Advancements in machine learning, unified policy, cloud integration, flow log, and user interface bolster Kubernetes security efficacy and operations efficiency.
Tigera is excited to announce several new capabilities with Tigera Secure Enterprise Edition 2.3, extending the ability to uncover sophisticated Kubernetes attacks. Tigera Anomaly Detection capabilities provide insight into unusual behaviors that compromise the security and performance of Kubernetes environments. The solution offers the best of breed anomaly detection by offering both machine learning and rule-based capabilities to handle large and complex Kubernetes network datasets. This release empowers businesses to detect and respond to reconnaissance scans, protocol deviation activities, and volumetric deviations activities. Detailed forensics for every detection enable security teams to resolve incidents faster than before. This major product release demonstrates Tigera’s long-term vision to deliver a comprehensive Kubernetes network security solution.
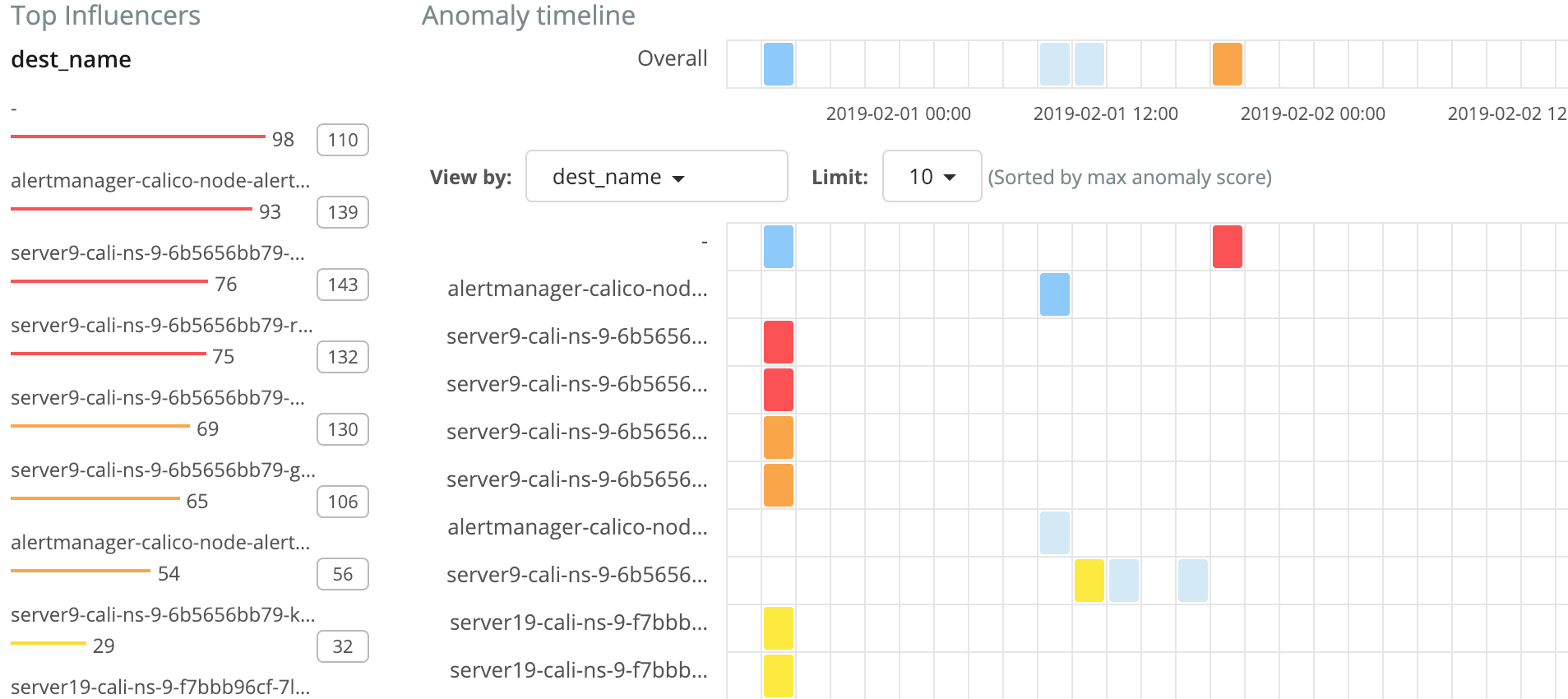
Figure 1 – Kubernetes pod anomaly behavior heatmap provided within Tigera Secure Enterprise Edition 2.3.
In addition to the new Anomaly Detection features, Tigera Secure Enterprise Edition 2.3 also brings the following additional capabilities:
-
- Enterprise Calico Policy – Enhanced with web application security support. The solution enables a single location for multi-layer enforcement with network and web application security policies. Multi-layer enforcement increases operations efficiency by reducing the need to write and manage multiple policies for different layers. In addition, Enterprise Calico Policy provides tiering and web application visibility capabilities beyond Open Source Calico Policy. Tiering capabilities enable enterprise teams to collaborate in a concurrent manner. Web application security insight helps meet security and compliance requirements.
-
- Security Groups and Kubernetes Policy Integration – Enables fine-grained policy control within Amazon Web Services (AWS) Security Groups. This capability allows access control between VPC members and pods, and vice versa. The solution extends a zero-trust security model to non-Kubernetes resources within VPC members by integrating Network Policy and AWS Security Groups.
-
- Network Flow and Audit Log — Enhanced flow logs with web application workload context containing allowed and denied HTTPS requests. Audit logs provide detail around authorized and unauthorized policy changes. Log retention has been extended to seven days for flow logs and a year for audit logs. Amazon S3 integration easily enables offline storage that helps meet multiple-year compliance retention requirements.
- User Interface with RBAC — Improved user interface with role-based access control (RBAC) that enables teams such as DevOps, Platform, and Security to have their own proper level of access. Each team can now resolve security and operational issues quicker with access to their own set of network flow data. Administrators can operate in a more efficient manner by delegating network troubleshooting to individual DevOps teams instead of relying on a centralized function.
Highlights of Tigera Secure Enterprise Edition 2.3
This new release builds upon the proven success of Tigera Secure Enterprise Edition. Large and complex Kubernetes network datasets make it difficult to detect malicious activities with traditional monitoring tools.
Anomaly Detection, powered by machine learning, deepens visibly into sophisticated Kubernetes attacks. It also addresses an essential compliance requirement by monitoring infrastructure and applications for unexpected behavior. Enterprise Calico Policy enables unified defense-in-depth web application security, even when infrastructure is compromised. Security Groups’ integration enhances Kubernetes’ security posture with fine-grain access control between resources in AWS security groups. The enhanced network flow and audit logs help address ever-growing compliance requirements. The new RBAC UI enhancements empower teams to work independently and also collaborate to resolve outage, security, and monitoring issues with Kubernetes.
Please schedule a demo for more information.
————————————————-
Free Online Training
Access Live and On-Demand Kubernetes Tutorials
Calico Enterprise – Free Trial
Solve Common Kubernetes Roadblocks and Advance Your Enterprise Adoption
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!