DevSecOps is a collaborative practice that incorporates security into the development and delivery of software. DevSecOps encourages a culture where security, development, and operations teams collaborate closely; this collaboration ensures that security considerations are understood and implemented by everyone involved in the software development lifecycle. Shift-left is a key principle in DevSecOps, emphasizing the need to address security early in the development process (shifting it “left” on the project timeline). By doing so, security vulnerabilities can be identified and rectified earlier, which is more efficient and cost-effective.
The same principle applies to Infrastructure-as-code (IaC) and guarantees that platforms are deployed and configured with adequate security controls to limit the attack surface. While shift-left security enforces the right checks before the software is deployed, in a continually evolving threat landscape, it is equally important to monitor the platform in real time to ensure that the security posture does not deteriorate during runtime. Security and DevOps teams must have complete visibility over the state and runtime behavior of workloads and the platform to detect and remediate vulnerabilities or prevent potentially malicious activity to limit the risk to production applications. This continuous feedback loop is essential to maintain the desired security posture in a Kubernetes environment.
Fragmented security solutions can lead to disjointed security measures, making it challenging to maintain a comprehensive view of the security posture across all clusters. Calico Cloud offers a unified solution to secure, monitor, and detect security events across the Kubernetes ecosystem regardless of where the clusters are located or the cluster type.
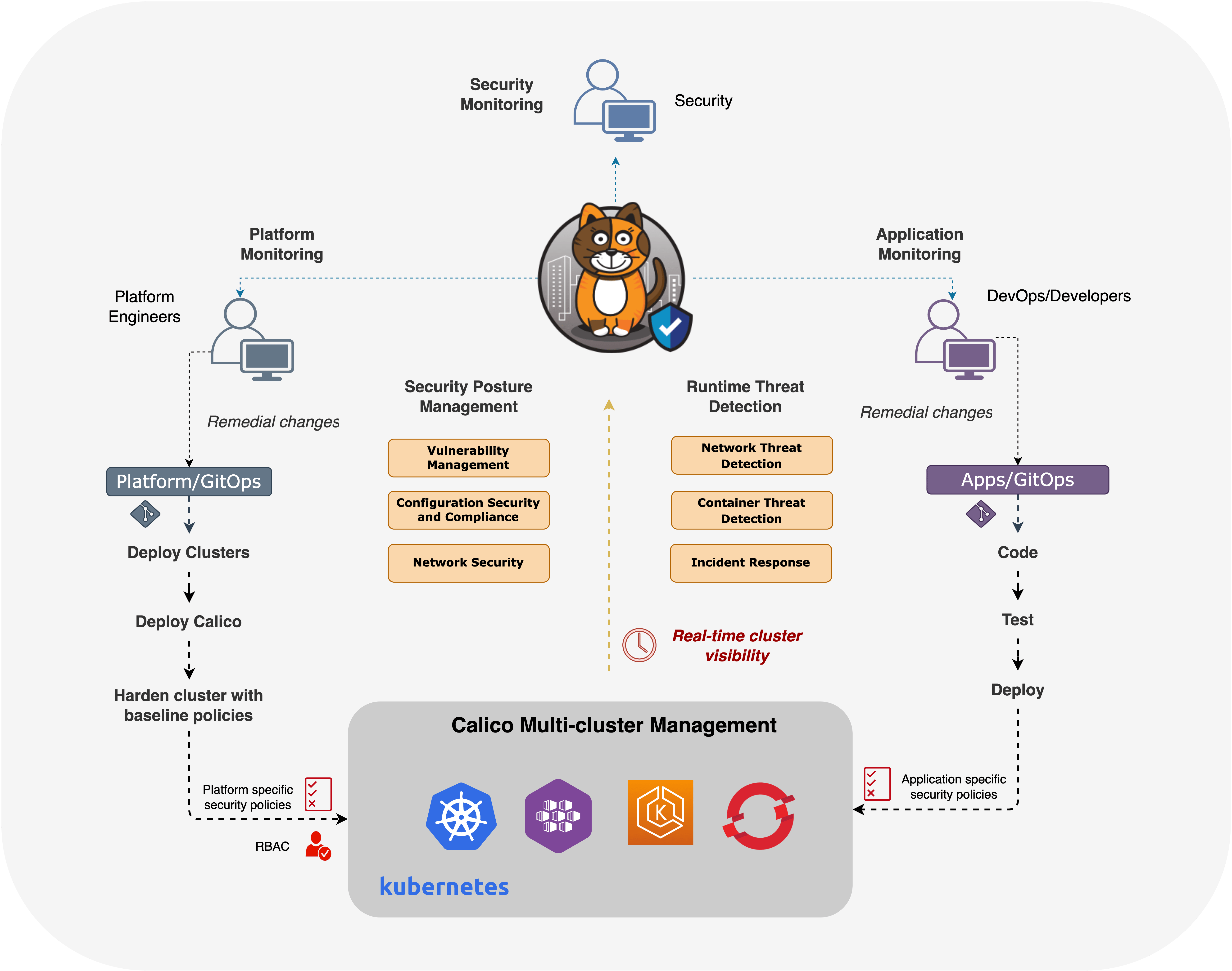
DevSecOps advocates for a shared responsibility approach, which is only achievable when development, security, and operations teams are equipped with the right tools that facilitate collaboration and foster a common understanding of the risks and threats facing the organization. The diagram below provides a high-level overview of how Calico Cloud ensures that all stakeholders participate in securing both workloads and platforms while providing the right level of visibility and monitoring so that teams can respond to security events, prioritize, and deploy changes in a timely manner.
Figure: Calico Cloud Multi-cluster Management Facilitating DevSecOps
In the next section of this blog post, we will look at how Calico Cloud helps organizations accelerate their DevSecOps practices.
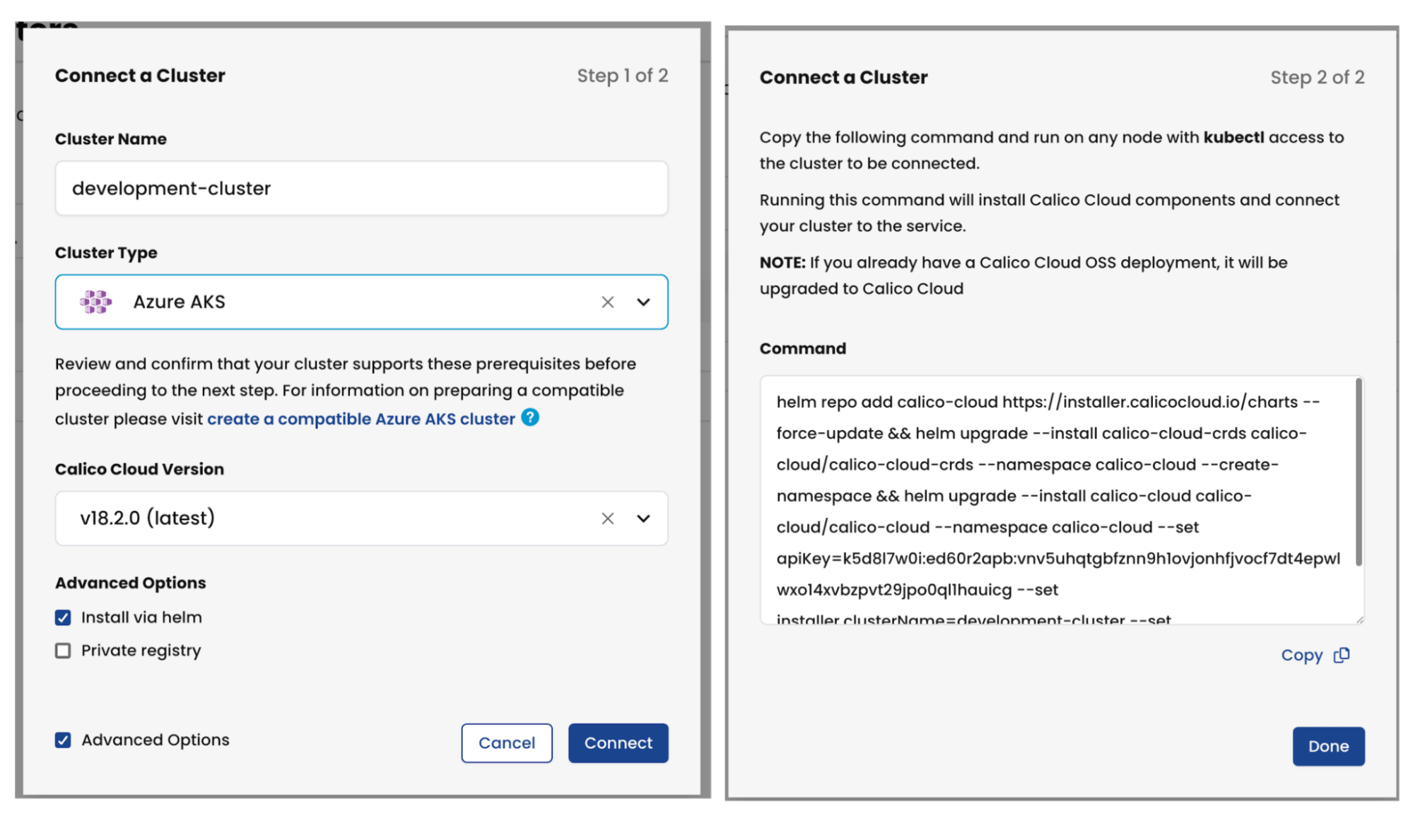
Getting Started: Secure Seamless Deployment with Helm
Calico Cloud can be seamlessly deployed to existing Kubernetes clusters or integrated into the build pipeline of new clusters using Helm which simplifies and automates the deployment process. The automation ensures that DevOps teams can integrate security into the early stages of infrastructure builds following best practices of “security as code” and “infrastructure as code”.
Figure: Calico Cloud Helm Deployment
Hardening Kubernetes Clusters and Improving Cluster Security Posture
Kubernetes platforms, by default, are open and permissive. While managed Kubernetes providers have streamlined the process of building clusters, the onus is still on the platform and security teams to ensure that these clusters are hardened to meet the organization’s security and compliance requirements. Below are some policies and practices that Calico Cloud helps enterprises implement to ensure that Kubernetes clusters are adequately secured:
- Control Plane Security: This involves blocking unauthorized access to the API, which is crucial for protecting the cluster’s command center.
- Default-Deny Security Posture: Implementing a default-deny security posture ensures that all traffic, both ingress and egress, is denied by default. Traffic is only allowed based on explicit rules, minimizing the risk of unauthorized access.
- Node Security: This involves securing the physical and virtual machines where Kubernetes runs, ensuring that they are accessible only from authorized endpoints.
- Ingress and Egress Control: Managing how data enters and leaves the Kubernetes cluster is essential. Defining external networks using NetworkSets allows for precise control over this traffic, ensuring that only legitimate and necessary communication occurs.
- Data Encryption: Communications between workloads on different nodes in a Kubernetes cluster are not encrypted by default. Calico offers a seamless solution to encrypt all node-to-node workload traffic within the cluster.
- Vulnerability Management: This involves verifying the security and integrity of container images to prevent the deployment of vulnerable or malicious containers.
- Logging and Monitoring: Vital for maintaining ongoing awareness of the cluster’s state and detecting potential security incidents. Network logging, DNS logging, and audit logging enable detailed tracking and analysis of activities within the cluster.
- Security Benchmarks and Compliance: Adhering to security benchmarks and compliance standards, such as the CIS (Center for Internet Security) benchmarks, helps align Kubernetes deployments with industry best practices, thereby enhancing the overall security posture of the platform.
Security Policy-as-code
Calico security policies are implemented as Kubernetes custom resources (CRs), which are extensions of the Kubernetes API and can be treated similarly to native Kubernetes resources such as pods, deployments, and services. These policies adhere to Kubernetes concepts such as namespaces and role-based access control (RBAC), providing a cloud-native experience for implementors. Like other Kubernetes resources, Calico policies are configured using YAML and can be applied using continuous deployment (CD) tools. This approach allows for consistent and efficient management of network security rules alongside other Kubernetes resources.
Below is a security policy example that demonstrates how PCI-compliant workloads can be isolated from other workloads in the cluster.
apiVersion: projectcalico.org/v3
kind: GlobalNetworkPolicy
metadata:
name: security.pci-restrict
spec:
tier: security
order: 1
selector: pci == "true"
namespaceSelector: ''
serviceAccountSelector: ''
ingress:
- action: Allow
source:
selector: pci == "true"
destination: {}
- action: Deny
source:
selector: pci != "true"
destination: {}
egress:
- action: Allow
source: {}
destination:
selector: pci == "true"
- action: Deny
source: {}
destination:
selector: pci != "true"
types:
- Ingress
- Egress
Figure: Policy-as-code
Shift left security with CI/CD Pipeline Integration
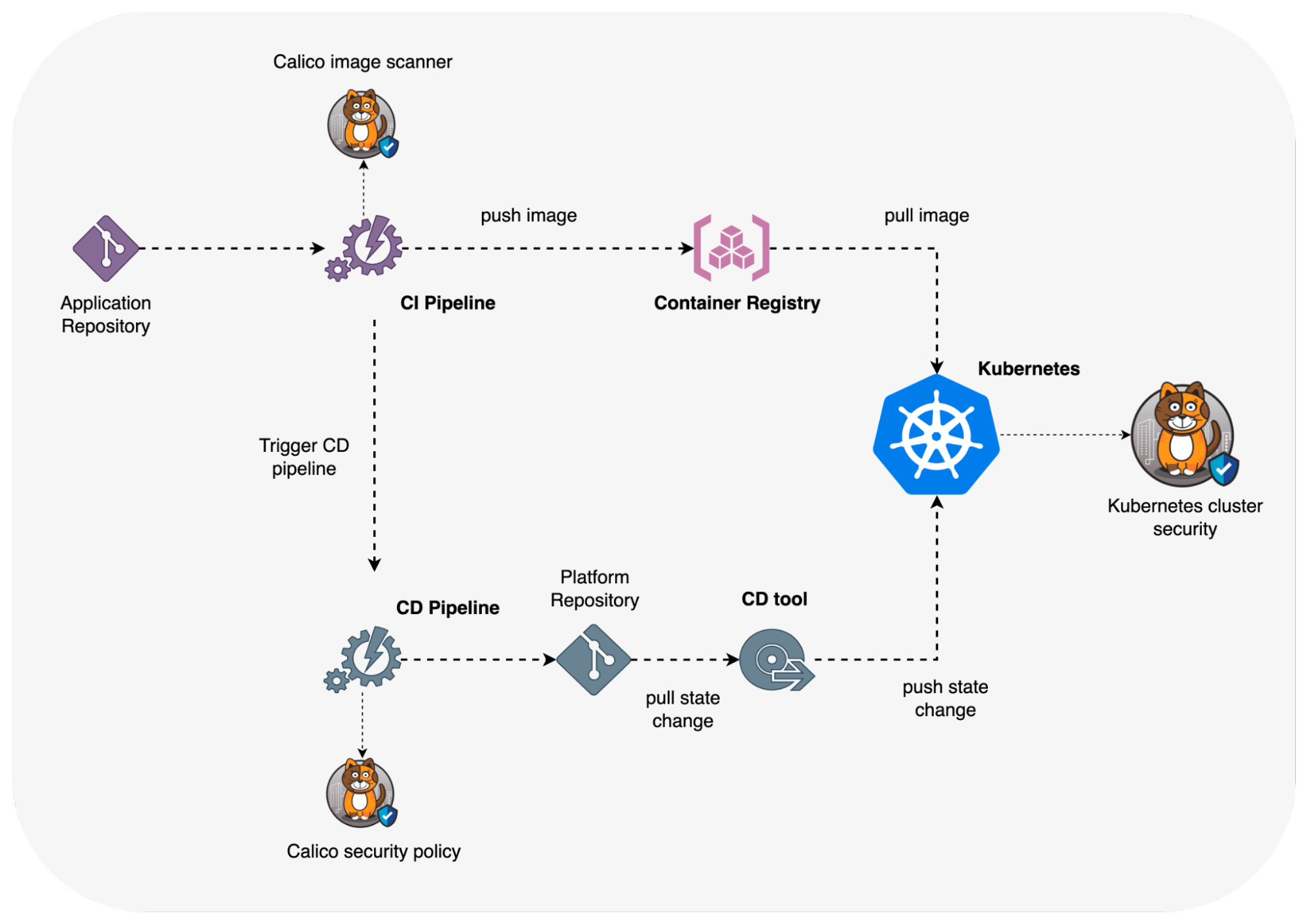
Calico Cloud can be utilized during various stages of the software development process – build, deployment, and runtime. In the build phase, Calico Cloud can help identify and mitigate security vulnerabilities within container images. It can be integrated with the CI pipeline to scan for vulnerabilities as part of the continuous integration process. This ensures that any security issues are caught early before the images are pushed to a registry or deployed into a production environment. During the deployment phase, Calico Cloud can enforce security policies and network controls to protect applications and their data. These policies can be defined as code, ensuring consistency and compliance across the entire Kubernetes environment.
At runtime, Calico Cloud continuously monitors and protects the Kubernetes clusters. It offers real-time threat detection and response capabilities, identifying and mitigating potential attacks or breaches as they occur. This includes monitoring network traffic and workload behavior for unusual patterns, ensuring that only legitimate traffic is allowed and that potential threats are quickly isolated and addressed. This comprehensive coverage across the build, deployment, and runtime phases of the software development lifecycle not only enhances security but also aligns with the principles of DevSecOps, promoting a proactive, integrated approach to security in Kubernetes environments.
Figure: Security during build, deployment, and runtime
For more information on this topic, read our blog post, How to integrate Calico Image Scanner with Argo CI/CD.
Shift-left and Shift-right
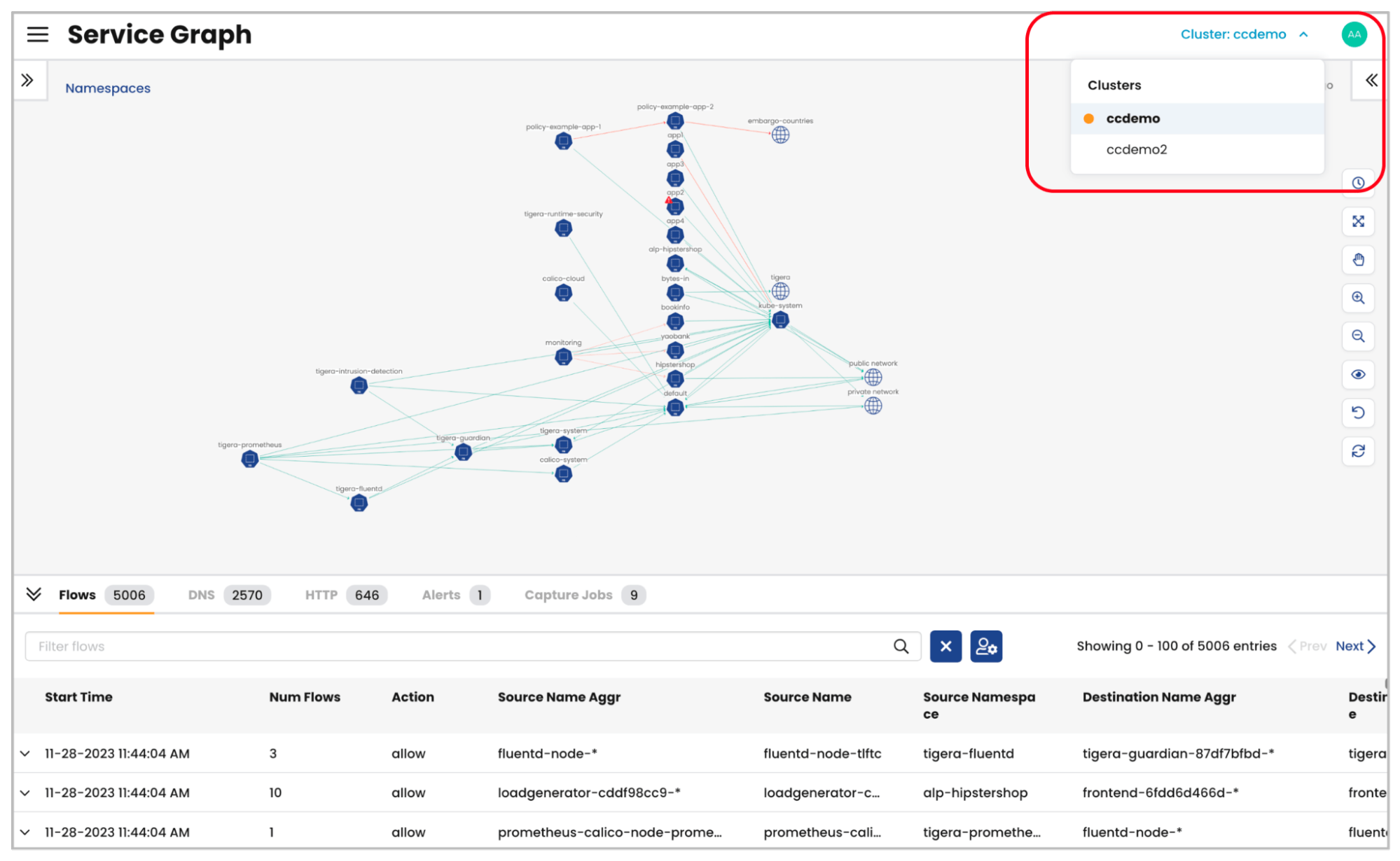
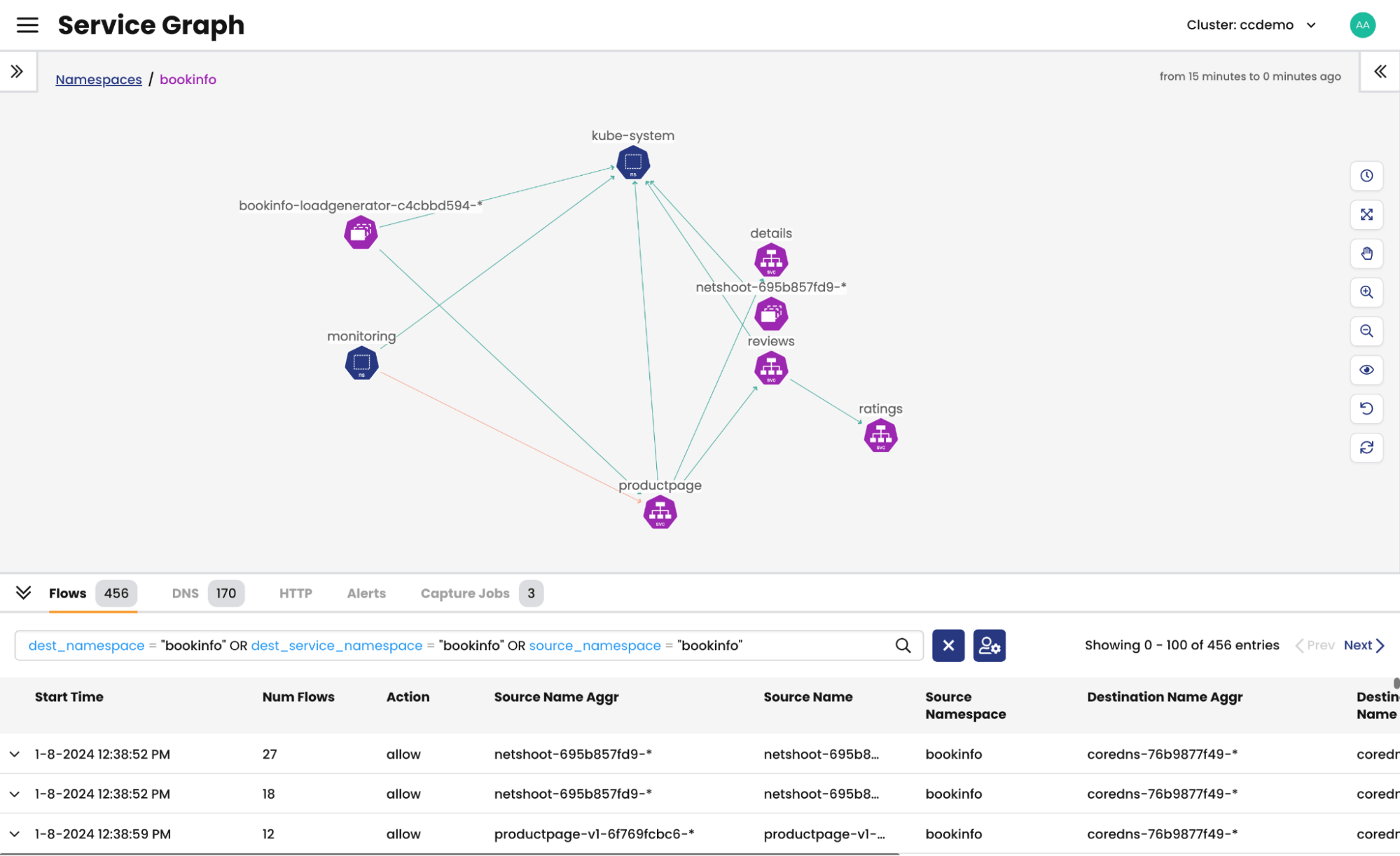
In this context, Calico Cloud helps all stakeholders – including developers, operations teams, and security professionals – understand the behavior of workloads in a Kubernetes cluster. The Service Graph in Calico can be configured with role-based access control (RBAC), enabling teams to have visibility into their namespaces and the workload activity within those namespaces. This common understanding of workload behavior is crucial not only for security applications but also for optimizing performance and reliability.
Figure: Service Graph Global Cluster View
Figure: Service Graph Namespace View
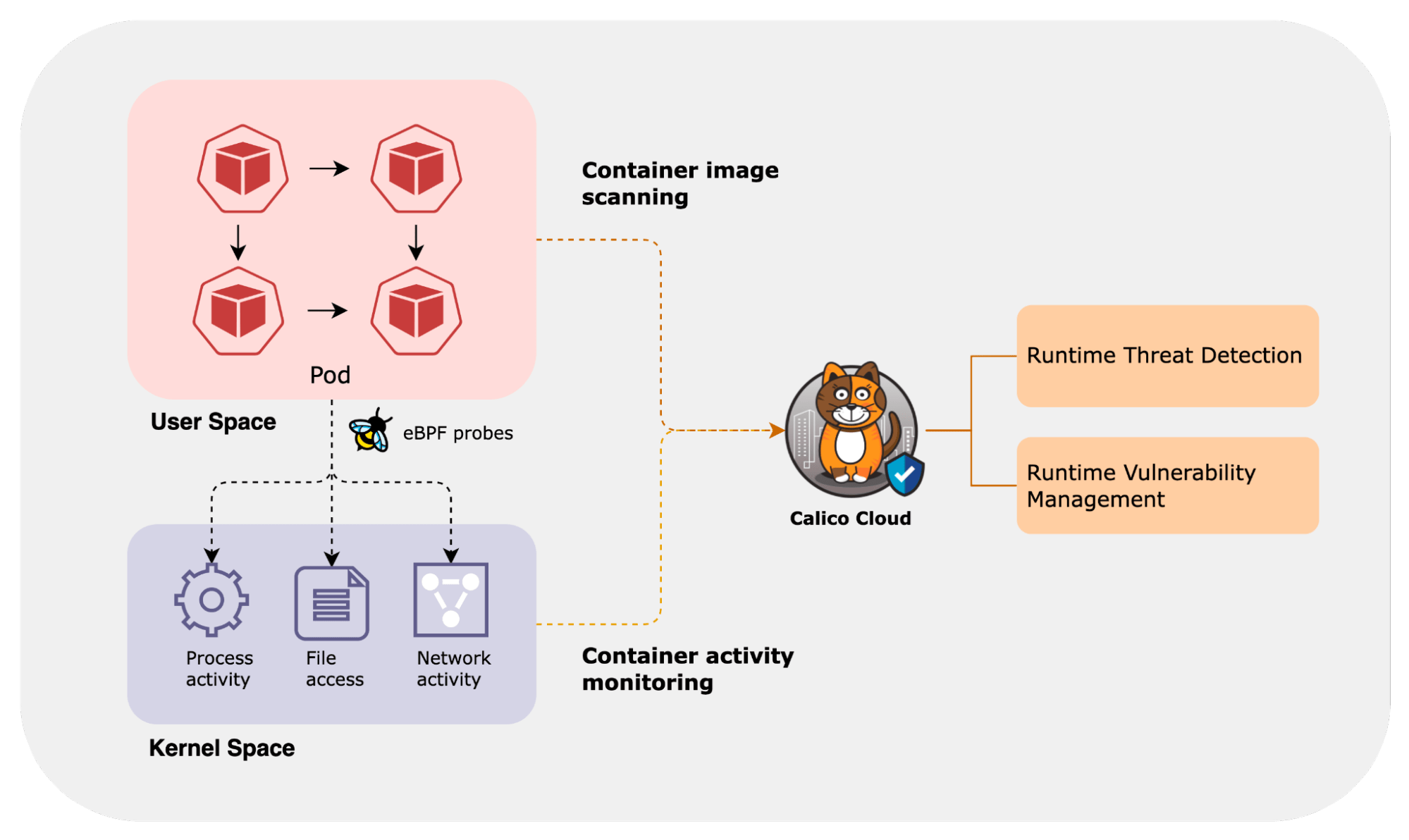
Runtime Vulnerability Management and Threat Detection
In addition to providing image scanning during build time, Calico Cloud also performs runtime vulnerability scans that are crucial in a rapidly evolving threat landscape. It also continuously monitors workload behavior to identify malicious activity during runtime. Traditional runtime security can’t keep pace with the rapid deployment and termination of containers. Calico uses advanced eBPF probes to understand the behavior at a container level. These capabilities offer the following benefits:
- Continuous Detection: Calico Cloud continuously monitors for new vulnerabilities. As threats evolve rapidly, this ensures that newly discovered vulnerabilities are identified as soon as possible.
- Real-time Security Posture: It provides an up-to-date view of your security posture, allowing for immediate action and reducing the window of exposure to threats.
- Covers Runtime Environment: Calico Cloud identifies vulnerabilities that may only be evident when the software is running, including those related to configurations or interactions with other services.
- Infrastructure Dependencies: It can capture changes in the environment or infrastructure, ensuring that security is maintained even as the system evolves.
- Real-time Alerting: Calico Cloud alerts users so that remedial measures can be taken to limit the exposure from vulnerabilities or malicious activity.
Figure: Runtime Vulnerability Management and Threat Detection
Conclusion
DevSecOps integrates security into the software development and delivery process, fostering collaboration among security, development, and operations teams. It emphasizes ‘shift-left’ security, which involves addressing vulnerabilities early in the development process and applying these principles to application development and Infrastructure-as-Code (IaC) for secure deployments. Also ensure that the security posture of Kubernetes clusters is maintained in an ever-evolving threat landscape by monitoring runtime behavior of your cloud-native application. Calico Cloud offers a comprehensive set of capabilities that help organizations implement DevSecOps practices and foster a collaborative approach to security.
Ready to try Calico network policies? Sign up for a free trial of Calico Cloud
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!