Workload-based IDS/IPS, DDoS, DPI, and WAF
Zero-trust granular runtime security to protect containerized workloads from network-based external threats and lateral movement
- Calico Cloud
- Workload-based IDS/IPS, DDoS, DPI, and WAF
Overview
For conventional perimeter-based security and compliance, firewalls are typically deployed enterprise-wide using a zone-based architecture (trusted, untrusted, DMZ). Traditional firewalls are inadequate to protect containerized workloads as they require a static source and destination IP address. Furthermore, Kubernetes pods have short-lived, ephemeral IPs that firewall rules can’t use.
Calico Cloud protects containerized workloads at a granular container level from network-based external threats and lateral movement. With north-south and east-west protection support, Calico Cloud prevents malicious actors from gaining a foothold and moving laterally across Kubernetes clusters.
Unlike traditional firewalls that rely on fixed network addresses, Calico Cloud’s workload-based security controls apply security policies as code to ensure consistent, deep, and granular container-level protection across multi-cloud and hybrid environments. These security controls are provided as declarative policies, ensuring that each and every workload has the same level of protection regardless of the environment.
Calico Cloud’s workload-based security controls provide:
- Security as declarative code to protect containers from network-based attacks
- Intrusion detection and prevention
- Deep packet inspection
- Honeypods to detect and trap malicious traffic/actors/activity
- Protection from DDoS attacks
- Envoy-based application-level security and web application firewall (WAF)
- Unified cloud security that works across multi-cloud and hybrid environments
Benefits
Runtime threat defense against known and unknown actors
With out-of-the-box threat feeds from AlienVault, and the ability to create custom threat feeds, Calico provides instant protection from known actors. In addition, Calico’s advanced anomaly detection capabilities help identify, quarantine, and remediate attacks from unknown actors.
Prevent data exfiltration from Kubernetes environments
Calico Cloud enforces granular security controls to prevent the exfiltration of data from Kubernetes environments.
Prevent the lateral spread of threats in Kubernetes clusters
Calico Cloud enables workload-based, east-west security controls for isolating endpoints and preventing lateral movement, thereby protecting workloads from APTs that can move laterally.
Capabilities
Intrusion detection and prevention
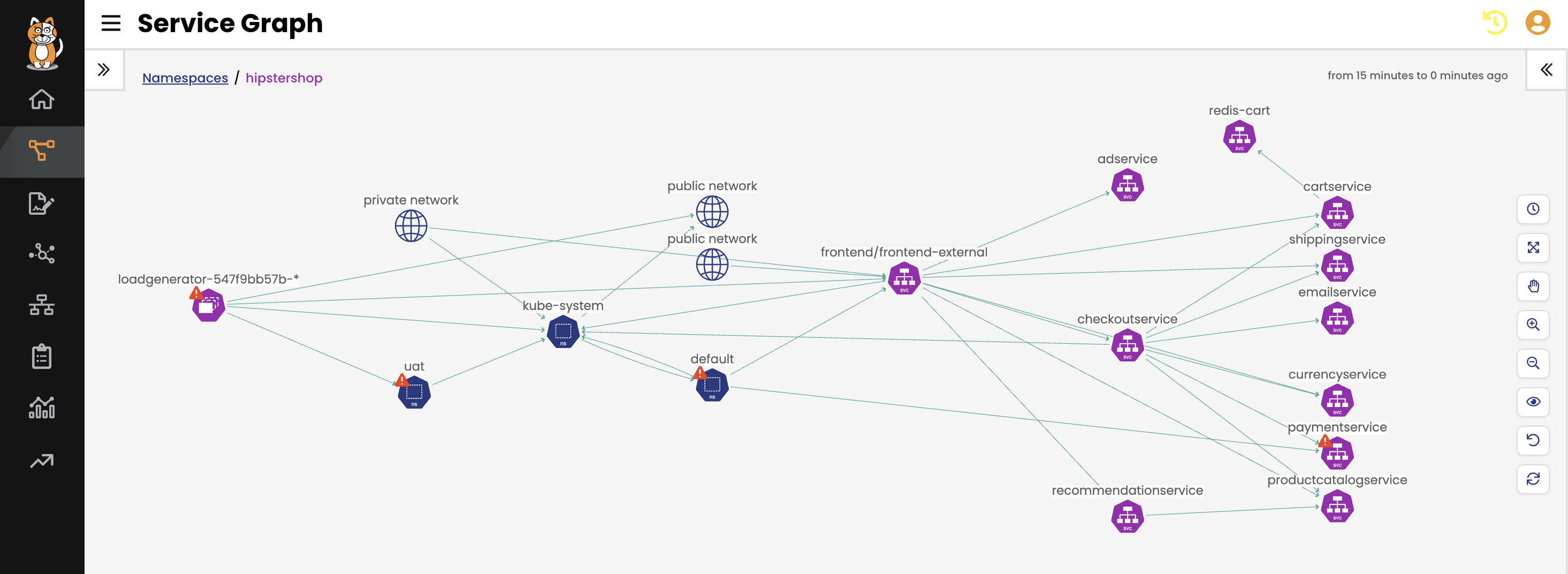
Calico Cloud delivers a workload-based, feature-rich IDS/IPS solution purpose-built for Kubernetes. The IDS solution ingests threat feeds from AlienVault and custom sources to pinpoint the source of malicious activity in case of a breach. It uses machine learning to identify zero-day threats, actively creates a security moat around critical workloads to mitigate risk, deploys honeypods to thwart zero-day attacks, and automatically quarantines potentially malicious workloads. Calico monitors inbound and outbound traffic (north-south) and east-west traffic that is traversing the cluster environment. Learn more.
Deep packet inspection
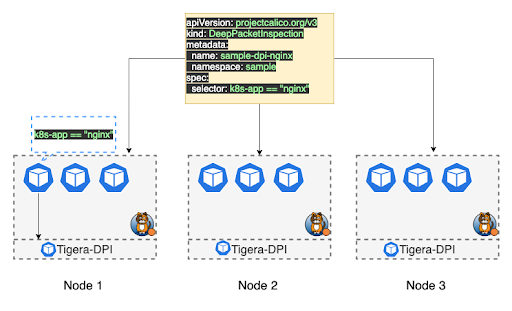
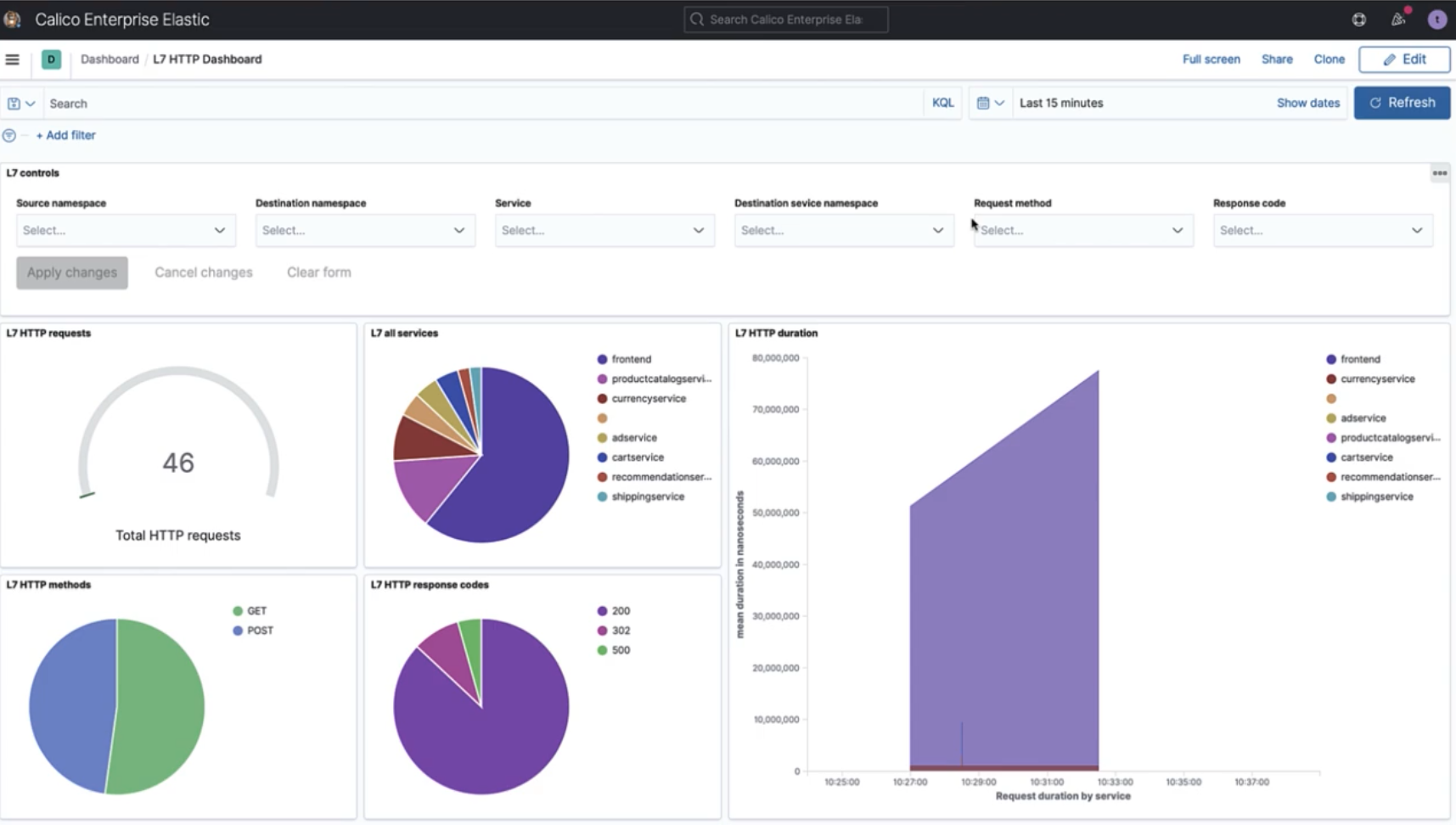
Calico Cloud offers workload-based deep packet inspection to inspect network data in detail and perform signature-based detection of potential threats. It further enriches IP-based network packet information with container and Kubernetes metadata to identify the source and destination of packets. Security teams can quickly run deep packet inspection in response to unusual network traffic in clusters, in order to identify potential threats. Deep packet inspection can also be used on select endpoints for efficient use of cluster resources and to minimize the impact of false positives. Learn more.
Application-level security and WAF
Calico Cloud provides application-level visibility using an Envoy integration and enforces security controls for application protection. The security controls are enforced on all east-west traffic including traffic between namespaces, Kubernetes clusters, and legacy workloads.
Calico offers the ability to enable a WAF as an add-on to the deployment of Envoy as a daemonset. This integration leverages Modsecurity, a popular open source WAF that provides a core rule set for the most common security risks identified by OWASP, and also enables operators to BYO rule sets or leverage subscription-based rules. The WAF also enables users to enforce security controls on all east-west traffic.
As east-west traffic is passing through Calico’s Envoy proxy, these rules are automatically evaluated and any potential threats or security issues are reported as Alerts, which can be sent to a SIEM or Ops tool to initiate security runbooks or playbooks. Learn more.

Extend traditional network firewalls to Kubernetes
Calico provides an Egress Gateway for universal firewall integration, enabling Kubernetes resources to securely access endpoints secured by a firewall. With this integration, firewalls can extend their zone-based architectures to Kubernetes. The Calico Egress Gateway enables customers to leverage existing firewall investments to enforce security and compliance requirements and protect cloud-native Kubernetes workloads using the same familiar tools, processes, and security workflows they use to protect their non-Kubernetes workloads. Learn more.
How It Works
See how Calico Enterprise and Calico Cloud protect cloud-native applications at the container level with Calico’s workload-based IDS/IPS, DDoS, DPI, and WAF.