As organizations adopt Microsoft AKS at scale, they need to enforce namespace or even workload-based isolation for better security and compliance. This isolation, often referred to as microsegmentation, can help prevent the lateral movement of threats inside Kubernetes clusters, achieve compliance by limiting communication across workloads or namespaces, and enable multi-tenancy by limiting communication.
Kubernetes native security features such as RBAC, pod security policies, and network policies are important, but they often fall short of meeting specific needs. Calico seamlessly integrates with AKS to provide enhanced security including advanced access controls, microsegmentation, threat detection and observability. For a quick reference on what Calico offers with AKS, check out this datasheet: How Calico Strengthens Cloud Native Application Security for Microsoft AKS Deployments.
Microsegmentation with Calico
Calico enables microsegmentation by creating fine-grained network policies that control traffic between pods and namespaces. This allows you to isolate critical workloads, prevent lateral movement of threats, and meet compliance requirements.
For example, you can create a policy that restricts communication between pods in different namespaces, or between pods that run different applications. You can also create policies that allow only certain types of traffic, such as traffic to a database or to a web server.
Microsegmentation with Calico offers a number of benefits, including:
- Improved security: Microsegmentation can help prevent the lateral movement of threats inside Kubernetes clusters, making it more difficult for attackers to spread across your environment.
- Enhanced compliance: Microsegmentation can help you meet compliance requirements by limiting communication across workloads or namespaces.
- Enabled multi-tenancy: Microsegmentation can help you enable multi-tenancy in your Kubernetes cluster by limiting communication between tenants.
- Simplified management: Calico Enterprise provides a centralized interface for managing network policies, making it easier to enforce microsegmentation across your cluster.
Microsegmentation is essential for securing AKS at scale. Calico provides a comprehensive solution for microsegmentation, offering advanced network security controls and threat detection capabilities. By implementing microsegmentation with Calico Enterprise, you can improve your security posture, meet compliance requirements, and enable multi-tenancy in your Kubernetes cluster. Tigera’s learn guide, AKS Security: The Basics and 5 Critical Best Practices, will offer additional insights into security best practices for AKS.
Using Security Policies to Isolate Workloads in Azure Kubernetes Service
Below I’m describing how, using Calico Enterprise Service Graph, Policy Recommendation and Threat Defense Alerts, we can:
- Allow only expected traffic among pods of an application
- Stage a recommended policy
- Test non-expected traffic
- Get alerts on suspicious domains and IPs
STEP 1: Deploy a test application
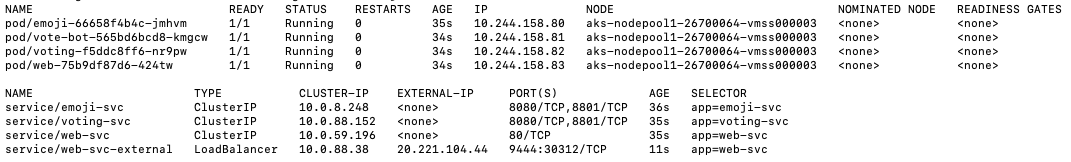
For this blog post, I deployed the application Emojivoto, which allows users to vote for their favorite emoji, and tracks votes received on a leaderboard. It is composed of the following services and pods:
- emojivoto-web: Web frontend and REST API
- emojivoto-emoji-svc: gRPC API for finding and listing emoji
- emojivoto-voting-svc: gRPC API for voting and leaderboard
- vote-bot: It generates traffic by voting on emoji “randomly”
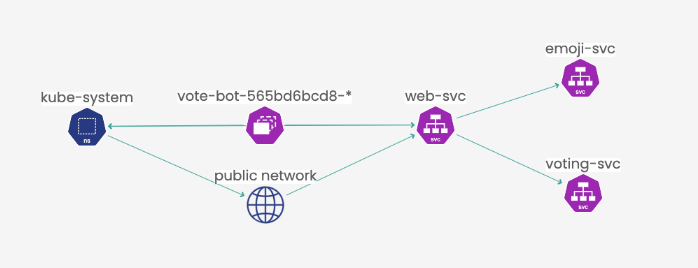
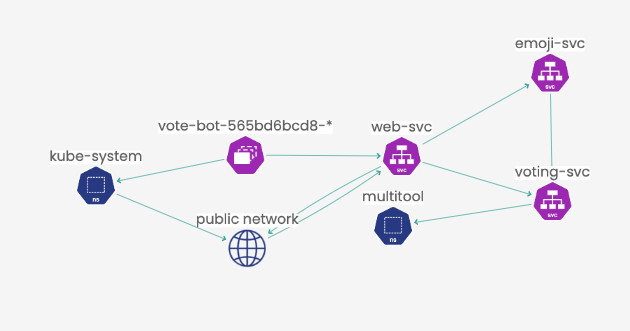
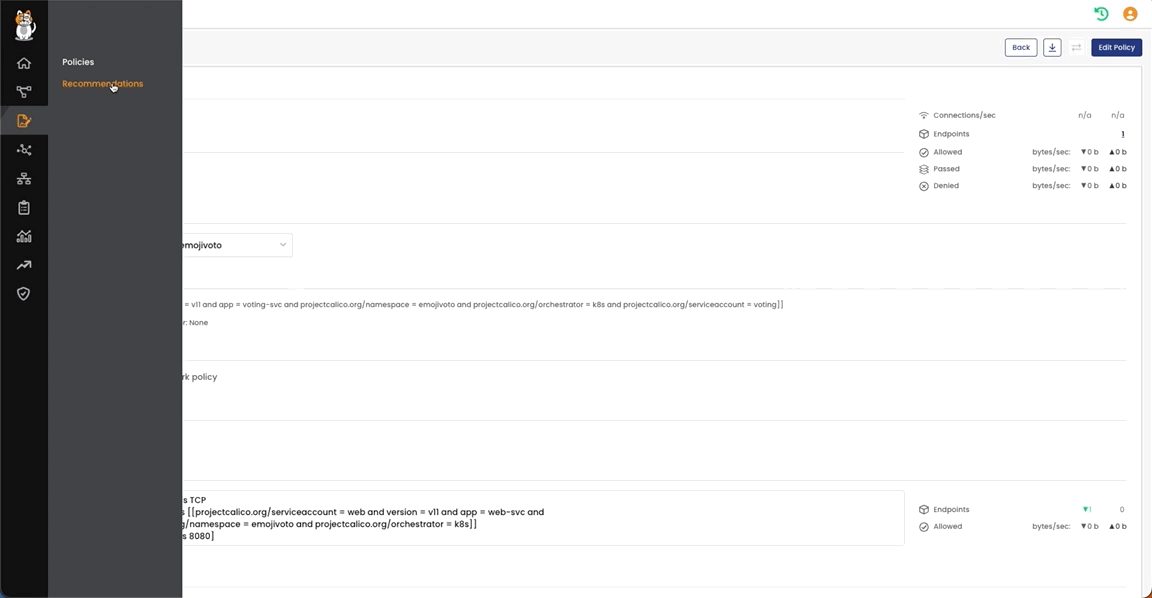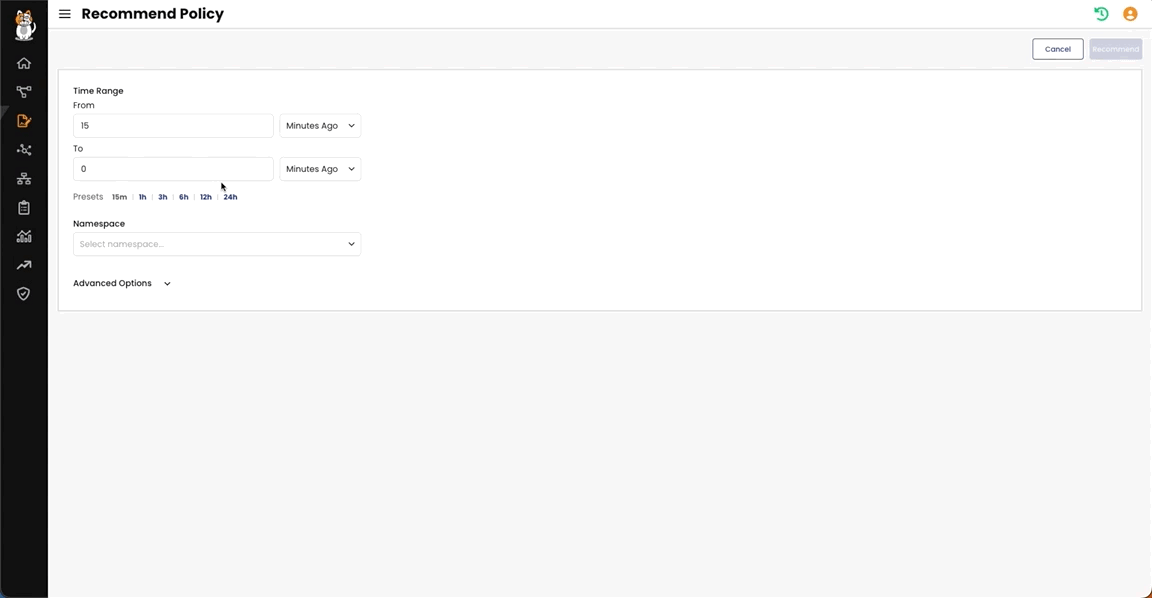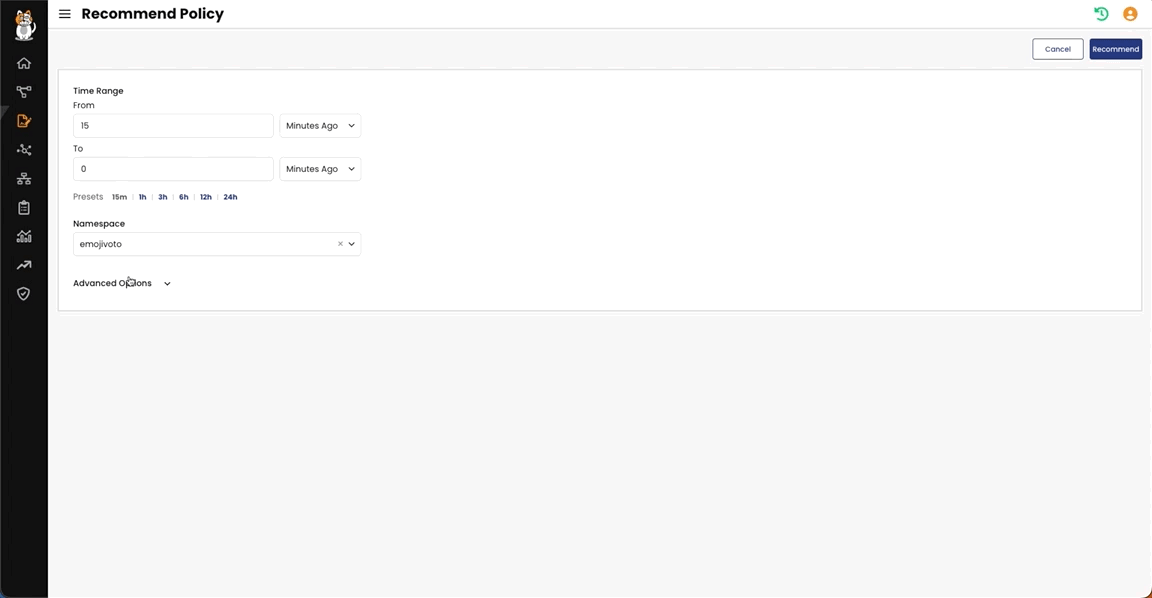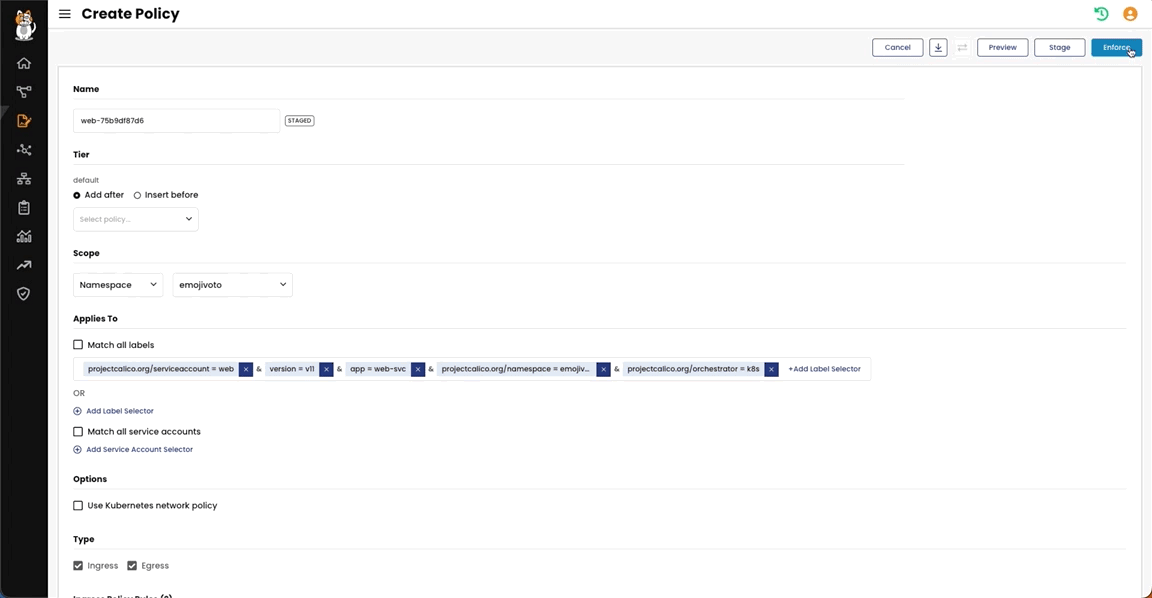
Here is the Service Graph for the expected traffic generated by the Emojivoto app components.
Here some details on services and pods:
STEP 2: Use Policy recommendation tool to generate and stage fine-tune policies
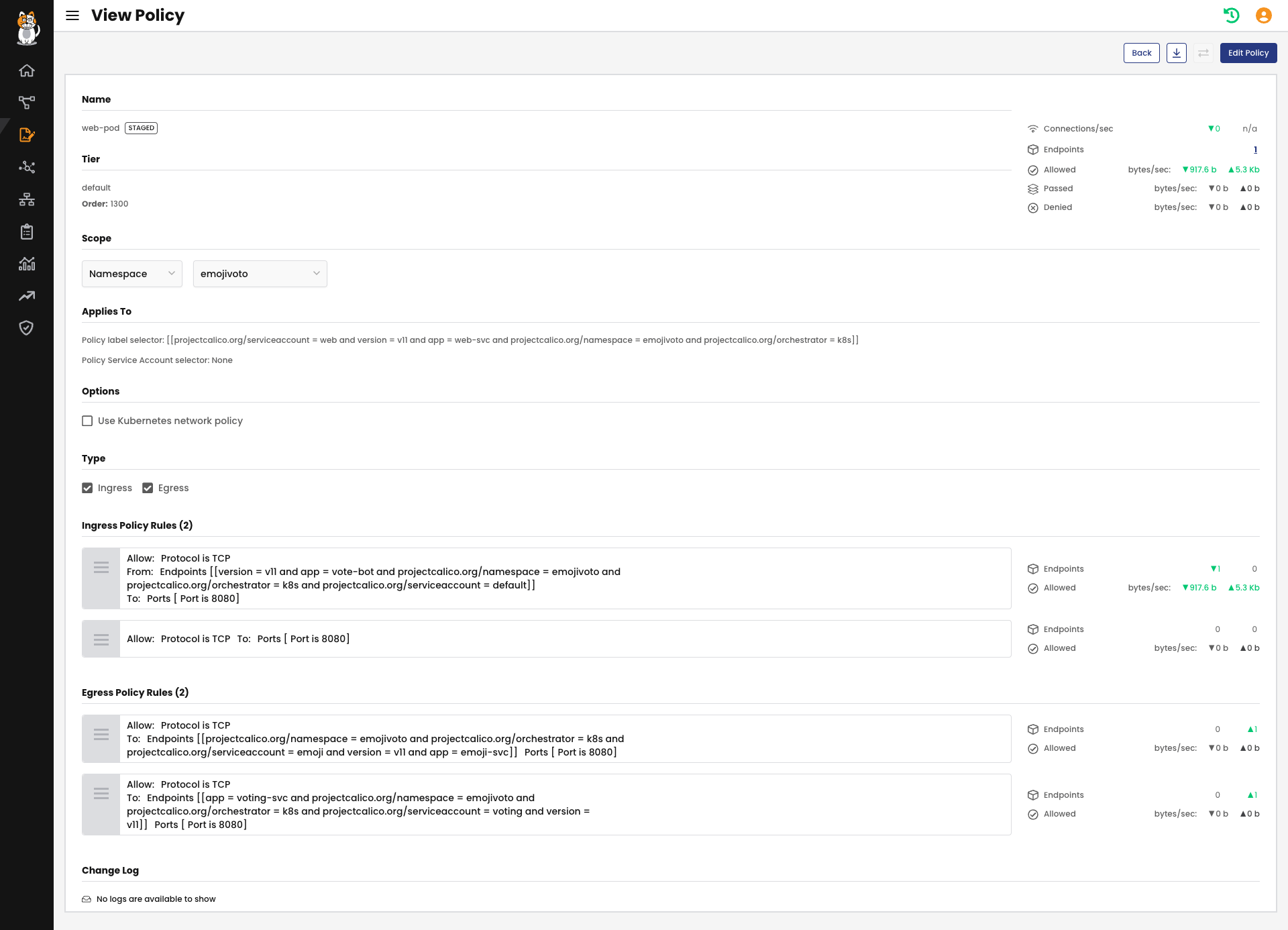
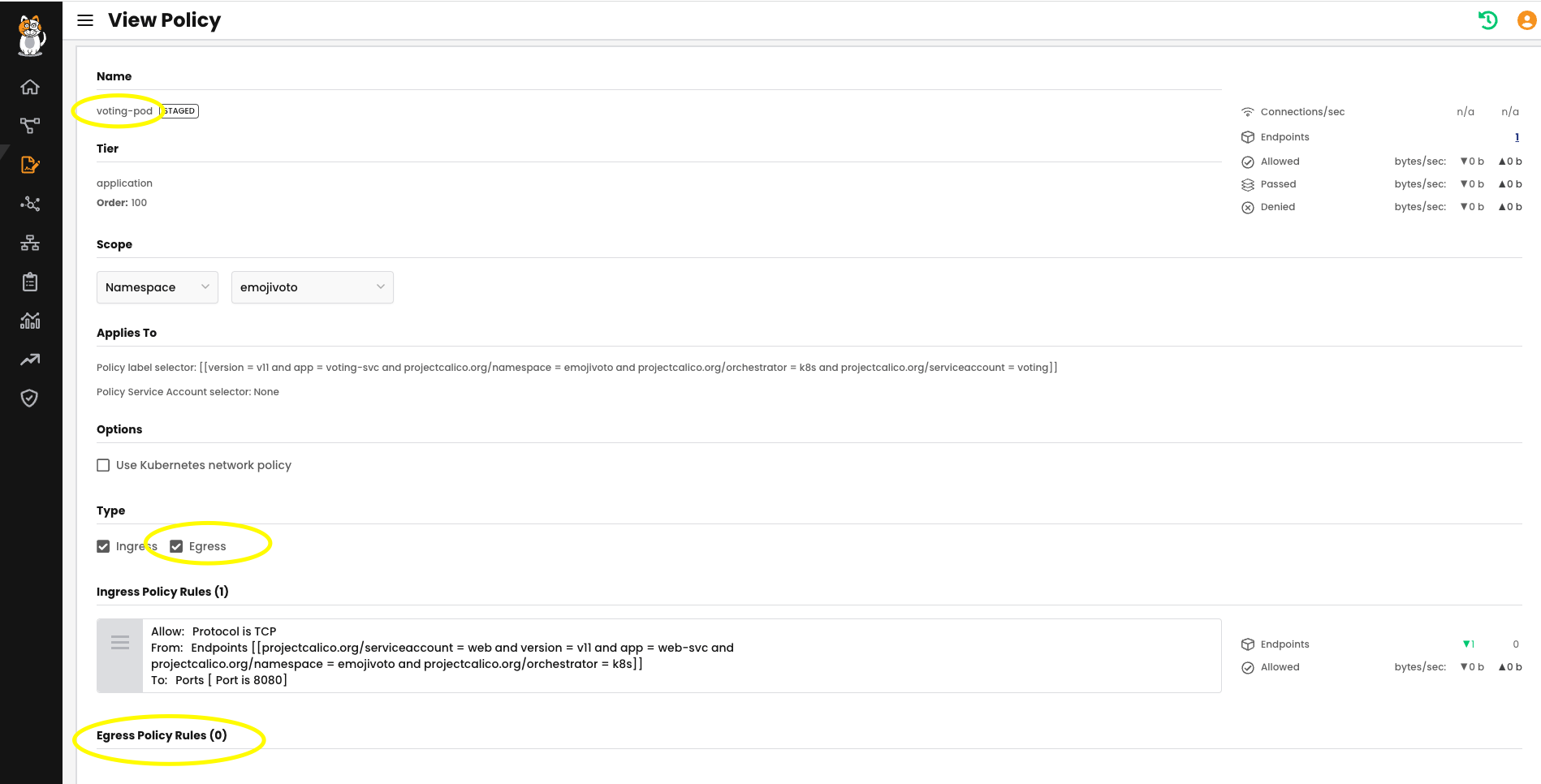
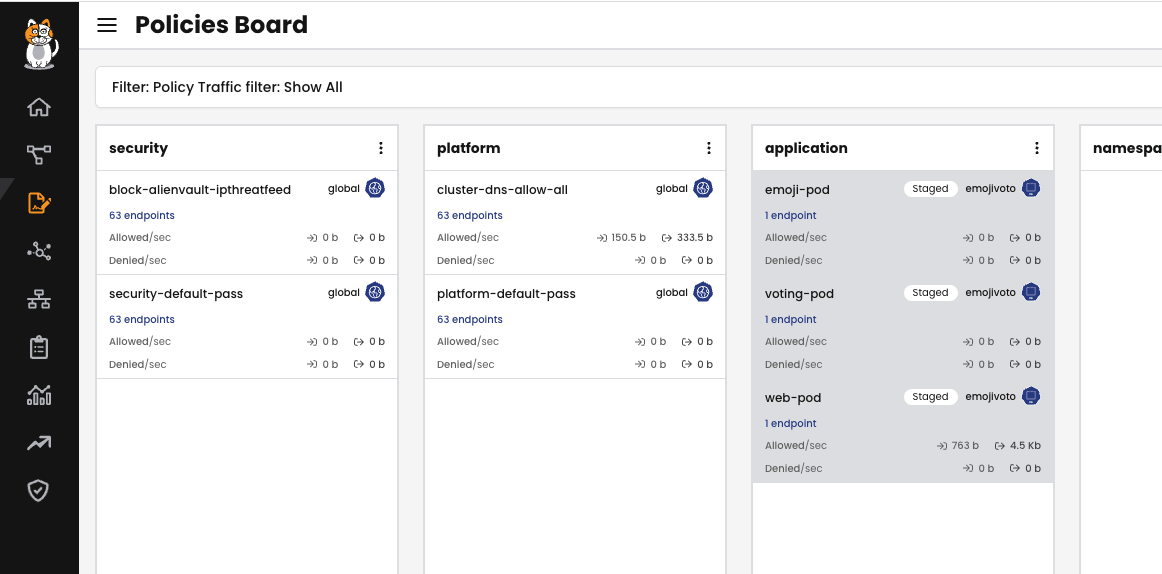
Policy Recommendation tool automatically inspects traffic to generate policies which can be edited and staged. Here an example of a staged policy:
In this policy, we are allowing only ingress and egress traffic scoping the web-pod for the expected usage.
Here is how this is done:
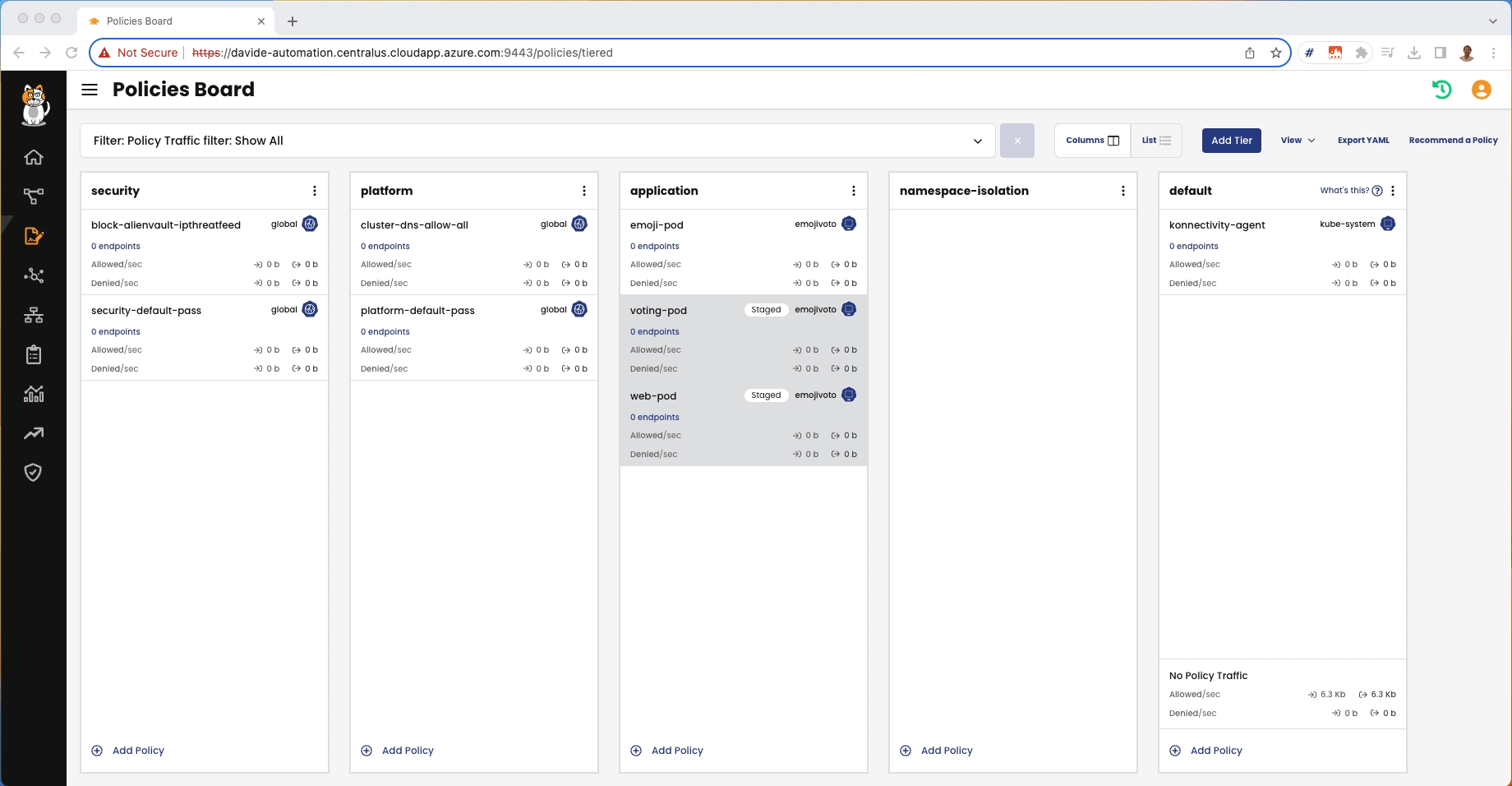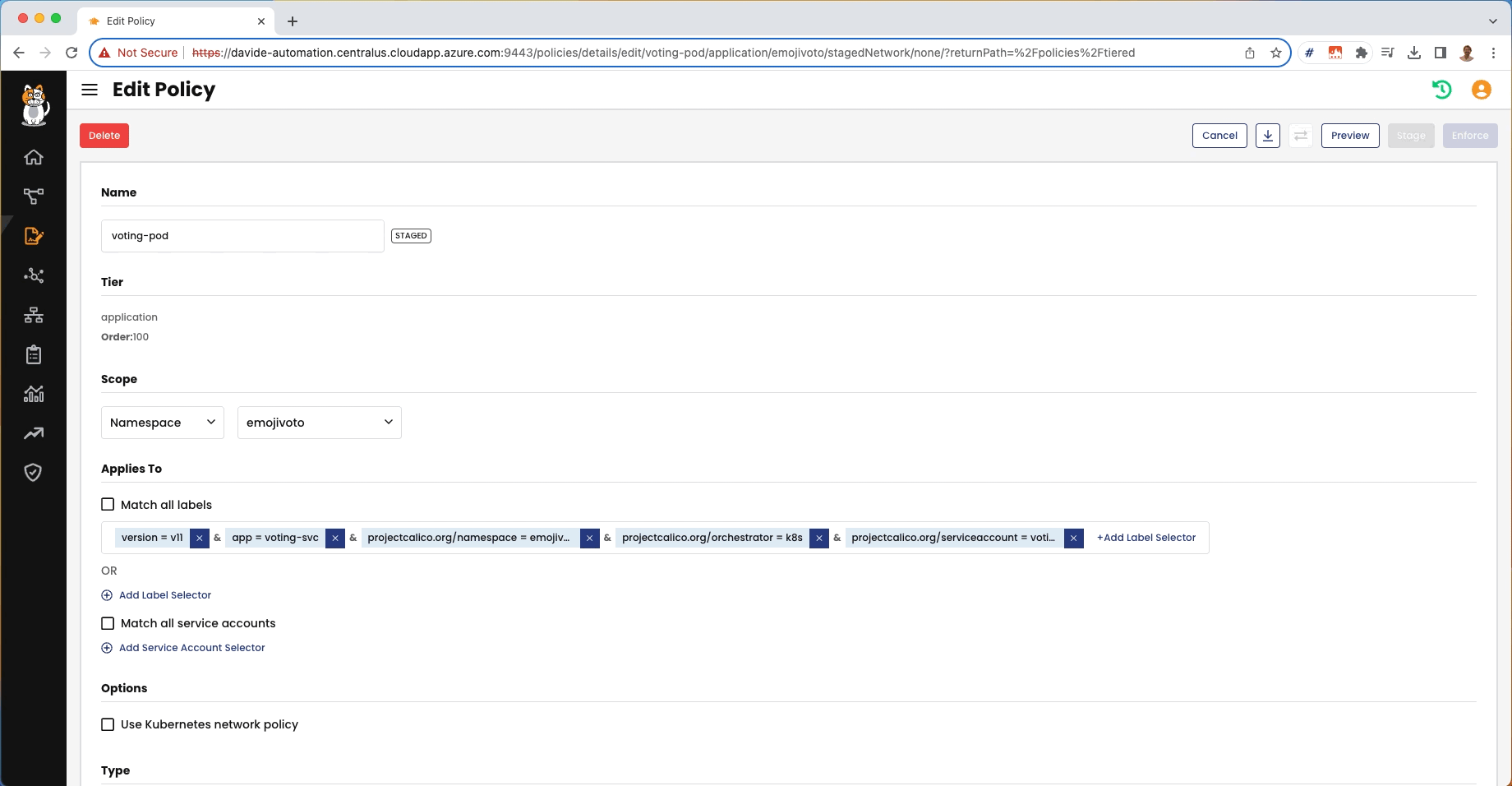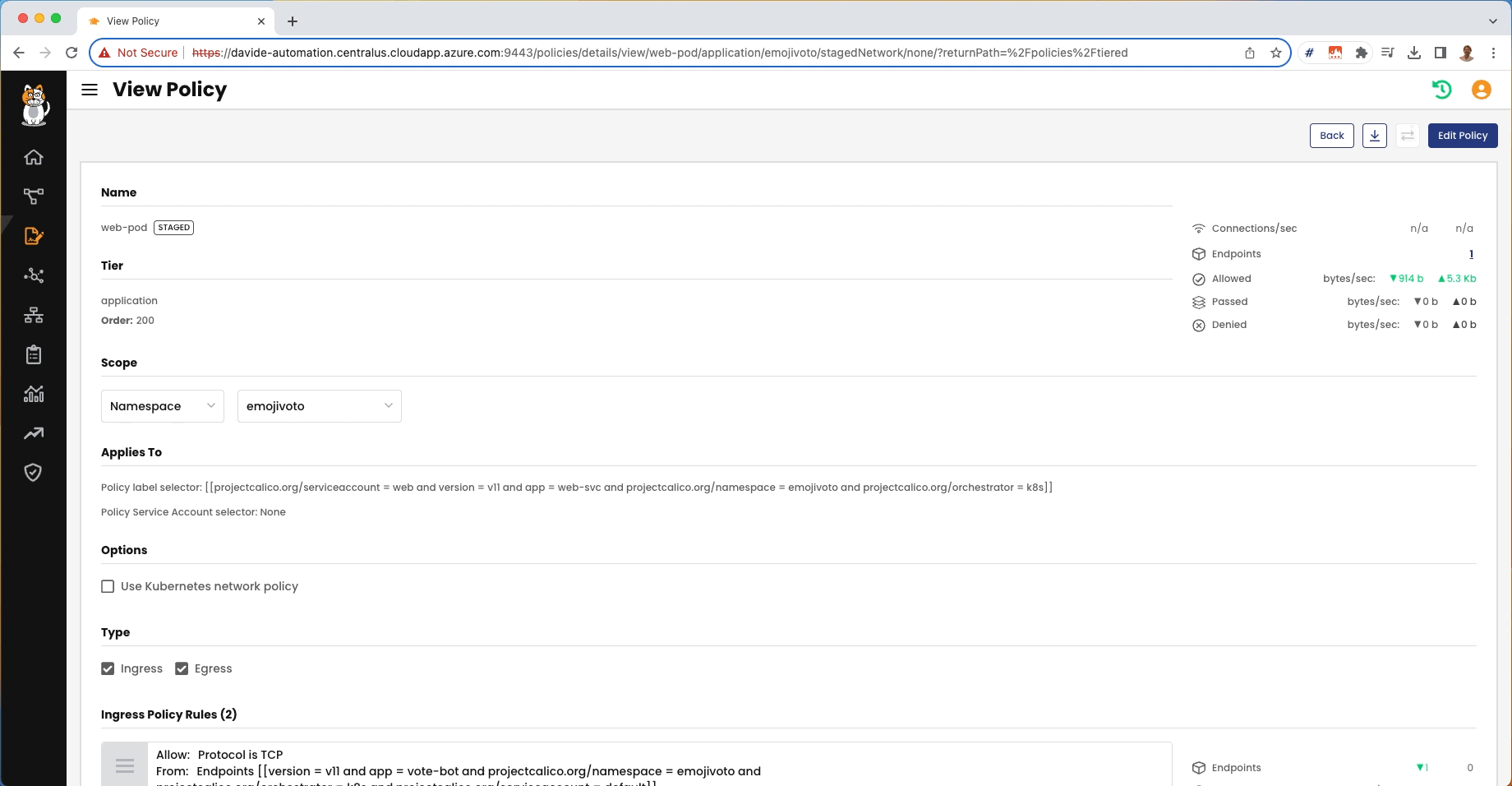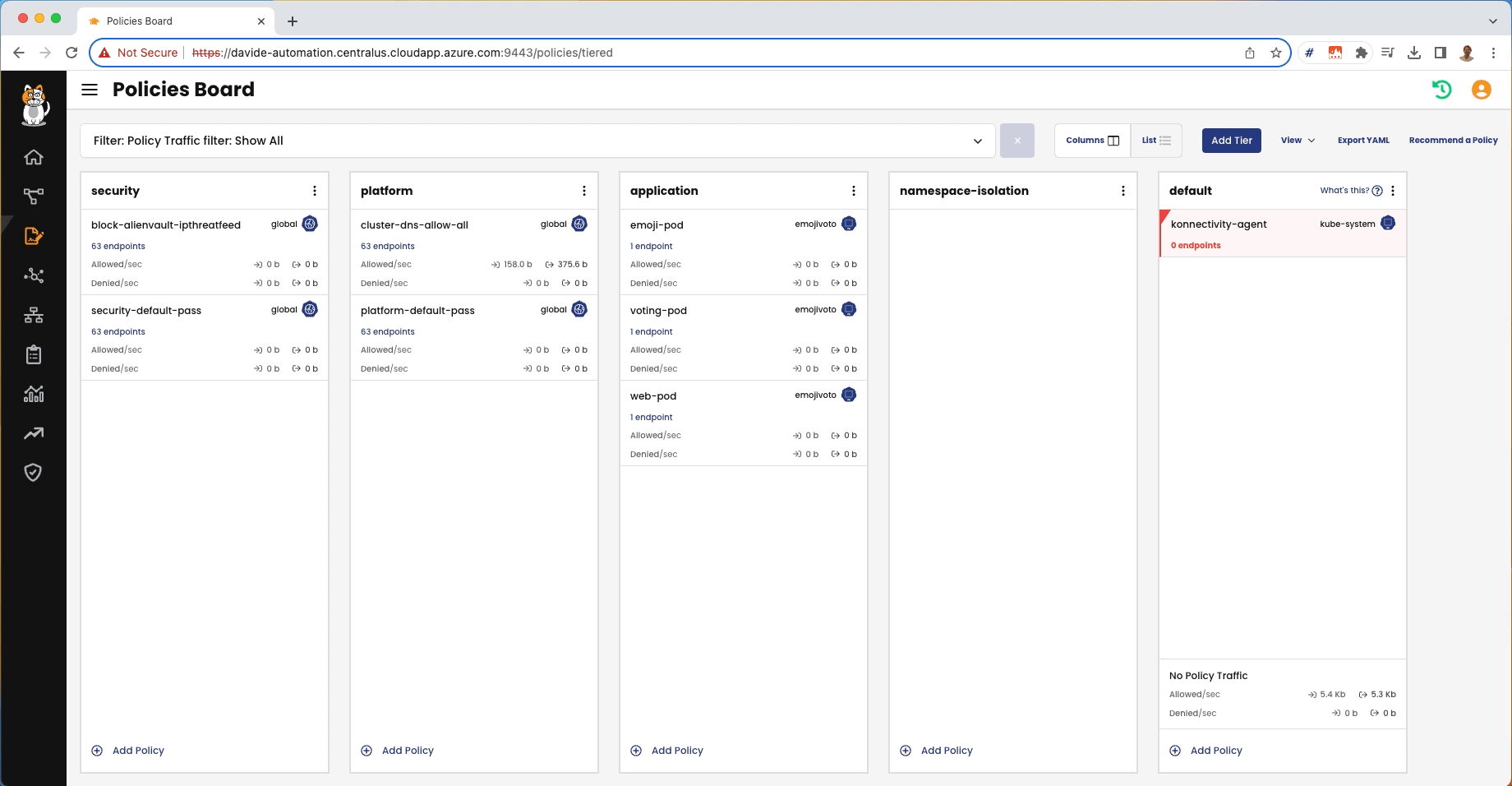
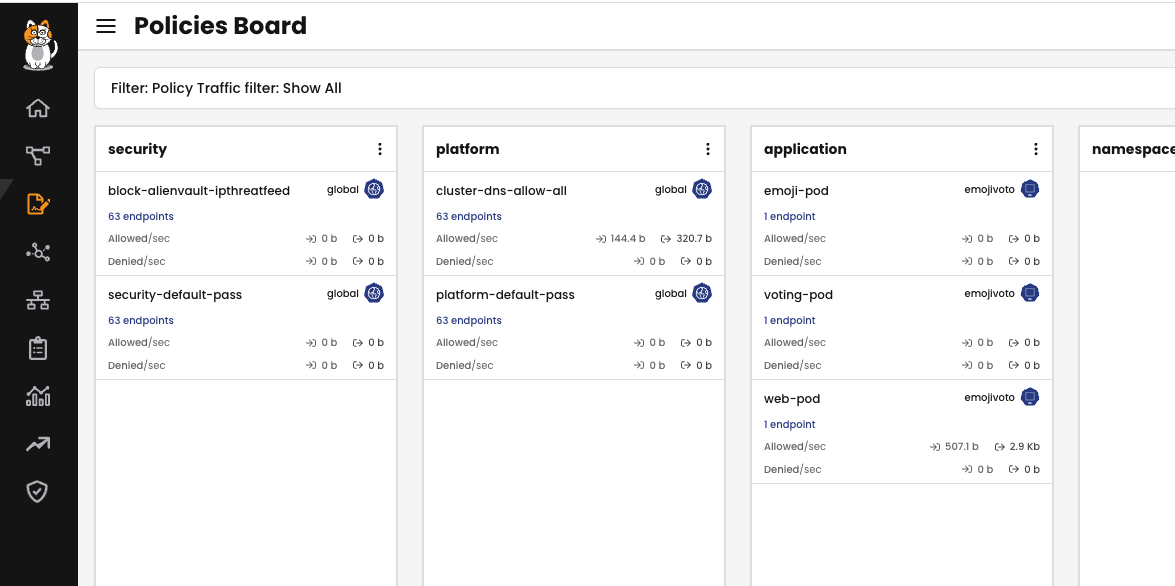
From the Policy Board, we can see that the staged policies are nor denying anything or detecting an non-expected traffic:
STEP 3: Deploy a Multitool application and generate some non-expected traffic
Now I’m going to simulate a compromised pod, by generating some non-expected traffic which should trigger the staged policies.
Here is the Multitool pod:
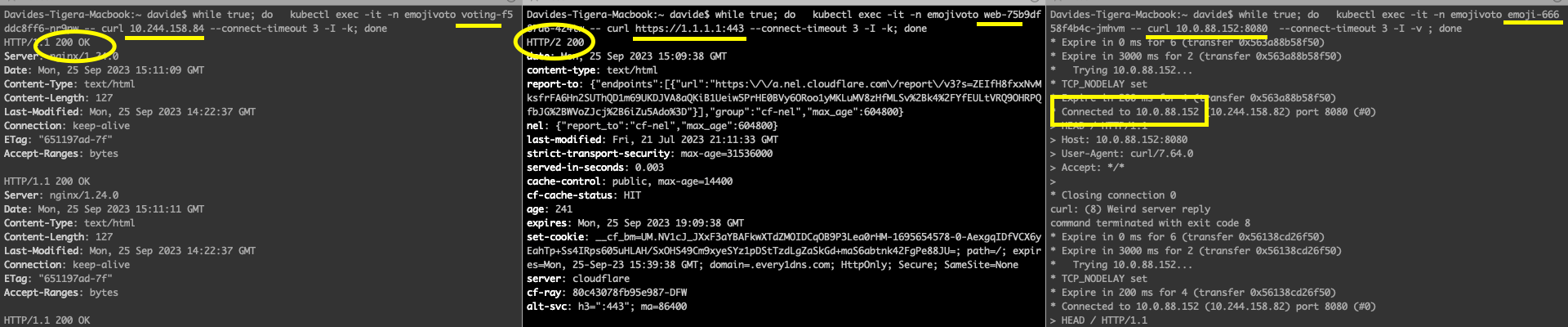
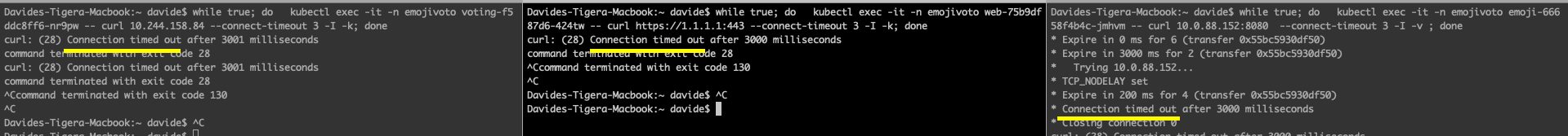
Non-expected traffic:
- voting-pod tries to curl multitool pod
- web-pod tries to curl 1.1.1.1 on port 443
- Emoji pod tries to curl voting service on port 8080
At this stage, everything is allowed because there are no fine-tuned policies and the staged policies do not take any action. They only show that some traffic will be denied. In fact, all the curl attempts are going through:
Here is the new flow shown by Service Graph:
As you can see, there are new lines and arrows which indicate the traffic among pods. Also, none of them are highlighted in red, which would have been present if the staged policies were enforced.
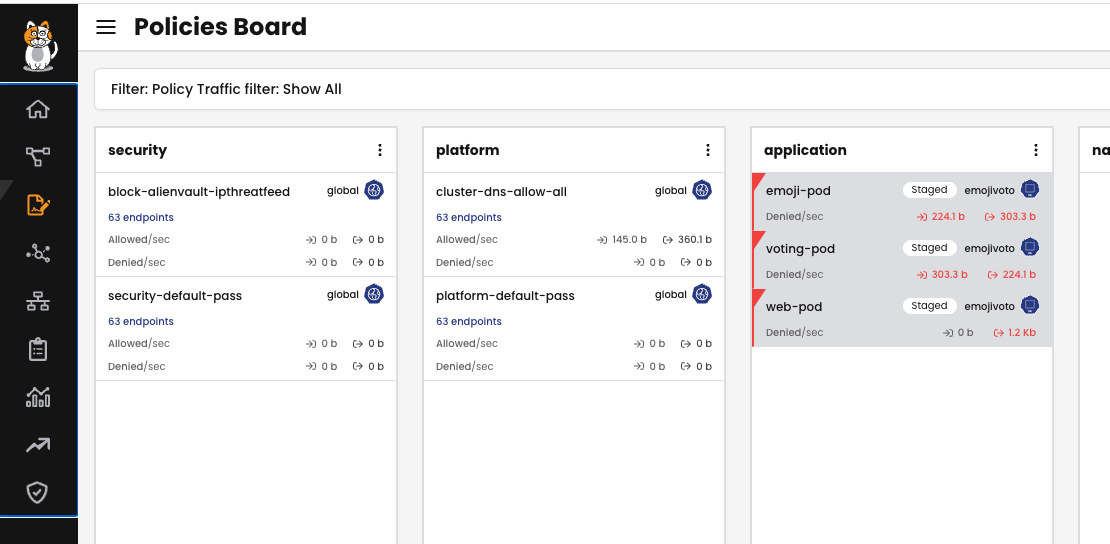
The staged policies would block the non-expected traffic and this is shown in Policy Board:
STEP 4: Enforce the staged policies
I’m going to enforce the staged policies and verify if the non-expected traffic is actually denied.
Here is how this is done:
From the Policy Board, we can see that those policies are no longer marked as “Staged”:
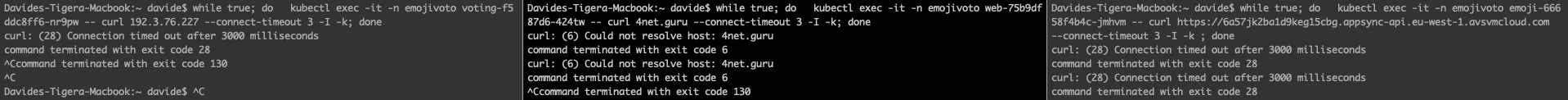
Since the policies are enforced, the non-expected traffic is blocked as expected:
STEP 5: Trigger suspicious DNS query and flow alerts
For this step, I have deployed a Threat Feed DomainSet with URL: https://installer.calicocloud.io/feeds/v1/domains
Then I used curl to connect to some of the suspicious URLs:
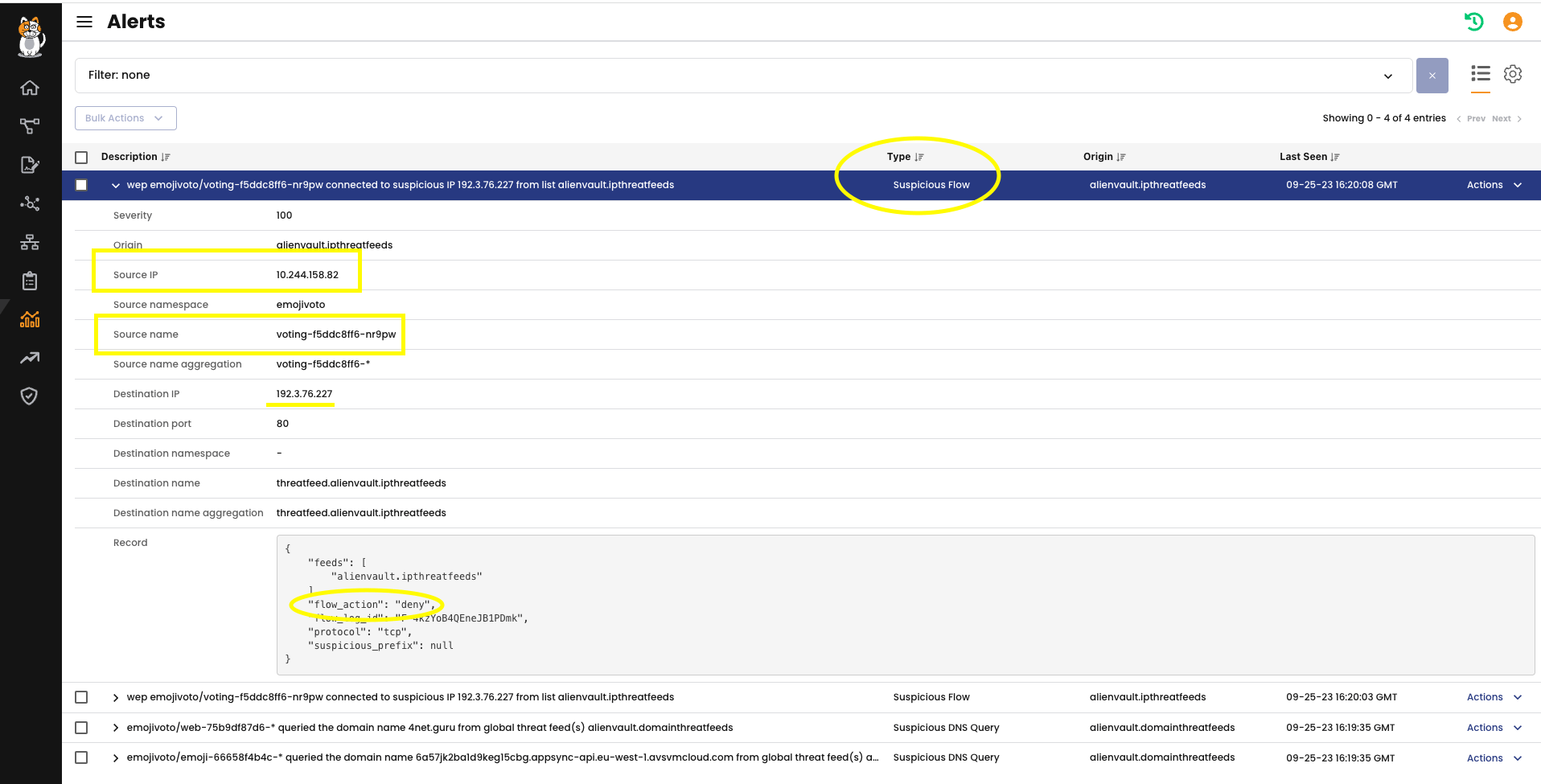
As you can see, those attempts were denied, thanks to policies we enforced above. However, the key takeaway is that we got some detailed alerts that can help administrators investigate a compromised pod.
Here an example of alert:
Here is more information about DNS observability and troubleshooting for Kubernetes and containers with Calico.
Conclusion
In the ever-evolving landscape of containerized applications, security is non-negotiable. Azure Kubernetes Service provides a solid foundation, but for organizations seeking comprehensive security, Calico Enterprise is the missing piece of the puzzle. By integrating Calico Enterprise with AKS, you can bolster your security posture, protect sensitive data, and stay one step ahead of emerging threats. In an era where cyberattacks are on the rise, the partnership between AKS and Calico Enterprise ensures your containerized workloads remain secure and compliant.
Ready to get started? Try Calico Cloud for free.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!