Data exfiltration and ransomware attacks in cloud-native applications are evolving cyber threats that pose significant risks to organizations, leading to substantial financial losses, reputational damage, and operational disruptions. As Kubernetes adoption grows for running containerized applications, it becomes imperative to address the unique security challenges it presents. This article explores the economic impact of data exfiltration and ransomware attacks, their modus operandi in Kubernetes environments, and effective strategies to secure egress traffic. We will delve into the implementation of DNS policies and networksets, their role in simplifying egress control enforcement, and the importance of monitoring and alerting for suspicious egress activity. By adopting these measures, organizations can strengthen their containerized application’s security posture running in Kubernetes and mitigate the risks associated with these prevalent cyber threats.
Economic impact of data exfiltration and ransomware attacks
Data exfiltration and ransomware attacks have emerged as formidable threats to organizations worldwide, causing substantial financial losses and service outage. According to IBM’s 2023 Cost of a Data Breach report, data exfiltration attacks alone cost businesses an average of $3.86 million per incident, a staggering figure that underscores the severity of this issue. Ransomware attacks, on the other hand, can inflict even more damage, with the average cost reaching a staggering $4.62 million.
According to IBM’s 2023 Cost of a Data Breach report, data exfiltration attacks alone cost businesses an average of $3.86 million per incident.
Beyond the immediate financial impact, data exfiltration and ransomware attacks can have long-term consequences that hinder a company’s growth and competitiveness. The compromise of sensitive data can undermine customer confidence and erode brand reputation, making it challenging to attract and retain customers. Moreover, the disruption caused by these attacks can hamper innovation and hinder a company’s ability to adapt to evolving market demands. In today’s fast-paced business environment, organizations that fall victim to such attacks may find themselves struggling to keep up with competitors who prioritize cybersecurity and data protection.
The economic impact of data exfiltration and ransomware attacks underscores the urgent need for organizations to prioritize cybersecurity measures and invest in robust data protection strategies. By implementing effective security controls, monitoring systems, and incident response plans, organizations can mitigate the risks associated with these threats and safeguard their critical data and operations.
How do these attacks happen in Kubernetes applications?
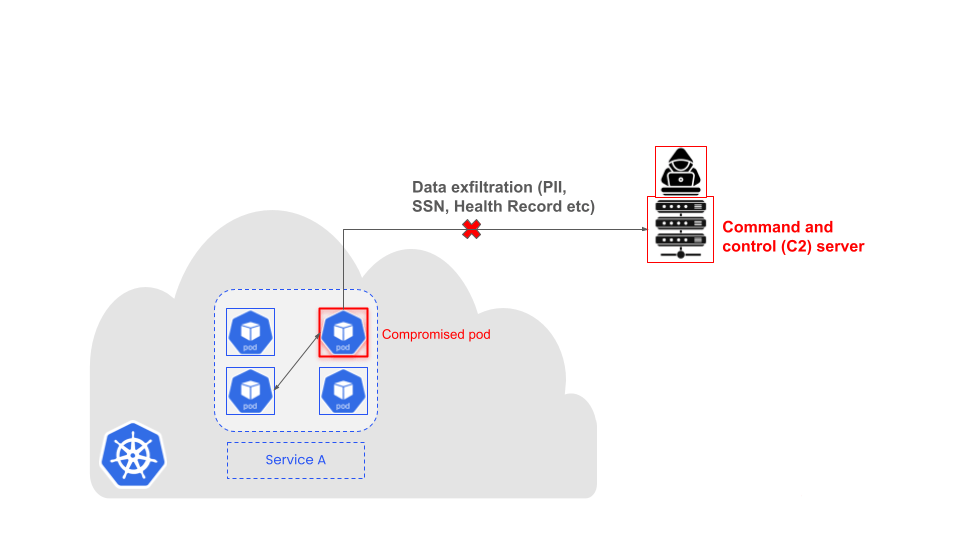
In Kubernetes applications, data exfiltration and ransomware attacks can occur due to the exploitation of vulnerabilities and misconfigurations. Attackers can exploit vulnerabilities by gaining access to the cluster and deploying malware that bypasses the default security controls.
Lack of proper egress controls can allow malicious pods to exfiltrate sensitive data to external attacker-controlled servers.
The absence of proper monitoring and alerting for unusual egress activity makes it difficult to detect and respond to data exfiltration attempts in a timely manner. By implementing robust monitoring and alerting mechanisms, organizations can detect suspicious egress activity and take immediate action to mitigate the risk of data exfiltration and ransomware attacks.
Ways to secure egress traffic in Kubernetes
In Kubernetes, implementing robust egress access controls is crucial for securing egress traffic and mitigating the risks of data exfiltration and ransomware attacks. Here are some effective strategies to secure egress traffic in Kubernetes:
Implement network policies
Network policies allow you to control the communication between pods and services within your cluster, as well as with external resources. By defining network policies, you can specify which pods and services are allowed to communicate with each other, and which external IP addresses and domains they can access. This helps to limit the potential attack surface and prevent unauthorized access to sensitive data.
Specify trusted IP addresses
When creating network policies, it is important to specify trusted IP addresses or domains that your pods and services can communicate with. This helps to ensure that pods are only communicating with authorized external destinations and reduces the risk of data exfiltration attacks.
Use DNS policies
3rd-party container network security solutions like Calico support DNS policies that allow the use of fully qualified domain names to allow traffic to destinations outside of a cluster. Using domain names in policies to communicate to services outside of the cluster is often operationally simpler and more robust than using IP addresses. In particular, they are useful when an external service does not map to a well-known set of static IP addresses. These solutions trust DNS information only from its list of DNS trusted servers. Using trusted DNS servers provides control over the resolution of DNS names for pods and services. By using DNS policies, you can prevent attackers from redirecting traffic to malicious sites or intercepting sensitive data by spoofing DNS responses.
Monitor egress traffic
Continuous monitoring of egress traffic is essential for detecting any suspicious or anomalous activity. By implementing monitoring solutions, you can gain visibility into the network traffic generated by your pods and services, identify any deviations from normal patterns, and promptly investigate potential security incidents.
Regularly review and update security configurations
The Kubernetes landscape is constantly evolving, and new vulnerabilities and threats emerge regularly. It is crucial to regularly review and update your security configurations, including network policies, DNS policies, and monitoring mechanisms, to ensure that your Kubernetes cluster remains secure against the latest threats.
Organizations can significantly reduce the risks of data exfiltration and ransomware attacks in Kubernetes environments by implementing these strategies and maintaining a proactive approach to egress security.
How DNS policies and networksets simplify enforcement of egress controls
This section discusses how Calico DNS policies and networksets can be used to simplify the enforcement of egress controls in Kubernetes clusters. DNS policies allow you to control which domains your pods can access, while NetworkSets allow you to define a set of IP addresses or domains that your pods can access. These two tools can be used together to create a more comprehensive egress control strategy.
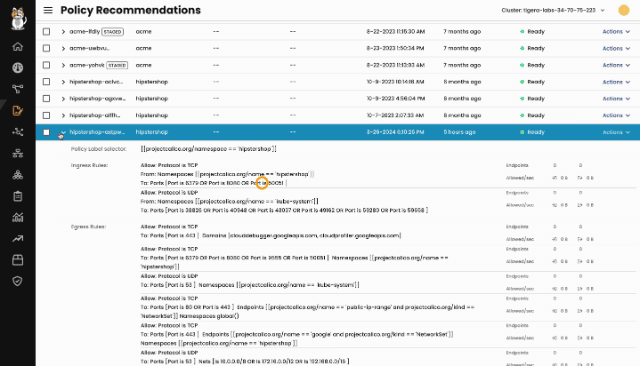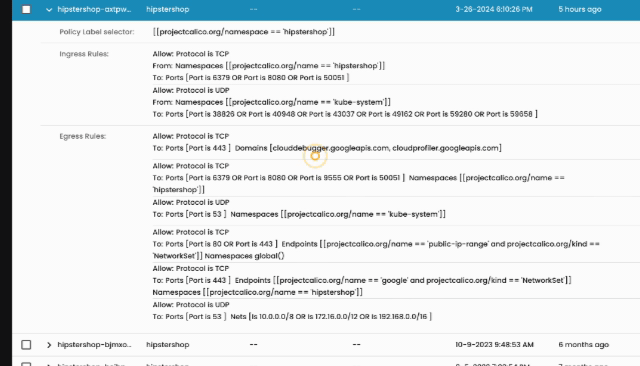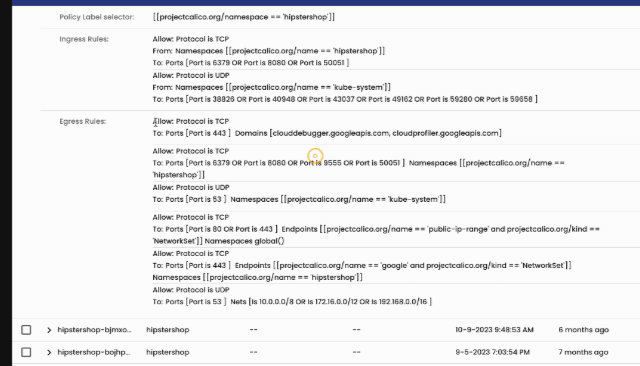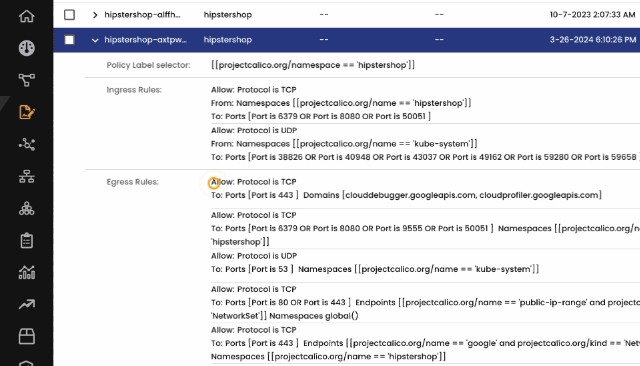
- DNS policies are a powerful tool for controlling egress traffic in Kubernetes. Without the support for DNS policies you are limited by allowing only IP addresses to be specified in network policies. This creates an operational overhead when the destination IP address keeps changing. By implementing DNS policies in conjunction with default-deny, you can prevent data exfiltration and ransomware attacks, as it prevents your pods from communicating with malicious hosts.
- NetworkSets are another useful tool for controlling egress traffic in Kubernetes. When you demand efficiency and scalability in managing a specific set of IP addresses or domains, network sets are your ultimate solution. This can be useful for allowing your pods to access specific services, such as a database or a load balancer, while preventing them from accessing other hosts.
Using DNS policies and NetworkSets together, you can create a more comprehensive egress control strategy that will help to protect your Kubernetes applications from data exfiltration and ransomware attacks.
Monitoring and alerting for suspicious egress activity
It is crucial to detect and respond to data exfiltration attempts in Kubernetes clusters as they increasingly run business-critical applications. By keeping a vigilant watch on network traffic, organizations can identify potential threats and take immediate action to mitigate risks.
One effective approach is to leverage security tools and services that provide real-time monitoring and analysis of network traffic. These tools can detect anomalies in egress traffic patterns and generate alerts when suspicious activities are identified. Additionally, organizations should implement log analysis and monitoring to capture and analyze relevant logs from Kubernetes components, such as kube-proxy and Envoy, to gain insights into egress traffic behavior.
Configuring alerts and notifications is essential for ensuring prompt responses to suspicious egress activity. Alerts should be set up to notify security teams or administrators in real time when predefined thresholds are met or specific patterns of egress traffic are detected. This enables timely investigation and containment of potential data exfiltration attempts.
In summary, monitoring and alerting for suspicious egress activity play a critical role in preventing data exfiltration in Kubernetes. By implementing these measures, organizations can enhance their cybersecurity posture and mitigate the risks associated with data breaches and ransomware attacks.
Conclusion
In conclusion, organizations must prioritize implementing robust egress access controls to safeguard their data and mitigate the risks of data exfiltration and ransomware attacks in Kubernetes environments. By adopting best practices such as implementing DNS policies and networksets, organizations can gain granular control over egress traffic and restrict access to trusted destinations. Additionally, continuous monitoring and alerting for suspicious egress activity empower organizations to detect and respond promptly to potential threats, minimizing the impact on their operations and sensitive data. By adhering to these security measures, organizations can enhance their overall security posture and ensure the integrity and confidentiality of their data within Kubernetes environments.
Curious to learn how Calico can help bolster egress security? Learn more about DNS policies and Network Sets.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!