Tigera provides the industry’s only active Cloud-Native Application Security Platform (CNAPP) for containers and Kubernetes. Available as a fully managed SaaS (Calico Cloud) or a self-managed service (Calico Enterprise), the platform prevents, detects, troubleshoots, and automatically mitigates exposure risks of security issues in build, deploy, and runtime stages across multi-cluster, multi-cloud, and hybrid deployments.
We are very excited to unveil Calico Enterprise 3.15 and its new capabilities that will further reduce your applications’ attack surface and improve threat detection capabilities. Read this blog to learn about some of the biggest highlights of this latest release.
FIPS-140-2 compliance for US federal regulation
US federal agencies require that any software they use be compliant with the Federal Information Processing Standard (140-2), also known as FIPS 140-2. FIPS 140-2 specifies security requirements that are satisfied by a cryptographic module of applications and environments. With the release of Calico Enterprise 3.15, you can now configure Calico Enterprise to run in a FIPS 140-2 level 1 compliant mode to pass compliance requirements when serving US federal regulatory agencies.
When installing Calico Enterprise, you now have the option to install the platform in FIPS-compliant mode. This will ensure that the Calico components that are being installed satisfy compliance requirements for FIPS-140-2. For example, in the FIPS-compliant mode, Calico will only enable TLS v1.2 encryption and disable any non-FIPS-compliant encryptions. Calico will also replace any MD5 message-digest algorithm usage with SHA-256 for cryptography.
Proactively restrict workload access with Global Threat Feeds
At the reconnaissance stage of a container attacker, the attacker looks for weaknesses in the Kubernetes environment and containers to exploit valuable information from inside the cluster. To prevent reconnaissance attempts, security and platform teams should block communication from bad actors.
Learn more about the stages of an attack in this blog: Using the MITRE ATT&CK framework to understand container security
Calico offers a workload-based IDS/IPS system that detects and blocks communication from bad IPs, DNS, and VPNs based on global threat intelligence feed databases.
Security teams can now enable, disable, or customize their threat feeds within Calico Cloud with just 3 easy steps: add a feed, provide a description/URL, and save. While Calico provides AlienVault as the default database, organizations can add multiple feeds as well as custom threat feeds as part of the IDS/IPS configuration. Teams can also configure the threat feed as a new DomainNameSet or as IPSet threat feeds.
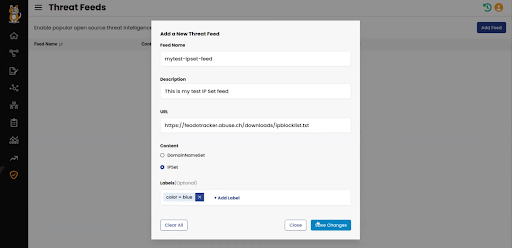
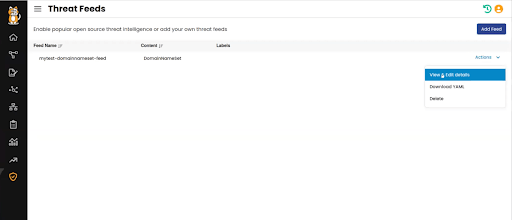
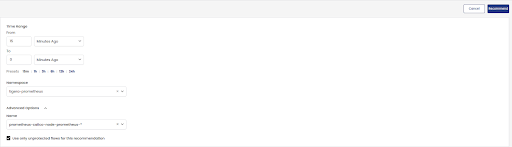
Secure specific namespaces with automatic security policy recommendations
A starting point to achieve zero trust in a cloud-native environment is to understand the traffic flow between the different workloads inside the cluster and also the traffic with the external resources. Writing security policies manually can result in gaps, such as dropping a legitimate connection or allowing unwanted communications.
Calico’s Policy Recommender inspects flows with an allow action between endpoints and generates a recommended policy accordingly, eliminating a significant amount of manual work. With the new 3.15 release, Calico can now inspect and recommend security policies for the whole namespace instead of examining every single pod in the namespace. Users can now micro-segment workloads based on namespaces, ensuring teams are following organizational and regulatory requirements.
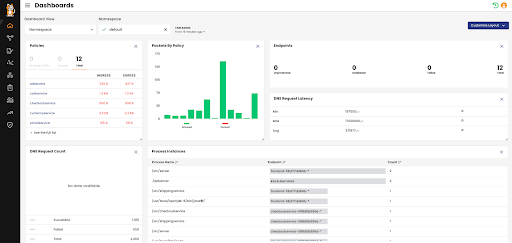
Namespace-based dashboards
As your cloud-native environment grows, checking the health status of your applications can become very challenging. A dashboard is a great way to monitor the health status of a cluster and the running applications at a glance.
Calico now provides namespace-based dashboards for DevOps, platform, and security teams in addition to the existing cluster-based dashboard.
New dashboard views provide HTTP response codes/latency, process instances, services, and more, enabling teams to troubleshoot and resolve issues faster.
Egress gateway pod failure detection and failover
Calico Egress Gateway lets you control the source IP of particular application traffic leaving the cluster. It is a critical component and any egress gateway pod failure can impact operations, which is why Tigera invests in increasing the productivity and reliability of the Calico Egress Gateway.
Previously, Calico relied on the Kubernetes readiness probe to monitor Egress Gateway health, which worked fine in detecting most of the failure scenarios. In this new release, we are introducing egress gateway pod failure detection and failover based on outgoing probes to check upstream connectivity.
In some scenarios, the health status of egress pods may take some time to be updated due to performance issues on the underlying Kubernetes platform or a complete node outage. In these cases, you now have the option to configure a list of ICMP Ping targets or HTTP URLs to check upstream connectivity and then take unhealthy egress gateways out of rotation as soon as possible.
Conclusion
Calico Enterprise is a leading self-managed active CNAPP for containers, Kubernetes, and cloud. It’s built on open-source Calico to provide Kubernetes-native security and observability capabilities. We’re happy to announce new features and capabilities in our latest release of Calico Enterprise, and we’re committed to continuing to add updates for future releases.
Want to try Calico for free? Sign up for a free trial.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!


