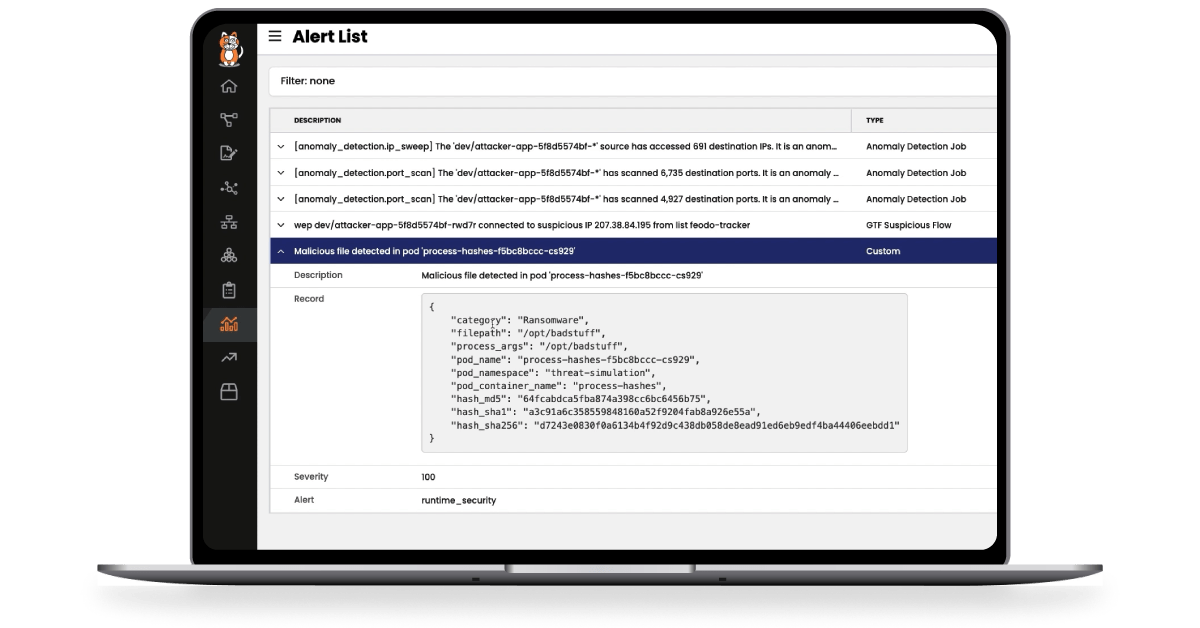
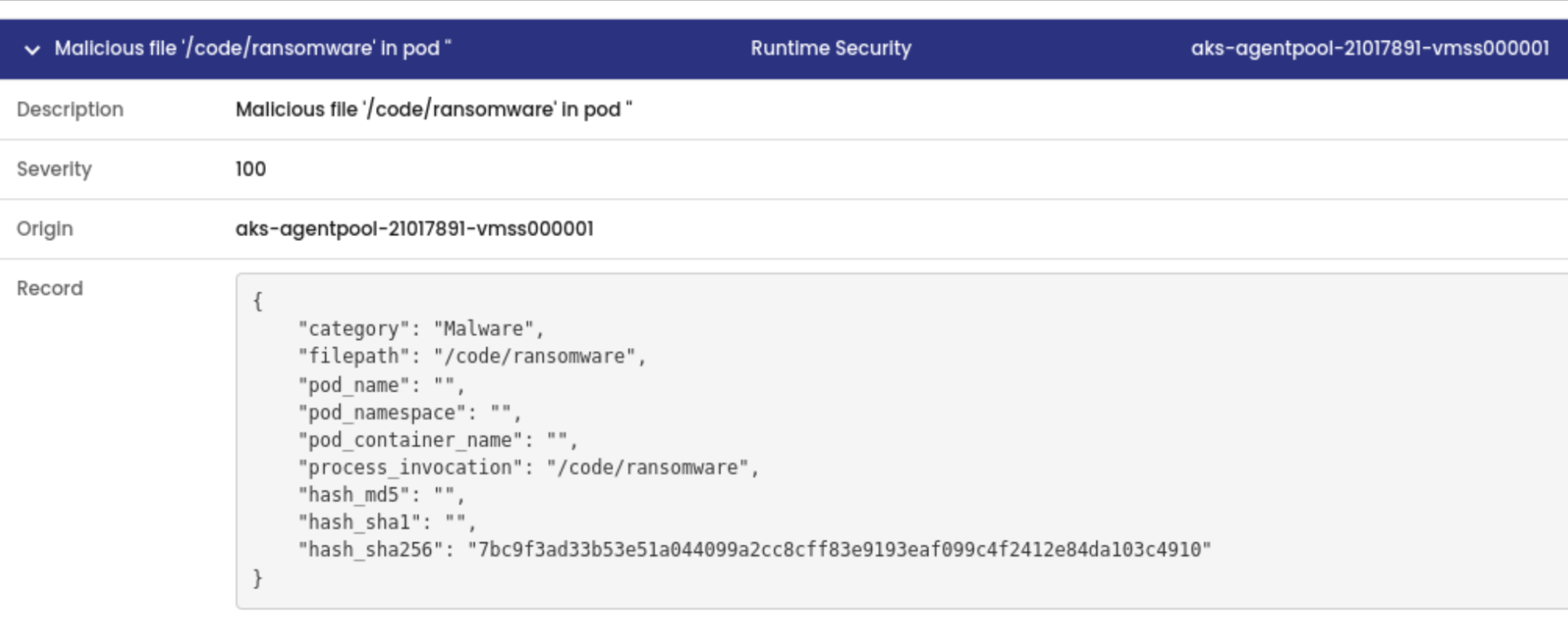
Detect known malware by comparing process file hashes with known malware signatures.
Detect zero-day threats with out-of-the-box detectors that use advanced eBPF probes to collect data and analyze suspicious behavior across processes, file systems, and system calls. New detectors are continuously rolled out as threats emerge.