Zero Trust Security
Provide zero trust security with encryption, least privilege access controls, and defense in depth for cloud-native applications with Calico.

Overview
Zero Trust security is a strong security model that assumes that networked entities should not be trusted by default, and that an application or infrastructure has been compromised and is currently hosting some form of malware. Zero Trust policies rely on real-time visibility into workloads, and require continuous monitoring and validation of each requested connection for the right privileges and attributes. One-time validation won’t suffice, because threats and connection attributes are all subject to change.
Cloud-native applications running on Kubernetes are particularly vulnerable to the spread of malware because of the open nature of cluster networking; by default, any pod can connect to any other pod, even across namespaces. It’s difficult to detect malware or its spread within a Kubernetes cluster without implementing a security model like Zero Trust. Calico enables a zero trust environment built on three core capabilities: encryption, least privilege access controls, and defense-in-depth.
Benefits
Protects sensitive data, enables compliance
Be compliant with corporate and regulatory data protection requirements that specify the use of encryption, including SOX, HIPAA, GDPR, and PCI.
Automatically blocks unauthorized access
Implement least privilege access control with deny-all network traffic by default, allowing only the connections that have been authorized.
Empowers developers with self-service policy changes
Helps developers maintain the security posture needed to meet compliance requirements mandated by legislation or internal security team.
Key Features

Data-in-transit Encryption
Protect sensitive data that falls under regulatory compliance mandates. Calico utilizes WireGuard to implement data-in-transit encryption. WireGuard runs as a module inside the Linux kernel and provides better performance and lower CPU utilization than IPsec and OpenVPN tunneling protocols. Calico supports WireGuard for self-managed environments such as AWS, Azure, and OpenShift, and managed services such as EKS and AKS.
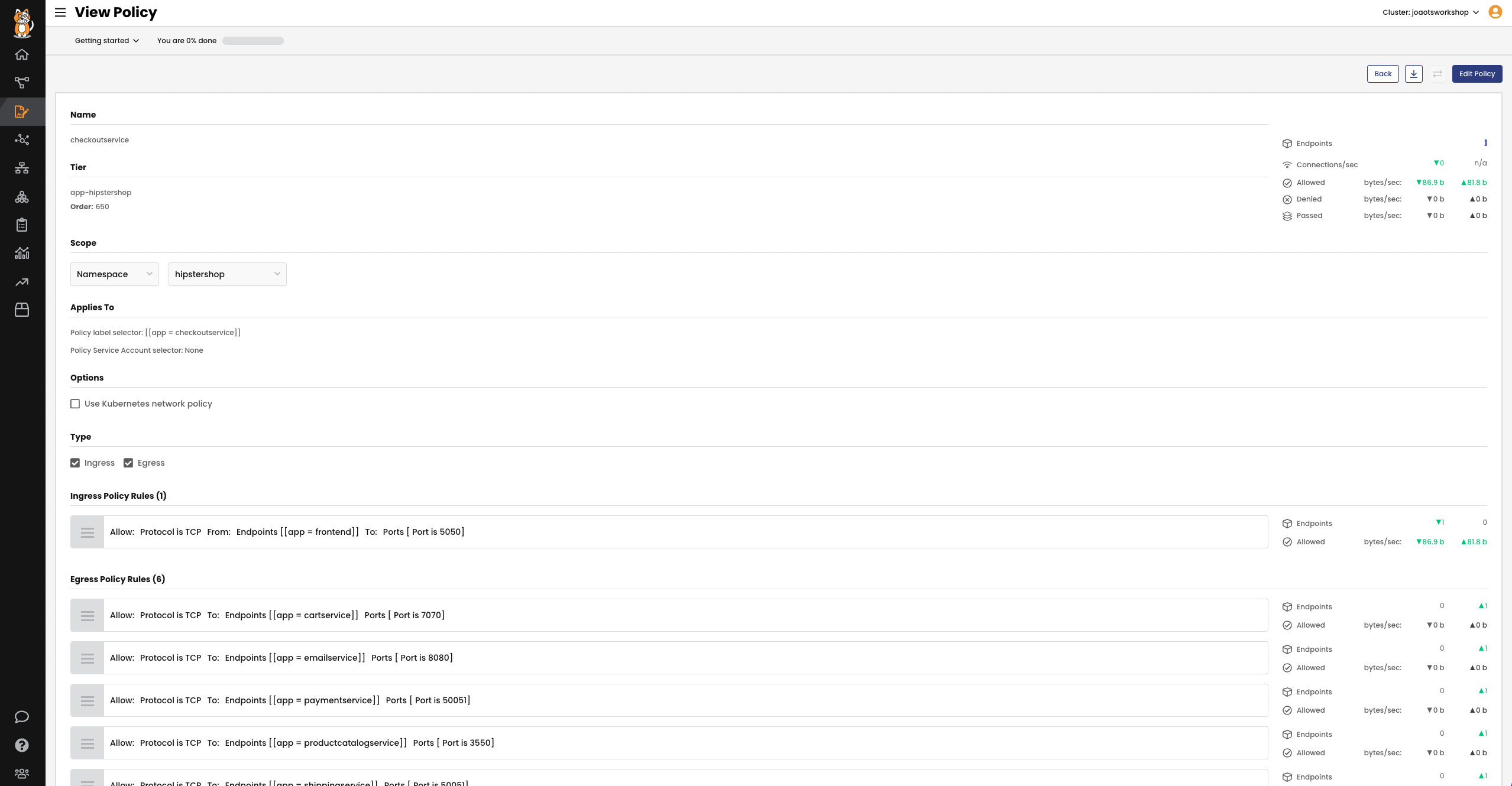
Least Privilege Access Controls
Protect your application by allowing access to only the information and resources that are necessary. Calico implements least privilege access controls by denying all network traffic by default and allowing only those connections that have been authorized, including ingress and egress outside the cluster.
Leverage Calico’s policy recommendation engine or define granular policies yourself to connect cluster resources externally, via application API paths and web methods.
Get notifications for unauthorized attempts to connect to another service or location.
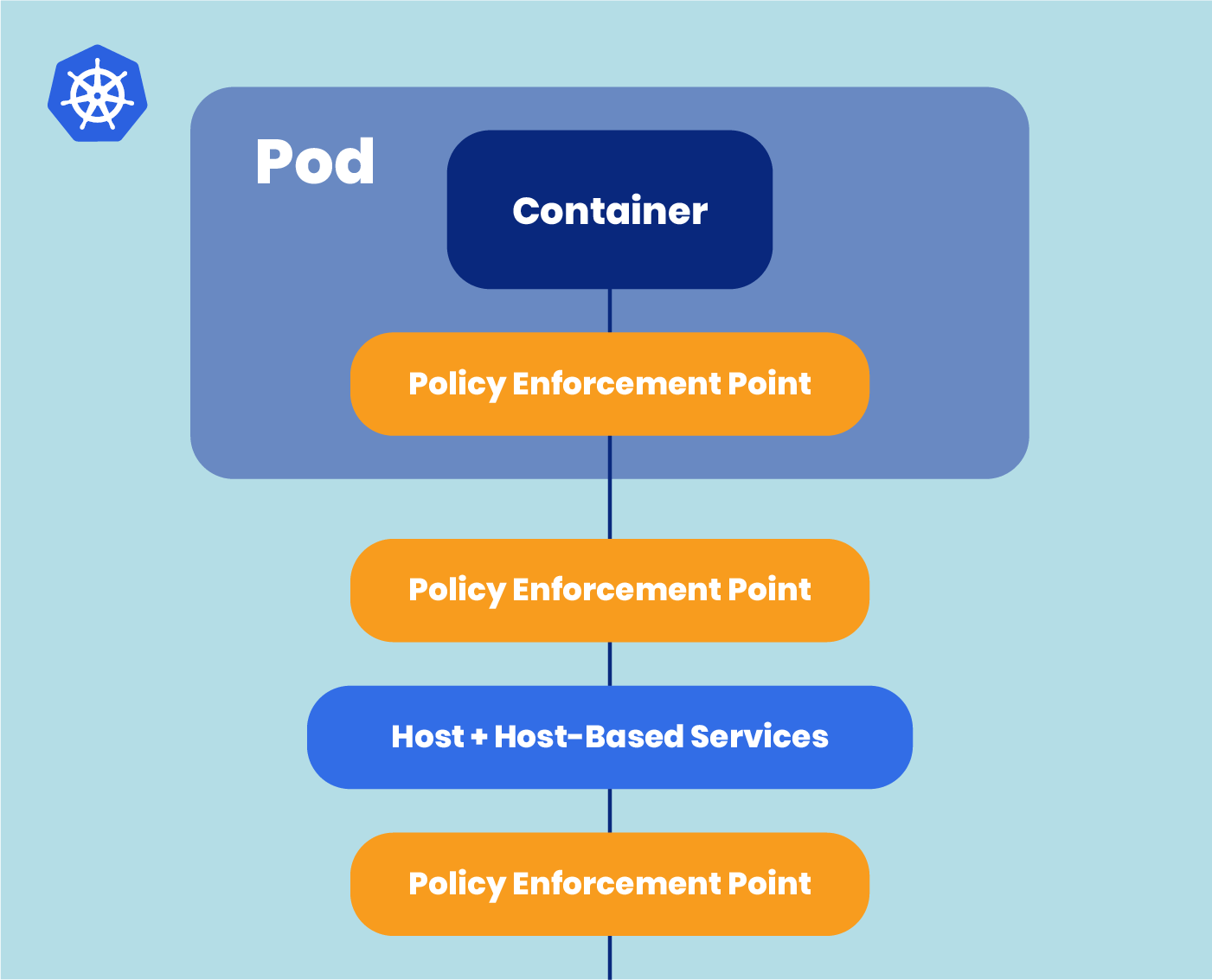
Defense-in-Depth
Get automatic alerts for security policies changes. Calico monitors and logs all changes to policies, including the version history. The change history shows exactly what changed and is the first step in providing security forensics that provide a record identifying what happened and how.