In the vast digital landscape, the flow of data across networks is akin to water coursing through a city’s plumbing system. Just as impurities in water can signal potential issues, deviations in network traffic, termed as network inserted anomalies, can hint at cyber threats. These anomalies range from overt signs like unauthorized access attempts to subtler indicators like unusual data transfer patterns. Given the complexity of today’s containerized environments, security platforms like Calico have become indispensable in detecting and addressing these anomalies, ensuring the security of Kubernetes clusters and containerized workloads in them.
The Landscape of Network Threats in Kubernetes
Kubernetes has revolutionized application deployment and scaling. Its dynamic nature, characterized by transient pods and inter-cluster communication, offers unmatched agility. However, this fluidity also introduces unique network security challenges. Threat actors continuously devise methods to exploit these gaps, leading to potential threats like inter-pod traffic exploits, ingress and egress attacks, service discovery abuse, and misconfigurations. Navigating this intricate landscape necessitates advanced tools, and Calico stands out, offering solutions tailored for Kubernetes environments.
Understanding Anomalies: What Constitutes an Anomaly?
Let’s understand what is an anomaly. An anomaly is a deviation from the “normal” network behavior. Establishing a clear baseline of typical network activity is crucial. Note that each cluster and workloads in it are unique and need their own baseline. This involves monitoring patterns, frequency, and volume of network traffic. Common anomalies include sudden traffic spikes, unauthorized access, unexpected protocol usage, and behavioral deviations. Tools employing machine learning can adaptively learn and refine this baseline, ensuring effective anomaly detection.
Leveraging Anomaly Detection for Network-Based Threats
Any security platform should provide following actionable insights when providing anomaly detection for Kubernetes environment:
- Real-time Monitoring: Continuous observation to instantly flag deviations.
- Advanced Machine Learning: Algorithms that adaptively learn network behavior.
- Customizable Alerting: Tailored alerts for pertinent anomalies.
- Visualizations and Dashboards: Graphical representations for trend spotting.
- SIEM System Integration: Centralized analysis and correlation of security events.
How Calico Provides Anomaly Detection for Network-Based Threats
Calico Cloud provides both signature-based and behavior-based network threat detection for Kubernetes environments.
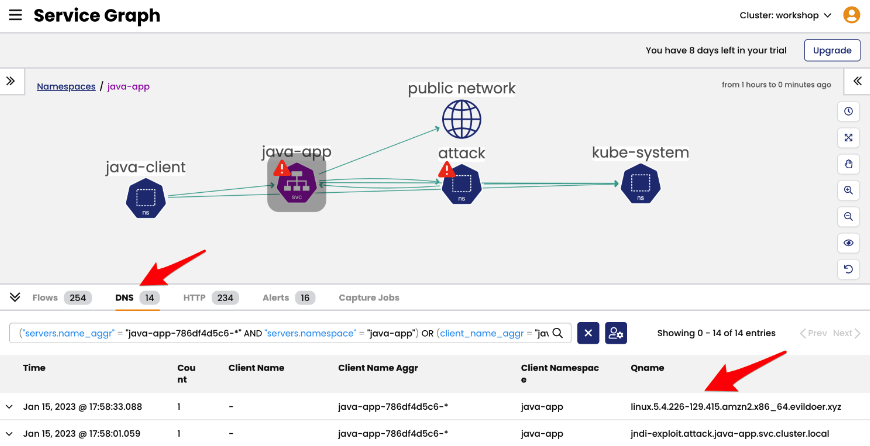
Dynamic Service and Threat Graph
A visualization tool highlighting detected anomalies, aiding users in identifying suspicious traffic sources.
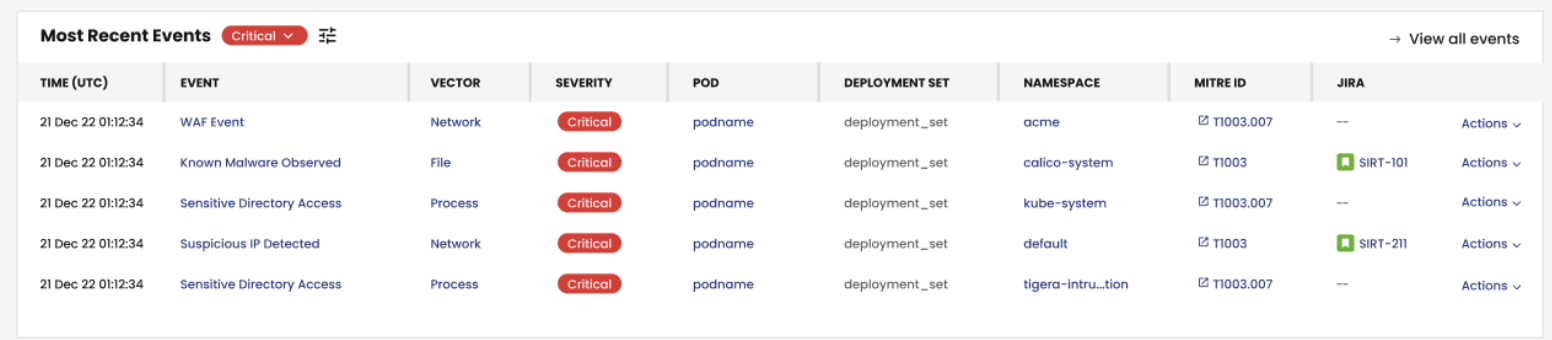
Security Events
A centralized dashboard displaying DPI-generated alerts.
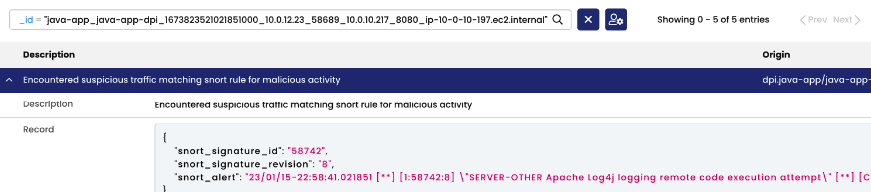
Deep Packet Inspection (DPI)
DPI examines both the header and payload of data packets. This in-depth inspection is pivotal for detecting malicious payloads and unauthorized data transfers. DPI can be enabled for specific services, optimizing resource usage without the need for sidecar containers.
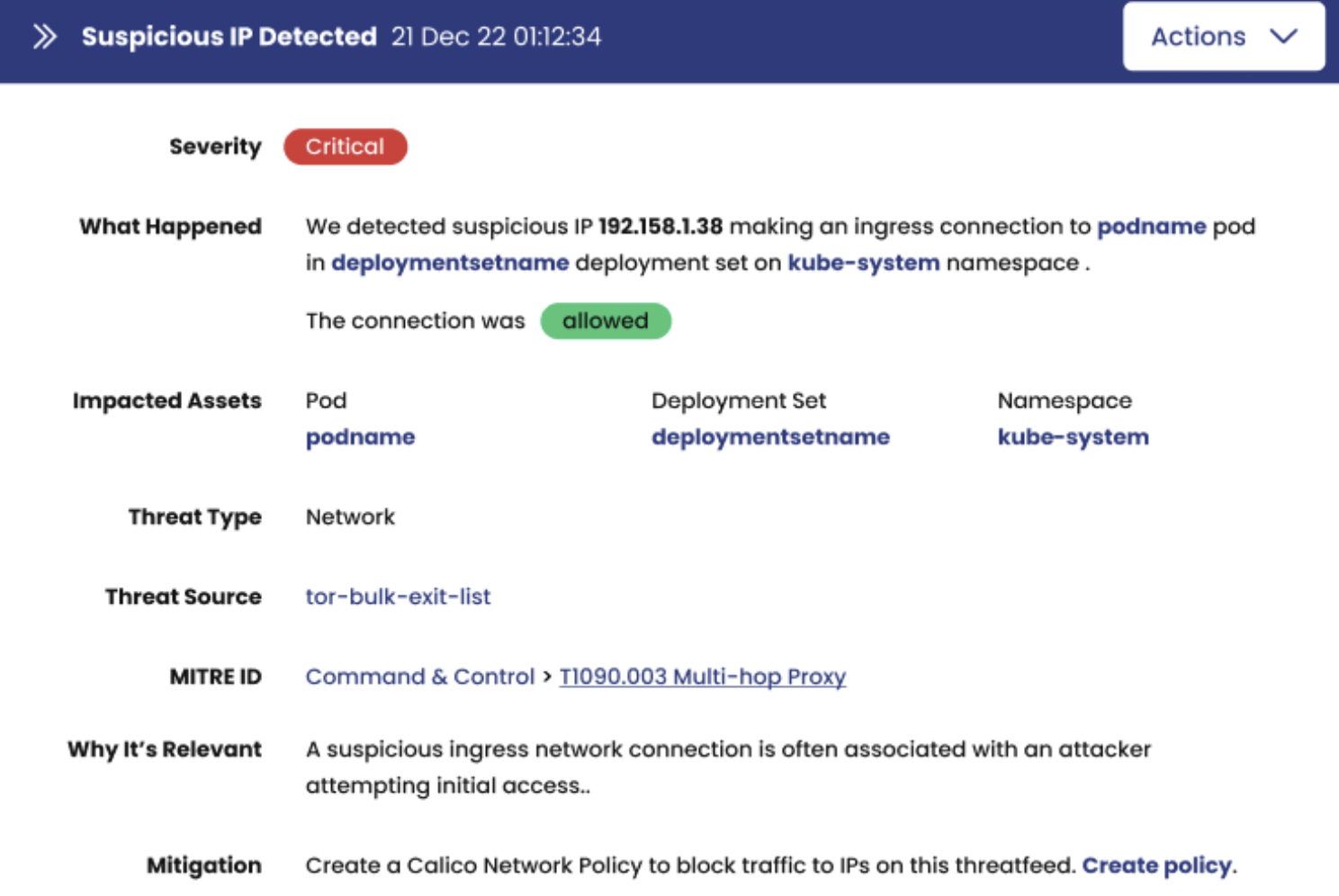
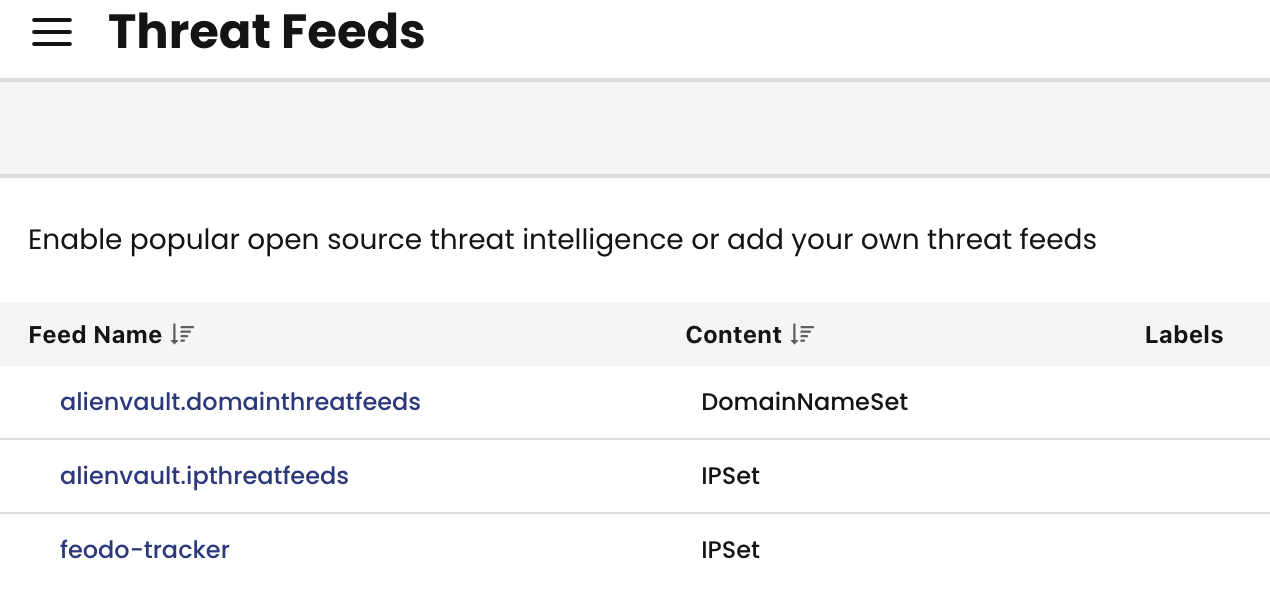
Global Threat Feeds
Staying Ahead of Threat Actors
Real-time threat intelligence is vital in today’s cybersecurity landscape. Calico integrates the Feodo Tracker from abuse.ch, providing a list of IP addresses linked to botnet command and control servers. Additionally, users can integrate custom threat feeds, allowing them to tailor their threat intelligence sources for comprehensive defense.
The Power of Behavior-Based Detection
While signature-based detection is essential, it’s often inadequate against novel threats. Behavior-based detection offers a dynamic approach to identify potential threats by understanding and flagging deviations from typical network activity. Calico’s continuous monitoring and baseline establishment enable the detection of anomalies like unusual access patterns, protocol deviations, and unexpected data transfers.
Responding to Anomalies: Mitigation and Prevention
Effective anomaly response is pivotal. Calico facilitates rapid response and mitigation through:
- Dynamic Network Policies – Swift implementation or adjustment of policies to contain threats.
- Visual Alerting – Intuitive dashboard alerts for quick threat pinpointing.
- Incident Response Platform Integration – Ensuring swift action through established response pathways. Calico also emphasizes prevention, continuously updating its threat intelligence and refining its detection algorithms.
Conclusion
Calico stands as a holistic solution in Kubernetes security. By integrating advanced techniques like DPI, real-time Global Threat Feeds, and behavior-based detection, it offers a formidable defense mechanism. Its proactive approach to anomaly response, emphasizing both mitigation and prevention, solidifies its position as an essential tool for organizations. As Kubernetes environments evolve, Calico’s comprehensive security solutions ensure a resilient and efficient digital ecosystem.
Ready to get started? Try Calico Cloud for free.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!