Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Runtime attack vectors
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:
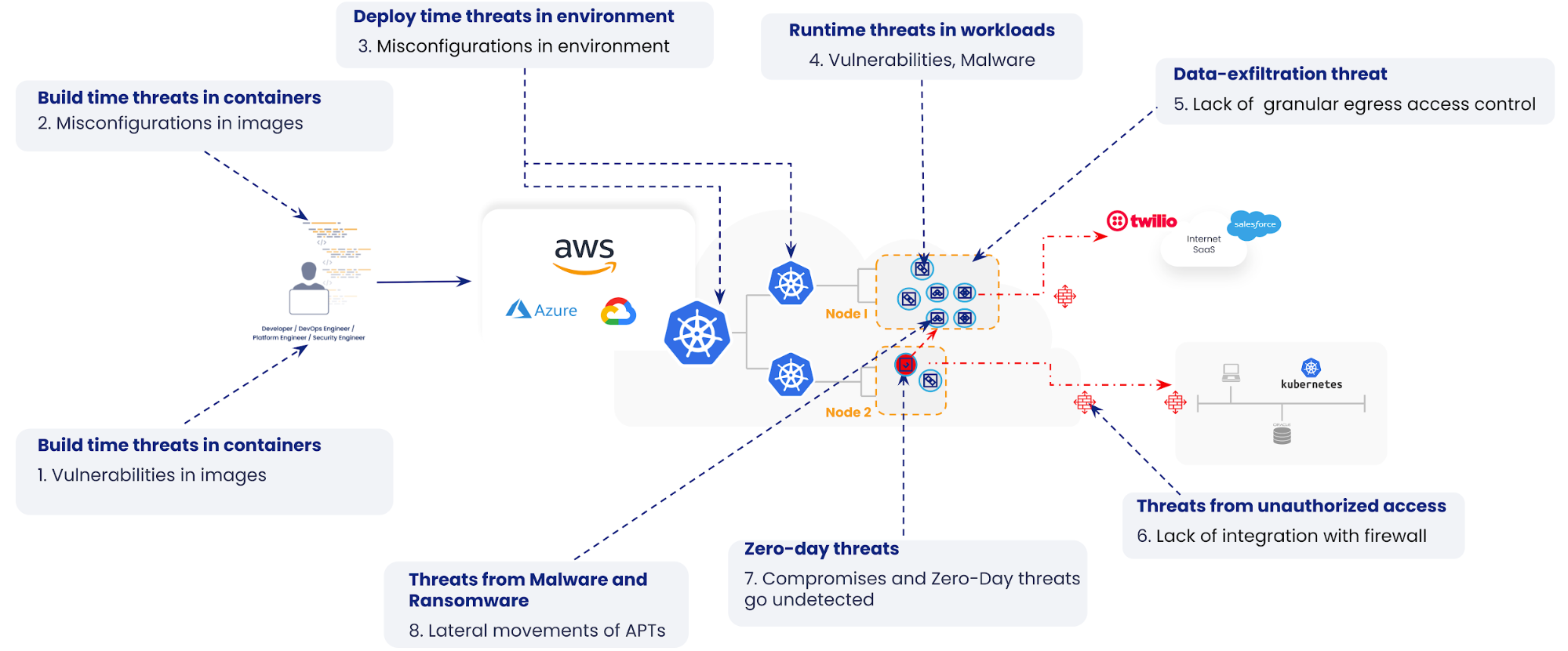
In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the attack surface during build time.
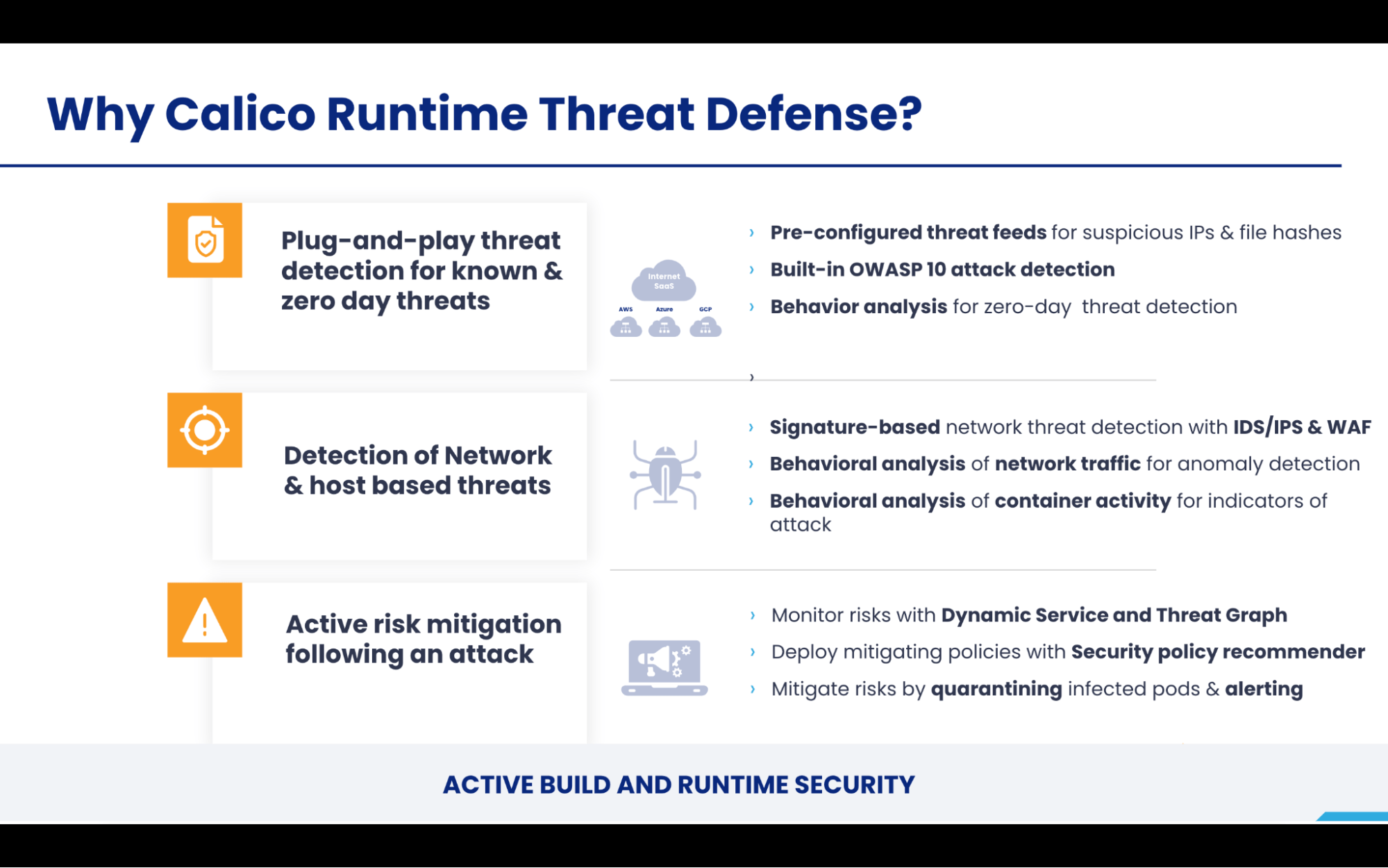
Calico Runtime Threat Defense is a transformational runtime security solution that provides comprehensive plug-and-play threat detection for known and zero-day attacks originating from the network or containers.
Comprehensive detection of known and zero-day attacks with Calico
If we can set aside the known vulnerabilities during build time, most of the threats shown in the graphical representation below are during runtime, which is also the reason why we need a solution that provides the broadest coverage. Calico Runtime Threat Defense uses a combination of behavior-based and signature-based techniques to detect Indicators of Compromise (IOCs) and Indicators of Attacks (IOAs) during runtime in both containers and on the network.
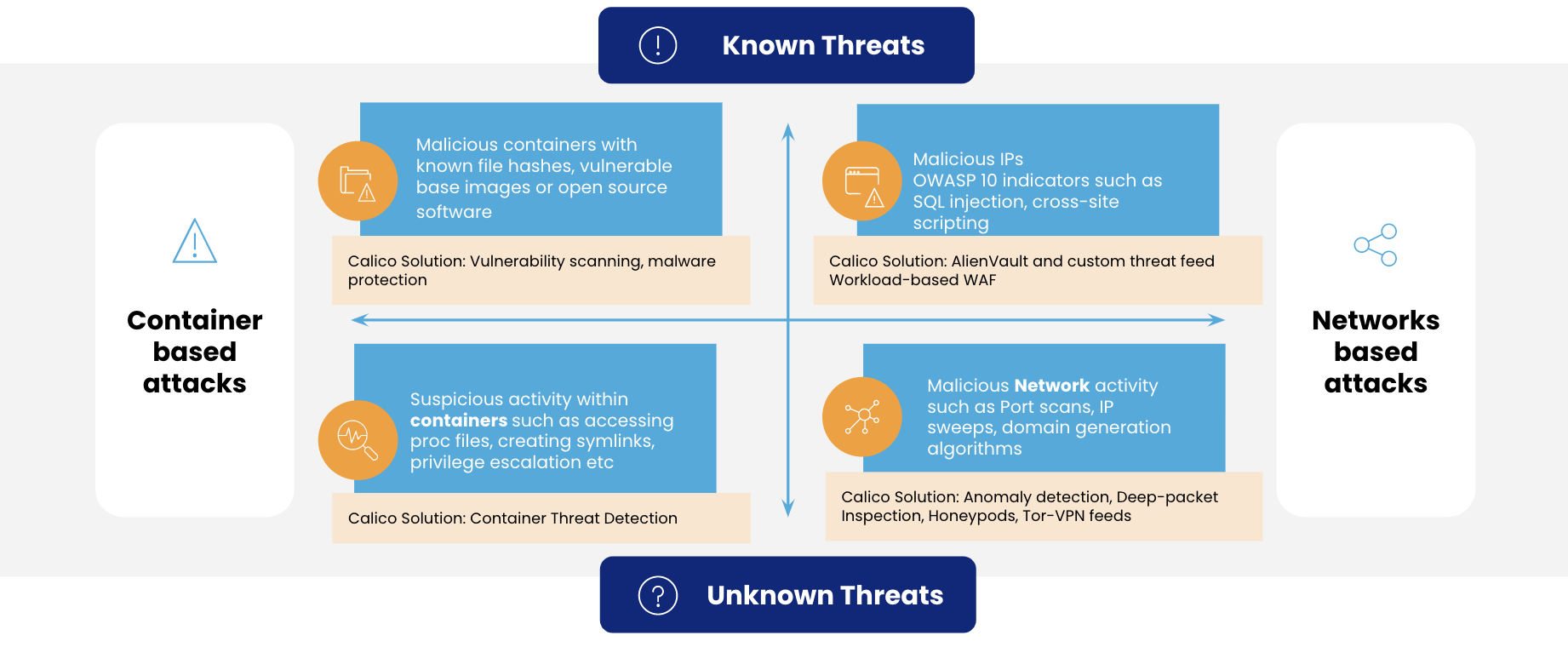
Behavior-based detection for zero-day attacks
Since the threat landscape changes every day, a vast majority of attacks are zero-day attacks, where the vulnerability was previously unknown. In such cases, the only way to identify the IOA is through behavior-based detection.
Calico Runtime Threat Defense’s behavior-based anomaly detection involves training the system with a normalized baseline and comparing activity against the baseline. Once an anomalous event appears, the system triggers an alert and provides a risk mitigation recommendation. Calico Runtime Threat Defense is currently the only solution on the market that delivers behavior-based anomaly detection for both network and container-based threats. It uses eBPF to track low-level container activity for suspicious process activity across filesystems, processes, and syscalls. The built-in behavioral detection process relies on deviation from established baseline behavior to identify IOAs and instantly send out alerts. For example, Calico Runtime threat defense will detect and alert you that a threat actor is trying to enumerate the Linux system information (files and directories, such as SELinux enumeration or ExeShield enumeration) to access the shell.. It can also detect and alert you of cryptomining attacks that use wget or curl to a known cryptomining top-level domain (TLD).

As for detecting unknown threats within containers during runtime, unlike rules-based engines that require configuration and tedious management, Tigera’s in-house security team provides a library of detectors that use container activity data to identify IOAs. Tigera’s security team continuously updates the library of detectors to stay abreast of evolving threats.
Calico’s network-based anomaly detection uses flow logs, L7 (application layer) logs, and DNS logs to baseline the behavior of cluster nodes, pods, and services. It applies algorithms to proactively determine IOAs such as port scans, IP sweeps and domain generation algorithms (DGA), generates alerts, and recommends risk mitigation strategies to resolve issues before services are compromised. A common DDoS application-level attack can be detected with our http_connection_spike or l7_bytes anomaly detectors. Once the user is alerted of the incident, they can immediately apply a quarantine policy for the workload and prevent the DDoS attack from happening.
Signature-based detections
The global community of security threat researchers works tirelessly to identify attackers. Once identified, the attacker’s signature and modus operandi is logged in a global threat intelligence database. Calico’s Runtime Threat Defense technology ingests threat intelligence feeds to provide comprehensive signature-based detection of the container and network-based threats and alerts if an IOC is detected.
Since Calico is running alongside the underlying network, it unlocks a unique security advantage with rich information on network packets. When you are given an opportunity to reduce the attack surface with known bad actors and their signature patterns, why would you not use it? Calico’s signature-based detection is highly differentiated and offers a cloud-native solution for known threats that enter through the network. This detection technique relies on a preprogrammed list of known IOCs, which can include malicious network attack behavior, file hashes of known malware, malicious IPs, domains, and external IP addresses.
Calico’s Runtime Security solution includes key capabilities such as workload-based intrusion detection and prevention, honeypods, deep packet inspection, and threat detection with Snort. Calico also offers protection against common OWASP Top 10 for known application-layer attacks with a workload-centric web \application firewall (WAF). The WAF is offered by leveraging Envoy as a DaemonSet so that any type of application-layer threat within the cluster can be detected. A traditional WAF/CDN that sits outside the cluster will be unable to offer this level of protection. For example, a workload-centric WAF can detect any type of abnormal HTTP header (HTTP type) information for traffic between services that is flowing within a cluster.
Plug-and-play solution
One of the key advantages of Calico Runtime Threat Defense is that it is fully automated, meaning that it can continuously monitor and analyze containerized applications’ behavior without requiring manual intervention. This allows organizations to free up valuable resources that would otherwise be spent on writing and maintaining security rules. Furthermore, this fully automated approach is more accurate and reliable than manual rule-based systems. Calico Runtime Threat Defense uses algorithms to analyze data that reduces the risk of human error and ensures that threats are detected and addressed quickly.
Active risk mitigation following an attack
Ask any security operations staff what their threat response plan is once they have detected an attack; the response is most likely a mitigation plan involving some kind of a fix so that business disruption is minimal. Risk mitigation needs three things in particular:
- Visibility into the affected workload(s)
- A robust policy mechanism to avoid further damage by isolating the workload(s)
- Assessment of the severity and nature of the risk
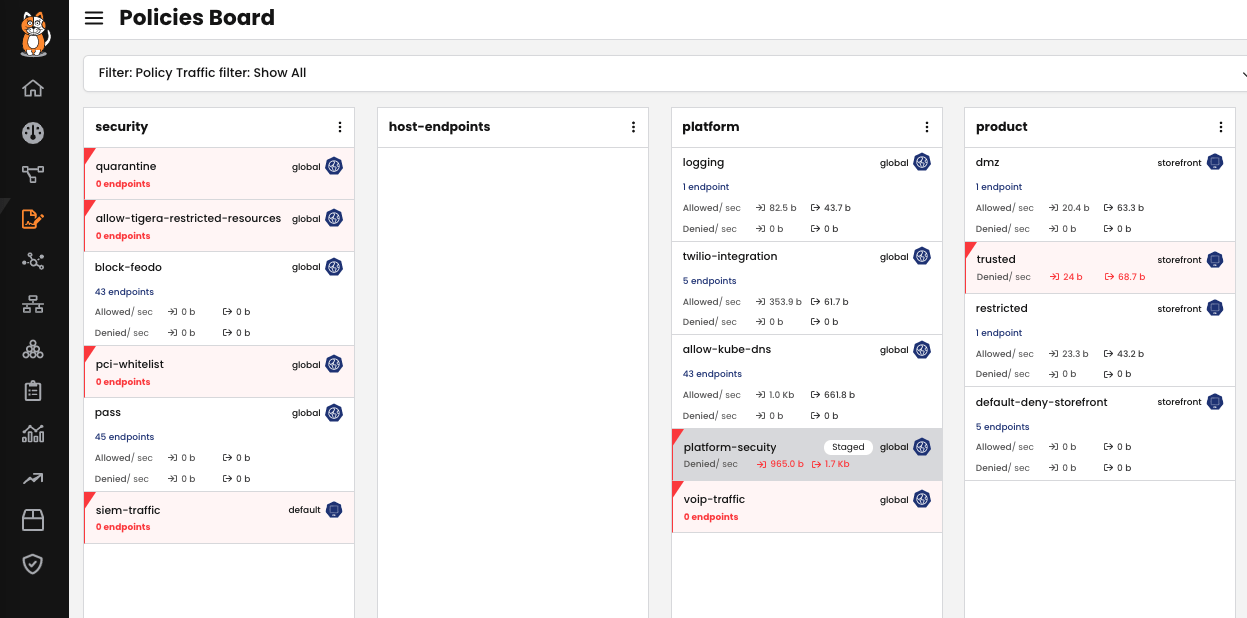
Calico has purpose-built tools such as Dynamic Service and Threat Graph that can help users easily understand the severity of an attack, how many workloads are affected, how these workloads communicate to other services and applications, and more. Once the affected workloads are identified, it takes only a matter of minutes for the operator to stage, test, and deploy access control policies to completely quarantine that particular workload. This will ensure that the rest of the application is not communicating with malware-infected systems. Calico simplifies the risk mitigation workflow by providing context of where the risk is and how it can be isolated, massively reducing the time spent on forensics and mitigation efforts.
Conclusion
Calico is truly the swiss army knife of active container security that will prevent, detect, and mitigate the ever-changing and ever-growing landscape of security threats. Calico will help organizations accelerate their businesses and actively strengthen their security posture.
Take a tour of our product and learn more about container security with our self-paced container security workshop.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!


