What is OWASP Top 10?
The OWASP® Foundation improves software security through community-led projects, chapters worldwide, and conferences. The OWASP Top 10 is a standard awareness document for developers, highlighting critical web app security risks and providing guidance on best practices for mitigation across different environments.
Adopting Kubernetes introduces new risks. The OWASP Kubernetes Top 10 prioritizes risks for security practitioners, platform engineers, and developers. The OWASP Top 10 for Kubernetes targets security risks and vulnerabilities in containerized environments, addressing unique challenges in Kubernetes deployments. It offers specific security recommendations for clusters and applications.
Below is the Top 10 list for Kubernetes:
- K01: Insecure Workload Configurations
- K02: Supply Chain Vulnerabilities
- K03: Overly Permissive RBAC Configurations
- K04: Lack of Centralized Policy Enforcement
- K05: Inadequate Logging and Monitoring
- K06: Broken Authentication Mechanisms
- K07: Missing Network Segmentation Controls
- K08: Secrets Management Failures
- K09: Misconfigured Cluster Components
- K10: Outdated and Vulnerable Kubernetes Components
Calico powerfully addresses OWASP Top 10 vulnerabilities in Kubernetes. It enhances security with advanced network security and eBPF technology, reducing the attack surface. Integrated with Kubernetes’ Network Policies, it enables precise traffic control. Calico’s built-in anomaly detection swiftly responds to threats, contributing to OWASP Top 10 mitigation.
This blog post explores how Calico contributes to mitigating OWASP Top 10 concerns.
Workload Isolation and Microsegmentation
Calico enables fine-grained network segmentation and isolation between pods, namespaces, and clusters in Kubernetes environments. Calico Enterprise helps mitigate risks such as injection, broken access control, and cross-site scripting through several key features and functionalities:
Identity-aware microsegmentation
This helps with workload Isolation, eliminates lateral movement of threat in the cluster, and provides instant threat response and mitigation
Security Policy Management
Calico provides self-service policy creation integrated into Gitop, automatic policy recommendations and lastly simplified security policy workflow
Service Accounts-Based Access Controls with Encryption and RBAC Integration
Calico allows you to control network access based on the identity of the pods, enabling more granular security and isolation. It associated network security policies with Kubernetes Services accounts ensuring that only authorized users have the ability to define or modify network policies.
Ingress and Egress Traffic Controls
You can define the source of incoming and outgoing traffic based on pod labels, namespaces, IP addresses, or even specific Kubernetes service accounts. This means you can allow or deny traffic from or to specific pods, namespaces and external sources. Calico allows you to specify the protocols (e.g., TCP, UDP) that are permitted for incoming traffic. In addition to the network policies, Calico offers application layer policies that let you allow or deny traffic based on layer 7. It helps reduce the risk of data exfiltration, limit the blast radius of breaches, and ensure workload isolation.
The ability to identify the traffic source at the namespace or pod level from a Kubernetes cluster to communicate to the external resource is also very important for the security team that observes the traffic activity from an outsider point of view (most likely from the firewall). The pod traffic may be NAT’d to the host or routed to the fabric and because of the nature of Kubernetes it can be nearly impossible to identify the application. That is why Calico offers the Egress Gateway feature that assigns a fixed, routable IP to a Kubernetes namespace to identify workloads running within that namespace.
Threat Detection and Anomaly Monitoring
As Kubernetes orchestrates containerized apps, the changing attack surface is addressed with tailored anomaly monitoring to:
Detect, Block, and Prioritize
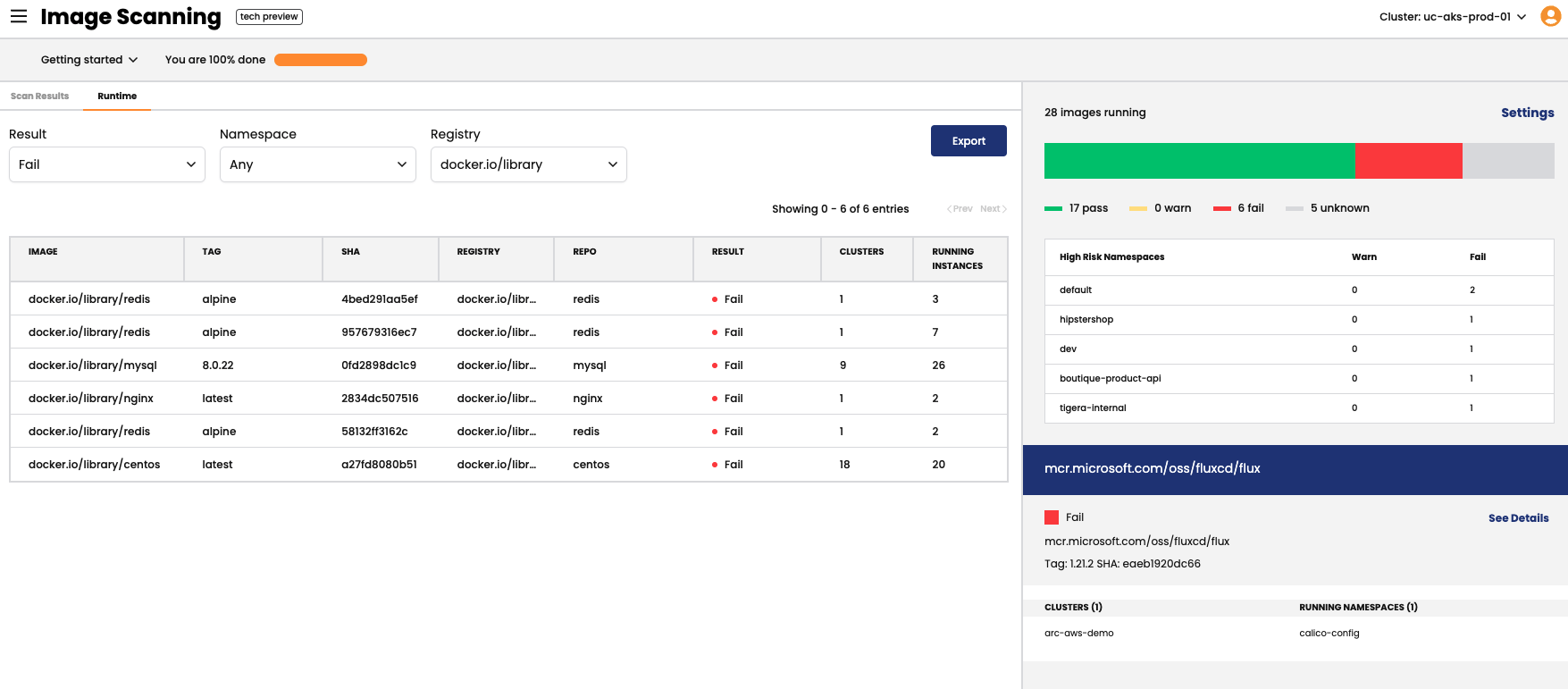
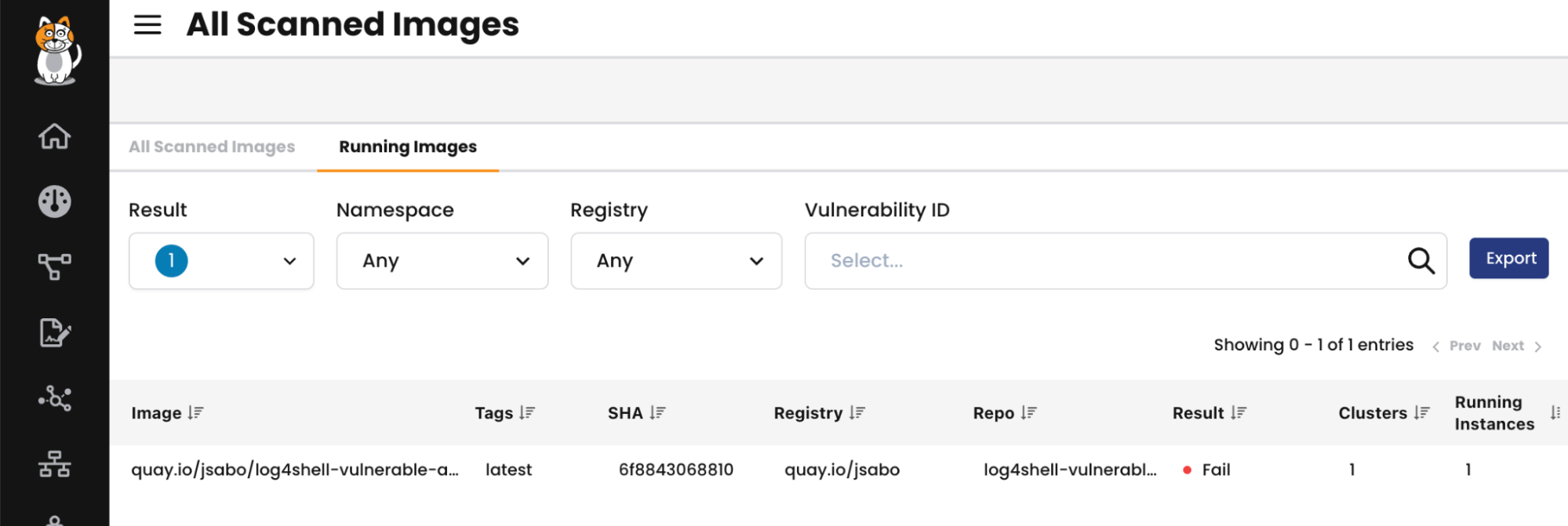
Scan images for vulnerabilities and misconfigurations prior to production deployment, automatically blocking risky images and creating exceptions for low-risk vulnerabilities based on usage.
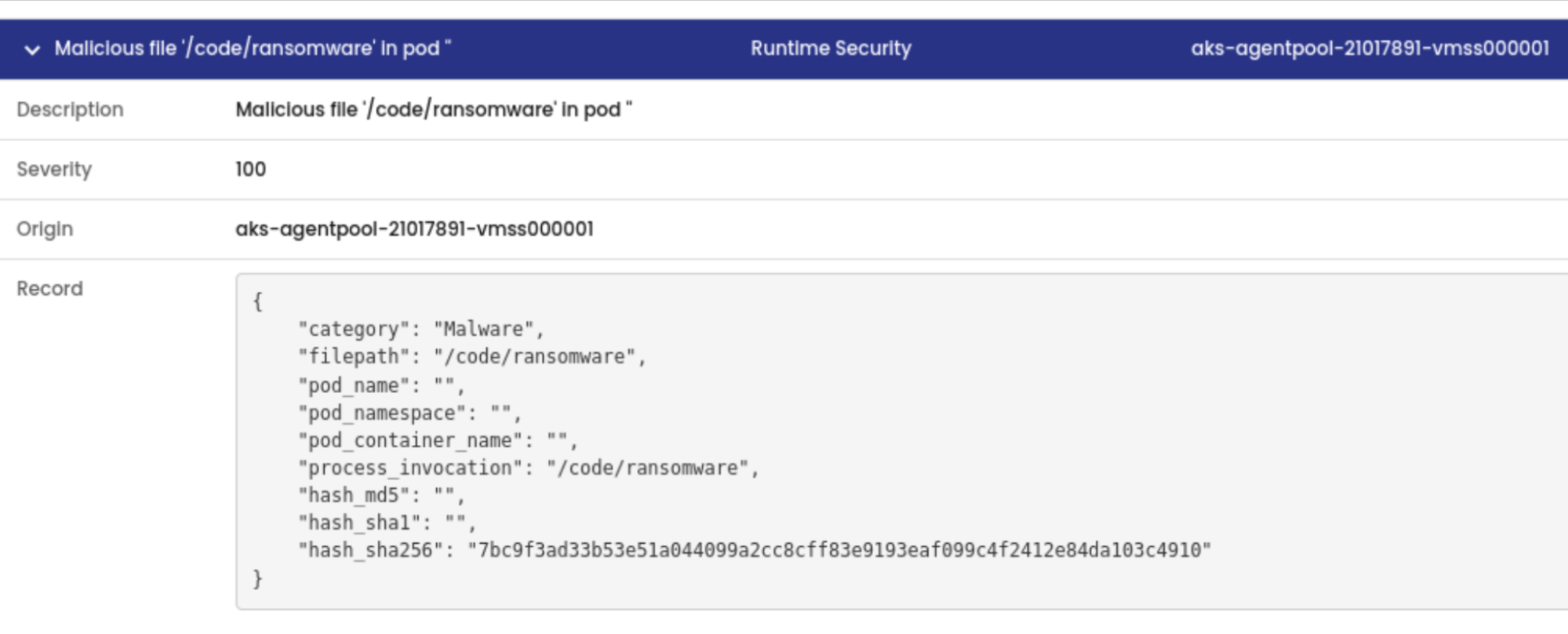
Detect known malware using process file hash comparisons against malware signatures. Identify zero-day threats with built-in eBPF probes, analyzing suspicious behavior across processes, file systems, and system calls, with ongoing addition of new detectors for emerging threats.
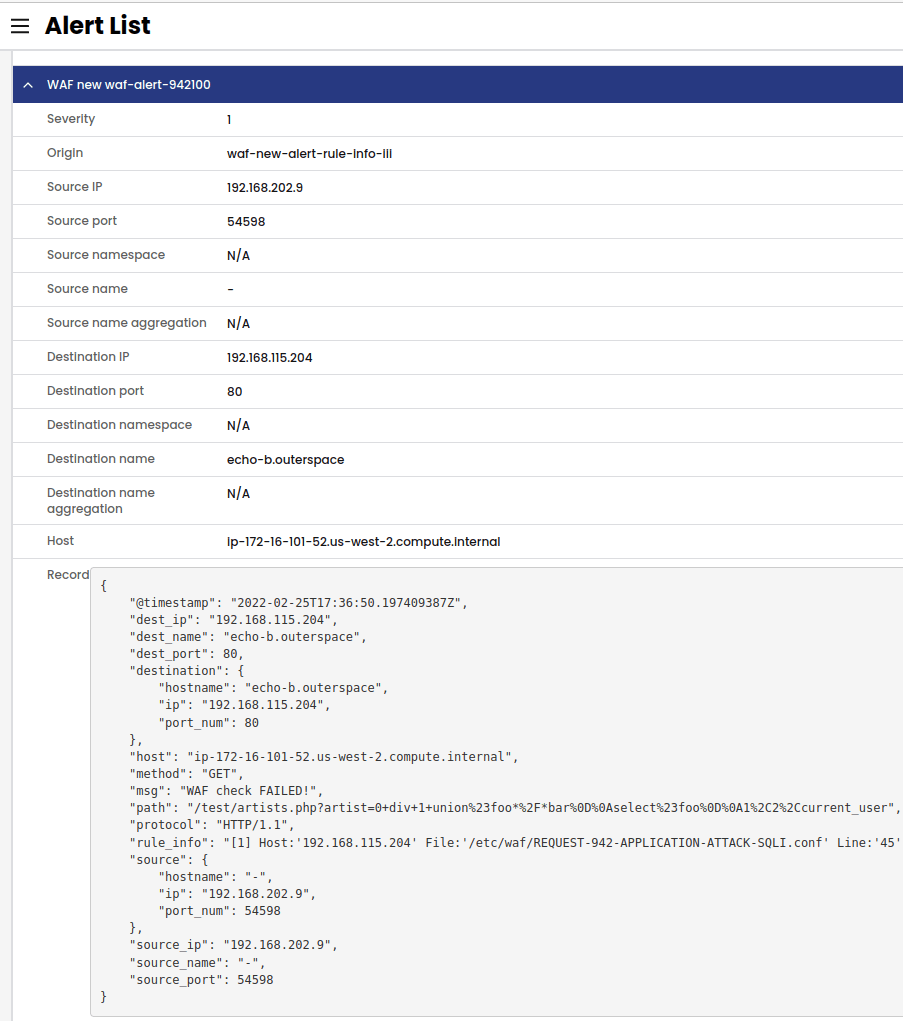
Block connections to malicious IPs from AlienVault and custom feeds, using workload-based IDS/IPS. Halt zero-day attacks via heuristic learning of unusual network activity. Prevent OWASP Top 10 attacks with workload-focused WAF. Intercept DDoS by blocking requests from malicious IPs.
Actively Mitigate Exposure Risks
Continuously monitor vulnerable workloads during runtime, connecting vulnerability scans with real-time insights into Kubernetes clusters and their associated risks. Evaluate and prioritize the risk level of deployed workloads as new vulnerabilities are identified and reported.
Utilize Calico Policy Recommender to quickly isolate infected workloads in just a few clicks. Implement security measures to safeguard the organization from widespread threats. Collaborate with developers and security personnel to apply patches and counter threats while maintaining service continuity.
Encryption and Secure Communication
Calico supports both host-to-host encryption for pod traffic, and direct node-to-node communication. Calico uses data-in-transit encryption with WireGuard that’s faster and more efficient than IPsec and OpenVPN protocols. Data cannot be read without a key. It comes along with automated WireGuard tunnel creation and management, and Calico provides transport-level security for on-the-wire, in-cluster pod traffic.
Observability, Logging, and Compliance
Calico provides network visibility and security in Kubernetes clusters with insights into network flow, security events, and real-time monitoring, improving troubleshooting and response capabilities.
Network Flow Visualization
Calico provides graphical representation of communication patterns between pods and namespaces.
- Helps identify suspicious traffic between pods, aiding in detecting Injection and Cross-Site Scripting (XSS) attempts.
- Enables visualization of communication channels, supporting better security policy configuration to prevent Broken Authentication and Access Control vulnerabilities.
Network Flow Logging
Calico collects and logs network flow data for analysis and auditing.
- Provides audit trails of network communications, aiding in investigations related to Sensitive Data Exposure or Unauthorized Access attempts.
- Helps identify unauthorized lateral movement within the cluster, mitigating risks associated with Security Misconfigurations.
Security Event Logging
Calico records security-related activities within the Kubernetes environment.
- Captures policy enforcement and violations, helping address Broken Access Control and Security Misconfigurations.
- Logs denied network connections, supporting the identification of attempts to exploit Injection or XSS vulnerabilities.
Real-time Monitoring and Alerting
Calico provides continuous assessment of network traffic with alerts for suspicious activities.
- Detects anomalous behavior in real-time, allowing prompt responses to Injection, XSS, or Insufficient Logging and Monitoring attempts.
- Enables proactive identification of unauthorized attempts and potential data breaches associated with Sensitive Data Exposure.
Security Policies and Compliance
Calico enforces security policies to limit access and improve compliance.
- Enforces access controls and policies to prevent Broken Authentication and Access Control vulnerabilities.
- Supports compliance with security best practices, helping to address multiple OWASP Top 10 threats.
Troubleshooting and Diagnostics
Calico assists in identifying and resolving network connectivity issues and performance bottlenecks.
- Facilitates swift troubleshooting of network misconfigurations that may lead to Injection or XSS vulnerabilities.
- Helps diagnose and rectify issues that could potentially cause Insufficient Logging and Monitoring.
Integration with External Monitoring and SIEM Tools
Calico connects with external tools for consolidated observability data.
- Facilitates a more comprehensive and unified view of Kubernetes security, aiding in identifying and mitigating various OWASP Top 10 threats.
Conclusion
Calico addresses the OWASP Top 10 vulnerabilities in Kubernetes clusters through network segmentation, traffic controls, threat detection, encryption, observability, security policies, and integration with external tools, enhancing the security posture and protection against web application vulnerabilities.
By leveraging Calico, organizations can significantly enhance their security posture, respond effectively to emerging threats, and safeguard their applications and data against the most critical web application vulnerabilities outlined in the OWASP Top 10. Take the proactive step toward securing your Kubernetes clusters by exploring Calico today.
Ready to try Calico for yourself? Get started with a free Calico Cloud trial.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!