According to the CNCF annual survey released in 2022, 96% of organizations are using or evaluating Kubernetes as a platform for their containerized workloads. Containerization has gained popularity as it fosters DevOps culture and provides the agility and flexibility required for faster software release cycles. Kubernetes has crossed the “adoption chasm” to become a mainstream global technology, emerging as the operating system for the cloud. However, despite its widespread adoption, security concerns continue to impact business outcomes. According to Red Hat’s State of Kubernetes Security Report in 2023, 67% of companies have delayed or slowed deployments due to security concerns. There is also a heightened need for mature service delivery and security response processes.
In this blog post, we will look at how the NIST Cybersecurity Framework can be used to manage and reduce cybersecurity risks in a Kubernetes environment with Calico. The framework provides a comprehensive structure that organizations can use to assess their current cybersecurity capabilities, set goals for cybersecurity improvements, and establish a plan for achieving those goals. It offers a methodology for identifying critical assets and assessing vulnerabilities, thereby aiding in effective data protection strategies. It places a strong emphasis on risk management, encouraging organizations to evaluate, prioritize, and mitigate potential threats. Additionally, the NIST Framework helps ensure that an organization’s cybersecurity measures are in line with legal and regulatory requirements, thereby reducing the likelihood of costly compliance violations. By adopting the NIST Cybersecurity Framework, organizations can establish a comprehensive security posture that is not only effective in safeguarding critical assets but also in meeting legal and regulatory requirements.
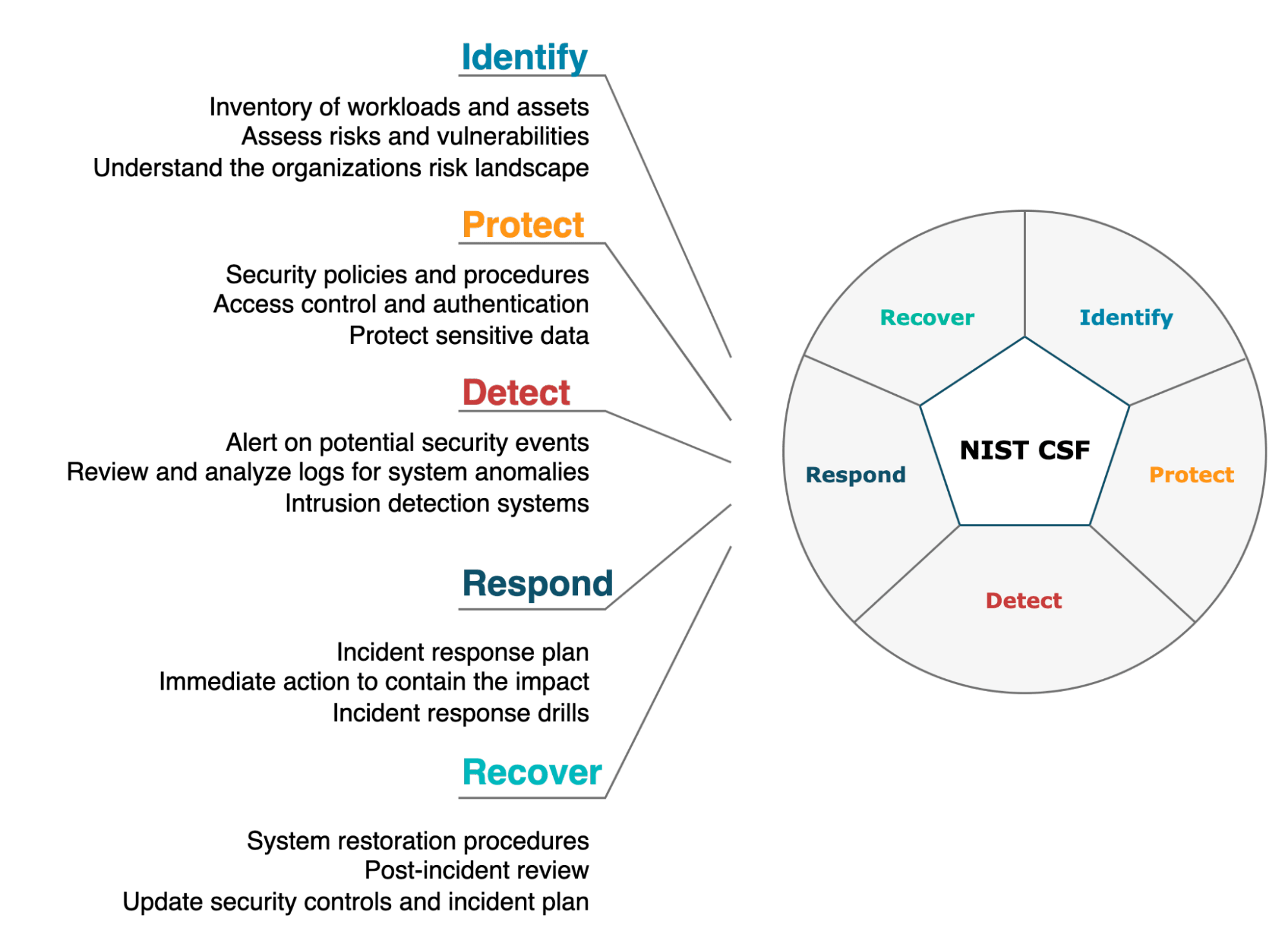
The framework is built around five core functions, which provide a high-level view of an organization’s management of cybersecurity risks.
- Identify: Understand the organizational context, assets, and risk environment to manage cybersecurity risk effectively.
- Protect: Implement safeguards to protect the organization’s services, systems, and data.
- Detect: Develop and implement activities to identify cybersecurity events quickly.
- Respond: Have plans and processes in place to take action regarding detected cybersecurity events.
- Recover: Develop and implement activities to restore systems that may have been impaired due to a cybersecurity event.
Next, we will explore Calico Cloud’s capabilities at a high level to understand how organizations can deploy both proactive and reactive measures as outlined in the NIST CSF. For ease of understanding, the NIST core functions can be categorized as follows:
- Proactive measures – Comprising the “Identify” and “Protect” functions, these measures focus on preventing cybersecurity incidents.
- Reactive measures – Including the “Detect,” “Respond,” and “Recover” functions, these measures are designed to manage and mitigate issues as they arise.
Proactive Measures
Identify
As organizations migrate their applications to Kubernetes, the initial security challenges often stem from inadequate visibility into containerized workloads. While managed Kubernetes services have streamlined the setting up of clusters, traditional security tools typically lack the capability to offer granular insights at the container and platform level. Enterprises find it easy to get started with Kubernetes but soon face challenges as security and platform teams can’t protect what they can’t see. Achieving visibility for effective cybersecurity requires a cloud-native approach and security tooling that can be seamlessly plugged into Kubernetes.
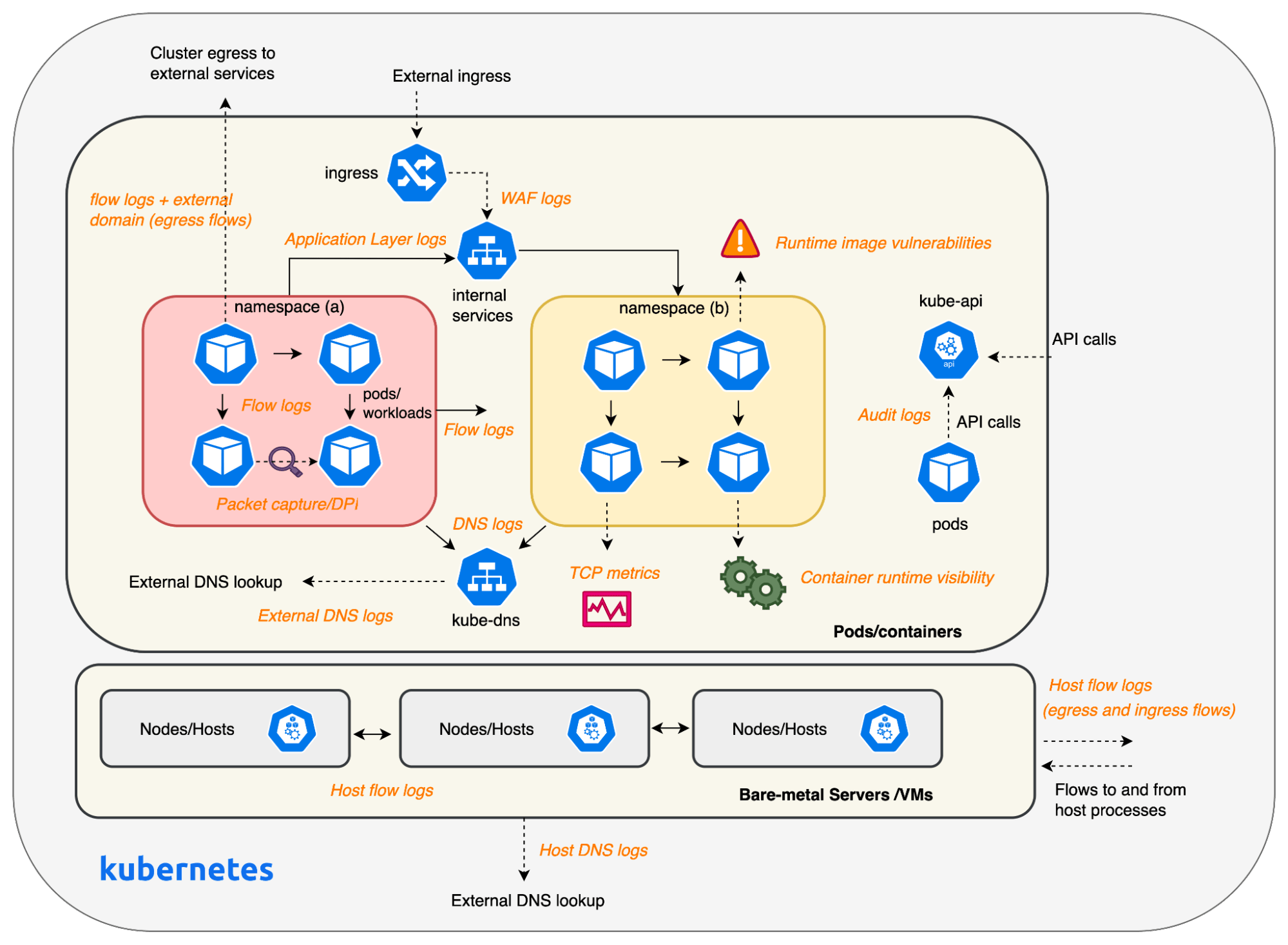
Calico Cloud offers deep visibility across the Kubernetes technology stack, helping organizations meet the requirements of the “Identify” function group. Its extensive logging features equip both security and DevOps teams with the crucial visibility required for implementing proactive measures to safeguard workloads within the cluster. Below are some logs that Calico generates across multiple touchpoints in a cluster.
- Flow logs – Flow logs offer end-end communication visibility for all containers and hosts in Kubernetes clusters, which is paramount to understanding network behavior and security vulnerabilities. Flow logs can be used to analyze traffic and deploy proactive security measures to protect workloads in the cluster.
- DNS logs – Provides visibility into all DNS requests and responses for pods and hosts in the cluster. It can be used to identify internal and external services that workloads are attempting to connect to.
- Application Layer logs – Calico offers visibility into the application layer without the need for a service mesh. Application layer logs are also key for detecting anomalous behaviors like attempts to access applications, restricted URLs, and scans for particular URLs.
- Audit logs – Can be used by security teams and auditors to see changes made to Kubernetes resources over time.
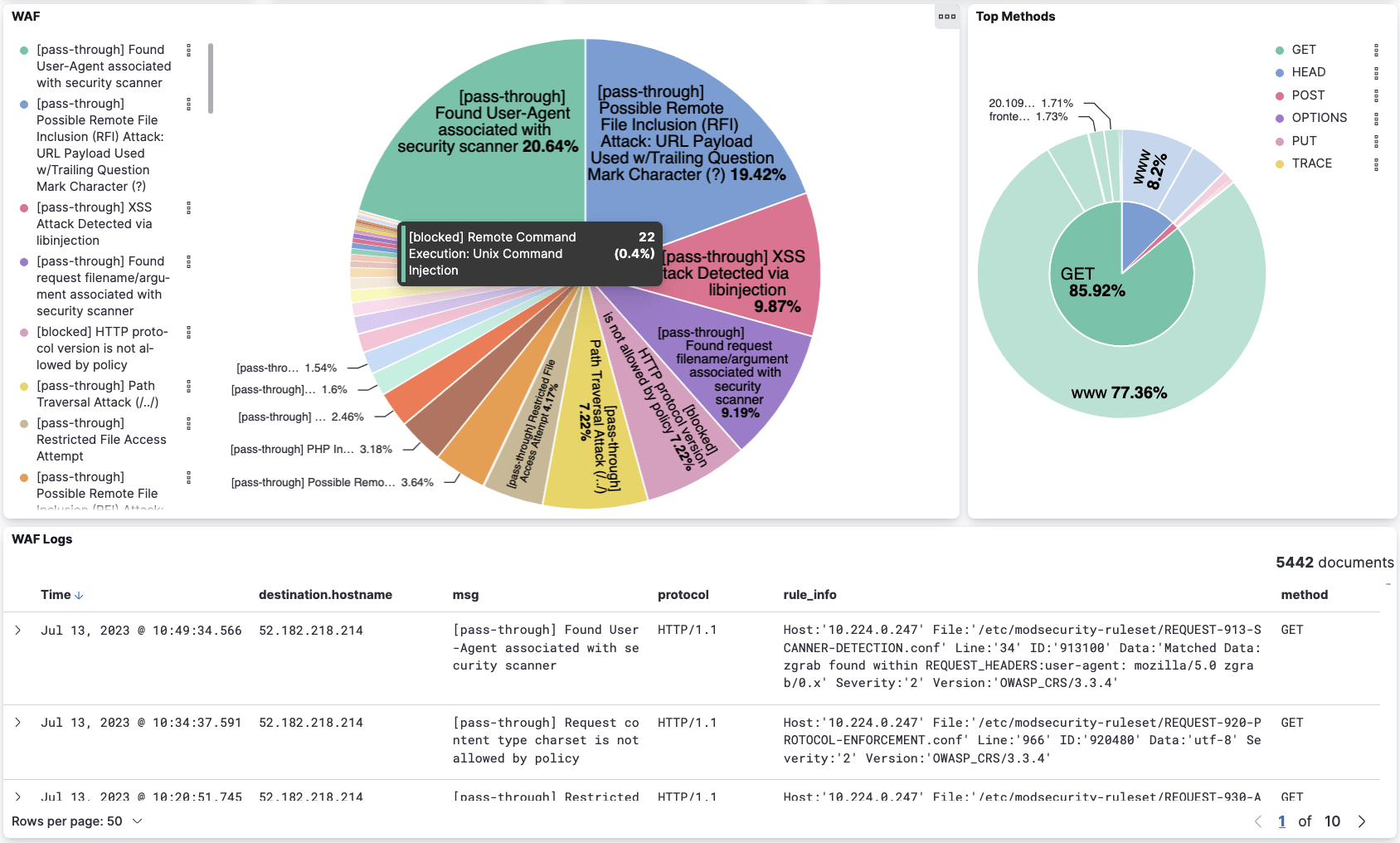
- Web Application Firewall (WAF) logs – Calico WAF allows you to selectively run service traffic within your cluster and protect intra-cluster traffic from common HTTP-layer attacks such as SQL injection and cross-site request forgery. In addition to protecting against application layer attacks, any blocked HTTP requests are logged and available in Elasticsearch for review. You can also create global alerts based on these logs.
- Container threat detection – Calico’s threat detection engine monitors activity within the containers running in your clusters to detect suspicious behavior and generate corresponding alerts. Suspicious behavior can include Access to sensitive system files and directories, defense evasion, discovery, execution, persistence, and privilege escalation techniques.
- Runtime image vulnerability – A vulnerability scan typically gates the deployment of container images to a cluster. However, security teams typically don’t have visibility into the vulnerability of the cluster as a result of the vulnerabilities found in running containers. Runtime image vulnerability scans provide vulnerability reports for running workloads in a cluster.
The diagram shown below provides an overview of the visibility blindspots that DevOps and security teams can alleviate with Calico.
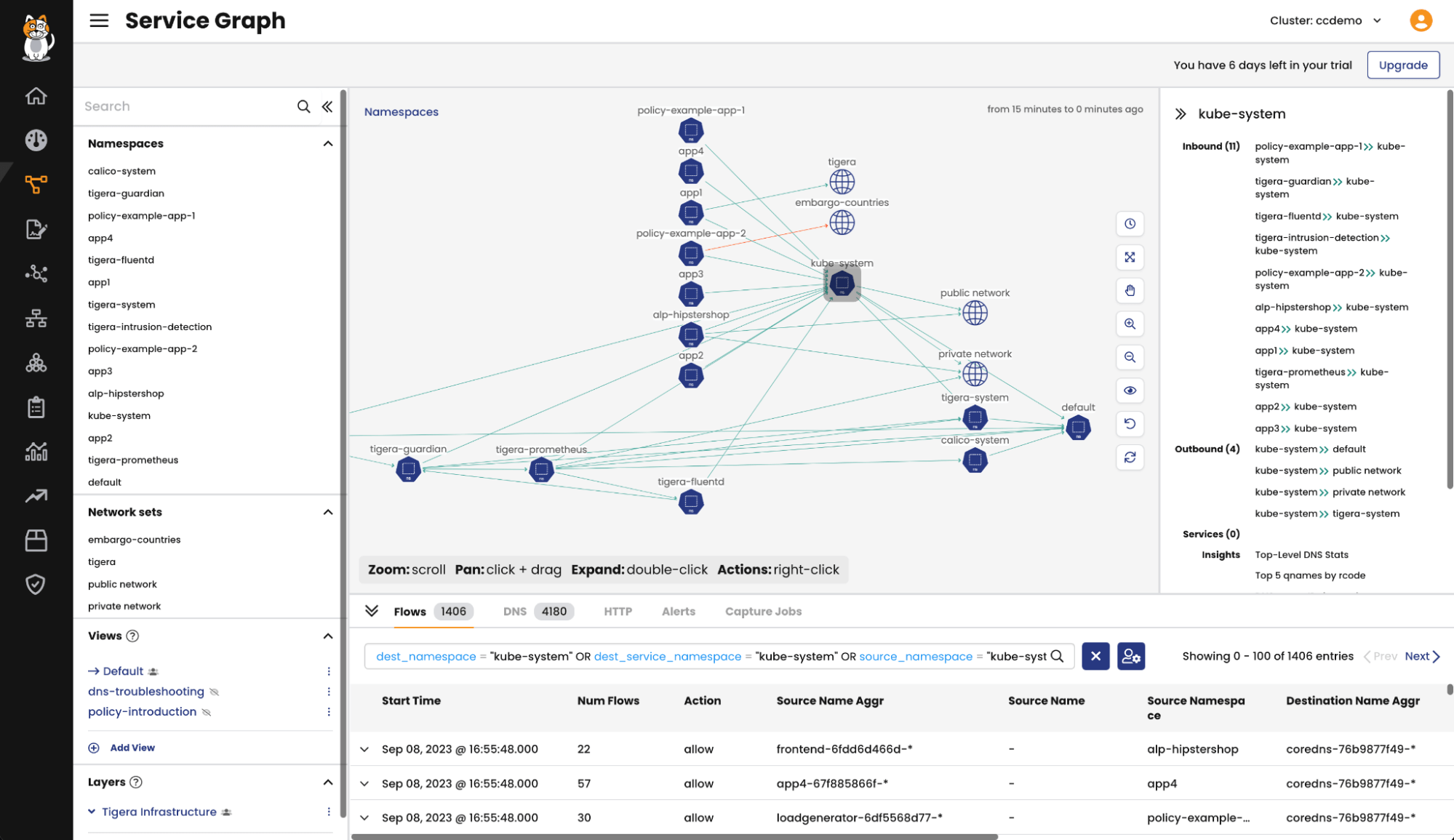
Leveraging logs generated by Calico at multiple touchpoints throughout the cluster, the Dynamic Service and Threat Graph creates a dynamic and navigable visual representation that enables users to gain a deep understanding of workload behavior. This level of insight is instrumental in identifying security risks and crafting effective strategies to mitigate potential threats. By distilling complex data into actionable insights, the Service and Threat Graph allows security teams to focus on the most important aspects of a cluster’s security posture without the need for in-depth familiarity with Kubernetes or infrastructure complexities.
Protect
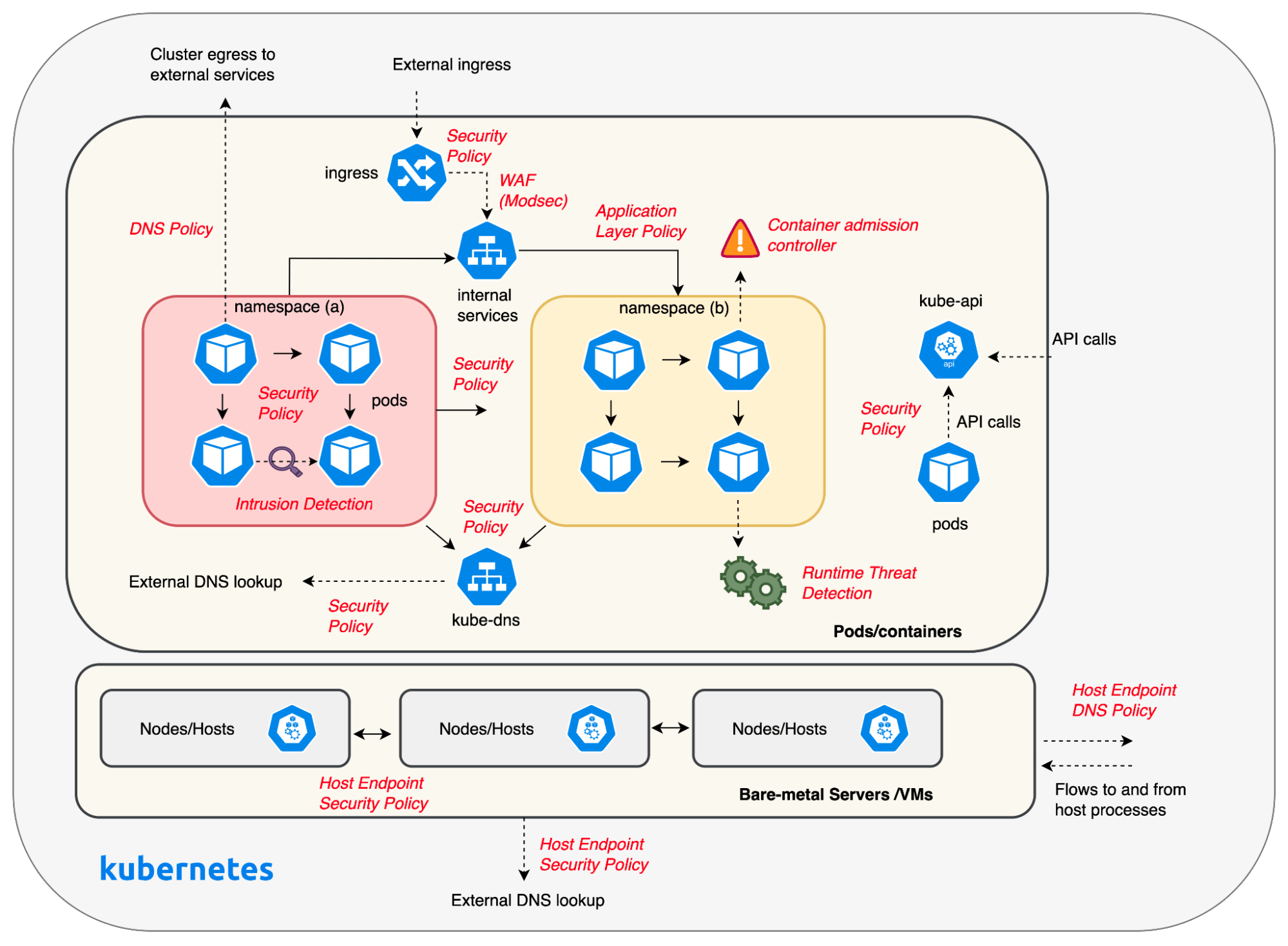
Calico offers a robust suite of security controls designed to safeguard cluster workloads. Through the use of Security Policies, including network policies and global network policies, Calico enables the implementation of identity-based microsegmentation, thereby enforcing least-privilege communication across all workloads within the cluster. Complementing this, DNS Policies further tighten security by restricting pods and hosts in the cluster from unauthorized communication with external services. These two controls alone can significantly reduce a cluster’s attack surface and are essential in maintaining a robust security posture for Kubernetes platforms.
Additional controls such as Application Layer Policy (ALP) and Web Application Firewall (WAF) can protect external facing applications or internal APIs exposing sensitive data. Calico Cloud’s UI can be used to enable these controls on a per-service basis with a single click that significantly reduces the friction and effort required to implement robust security for your applications.
Calico Cloud offers a streamlined Policies Board that enables Security and DevOps teams to implement a hierarchical approach to security in Kubernetes. The controls presented above can be implemented on a per-workload basis using application-centric constructs. Further, security teams can implement segregation of duties (SoD) and delegate access to downstream teams to enforce fine-grained controls without violating high-level security guardrails using Calico’s tiered policy model.
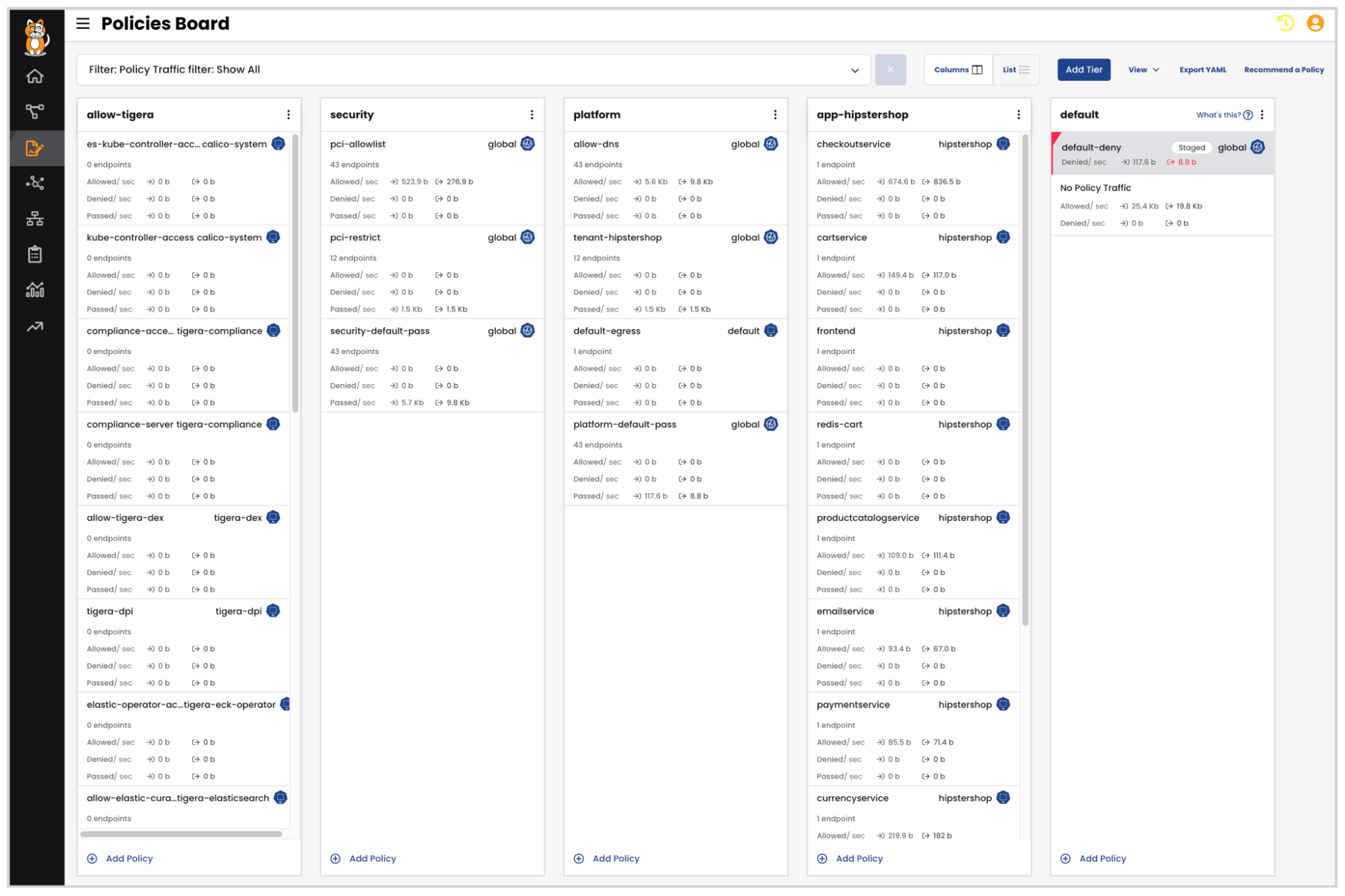
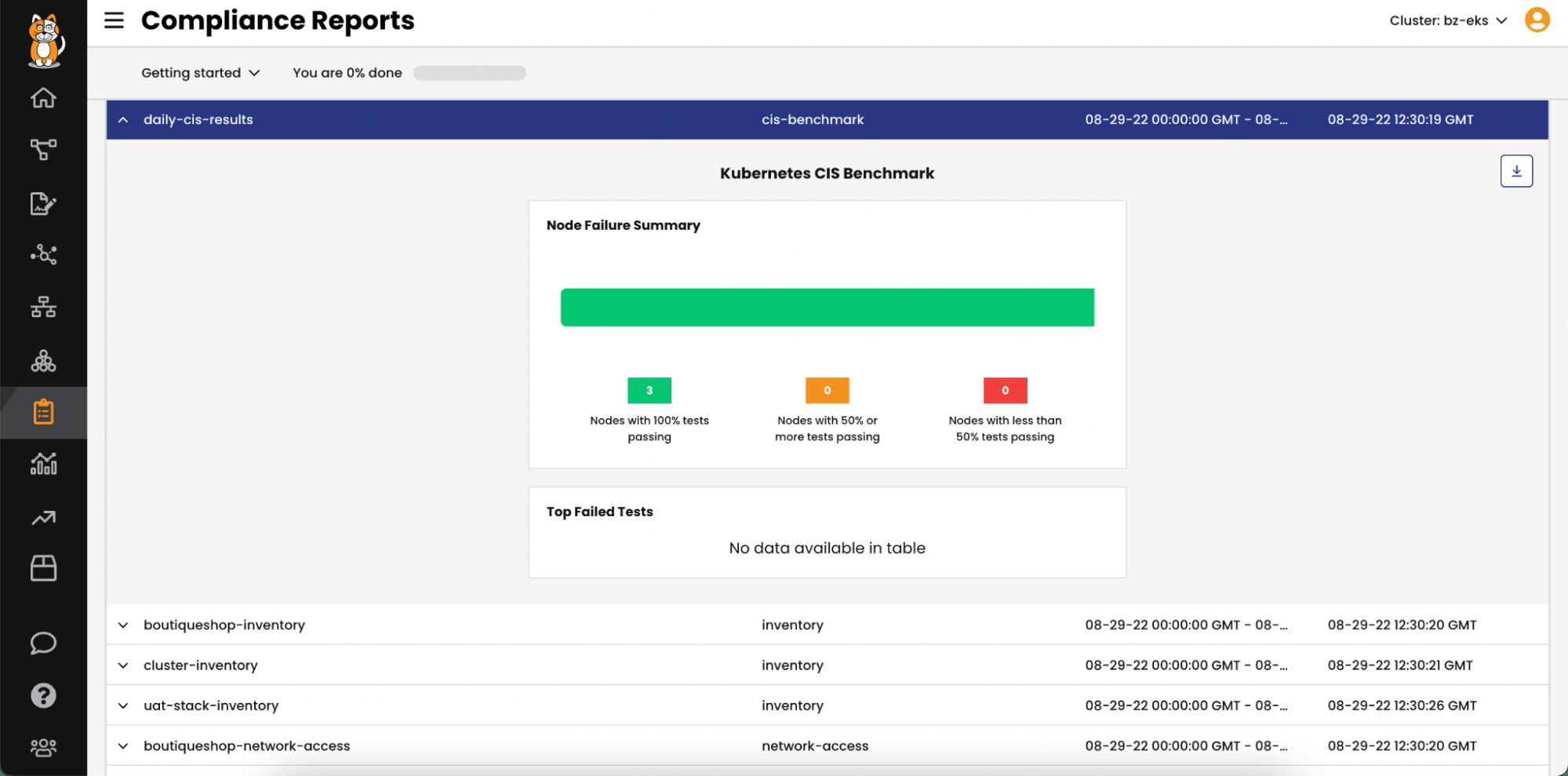
Security teams in many organizations are required to showcase and validate security controls that have been implemented to protect applications from potential threats, intrusions, and breaches. Calico’s compliance reports provide an overview of the cluster’s security posture that serves as evidence of the organization’s commitment to meeting regulatory and industry standards. Daily compliance reports can also be used to identify any deviations from the standards and take remedial action to restore the cluster’s security posture. In addition to meeting standards, these reports can also facilitate audit and regulatory checks.
Reactive Measures
Detect
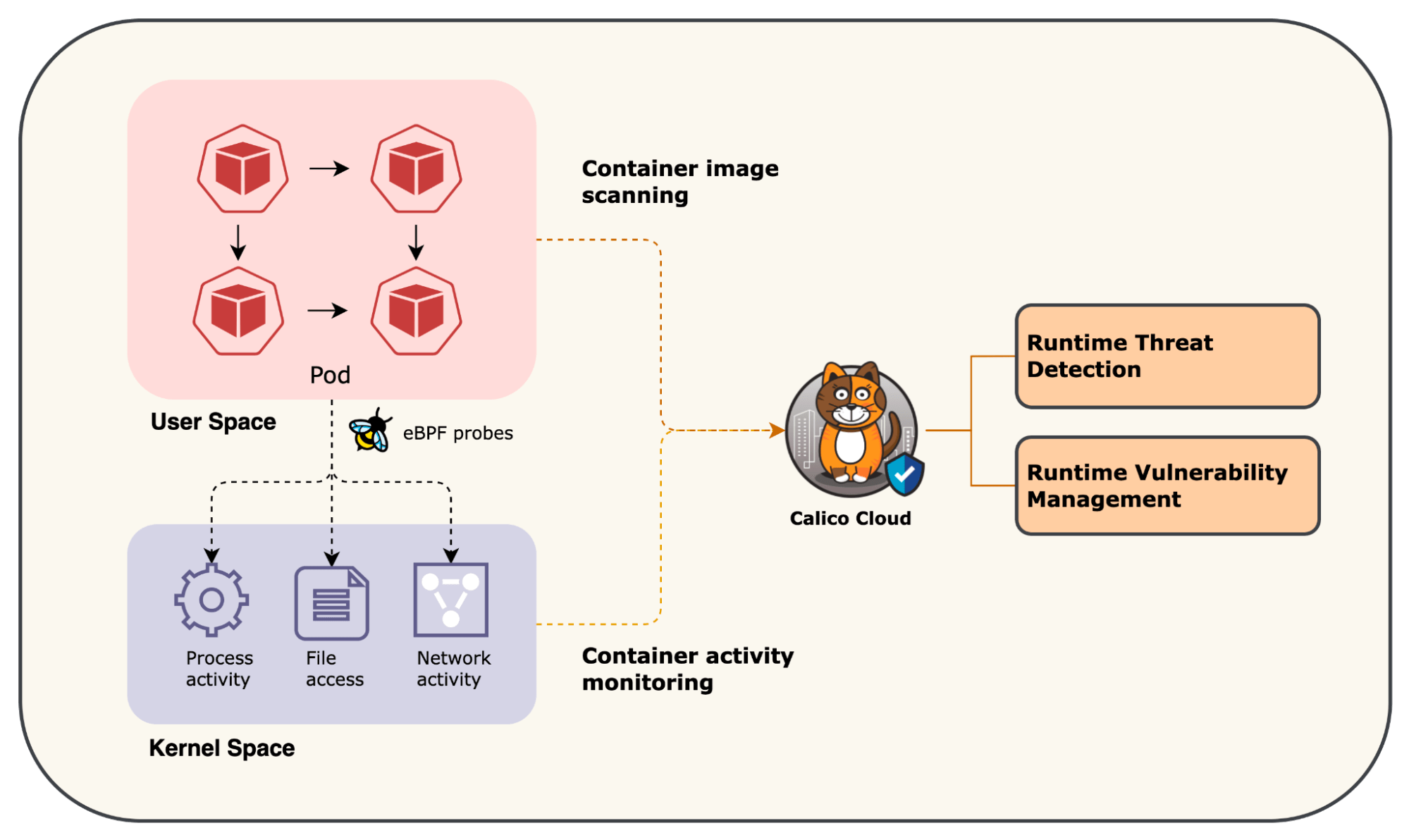
Calico offers several advanced real-time detection capabilities with out-of-the-box detectors that use advanced eBPF probes to collect data and analyze suspicious behavior across processes, file systems, and system calls. Further, users can also add open-source and commercial threat intelligence feeds that eliminate the need to create and manage complex rulesets. All activities are logged and enriched with workload-specific metadata. This approach not only flags anomalies but also helps understand the context behind security events. Also, unlike conventional tools that perform image vulnerability scans at specific intervals, Calico continuously scans images during runtime to identify new vulnerabilities for workloads running in the cluster. Overall, Calico’s runtime threat detection and runtime vulnerability offer security engineers comprehensive visibility into the security posture of their Kubernetes clusters, helping detect malicious activity.
Unified observability across various Kubernetes platforms has emerged as a significant security concern, especially as platform teams, product owners, and business units increasingly spin up distinct clusters for specific applications or use cases. As organizations pursue a multi-cloud strategy, Kubernetes clusters can be provisioned on-premises or in different cloud environments. Fragmented security solutions can lead to disjointed security measures, making it challenging to maintain a comprehensive view of the security posture across all clusters. Calico Cloud addresses this complexity with its Multi-cluster Management capabilities, offering a unified platform enabling real-time detection of security events across the Kubernetes ecosystem regardless of where the cluster is located or the type of cluster.
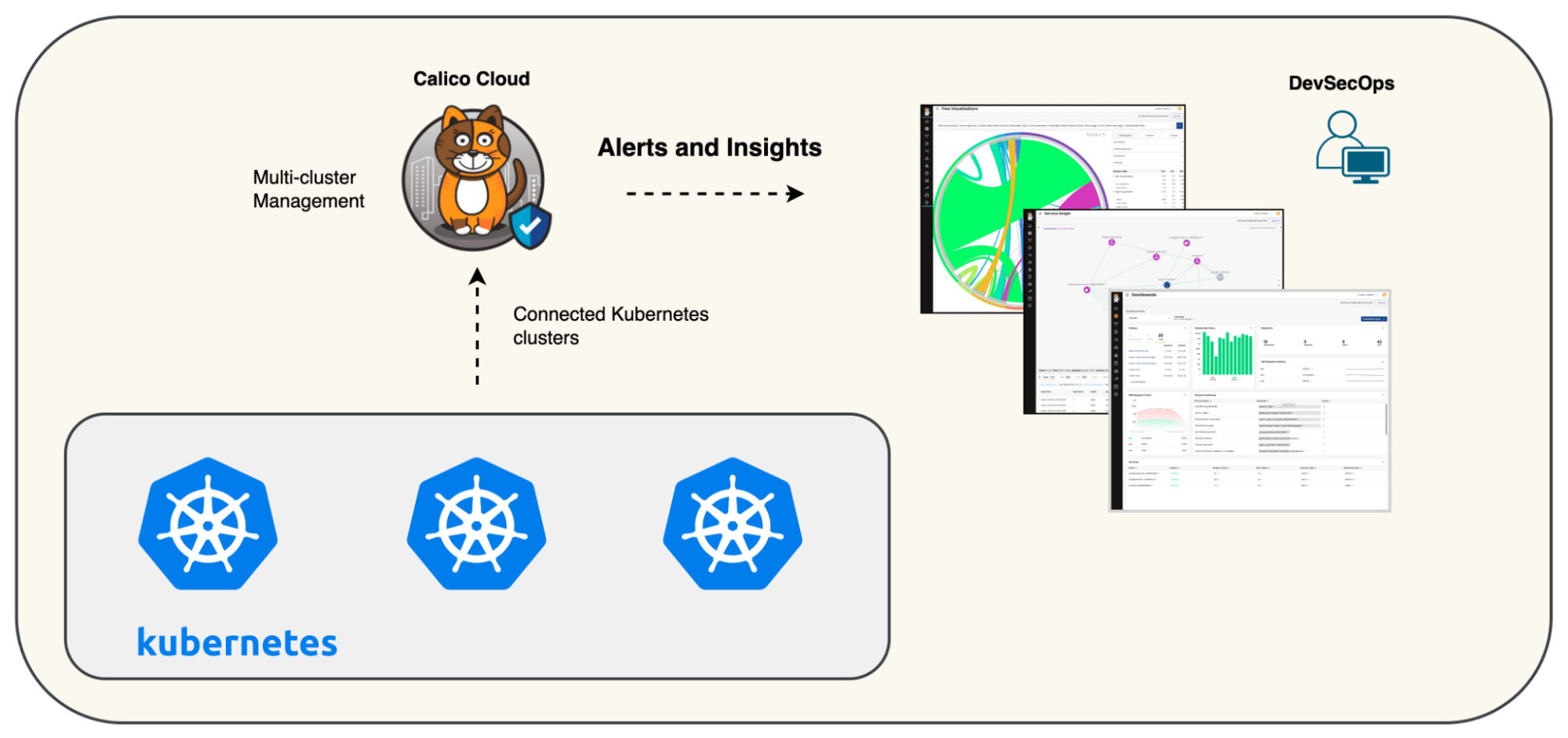
Security teams have a single pane of glass to assess, remediate, and respond to security threats across the organization’s Kubernetes estate. The Calico Cloud installation can be automated so that new clusters, by default, are deployed with the required security controls.
Calico’s unified observability and alerting means that security teams can now manage and respond to security events across disparate clusters from a single console. By aggregating real-time metrics and logs from across the Kubernetes ecosystem, Calico Cloud allows for more effective risk management by empowering security teams to act in a timely manner to potential security threats.
Respond
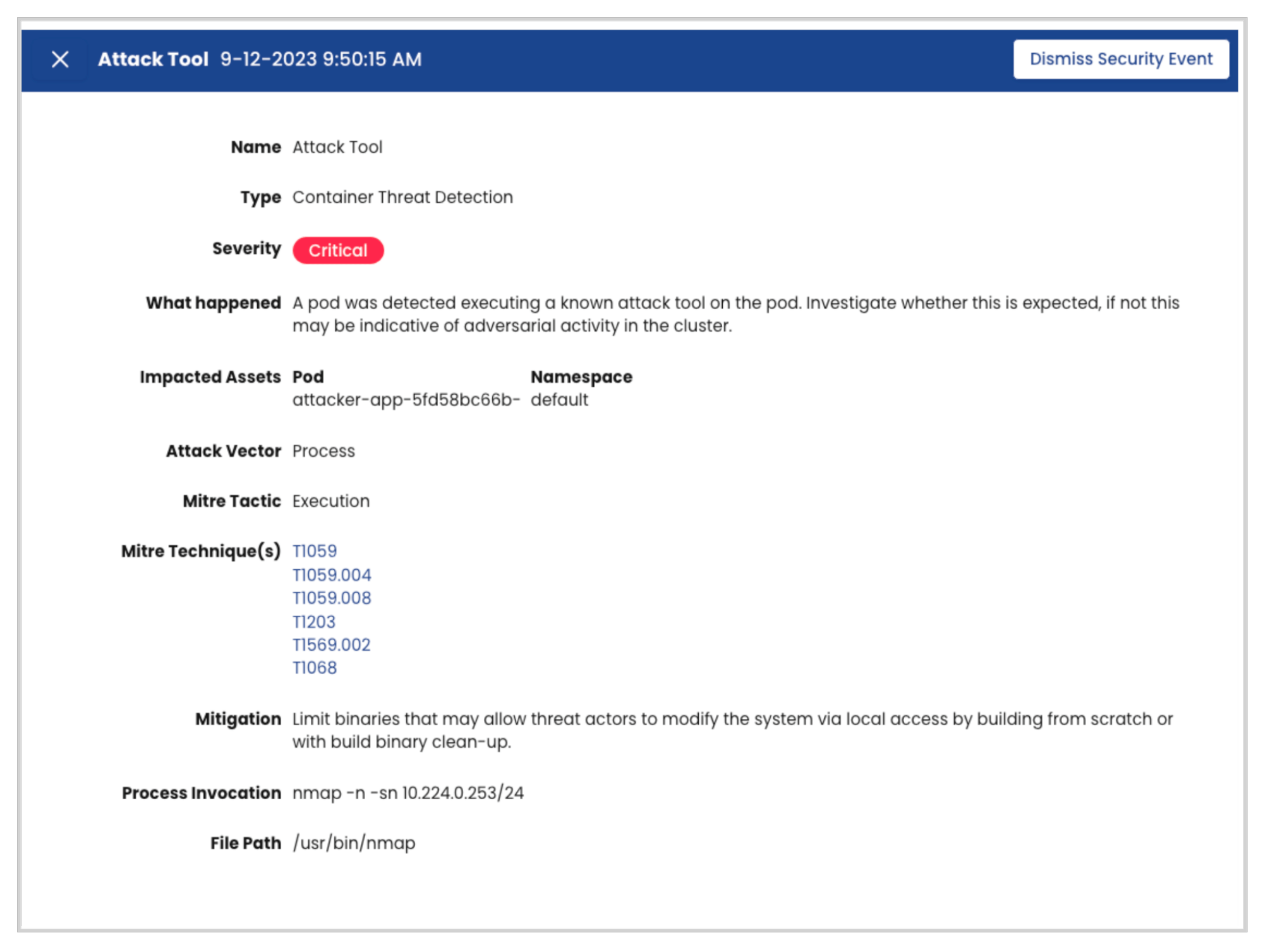
It is crucial to investigate security events as they are detected. Security engineers must identify whether those events pose a threat to the operational integrity of the workloads running in those clusters. Traditionally, security teams have to sift through logs produced by various security tools to identify the risks posed by such events. This becomes even more difficult in Kubernetes due to the highly dynamic and ephemeral nature of workloads. Calico offers out-of-the-box dashboards that make it significantly easier for security teams to identify and assess the potential threat of a suspicious event.
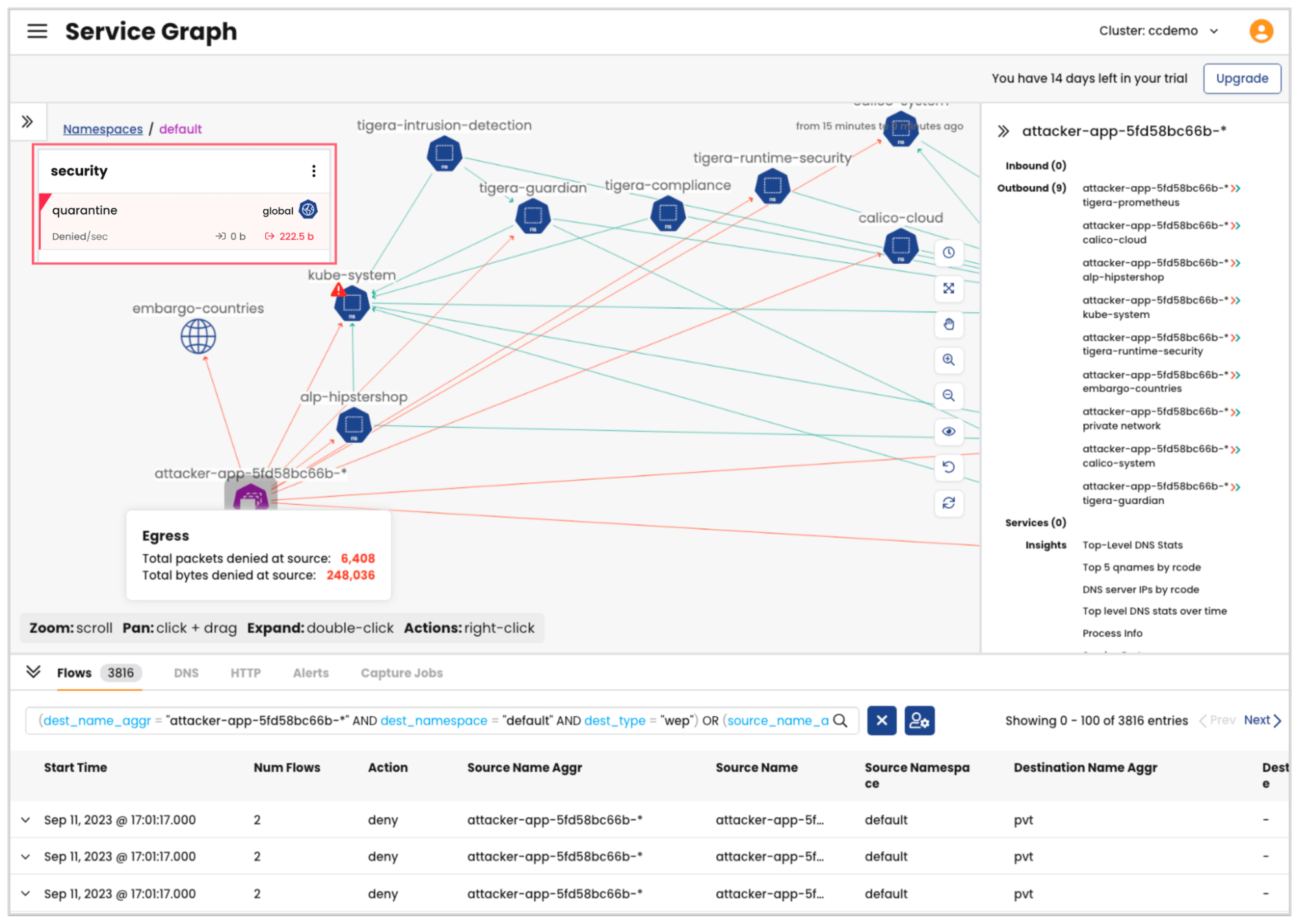
When a legitimate threat is identified in a cluster, Calico can be used to implement security policies to quarantine the affected workloads and limit their access to external networks or vital resources. In a scenario where a security incident is flagged, DevOps or security engineers may aim to isolate suspicious workloads to prevent them from interacting with or compromising legitimate workloads in the same cluster. Organizations may not be in a position to place the entire cluster in quarantine as such a measure could have a broader business impact. Calico offers a more nuanced approach to incident management, allowing for surgical isolation of suspicious workloads using security policies.
Recover
Once an organization has responded to a security event, post-incident forensic analysis is essential for digging deep into the causes of the security incident and strengthening future security measures. This involves examining various data points and logs to understand how the incident occurred and how similar events can be prevented. Calico’s observability across the technology stack plays a crucial role as it provides a detailed record of activities across multiple data points in the cluster. By examining these logs, security experts can trace back the sequence of activities that led to the incident. This audit trail makes it easier to identify vulnerabilities or configurations that may have been exploited, thereby providing insights into how to bolster security controls moving forward. A detailed view of time-series data means that teams can identify at which point a threat agent became active in the cluster.
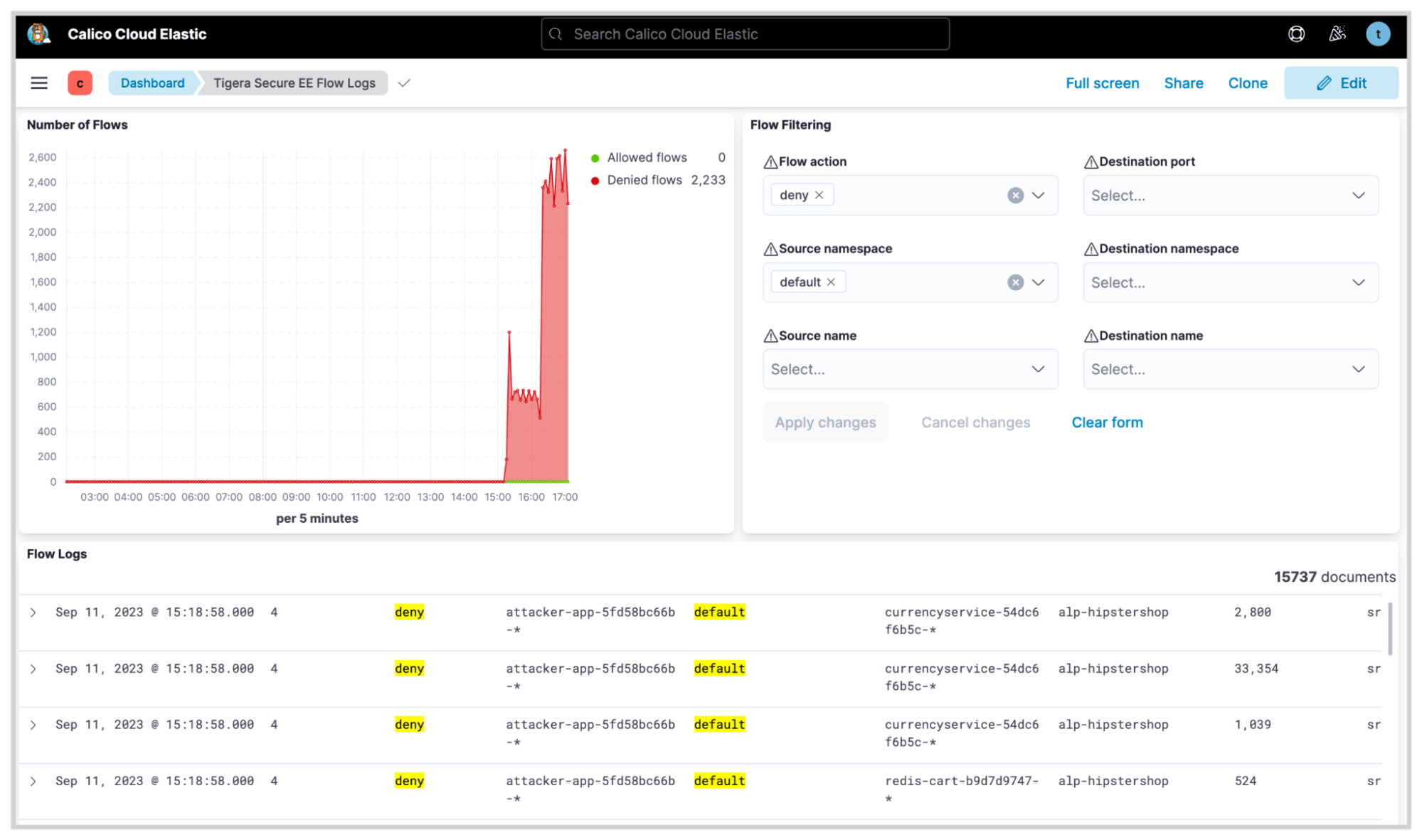
By correlating time-series data with other events in the cluster, it’s possible to identify the impact of a cybersecurity incident and initiate appropriate recovery procedures. For example, it’s possible to identify the impacted applications and initiate data restoration or patch an exploitable vulnerability using virtual patching capabilities offered by Calico’s Web Application Firewall (WAF).
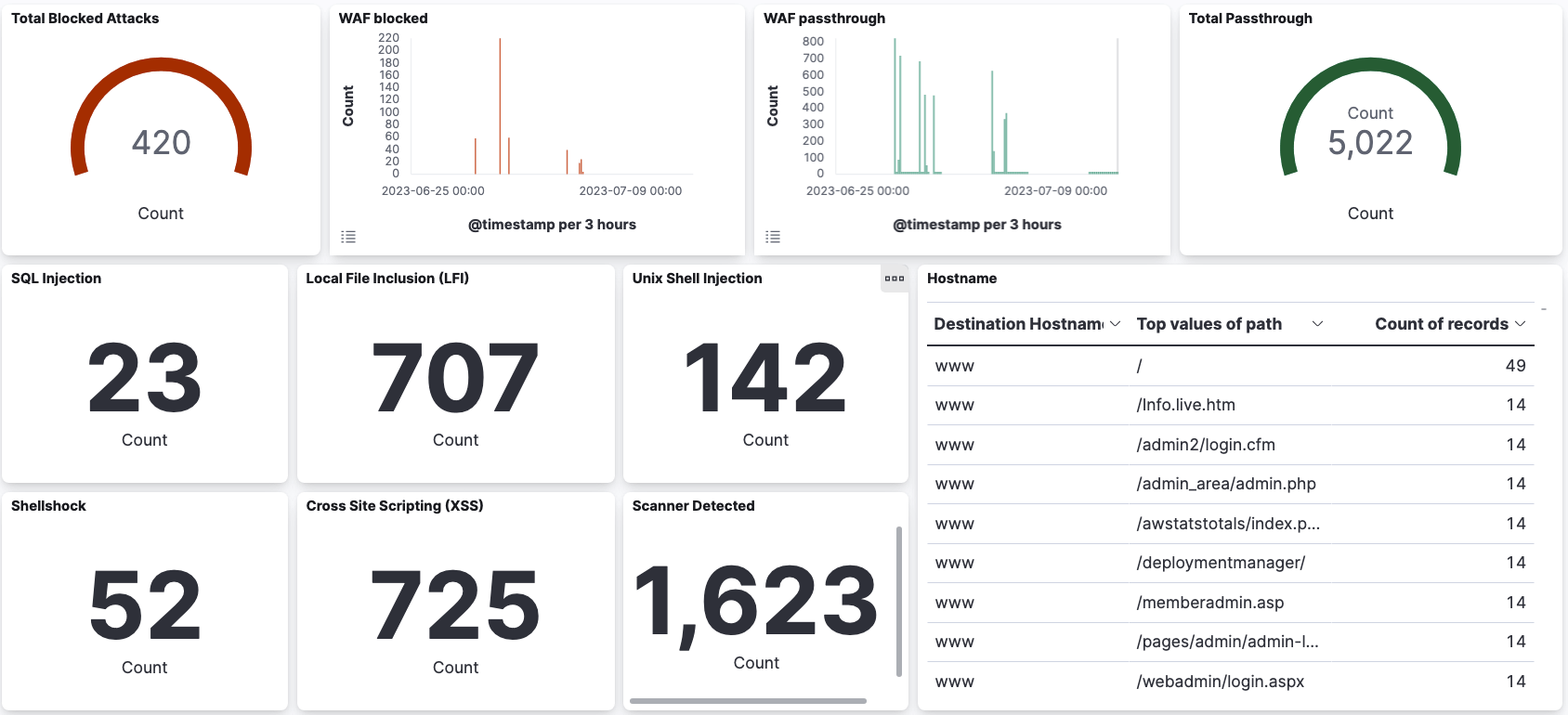
In a constantly evolving threat landscape, one of the greatest challenges faced by security teams is the risk of being caught off-guard by sophisticated threat actors. Calico’s advanced observability and security features serve as a critical safeguard against such threats.
Summary
In this blog post, we looked at how the NIST Cybersecurity Framework can be used to manage and reduce cybersecurity risks in a Kubernetes environment. Calico offers a comprehensive set of capabilities that allows security and DevOps engineers to deploy proactive and reactive measures to secure workloads and respond to incidents in Kubernetes. Calico’s capabilities can be aligned with the NIST CSF to develop robust standards, policies, and procedures to establish security governance for Kubernetes and containers.
Next Steps: Evaluate your Kubernetes environment security posture
Security professionals are invited to complete our brief NIST cybersecurity framework assessment to evaluate their organization’s security practices for container and Kubernetes environments in alignment with the NIST Cybersecurity Framework (CSF). Upon completing the survey, participants will receive a comprehensive guide that maps out how Calico Cloud can help them meet specific NIST CSF controls.
Ready to get started? Try Calico Cloud for free.
Join our mailing list
Get updates on blog posts, workshops, certification programs, new releases, and more!