New applications and workloads are constantly being added to Kubernetes clusters. Those same apps need to securely communicate with resources outside the cluster behind a firewall or other control point. Firewalls require a consistent IP, but routable IPs are a limited resource that can be quickly depleted if applied to every service.
With the Calico Egress Gateway, a new feature in Calico Enterprise 3.0, existing firewalls and control points can now be used to securely manage access to infrastructure and services outside of the cluster. In addition, IT teams are now able to identify an application/workload in a Kubernetes namespace via the source IP.
As organizations progress on their Kubernetes journey from pilot to production, they begin migrating existing applications into the cluster, which has merged with the greater IT environment. For the platform teams involved, this creates challenges because these apps will need to communicate to services outside of the cluster.
- The Platform team will need to enable Kubernetes connectivity to infrastructure and services behind a firewall or to enable a DLP solution or a monitoring solution like a SIEM to associate packets to the intended applications.
- The firewall will require a consistent IP to enable the service, and this becomes a significant pain-point. Why? Routable IPs are a limited resource that can be quickly depleted if applied to every service that needs one. This limitation can constrain the ability of the platform team to scale the cluster.
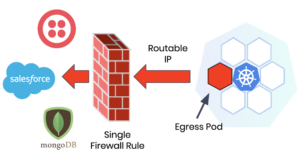
The Calico Egress Gateway ingeniously solves these problems. First, it defines a static egress IP for SNAT on traffic leaving the cluster and applies it to a specific namespace. Then it designates one pod in a namespace as the egress pod and assigns a routable IP which is used specifically for egress traffic leaving the cluster.
Instead of having all pods in a Kubernetes namespace be routable, a single pod in a namespace is designated as an egress pod. Platform teams can continue to scale the cluster while preserving the limited number of routable IPs available by leveraging non-routable IPs for all other pod traffic within the cluster.
The Calico Egress Gateway also extends the scope of firewalls to Kubernetes to manage traffic originating from a cluster. You can now enforce egress policies for Kubernetes resources using your existing firewall infrastructure or other IP control point. A single firewall rule can be defined that allows all pods within a namespace to securely access resource(s) outside of the cluster, in effect, creating a “universal firewall”.
The Calico Egress Gateway, along with other new capabilities in Calico Enterprise 3.0, is designed to streamline cluster management and enable you to more easily scale your Kubernetes environment. With the Calico Egress Gateway, you can securely connect to resources outside of the Kubernetes cluster while preserving the limited number of routable IPs. The platform team only has to manage one firewall rule instead of many, saving time and eliminating the burden of multiple firewall change requests to SecOps. And beyond the cluster, enterprise monitoring systems can identify an application/workload in a Kubernetes namespace via its source IP.
————————————————-
Free Online Training
Access Live and On-Demand Kubernetes Tutorials
Calico Enterprise – Free Trial
Solve Common Kubernetes Roadblocks and Advance Your Enterprise Adoption
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!