Enterprises that deploy Kubernetes in corporate data centers or cloud environments often use Cisco Secure Firewall to protect their networks and cloud resources. These firewalls are crucial for examining traffic coming from Kubernetes clusters. However, accurately determining the origin of this traffic as it passes through Cisco Secure Firewall can be challenging. By default, traffic leaving a Kubernetes cluster is not assigned a meaningful network identity that can be used to associate it with the application it came from.
Kubernetes is designed with dynamism in mind, allowing workloads to consistently scale up and down across various cluster nodes. Consequently, these workloads frequently acquire new IP addresses on the network. In some instances, the traffic exiting the cluster seems to come from the IP addresses of the cluster nodes, which are also dynamically scaling. This dynamism necessitates allowing a wide range of network CIDRs through firewalls to accommodate the ever-changing and transient nature of Kubernetes workloads, a practice typically not favored or approved by security teams.
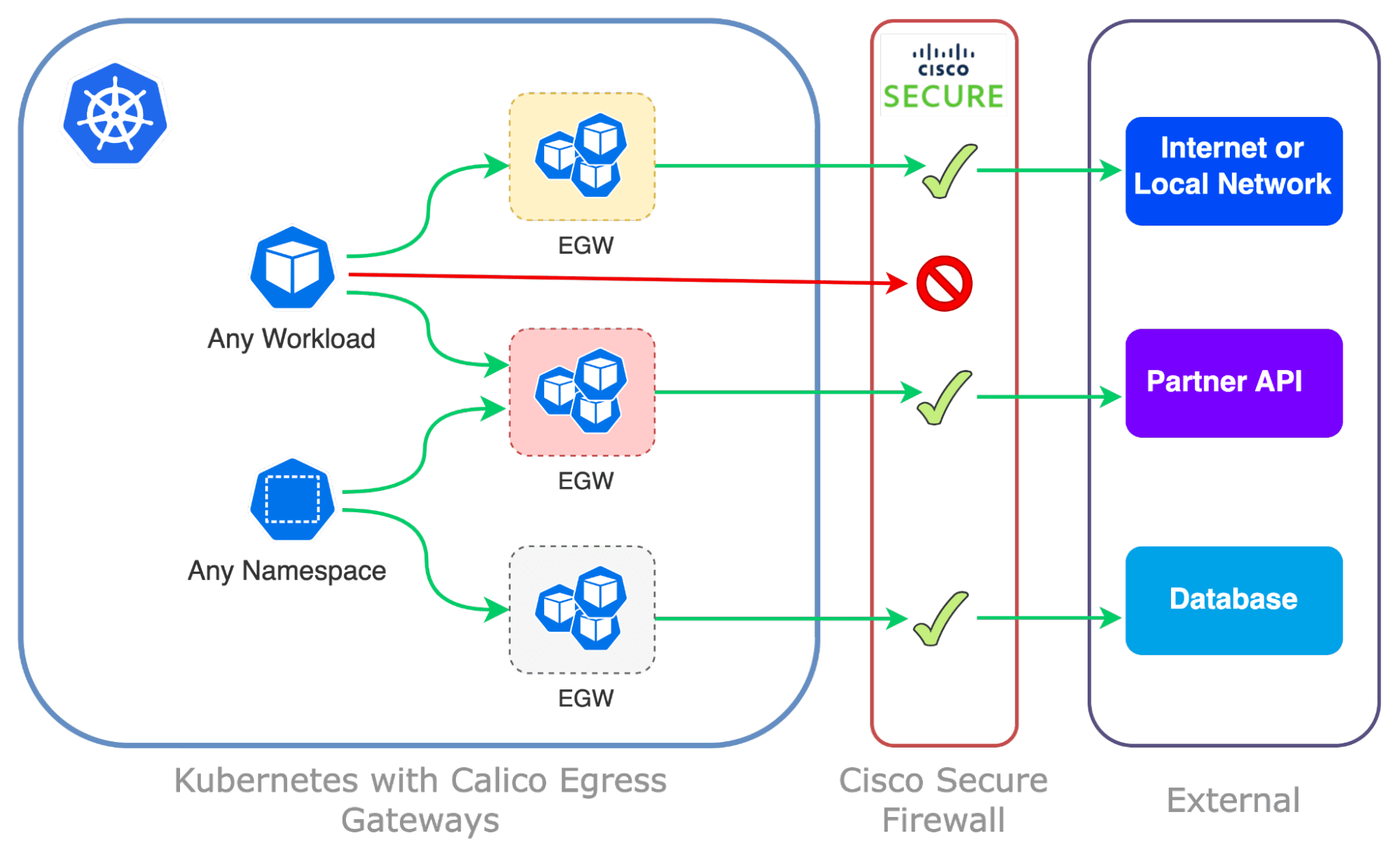
Calico Egress Gateways for Kubernetes
Egress Gateways with Calico allow you to identify the Kubernetes namespaces and pods associated with egress traffic outside of your clusters. This makes it easy to know the source of traffic to be inspected by the Cisco Secure Firewall. Understanding the source of application traffic leaving the Kubernetes cluster and passing through the Cisco Secure Firewall is crucial for several important reasons:
- Security and Compliance: Recognizing the origin of outbound traffic is crucial for ensuring that only authorized applications and services interact with external resources. This recognition enables administrators to implement appropriate security measures, thereby averting unauthorized access and potential data breaches. Comprehending the source of traffic is vital for adhering to industry regulations and data protection standards.
- Troubleshooting and Debugging: Identifying the source of outbound traffic is essential when issues arise, as it facilitates swift troubleshooting and debugging. Administrators can accurately locate the specific application or namespace generating the traffic, streamlining the process of identifying and resolving issues effectively.
- Billing and Cost Management: Having precise information regarding the origins of egress traffic allows organizations to manage costs and optimize cloud resources more effectively. By identifying which applications are major contributors to egress traffic, organizations can make well-informed decisions regarding resource allocation and billing.
Egress Gateway Cisco Secure Firewall Integration
Calico’s Egress Gateways integrates with Cisco Firewalls and extends a consistent network identity for Kubernetes workloads to ensure in-depth traffic visibility and thorough inspection beyond clusters. Calico strategically directs egress traffic through its Egress Gateways, utilizing AWS-backed Calico IP Pools, to ensure optimal routing and enhanced security.
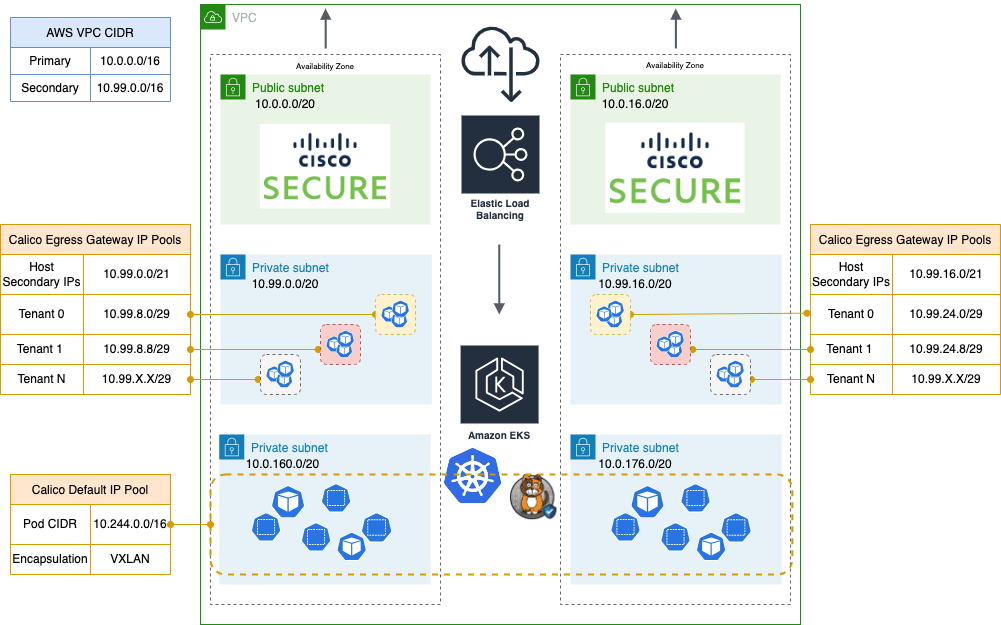
AWS-Backed Calico IP Pools
Calico Egress Gateways can utilize address space from several sources within AWS: dedicated VPC Subnets, shared VPC subnets with Subnet CIDR reservations, and VPC subnets using Secondary VPC CIDRs. They can operate with both public and private subnets. Furthermore, for their public IP addresses, they can employ AWS Elastic IPs. Consequently, Calico can offer a consistent network identity for Kubernetes workloads that access external resources, simplifying source identification in Cisco firewalls.
Diagram of example AWS VPC architecture utilizing Calico Egress Gateways with Cisco Secure firewalls.
Policy Based Routing for Calico Egress Gateways
Traffic exiting Kubernetes workloads can be channeled through designated Egress Gateways, or bypass them entirely, based on the configurations set by advanced Egress Gateway Policy settings. This setup establishes a unique network identity that aligns well with the rule settings of Cisco firewalls.
apiVersion: projectcalico.org/v3
kind: EgressGatewayPolicy
metadata:
name: "Cisco-Secure-Firewall"
spec:
rules:
- destination:
cidr: 103.47.244.0/24
description: "Gateway to Data Loss Prevention"
gateway:
namespaceSelector: "projectcalico.org/name == 'dlp-service-egw'"
selector: "k8s-app == 'dlp-service-egw'"
- destination:
cidr: 172.16.0.0/24
description: "Gateway to Corporate Mainframe"
gateway:
namespaceSelector: "projectcalico.org/name == 'corp-mainframe-egw'"
selector: "k8s-app == 'corp-mainframe-egw'"
- destination:
cidr: 172.16.99.0/24
description: "Gateway to Corporate Database"
gateway:
namespaceSelector: "projectcalico.org/name == 'corp-database-egw'"
selector: "k8s-app == 'corp-database-egw'"
- destination:
cidr: 10.0.0.0/8
description: "Local: no gateway"
Traffic originating from workloads and exiting the Kubernetes cluster is routed through specified Egress Gateways. The routing is determined by policies that are based on the external destination. This method streamlines the collaborative efforts between Platform and Security teams to secure Kubernetes environments.
Conclusion
In conclusion, the integration of Calico Egress Gateways with Cisco Firewalls in Kubernetes environments improves the oversight and regulation of outbound traffic for security purposes. This approach effectively addresses the dynamic characteristics of Kubernetes, enabling teams to maintain robust security without hindering the platform’s scalability or impeding operations.
Providing teams with the ability to accurately trace the source of their outbound traffic enhances an organization’s security and compliance, streamlines troubleshooting, and refines cost management strategies. Embracing these methodologies is essential for teams aiming to leverage the full benefits of Kubernetes while maintaining secure, compliant, and efficient operations.
Ready to get started? Try Calico Cloud for free.
Reference
Tigera – Enterprise Grade Egress Gateway for Kubernetes
Tigera – Using Calico Egress gateway and access controls to secure traffic
Tigera – Multi-VRF support for Egress Gateways using Calico
Cisco – Cisco Application Centric Infrastructure K8s Design White Paper
Cisco – Cisco NX-OS Calico Network Design White Paper
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!