Ensuring the security of containerized workloads has become a top priority given the accelerated adoption of managed Kubernetes services. The complexity of hosting these workloads securely in the cloud necessitates a comprehensive array of security measures. Among these, network policies and encryption stand out as indispensable prerequisites for safeguarding sensitive workloads in a shared, multi-tenant environment.
Sadly the ground truth is that organizations have overlooked this security best practice as evident in this Wiz report.
“Only 9% of clusters use network policies for traffic separation within the cluster.” —Wiz report
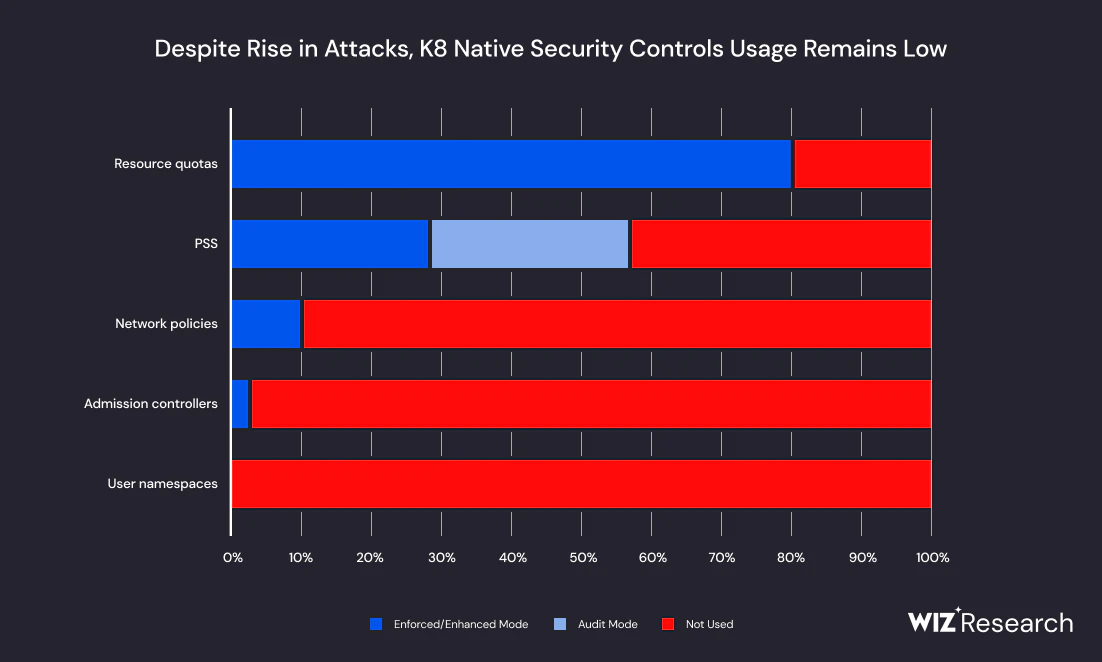
Source: Wiz
Network policies establish stringent access controls and traffic regulations to prevent unauthorized access and fend off malicious exploits within shared cloud spaces. These policies are crucial in preserving the integrity of interactions between containers, a critical factor in regulated organizations. Encryption plays a fundamental role in fortifying security by securing network traffic, maintaining data confidentiality, and ensuring compliance with stringent regulatory standards. This combined security approach constructs a robust defense mechanism that effectively safeguards sensitive information within the dynamic and shared landscape of the cloud, countering potential threats.
This blog post focuses on examining the significance of network security in ensuring the security of managed Kubernetes services within cloud environments. Additionally, it will briefly explore the specific security controls offered by Calico to strengthen this security framework.
Controlling workload access: The Importance of Network Policies
Network policies are essential for enhancing the security, compliance, and efficiency of containerized applications in public shared infrastructure. This section discusses some of the most common reasons behind implementing these policies and their critical role in safeguarding Kubernetes workloads.
Network policies enforce access controls and restrict network traffic most commonly at layer 3 and 4, effectively preventing unauthorized access and malicious activities. In Kubernetes, these policies provide granular access controls and segmentation, ensuring robust security and isolation between pods and namespaces in shared and multitenant clusters. Namespaces are used to implement multi-tenancy in K8S. However, without network policy, applications in different namespaces can freely communicate with each other. There is no replacement or alternative for network policy to secure container traffic at layer 3 and 4.
Network policies play a crucial role in ensuring regulatory compliance, such as PCI-DSS. By effectively controlling network traffic and safeguarding sensitive data, organizations can meet compliance requirements and establish a foundation for data protection. Kubernetes clusters are highly dynamic, with continuously changing metadata information, including pod names and IP addresses. Calico network flow logs, enriched with Kubernetes pod metadata, are essential for enhanced observability, troubleshooting, and compliance reporting. These enriched logs provide valuable visibility into connection information. In compliance-driven clusters, the ability to track historical connection information becomes vital, and Calico’s flow logs with pod metadata prove invaluable in meeting this requirement.
Network policies optimize resource utilization in Kubernetes clusters, resulting in improved performance and stability. By efficiently managing network traffic, these policies prevent resource bottlenecks and congestion, enabling applications to operate smoothly.
Calico provides a mature, sophisticated, and performant policy engine for Kubernetes clusters. Additionally, Calico offers advanced network policy tooling such as a network policy UI, staged policy, policy recommendation, policy tiers, DNS policy, ServiceGraph, and flow logs, which facilitate the creation, validation, and troubleshooting of network policies. The Calico policy engine not only governs pod-to-pod traffic on the network, but also secures Kubernetes nodes, non-cluster bare-metal and virtual machines, all within a unified policy language and control plane.
Securing Managed Kubernetes Network: Encrypting In-Transit Traffic
Network encryption is crucial for maintaining the security and privacy of data and communication within a Kubernetes cluster, especially for unsecured pod traffic over a shared network fabric. It plays a significant role in ensuring that information remains confidential and protected. Network encryption provides protection against unauthorized access and eavesdropping. Additionally, it helps meet compliance regulations and safeguards against man-in-the-middle attacks. Implementing network encryption is vital for preserving the integrity and privacy of data, adhering to regulatory standards, and establishing secure Kubernetes deployments. WireGuard is a simple, lightweight, and performant tunneling protocol that enables us to establish secure connections. Calico leverages WireGuard to deliver simple, streamlined and automated encryption for Kubernetes clusters, making the process of securing network connections easier and more efficient. Calico also fully manages the network encryption lifecycle across all the WireGuard enabled nodes as they are added to and removed from the cluster.
Calico WireGuard encryption protects inter-node pod traffic. If the Kubernetes clusters are managed clusters deployed on EKS (AWS CNI) and AKS (Azure CNI), Calico WireGuard encryption also protects inter-node host-network traffic as well. Following are some of the most common reasons why Calico WireGuard encryption is used:
- On-the-Wire Security: Ensuring network encryption across public and shared infrastructures, particularly in cloud environments.
- Securing Intra-Cluster Traffic: Safeguarding application traffic within the cluster, especially for insecure protocols like HTTP. Typically traffic up to the ingress point in the cluster is secured using https. However, beyond that point the traffic is forwarded using clear text. Calico WireGuard helps secure such connections.
- Compliance Requirements: Meeting stringent compliance standards such as HIPAA and PCI, where data in-transit encryption stands as a critical mandate. Calico WireGuard encryption addresses this imperative need for secure transmission.
Summary
The maturation of managed Kubernetes services offered by leading cloud providers has expedited their adoption, streamlining operations for organizations across various scales. However, the implementation of multitenant Kubernetes clusters within shared public cloud spaces has highlighted notable security risks.
While Kubernetes security involves a wide array of measures, this blog post emphasizes the crucial role of network security in cloud environments. Preserving the security of containerized workloads stands as a primary concern within shared cloud spaces. Implementing effective measures such as network policies and encryption plays a pivotal role in strengthening the integrity of these workloads. Network policies, empowered by advanced Calico policy tools, establish stringent access controls, ensuring compliance and optimizing resource utilization within Kubernetes clusters. Simultaneously, network encryption, utilizing WireGuard within Calico’s framework, serves as a simple yet robust shield, thwarting unauthorized access and eavesdropping attempts on inter-node pod traffic across public and shared infrastructures.
Ready to try Calico for yourself? Sign up for a free trial of Calico Cloud
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!