Intrusion Detection System
Detect and mitigate Advanced Persistent Threats (APTs) using machine learning and a rule-based engine that enables active monitoring
- Calico Cloud
- Intrusion Detection System
Overview
Threat actors are now aware of Kubernetes and the inherent vulnerabilities of its larger attack surface. By default, Kubernetes clusters are left open, which means that any pod can talk to any other pod, even across namespaces. Attackers can hop from service to service until they find valuable data. Firewalls have traditionally been used to block attacks, but if the perimeter is breached, there's no protection from within the cluster. The conventional way of identifying attacks is with an intrusion detection system (IDS); however, the dynamic nature of Kubernetes requires a specialized approach.
Calico delivers a feature-rich IDS solution purpose-built for Kubernetes. Calico’s IDS pinpoints the source of malicious activity, uses machine learning to identify anomalies, and can create a security moat around critical workloads, deploy honeypods that capture zero-day attacks, and automatically quarantine potentially malicious workloads to thwart an attack. Calico’s IDS monitors inbound and outbound traffic (north-south) and east-west traffic that is traversing the cluster environment.
Benefits
Workload Protection
Protects sensitive Kubernetes workloads against vulnerabilities and threat actors deploying APTs, zero-day attacks, and other exploits, using automated detection, response, and mitigation
Custom Alerts
Ensures security teams are immediately notified when an attack or intrusion occurs, enabling further investigation and prompt remediation
Runtime Defense
Provides critical, supplemental protection to firewall defenses to ensure that sensitive workloads are not exposed if there is a perimeter breach
Capabilities

Threat Feed Integration
- Calico ingests threat feeds that identify IP addresses and matches SNORT signatures for known bad actors such as botnets. Any ingress or egress traffic to those IPs or SNORT signatures are automatically blocked and can be configured to generate alerts. Traffic to VPNs and ToR exit nodes is blocked and triggers alerts when detected.
- Firewalls often detect and block traffic associated with known bad actors, but don’t have visibility into which pod is infected. The Calico threat feed pinpoints and reports on the exact source of malicious traffic.
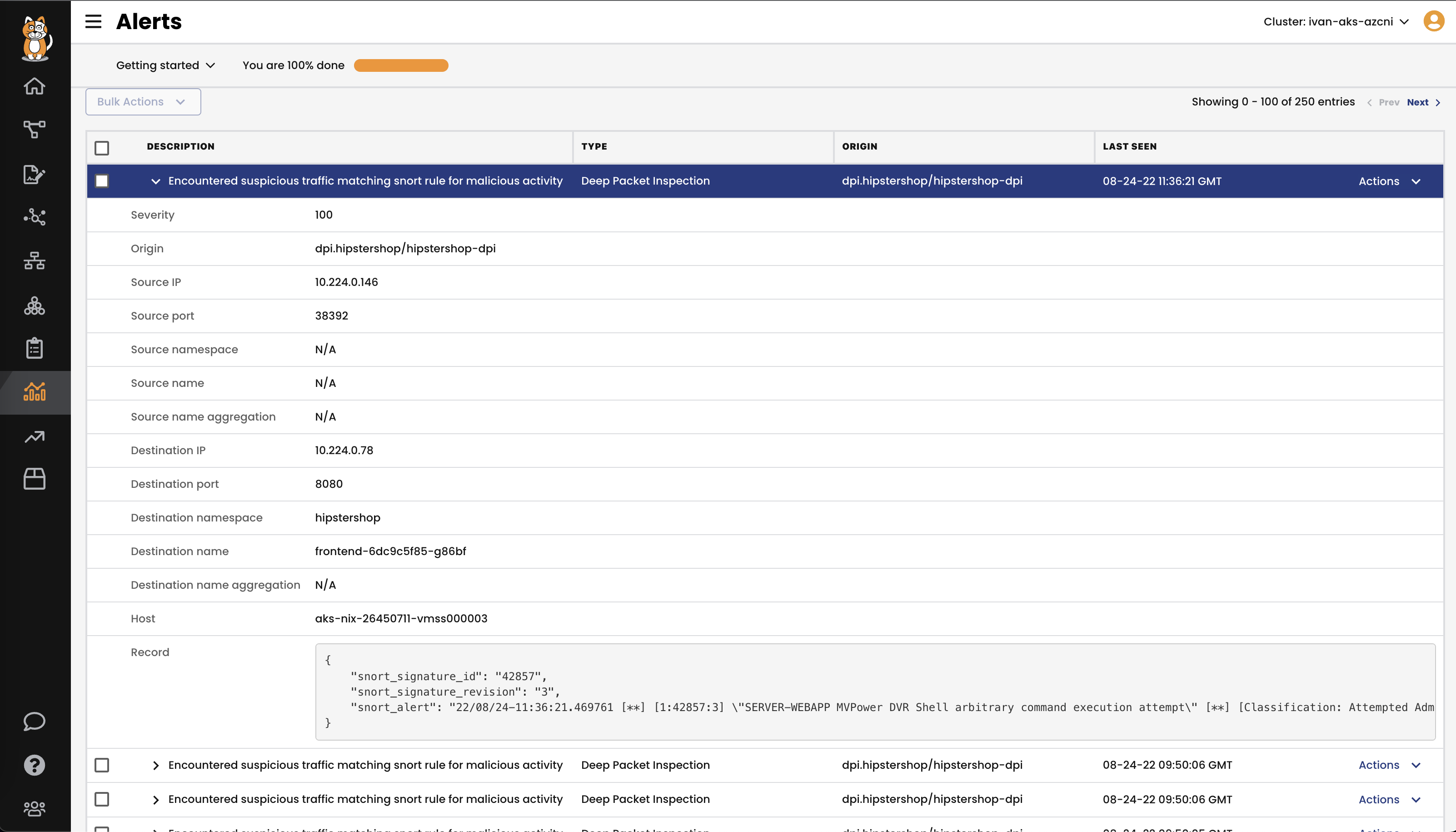
Custom Alerts
- Calico alerts on unauthorized changes to your cluster and security policies as well as known attack patterns such as domain generation algorithms (DGA).
- Alerts are available out-of-the-box and can be customized and augmented by your security researchers or Tigera’s team of experts.
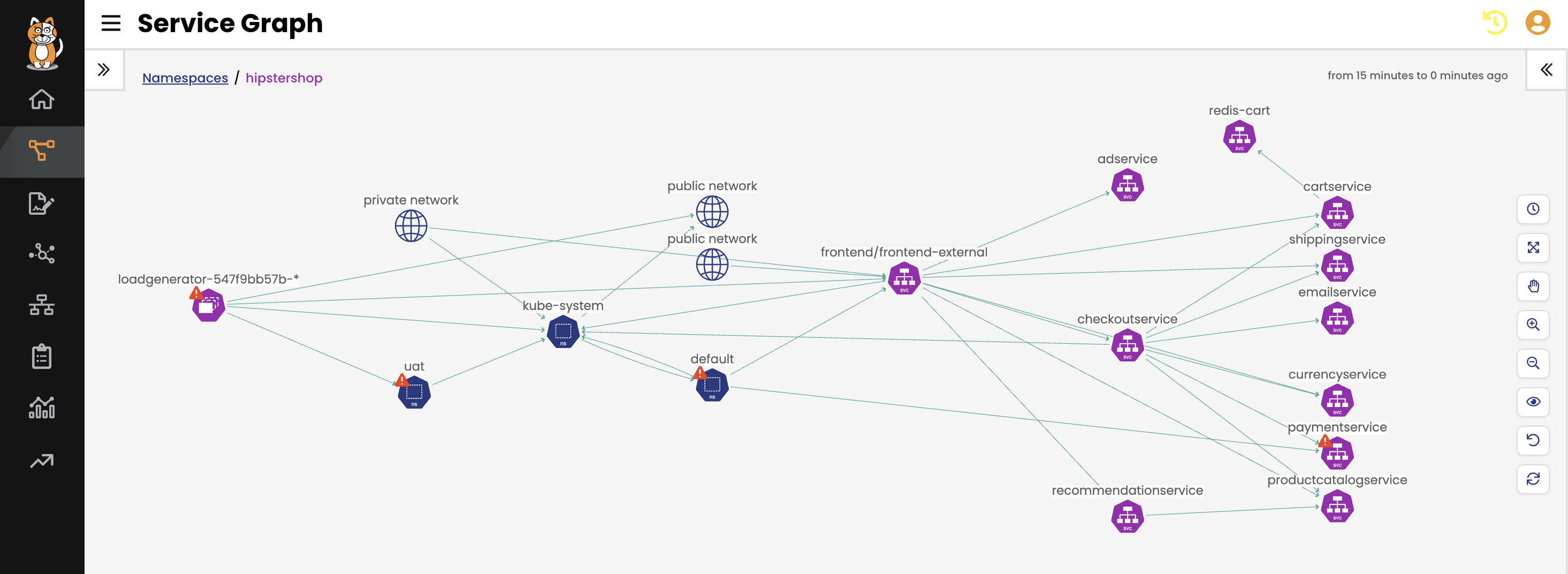
Anomaly Detection
- Calico’s Anomaly Detection capability evaluates traffic flows using machine learning to identify the baseline behavior of your microservice environment, and generates alerts when unexpected behavior is detected. This enables you to detect and protect your Kubernetes environment against zero-day exploits.
- Port scans, IP sweeps, and service byte anomalies can all be indicators that your environment has been compromised and is hosting an advanced persistent threat (APT). Calico detects and alerts on that activity and can quarantine those workloads.
- Calico can detect and prevent OWASP Top 10 attacks that might be targeting your microservices.

Honeypods
- Honeypods are fake pods that run in your cluster. Any traffic to these pods will generate an alert in Calico that will trigger further inspection.
- When traffic hits a honeypod, Calico inspects packets from the traffic and analyzes it for known malware signatures, using SNORT and other tools.
- Inspecting all cluster traffic for malware can create a huge performance penalty. Calico utilizes an innovative approach that doesn’t impact performance to identify suspicious cluster traffic that warrants deeper inspection.

Sensitive Workload Protection
- Calico provides supplemental detection and alerting for any workloads that may have access to sensitive data.
- Calico will detect and alert on abnormal activity, effectively creating a virtual moat to protect your critical workloads.
- Defining your moat is as simple as using a label and then defining detailed alerts for workloads with those labels.

Automatic Remediation
- Alerts generated by Calico can be configured to trigger automated remediation.
- Rogue microservices are immediately isolated from the network, and Calico’s IDS automatically generates policy
- Quarantined workloads can be left running for forensic analysis.
How It Works
Companies are leveraging the power of Kubernetes to accelerate the delivery of applications to meet the pace of business. However, the dynamic nature of Kubernetes makes it operationally challenging to protect applications against vulnerabilities and threat actors deploying APTs, zero-day attacks, and other exploits. Calico’s IDS protects sensitive data from these threats using a highly-effective combination of automated detection, response, and mitigation.