit, DNS and Flow logs hence it can be stored for how long is needed and can be integrated with other tools to trigger actions/alerts based on the logs entries.
Monitor the LogCollector resource until get available through the command below:
kubectl get tigerastatuses.operator.tigera.io log-collector NAME AVAILABLE PROGRESSING DEGRADED SINCE log-collector True False False 9m48s
After getting the LogCollector available as above, check the Syslog server to see if it is ingesting the logs from the Calico Cloud cluster.
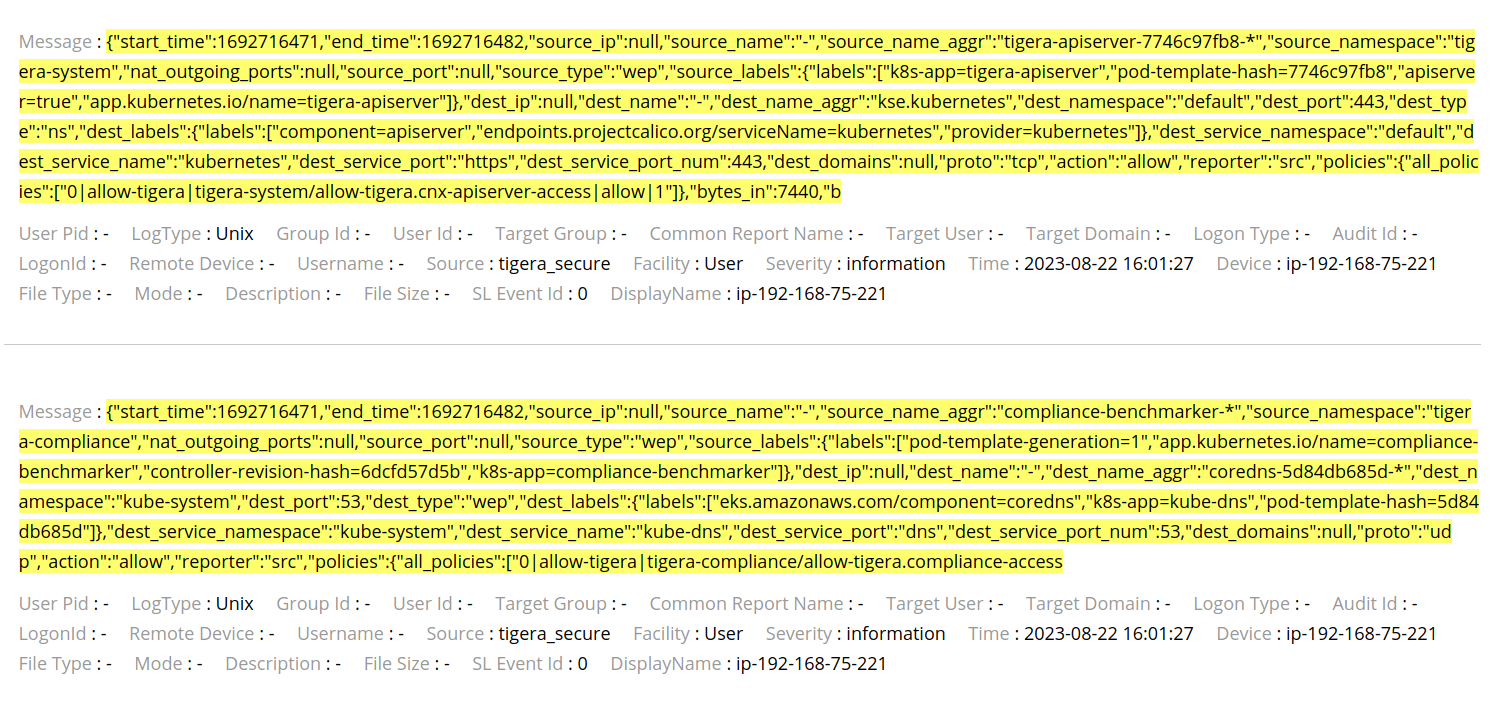
The Flow logs can be seen in the image below:
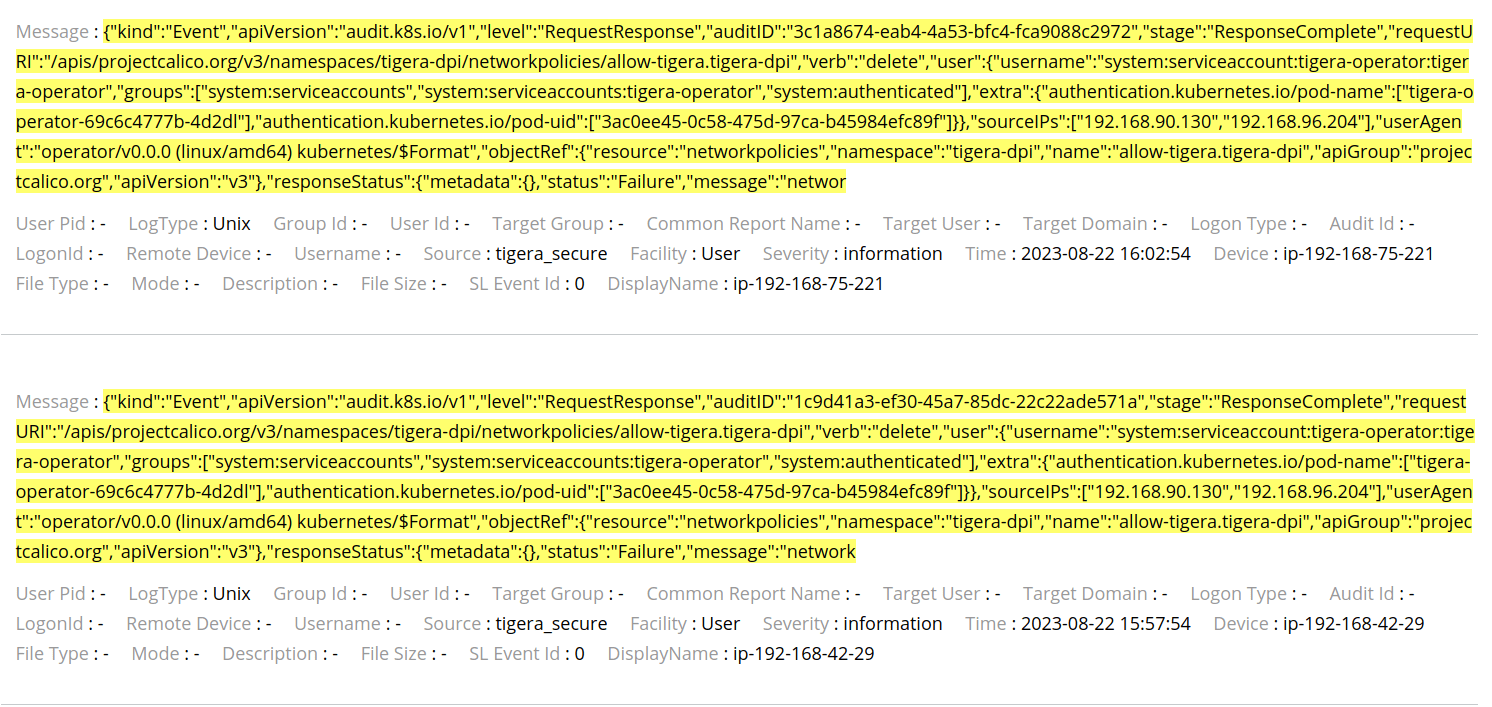
The Audit Logs can be seen in the image below:
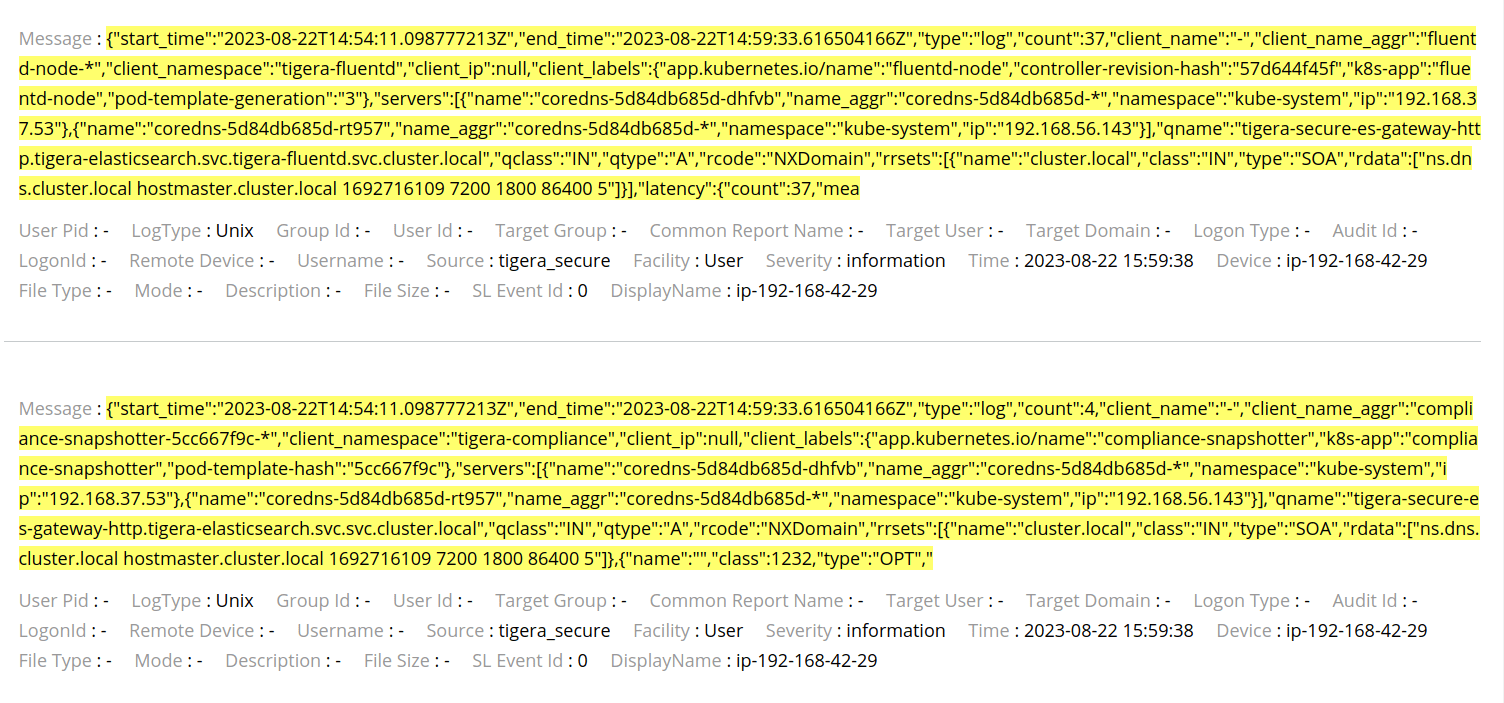
The DNS Logs can be seen in the image below:
Note that the Source is “tigera_secure” and the Device is the EKS node which sent the log, this way, the logs can be filtered in the queries and make it easy to find what is looking for.
Conclusion
Calico Cloud integrates with popular SIEMs to save log data. This ensures that not only can logs be kept for a longer period for satisfying the compliance and audit requirements but also leveraging the SIEM capabilities to analyze log data and provide automated incident responses and perform forensic analysis.
Ready to get started? Try Calico Cloud for free.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!