Calico Cloud is the industry’s only container security platform with built-in network security to prevent, detect, and mitigate security breaches across multi-cloud and hybrid deployments. Calico Cloud is built on Calico Open Source, the most widely adopted container networking and security solution.
As a fully managed, pay-as-you-go SaaS security solution, users only pay for services consumed—getting immediate value without upfront investment.
Secures containers, microservices, namespaces, and workloads at build and deploy time with image assurance, a runtime view of vulnerable images, an admission controller, and security policy.
Helps both security and DevOps teams maintain and improve the security posture of their cluster and meet compliance requirements mandated by regulations including PCI DSS, SOC 2, HIPAA, GDPR, FIPS, and custom frameworks.
Provides audit reports on a scheduled or on-demand basis to demonstrate proof of compliance.
Implement egress-based workload access controls for traffic to and from individual pods to external endpoints on a per-pod basis to protect your Kubernetes cluster. Author DNS policies that implement fine-grained access controls between a workload and the external services it needs to connect to, like Amazon RDS, ElasticCache, and more.
Limit the blast radius when a security breach results in an APT (advanced persistent threat) with identity-aware microsegmentation for both container and VM workloads. Use a single policy framework and Kubernetes declarative model to set controls at the host, container/VM, and application levels.
Extend the use of existing firewalls and SIEMs to your Kubernetes environment with out-of-the-box firewall and SIEM integrations.
Calico Cloud protects your workloads at runtime from both known and zero-day threats.
Calico Cloud has built-in probes that collect workload activity data across network traffic, file system, processes, sys calls, binaries, and more. The threat defense engine compares data from these probes, in near real time, with known malicious attacks. It uses machine learning to create a behavioral baseline of the workload in addition to Tigera’s own curated ruleset based on historical attacks, to provide a comprehensive threat defense solution against zero-day threats.
Calico provides workload-level intrusion detection and prevention, deep packet inspection, protection from DDoS attacks, Envoy-based application-level protection, and WAF. Calico Cloud uses AlienVault and custom threat feeds to actively protect your containers from known malware and DGA attacks.
Calico Cloud’s robust and highly performant security policy engine can alert, pause, quarantine, or terminate infected pods within milliseconds in multi-cloud and hybrid environments.
The Policy recommendation monitors your environment and recommends policies based on workload communication patterns for robust security. It also provides namespace isolation for a default-deny approach to minimize surface attack area and enable defense in depth.
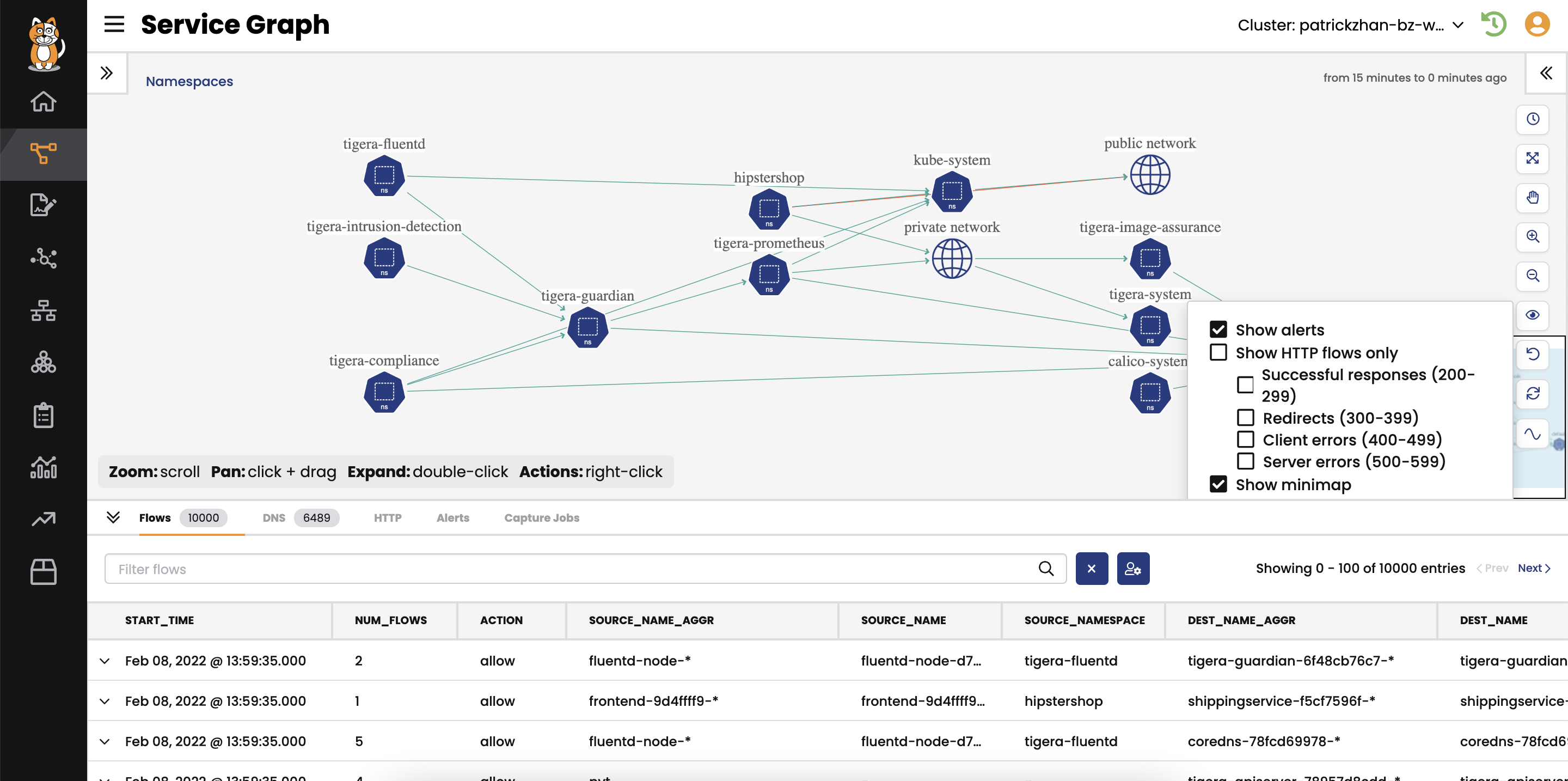
Distributed applications are very difficult to troubleshoot. Calico solves this problem by dynamically generating a Dynamic Service and Threat Graph, as well as providing a built-in, UI-driven troubleshooting tool that enables easy monitoring and troubleshooting for microservices.
The Dynamic Service and Threat Graph provides a rich set of information with Kubernetes context, including across which namespaces workloads are communicating, detailed DNS information, detailed logs for every flow in your cluster, and how security policies are being evaluated.
Dynamic Packet Capture is a self-service, on-demand tool for capturing and evaluating traffic for a specific pod or collection of pods based on secure user access. It allows you to monitor how microservices are behaving and interacting with each other at runtime.
Calico Cloud provides a single pane of glass to ensure consistent application of security controls across both containers and VMs in heterogeneous environments. Unified controls reduce the complexity for DevOps teams running the clusters by supporting self-service security and CI/CD integration. Using “Security as code,” Calico Cloud fully automates the cluster-wide, end-to-end policy deployment process including any necessary security changes. Built on Calico Open Source, the most widely adopted networking and security solution for containers and Kubernetes, Calico Cloud also supports third-party CNIs including EKS VPC, Azure CNI, and GKE to expand your choice of public cloud providers.
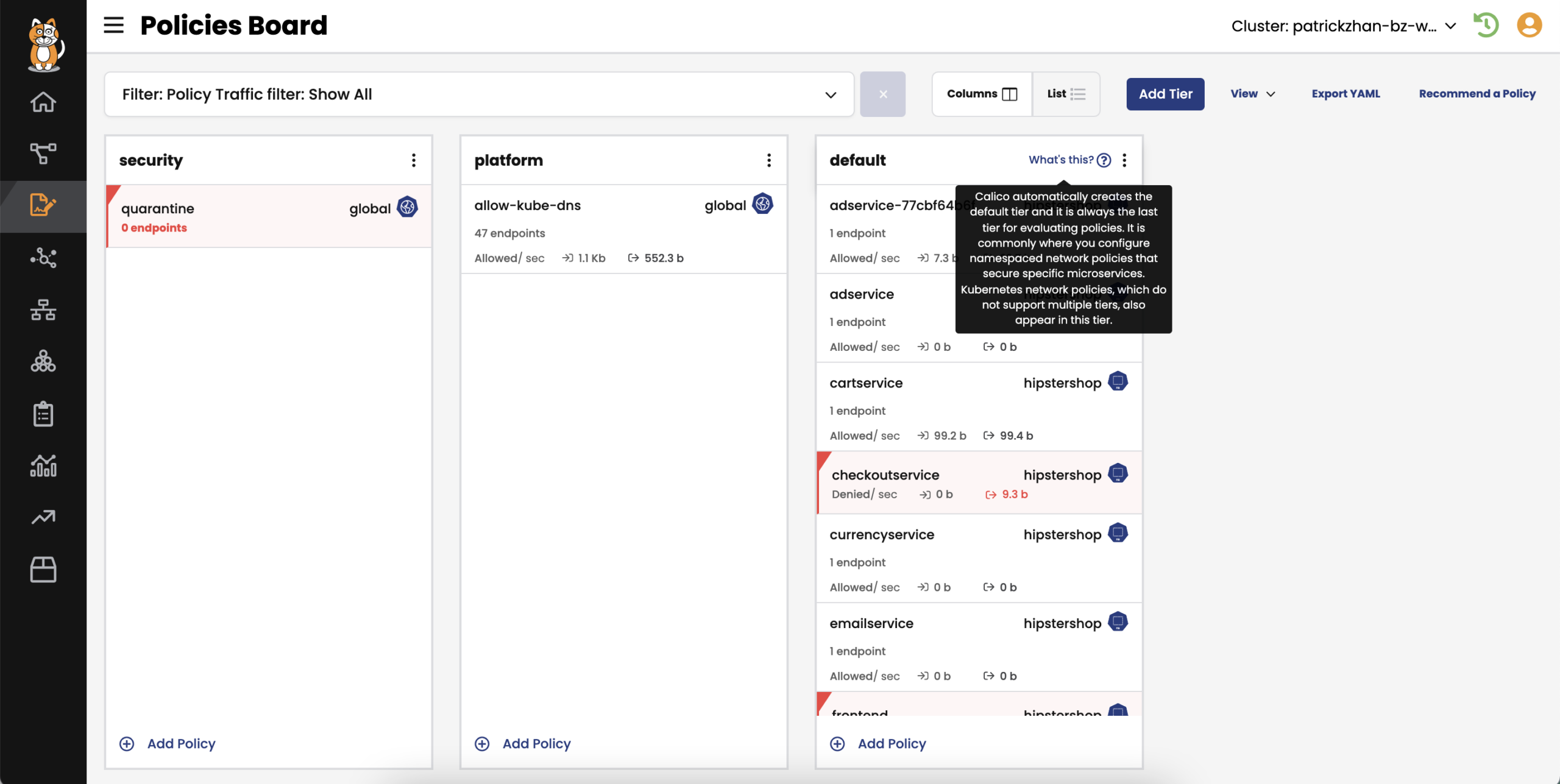
Developers, DevOps teams, and SREs want to follow a simple workflow and generate security policies with minimal effort in their code. Calico Cloud allows them to create their own security policies within their tiers and customize permissions based on organizational structure.
Calico ensures the policies in the left-most tiers are given precedence over the right. Tiers are a Kubernetes object, so you can control who can view/modify policies in specific tiers. Every change of record to tiers and policies is captured, enabling you or auditors to go back in time for review or troubleshooting purposes.
See active build, deploy and runtime security in action for any distribution across public cloud providers.
Additional Resources:

Microsegmentation represents a transformative approach to enhancing network security within Kubernetes environments. This technique divides networks into smaller, isolated segments, allowing for granular control over traffic flow and significantly bolstering...
Read more >
The use of Amazon EKS is becoming more prevalent in the healthcare sector for their healthcare application modernization. To ensure compliance with HIPAA’s privacy regulations, DevOps, SREs, and platform teams...
Watch here >
Attend this in-depth, hands-on security workshop with Calico and Amazon AWS experts to get insights into Kubernetes cluster traffic, workload interactions, and security policy enforcement. The 90-minute interactive lab comes...
Register here >