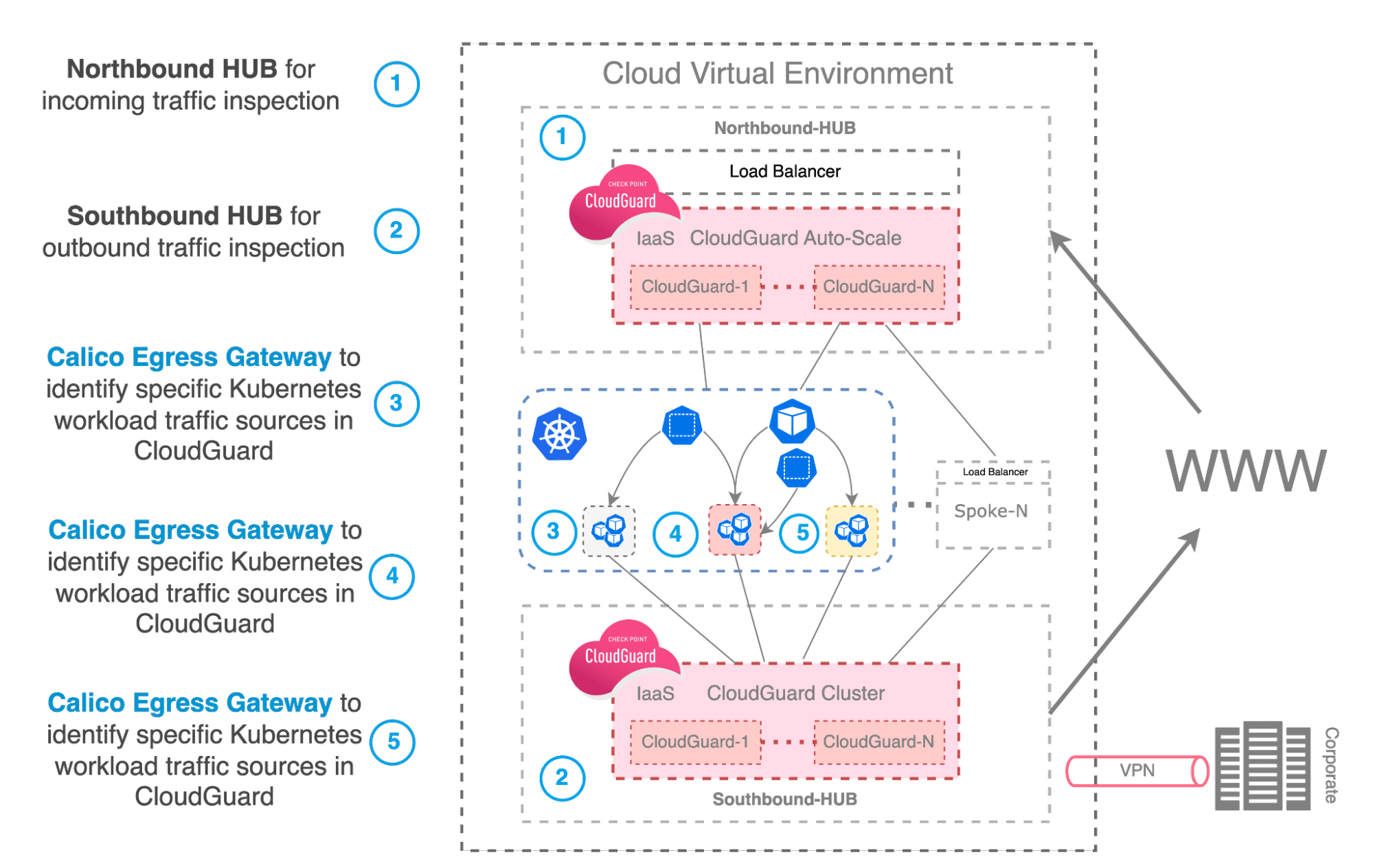
Enterprises implementing containers and Kubernetes in either corporate datacenters or cloud environments typically employ Checkpoint Quantum to secure traffic between their datacenter networks and Checkpoint CloudGuard to safeguard their cloud resources. Often these network security perimeter focused solutions are also used to scrutinize traffic originating from Kubernetes clusters. However, accurately identifying the source of this particular traffic as it traverses through Checkpoint firewalls presents challenges. By default, traffic leaving a Kubernetes cluster is not assigned a meaningful network identity that can be used to associate it with the application and particular workload it came from.
Kubernetes is built to continually scale up and down workloads across different cluster nodes. As a result, platform owners or network security teams often rely on using new IP addresses on the network, or have a source of traffic leaving the cluster appear to originate from the IP address of cluster nodes that are also scaling up and down. In such a scenario, teams have to permit extensive network CIDRs through firewalls in order to adapt to the frequently changing IPs due to ephemeral characteristics of Kubernetes workloads. Constant change is burdensome on platform teams and network security teams usually do not favor or approve of such a suboptimal approach.
Leveraging Calico Egress Gateways with Checkpoint Firewalls for Kubernetes clusters
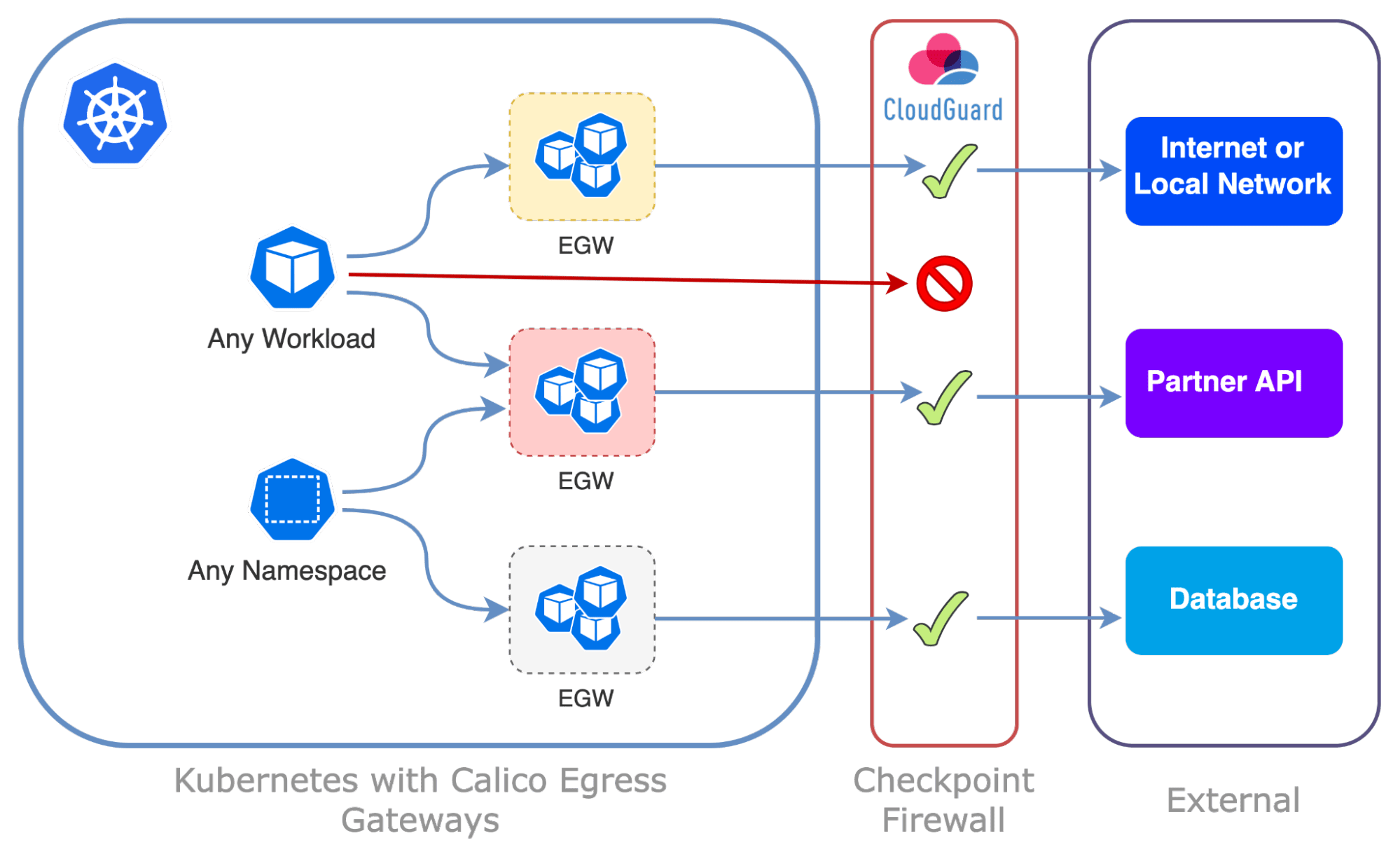
Calico’s Egress Gateways allows you to identify the Kubernetes namespaces and pods associated with egress traffic outside your clusters. This makes it easy to know the traffic source to be inspected by the Checkpoint firewall from a workload perspective. Understanding the source of application traffic at workload-level leaving the Kubernetes cluster and passing through the Checkpoint firewall is crucial for several important reasons:
- Security and Compliance: Identifying the source of outbound traffic helps ensure that only authorized applications and services are communicating with external resources. It allows administrators to enforce proper security measures, preventing unauthorized access and potential data breaches. This understanding is essential for compliance with industry regulations and data protection standards.
- Troubleshooting and Debugging: When an issue arises with outbound traffic, knowing the source allows for quick troubleshooting and debugging. Administrators can pinpoint the exact application, workload, or namespace responsible for the traffic, making it easier to identify and resolve problems efficiently.
- Billing and Cost Management: With accurate information about the sources of egress traffic, organizations can better manage costs and optimize their cloud resources. They can identify which applications, services or workloads contribute to most of the egress traffic and make informed decisions on resource allocation and billing.
Integrating Calico Egress Gateway with Checkpoint Firewall
Calico’s Egress Gateways facilitate integration with Checkpoint Firewalls in both self-managed datacenters and the public cloud. Calico Egress Gateways establish a stable network identity, enabling detailed visibility and thorough inspection of traffic for Kubernetes workloads.
Egress traffic from Kubernetes workloads can be directed through specific Egress Gateways (or none at all), guided by advanced Egress Gateway Policy settings. This configuration creates a distinct network identity suitable for Checkpoint firewall rule settings.
apiVersion: projectcalico.org/v3
kind: EgressGatewayPolicy
metadata:
name: "Southbound-HUB-CheckPoint"
spec:
rules:
- destination:
cidr: 103.47.244.0/24
description: "Gateway to Data Loss Prevention"
gateway:
namespaceSelector: "projectcalico.org/name == 'dlp-service-egw'"
selector: "k8s-app == 'dlp-service-egw'"
- destination:
cidr: 172.16.0.0/24
description: "Gateway to Corporate Mainframe"
gateway:
namespaceSelector: "projectcalico.org/name == 'corp-mainframe-egw'"
selector: "k8s-app == 'corp-mainframe-egw'"
- destination:
cidr: 172.16.99.0/24
description: "Gateway to Corporate Database"
gateway:
namespaceSelector: "projectcalico.org/name == 'corp-database-egw'"
selector: "k8s-app == 'corp-database-egw'"
- destination:
cidr: 10.0.0.0/8
description: "Local: no gateway"
Traffic from workloads exiting the Kubernetes cluster will be directed through designated Egress Gateways, with the routing determined by policies based on the external destination. This approach simplifies the collaborative efforts of platform and security teams in securing Kubernetes environments.
Conclusion
In conclusion, integrating Calico Egress Gateways with Checkpoint Firewalls in Kubernetes environments enhances the monitoring and control of outgoing traffic. This strategy manages the dynamic nature of Kubernetes, allowing network security teams to uphold stringent security requirements without compromising the platform’s scalability or slowing down operations.
Equipping teams with the capability to accurately trace the origin of their egress traffic not only strengthens an organization’s security and compliance stances but also streamlines troubleshooting processes and fine-tunes cost management approaches. Adopting such methodologies is crucial for teams desiring to fully harness the advantages of Kubernetes while upholding solid, compliant, and streamlined operations.
Ready to get started? Try Calico Cloud for free.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!