Over the past year, we’ve been building something new for Calico Cloud that’s aimed at helping anyone who is charged with improving the security of their Kubernetes clusters. I’m excited to announce that Calico Cloud is releasing new capabilities for security posture management called Security Scoring and Recommended Actions.
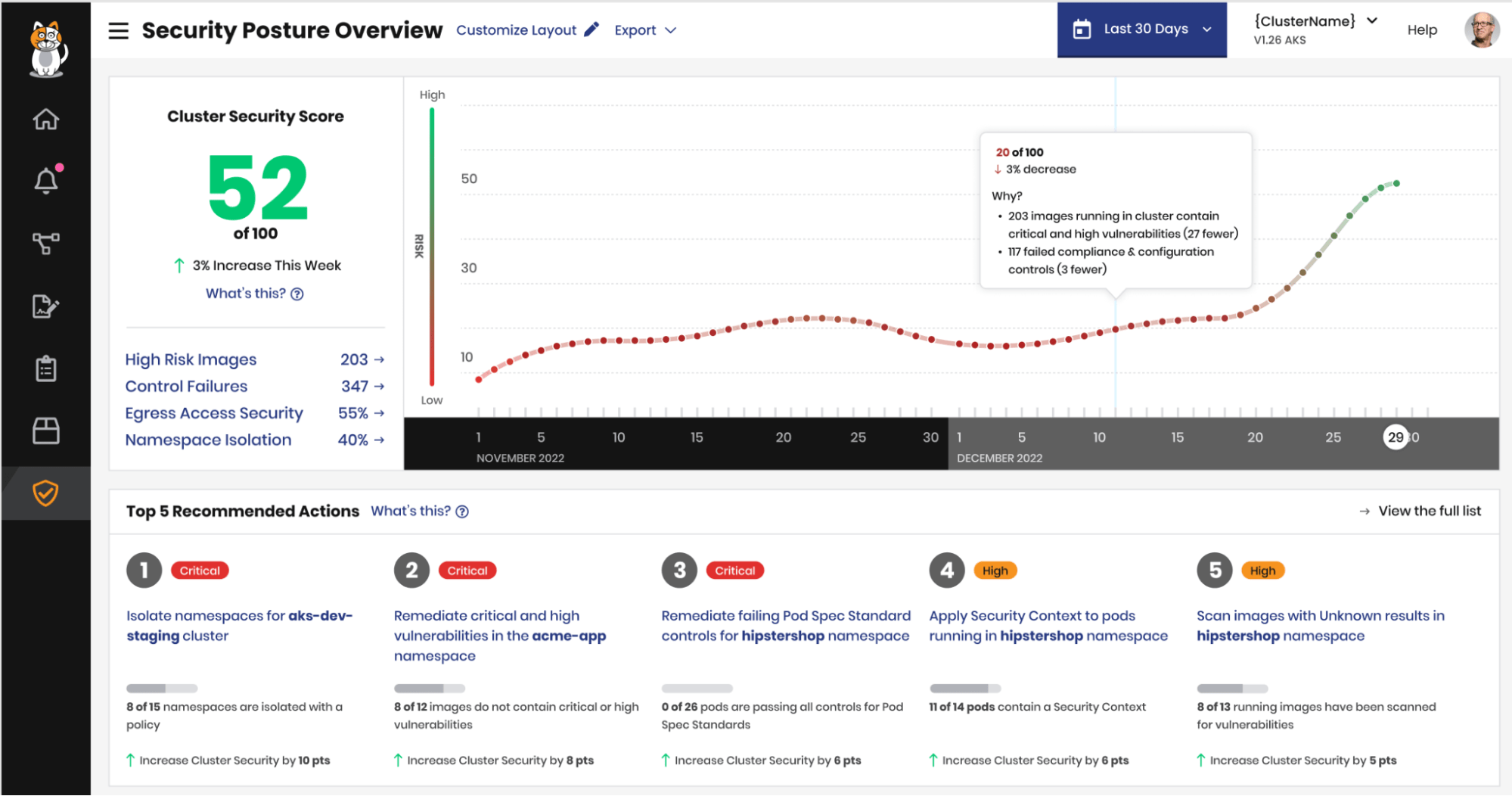
Calico Cloud will be able to generate a Cluster Security Score for each cluster you connect to the service to help you measure and track your security posture, and provides Recommended Actions to give you a prioritized list of actions you can take with Calico to improve your score.
In this blog post, I’m going to provide an overview of these new features and how they work, along with a sneak preview of what’s coming next. But before we dive in, let’s take a closer look at security posture management, what it means, and what it entails for you Kubernetes wranglers out there.
Security posture management for the home
Chances are when it comes to your home and the place that you live, you might have already thought about security posture management. Some questions that might assess the security posture of your home include the following:
- Do you have locks on all of the doors and entry points to your home?
- Are your windows secured and tamperproof?
- Is the wireless technology used to open and close your garage door secure?
- Do you have a fence around your property that is in good repair?
- Do you have outdoor flood lights that automatically turn on when motion is detected?
These are just a few examples of the “configuration” and “controls” you might consider for your home to improve its security posture. Security posture management is all about being proactive and doing your best to prevent bad things from happening.
For your home, this means assessing the physical security and physical integrity of where you live and making improvements to reduce the risk of a break-in. Security posture management for Kubernetes is very similar; it’s just that Kubernetes is a much more complex house. It might actually be more akin to getting a dozen or more houses ready to list on Airbnb!
Security posture management for Kubernetes
Kubernetes is awesome, right? There’s no denying that our favorite orchestrator changed the way we build, deploy, and run cloud-native applications for the better. But there’s a lot that goes into making it all work, and there’s a lot more to consider if you’re the person or team responsible for making sure it’s and workloads in it are secure.
Most teams responsible for operating Kubernetes have taken some initial steps that address aspects of security posture management. This typically comes in the form of shift left initiatives that focus on application security such as code scanning or image scanning in your CI/CD pipeline, looking for vulnerabilities, secrets, and more. You might also be doing configuration scanning for controls like CIS Benchmarks that assess the posture of infrastructure and the Kubernetes control plane.
Another aspect of posture management that is often overlooked are authorization rules and taking a least privileged approach to network security. Are namespaces effectively isolated with a policy? Is egress access and external communication with external endpoints explicitly authorized? This is very much akin to making sure there are locks on the entry points to your house.
Calico Cloud can help with a lot of the work that you do to improve your security posture, from scanning images in your pipeline to assessing CIS benchmarks or automatically isolating namespaces with Calico’s policy recommendations. But as you’re working through implementing these controls, how can you measure the progress that you’re making? And from the long list of things you could do, how do you decide what to do next?
This was our primary goal with introducing Security Scoring and Recommended Actions. A Cluster Security Score helps you measure and track your security posture over time, and also provides Recommended Actions to give you a prioritized list of actions you can take with Calico to improve your score.
Let’s dig in and see how it works.
Cluster Security Score: “Am I getting better or am I getting worse?”
For each cluster that you connect to Calico Cloud, we calculate a Cluster Security Score that measures its security posture. We also show you how the Cluster Security Score compares with 1-week ago and how it’s tracking over a 60-day period so you can answer the most important question when it comes to security: “Am I getting better or am I getting worse?”
This score provides a way to quantify and measure the security posture of your Kubernetes cluster based on the following risk types: namespace isolation, egress access, high risk images, and control failures*.
- Namespace Isolation ensures that every namespace is isolated with a Calico policy
- Egress Access ensures that communication with endpoints external to a cluster is authorized and explicitly secured with a Calico policy
- High Risk Images measures the number of running images that contain Critical or High vulnerabilities OR do not have scan results
- Control Failures* measures the number of misconfigurations of the k8s control plane, nodes, and application resources (e.g. CIS benchmarks, setting resource limits on pod specs)
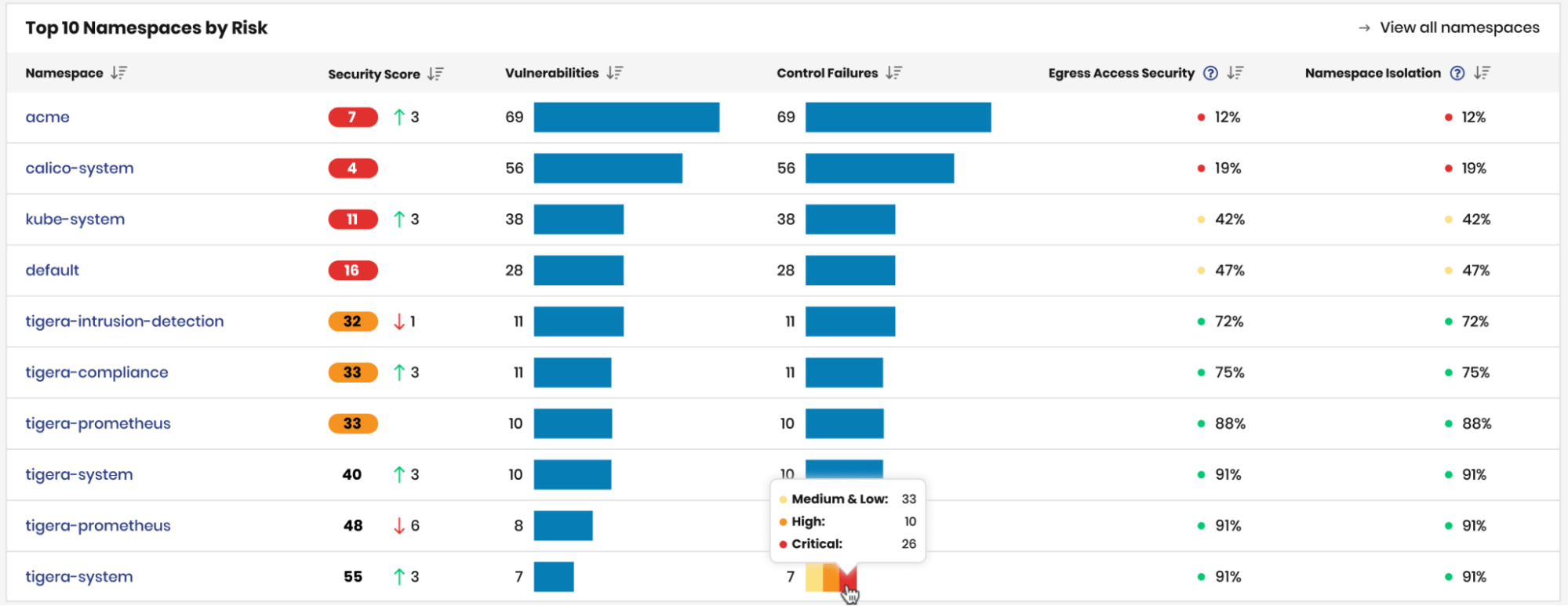
Security scores are also calculated at a namespace level to quickly identify specific tenants/applications that may be higher risk.
Top 10 Namespaces by Risk
Improving your security posture with Recommended Actions
In the process of calculating the security scores for a cluster and its namespace, Calico Cloud can also provide a prioritized list of Recommended Actions to improve your score and strengthen your security posture.
Recommended Actions are prioritized by how much they will improve your Cluster Security Score (i.e. they’re prioritized by how much they will improve your security posture and reduce risk).
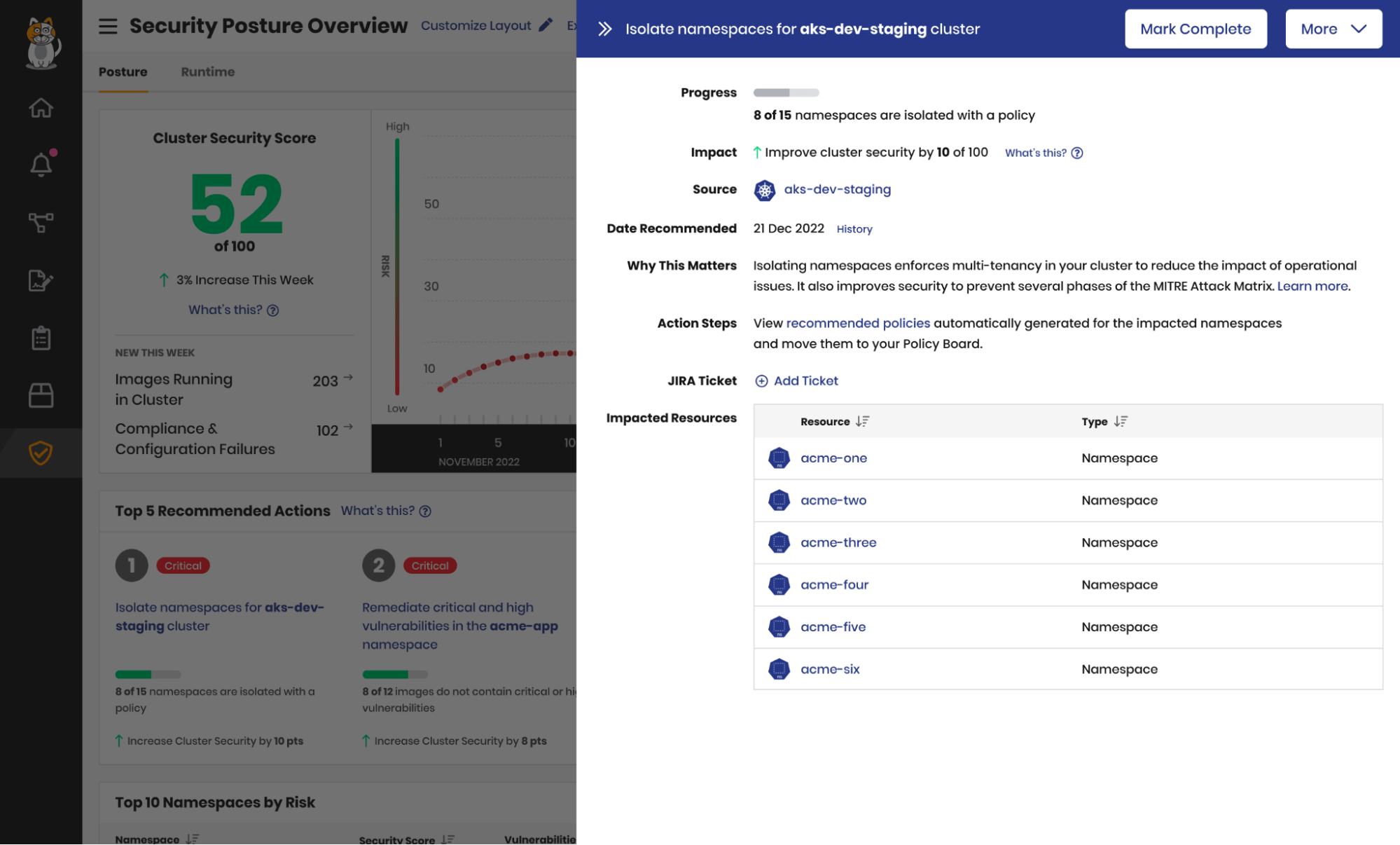
Prototype for Recommended Action details panel
Each recommendation corresponds to a risk type, such as namespace isolation or high risk images, and provides the necessary context to understand why it’s important, which resources are affected, and where you need to go in Calico Cloud to complete that action.
Recommended actions can also be dismissed and later reactivated, giving you the flexibility to temporarily accept risk and exclude it from scoring.
What’s next?
We’ll be releasing a tech-preview of Security Scoring and Recommended Actions in Calico Cloud before the end of the year, and we’re excited to work with some of our existing customers to fine-tune the experience.
(*) Next year, we’ll also be adding Control Failures as another contributing risk type for security scoring to assess configuration frameworks like CIS Benchmarks, and going further with some of the in-product workflows we enable for users around the actions they take to address gaps in security posture management.
If you’re interested in learning more about how Calico Cloud can help you improve the security posture of your Kubernetes clusters, sign up at calicocloud.io for a free trial.
Ready to try Calico node-specific policies? Sign up for a free trial of Calico Cloud.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!