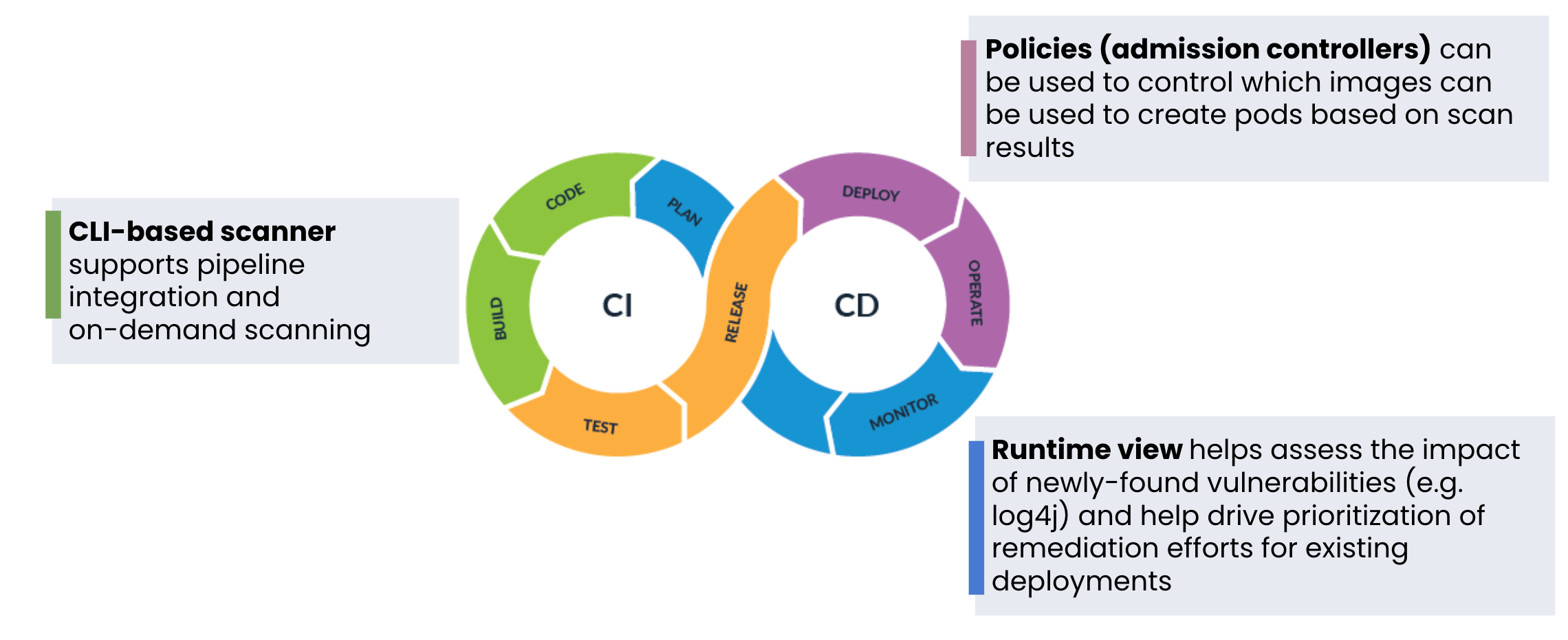
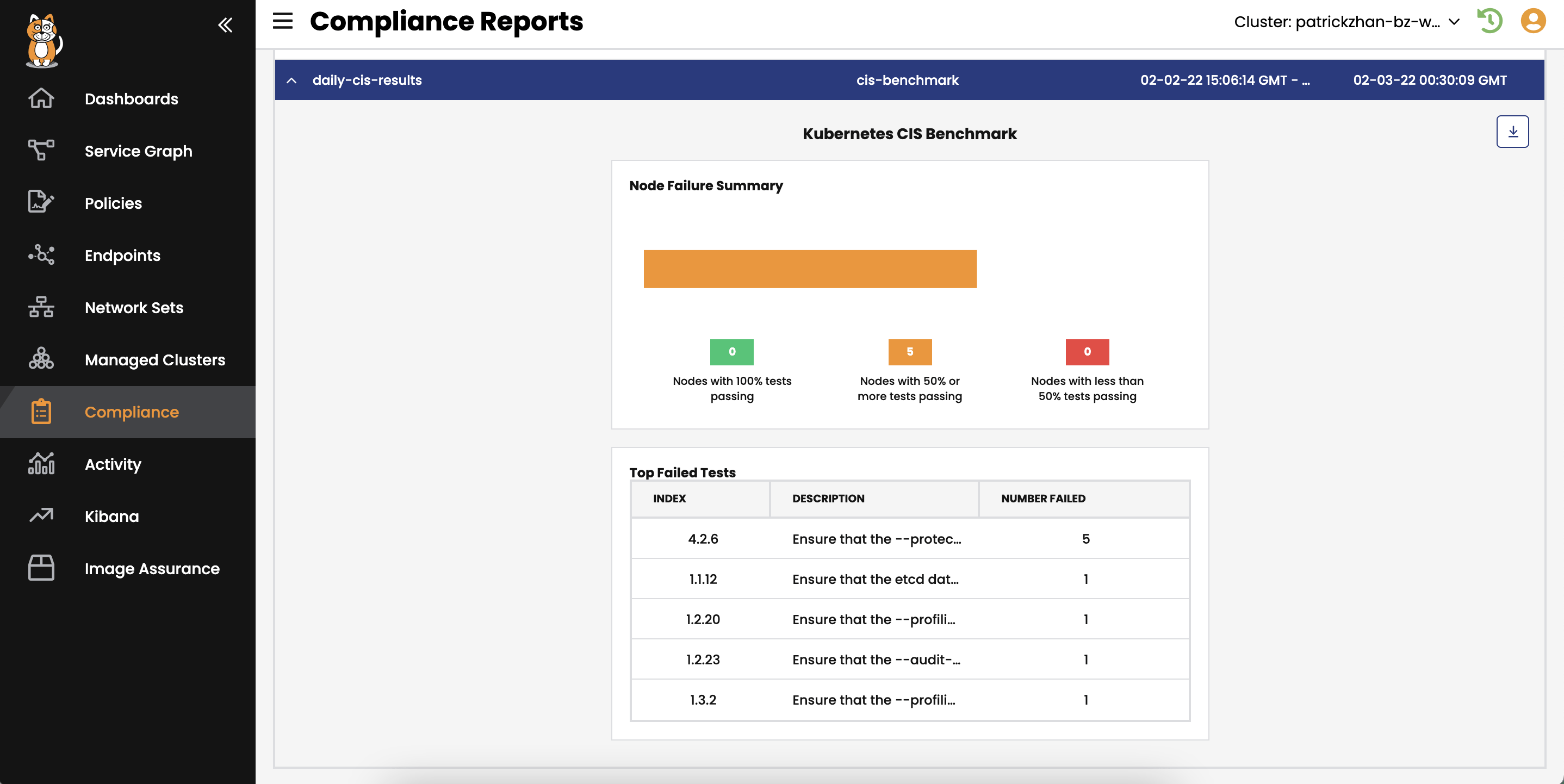
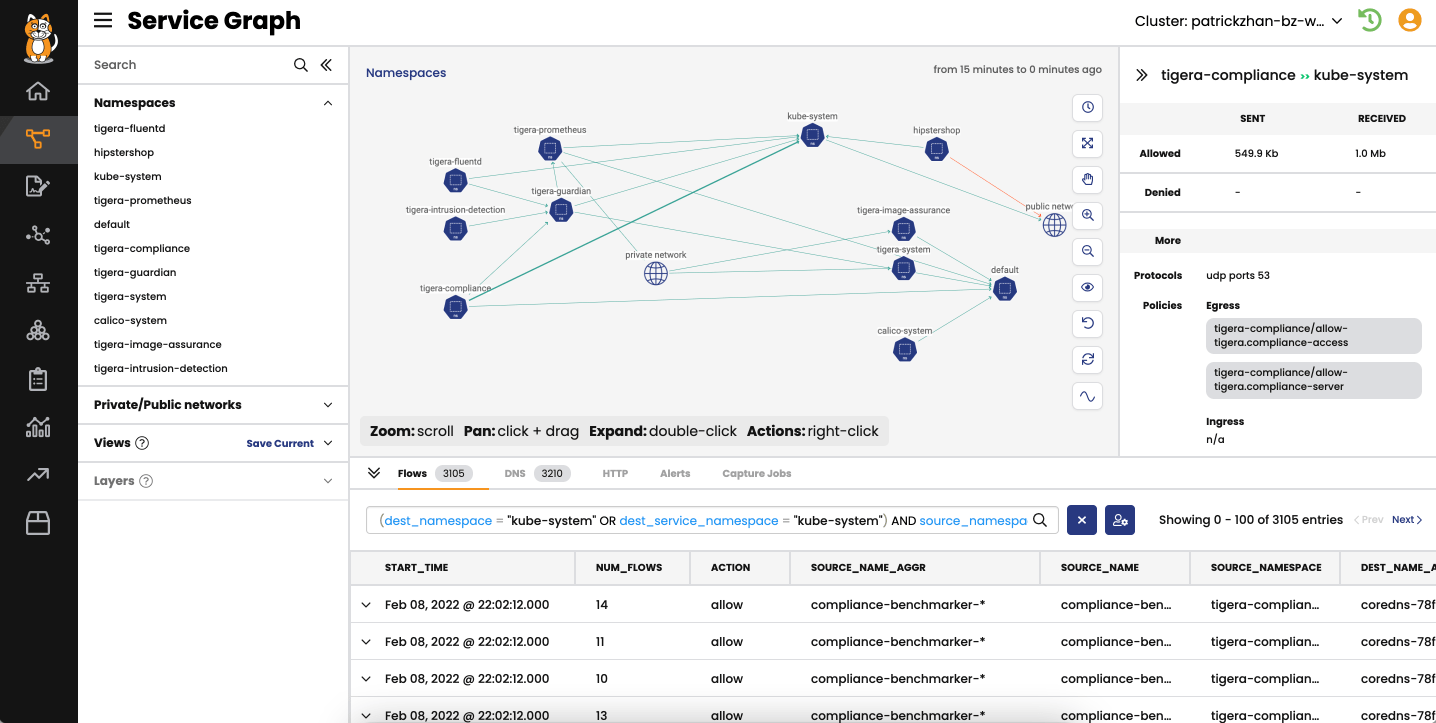
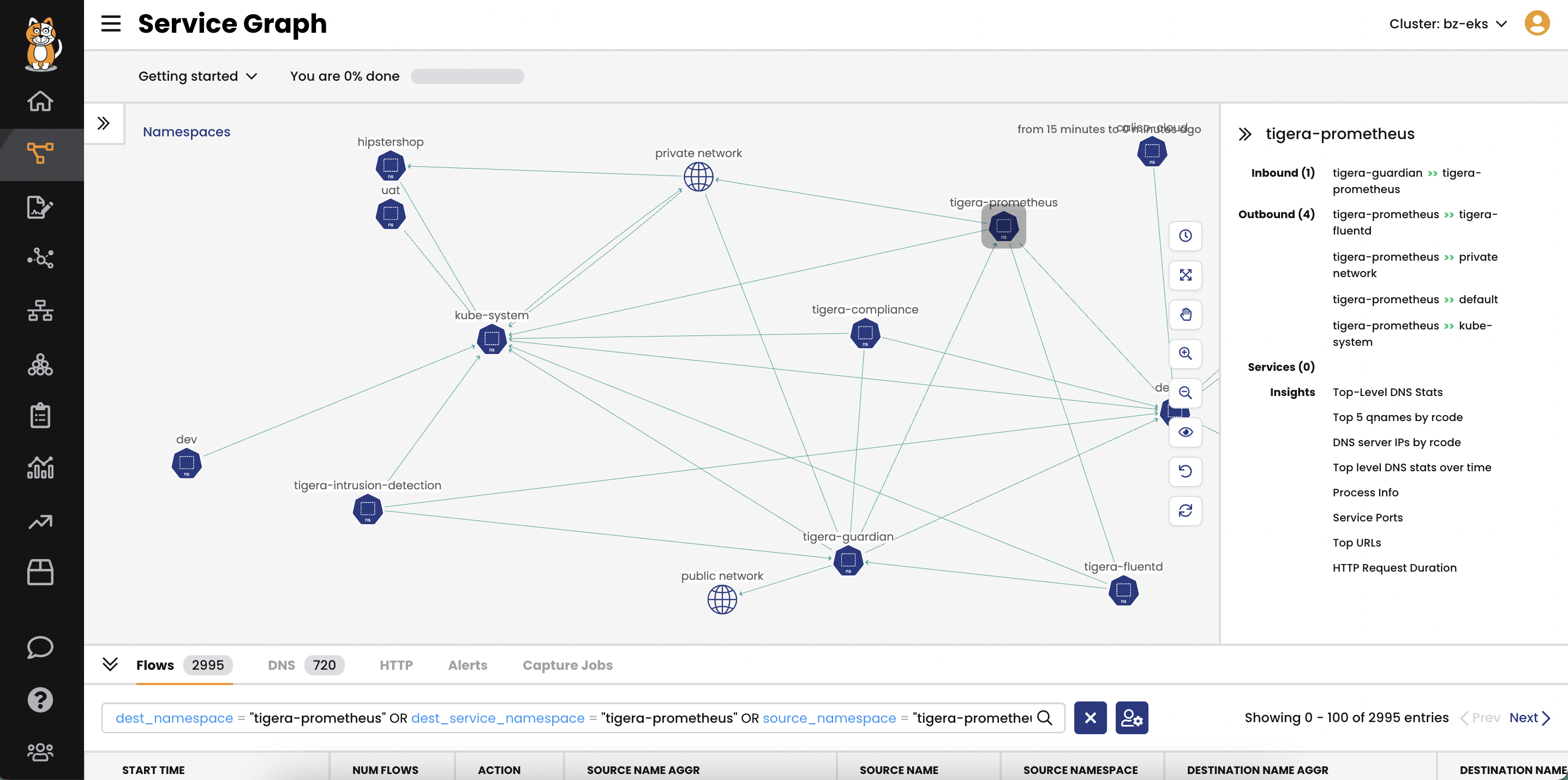
Automated and fully integrated CI/CD pipeline security. Continuously scan first- and third-party images for known CVEs and prevent vulnerable workloads from being deployed.
Runtime view of vulnerable workloads to assess risks and deploy mitigating security controls to minimize blast radius.